Configure a TLS certificate by using an existing certificate
This topic tells you how to use the certificate information from your external certificate authority to encrypt inbound traffic to Tanzu Developer Portal (formerly called Tanzu Application Platform GUI).
Prerequisites
Your certificate authority gave you a certificate file, of the form CERTIFICATE-FILE-NAME.crt, and a signing key, of the form KEY-FILE-NAME.key. Ensure that these files are present on the host from which you run the CLI commands.
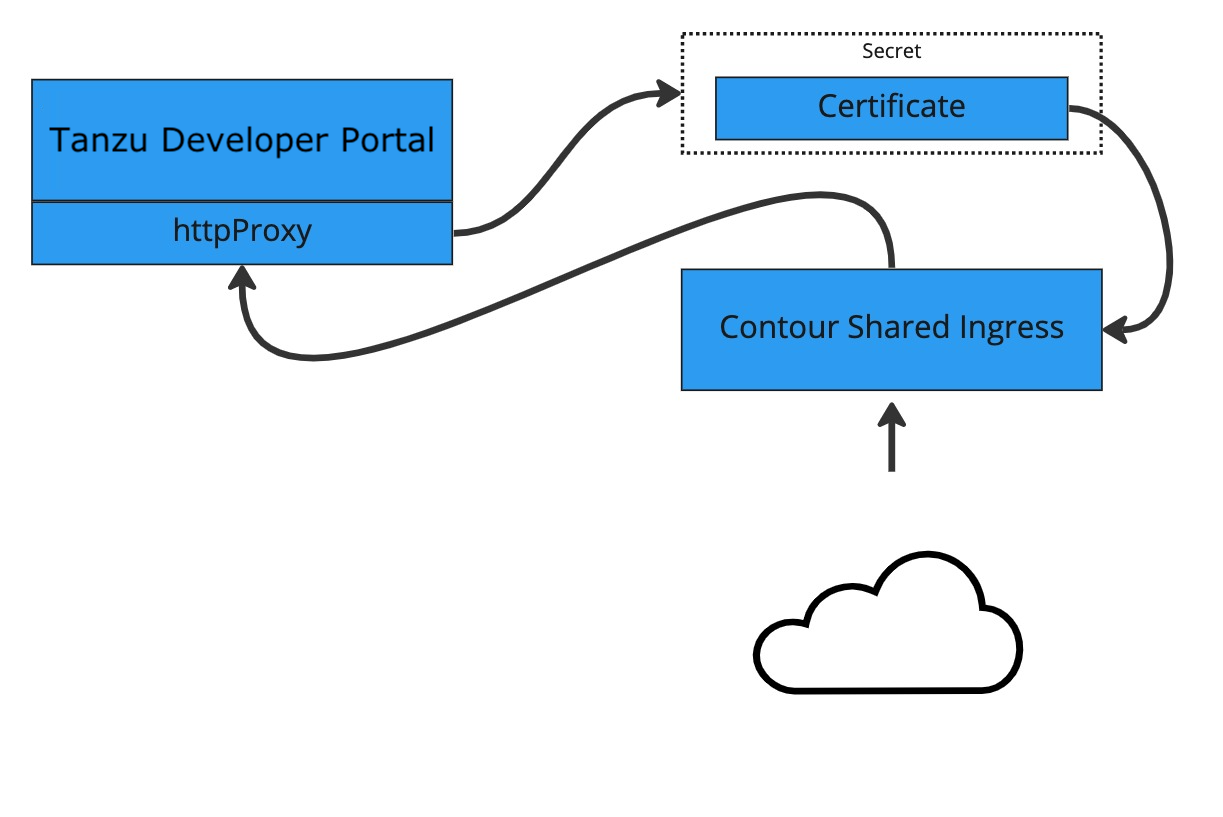
Procedure
To configure Tanzu Developer Portal with an existing certificate:
-
Create the Kubernetes secret by running:
kubectl create secret tls tap-gui-cert --key="KEY-FILE-NAME.key" --cert="CERTIFICATE-FILE-NAME.crt" -n tap-guiWhere:
KEY-FILE-NAMEis the name of thekeyfile that your certificate issuer gave youCERTIFICATE-FILE-NAMEis the name of thecrtfile that your certificate issuer gave you
-
Configure Tanzu Developer Portal to use the newly created secret. Do so by editing the
tap-values.yamlfile that you used during installation to include the following under thetap-guisection:- A top-level
tlskey with subkeys fornamespaceandsecretName - A namespace referring to the namespace used earlier
- A secret name referring to the
secretNamevalue defined earlier
Example:
tap_gui: tls: namespace: tap-gui secretName: tap-gui-cert # Additional configuration below this line as needed - A top-level
-
Update the Tanzu Application Platform package with the new values in
tap-values.yamlby running:tanzu package installed update tap -p tap.tanzu.vmware.com -v TAP-VERSION --values-file tap-values.yaml -n tap-installWhere
TAP-VERSIONis the version number that matches the values you used when you installed your profile.