This topic describes how to create a public-facing website and an intranet microservice in the same app.
Overview
The configuration described in this topic may be ideal for those in financial or health sectors who need extra security and convenience managing internal and external services. If the configuration is successful, developers can only use the Cloud Foundry Command Line Interface (cf CLI) command cf push from approved network paths. For more information about cf push, see the push section of the cf CLI documentation.
Prerequisites
Before beginning your configuration, you must register three domains through your trusted DNS provider:
-
A system domain for VMware Tanzu Application Service for VMs (TAS for VMs) and its accompanying tile services
-
An apps domain for your intranet microservice
-
An additional domain for the public-facing portions of your app
Note: VMware recommends that you use the same domain name but different subdomain names for your system and app domains. Doing so allows you to use a single wildcard certificate for the domain while preventing apps from creating routes that overlap with system routes.
Step 1: Configure System and Apps Domains
-
Navigate to the Ops Manager Installation Dashboard.
-
Click the TAS for VMs tile.
-
Select Domains.
-
Enter the System domain and Apps domain defined in Prerequisites.

-
Navigate to your DNS provider to create A records that point from your apps domains to the public IP address of your load balancer.
-
Click Save.
Step 2: Secure Apps Domain with HAProxy
Caution This method is easy to implement but may not be the best option for your security needs. Contact Support if you need a custom solution to building secure, internal services.
VMware supports HAProxy by default. However, you may configure an internal domain using any load balancer you choose that supports host header filtering.
-
Navigate to the Ops Manager Installation Dashboard.
-
Click the TAS for VMs tile.
-
Select Networking.
-
Enter HAProxy protected domains. The domain you enter should be the same domain as the Apps domain defined in Prerequisites.
-
Enter HAProxy trusted CIDRs, separated by spaces. This specifies CIDRs allowed to make requests to the domains listed in the HAProxy protected domains field. For example, entering
10.0.1.0/24would allow any requests originating at a host IP in that range to reach apps or services hosted on the HAProxy protected domains list. -
(Optional) If you want to force browsers to use HTTPS when making requests to HAProxy, select Enable under HAProxy support for HSTS and complete these optional configuration steps:
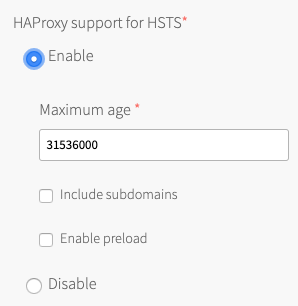
- Enter a Maximum age in seconds for the HSTS request. HAProxy forces HTTPS requests from browsers for the duration of this setting. The maximum age is one year, or 31536000 seconds.
- Enable the Include subdomains check box to force browsers to use HTTPS requests for all component subdomains.
-
Select the Enable preload check box to force instances of Google Chrome, Firefox, and Safari that access your HAProxy to refer to their built-in lists of known hosts that require HTTPS, of which HAProxy is one. This ensures that the first contact a browser has with your HAProxy is an HTTPS request, even if the browser has not yet received an HSTS header from HAProxy.
-
(Optional) Configure an additional HAProxy for BOSH to secure your public-facing domain with credentials. For more information, see proxy-boshrelease on GitHub.
Step 3: (Optional) Enable an Authentication Service
For added security, you may want to install an authentication service to your private domain like Single Sign-on (SSO) for VMware Tanzu. For more information about SSO for VMware Tanzu, see Single Sign-On Overview.