You can configure route service lookup in VMware Tanzu Application Service for VMs (TAS for VMs).
You can bind your app to a route service to pre-process requests before they reach an app. Example use cases include authentication, rate limiting, and caching services. For more information, see Route Services.
The Bypass security checks for route service lookup check box in the Networking pane of the TAS for VMs tile allows you to configure how the Gorouter handles traffic for apps that are bound to route services. The configuration options are:
-
Default lookup: Default lookup is configured when you deactivate the Bypass security checks for route service lookup check box. In this case, the Gorouter does not check for an existing route. It sends traffic back through the load balancer when the traffic is for an internal route service.
-
Bypass mode: Bypass mode is configured when you enable the Bypass security checks for route service lookup check box. The Gorouter checks for an existing route. If the Gorouter finds the route and the route service is internal, it sends the traffic directly to the route service and skips the load balancer. This improves performance, but introduces the security risk described in Bypass Mode and External Route Service (Security Risk).
Configure Route Service lookup
These sections provide guidance and configuration steps for route service lookup.
Guidance
VMware recommends that you do not configure TAS for VMs for bypass mode because of the security risk described in Bypass Mode and External Route Service (Security Risk). However, you might need to do so if your load balancer requires mutual TLS from clients.
If your load balancer requires mutual TLS from clients and TAS for VMs is configured for default lookup, the Gorouter cannot handle traffic successfully for internal route services. This is because the Gorouter does not have the necessary certificates from the client to communicate back with the load balancer for DNS lookup. Therefore you must configure bypass mode so the Gorouter can send the traffic directly to the route service.
Configure TAS for VMs for bypass mode
To configure bypass mode:
-
Go to the VMware Tanzu Operations Manager Installation Dashboard.
-
Click the TAS for VMs tile.
-
Select Networking.
-
In Route services, select Allow.
-
Enable the Bypass security checks for route service lookup check box.
-
Follow the procedure in Mitigate Security Risk.
Mitigate security risk
To prevent users from intercepting traffic for externally-hosted route services:
-
Create an org for use by the TAS for VMs admin.
-
Register all external route service domains as private domains in the org you created.
-
Monitor TAS for VMs for the addition of new external route services and ensure you follow the same process for those external route services. One way to do this is by using
cf curlto regularly view a list of user-provided service instances. Run:cf curl /v2/user_provided_service_instancesNote Since route services can be added by any space developer, this can be difficult to manage.
Configure TAS for VMs for default lookup
To configure TAS for VMs for default lookup behavior, with bypass mode deactivated:
-
Go to the VMware Tanzu Operations Manager Installation Dashboard.
-
Click the TAS for VMs tile.
-
Select Networking.
-
In Route services, select Allow.
-
Deactivate the Bypass security checks for route service lookup check box.
-
Communicate to developers of route services that the domain name for their internally-hosted route services must resolve to the load balancer.
-
If your load balancer or Gorouter terminates TLS:
- Work with developers of route services to ensure the load balancer or Gorouter have TLS certificates that are valid for the route service URL.
- Ensure that the TLS certificate from your load balancer is either signed by a well-known Certificate Authority (CA), or the CA has been added to the Certificate Authorities trusted by the Gorouter and HAProxy field in the Networking pane of the TAS for VMs and Isolation Segment tiles. The CA for the TLS certificate provided by the load balancer must be trusted by the Gorouter.
-
Work with developers of route services to verify that their internal route service apps are reachable. You can do this by visiting the HTTPS URL of the route service directly and confirming that the app received the request with the
cf logsoutput for the route service app.
Summary of behavior in different configurations
These sections describe how the Gorouter behaves when bypass mode is activated or deactivated and when a route service is internal or external.
Default lookup and internal route service
This section describes how the Gorouter handles app requests when:
- The Bypass security checks for route service lookup check box in TAS for VMs is deactivated.
- The app is bound to a route service that is hosted on TAS for VMs.
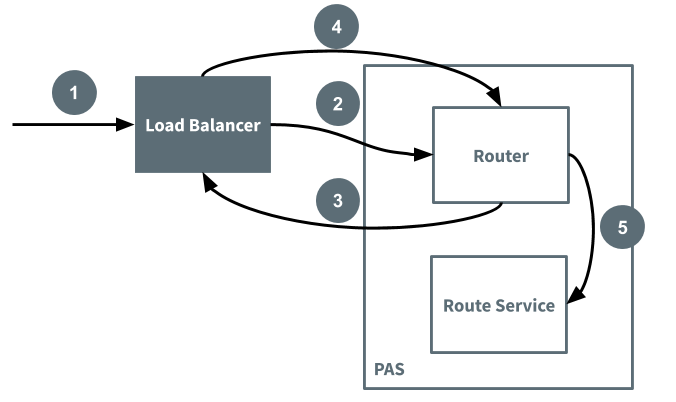
In this case, when the Gorouter receives the request, it sends the traffic back to the load balancer to resolve DNS. The load balancer then sends the traffic back to the Gorouter.
The following diagram illustrates the flow of the request and numbers the steps to indicate order of occurrence:
Bypass mode and internal route service
This section describes how the Gorouter handles app requests when:
- The Bypass security checks for route service lookup check box in TAS for VMs is enabled.
- The app is bound to a route service that is hosted on TAS for VMs.
In this case, when the Gorouter receives the request, it sends it directly to the route service. This assumes the Gorouter finds an existing route for the route service.
Bypass mode and external route service (security risk)
This section describes how the Gorouter handles app requests when:
- The Bypass security checks for route service lookup check box in TAS for VMs is enabled.
- The app is bound to a route service that is hosted outside of TAS for VMs.
In this case, when the Gorouter receives the request, it checks for an existing route and then sends the request directly to the route service. This enables external clients to intercept route service traffic. A developer can register the external route service domain as a private domain in TAS for VMs and map it to their own, malicious app. When the Gorouter receives a request for the original app bound to the external route service, it finds the domain internally and sends the request to the malicious app.
This vulnerability exists for both externally hosted route services and route services hosted on a separate foundation. If all of your route services are hosted internally on the same foundation, you are not at risk. However, you would be at risk if externally hosted route services are configured later.
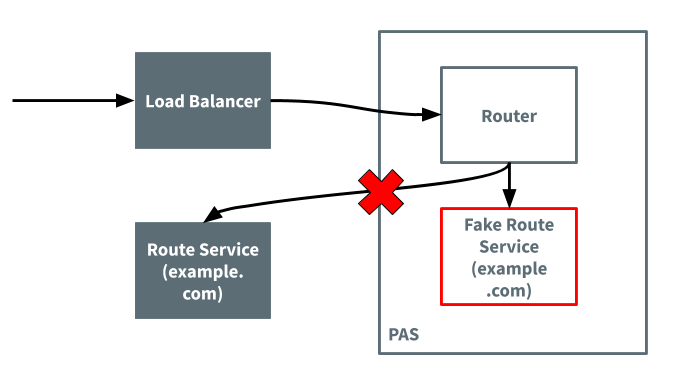
A fake route service inside of TAS for VMs intercepts traffic intended for a route service outside of TAS for VMs. Five boxes are labeled as follows: Load Balancer, Gorouter, Route Service (example.com), Fake Route Service (example.com), and TAS for VMs. The Gorouter and fake route service boxes are inside of the TAS for VMs box to show that they are running inside of TAS for VMs. The arrows point to the load balancer and then the Gorouter to indicate the flow of traffic. The two arrows then point from the Gorouter: one to the fake route service and another to the route service. A red “X” indicates that the traffic does not go to the route service. It instead goes to the fake route service.
The following diagram illustrates the flow of the request in the case that it is intercepted.
Default lookup and external route service
This section describes how the Gorouter handles app requests when:
- The Bypass security checks for route service lookup check box in TAS for VMs is deactivated.
- The app is bound to a route service that is hosted outside of TAS for VMs.
In this case, the Gorouter sends traffic directly to the external route service without checking for an existing route.
The following diagram illustrates the flow of the request. The arrows indicate the flow of the request through platform components. A request goes directly from the load balancer to the Gorouter to the route service.