This topic provides you with an overview of VMware Tanzu Application Service for VMs (TAS for VMs) security. For an overview of container security, see Container Security.
TAS for VMs implements the following measures to mitigate against security threats:
- Minimizes network surface area
- Isolates customer apps and data in containers
- Encrypts connections
- Uses role-based access controls, applying and enforcing roles and permissions to ensure that users can only view and affect the spaces for which they have been granted access
- Ensures security of app bits in a multi-tenant environment
- Prevents possible denial of service attacks through resource starvation
System boundaries and access
In a typical deployment of TAS for VMs, the components run on virtual machines (VMs) that exist within a VLAN.
In this configuration, the only access points visible on a public network are a load balancer that maps to one or more TAS for VMs routers and, optionally, a NAT VM and a jumpbox. Because of the limited number of contact points with the public internet, the surface area for possible security vulnerabilities is minimized.
As the following diagram shows the architecture of a typical deployment of TAS for VMs:
Important VMware recommends that you also install a NAT VM for outbound requests and a jumpbox to access the BOSH Director, though these access points are optional depending on your network configuration.
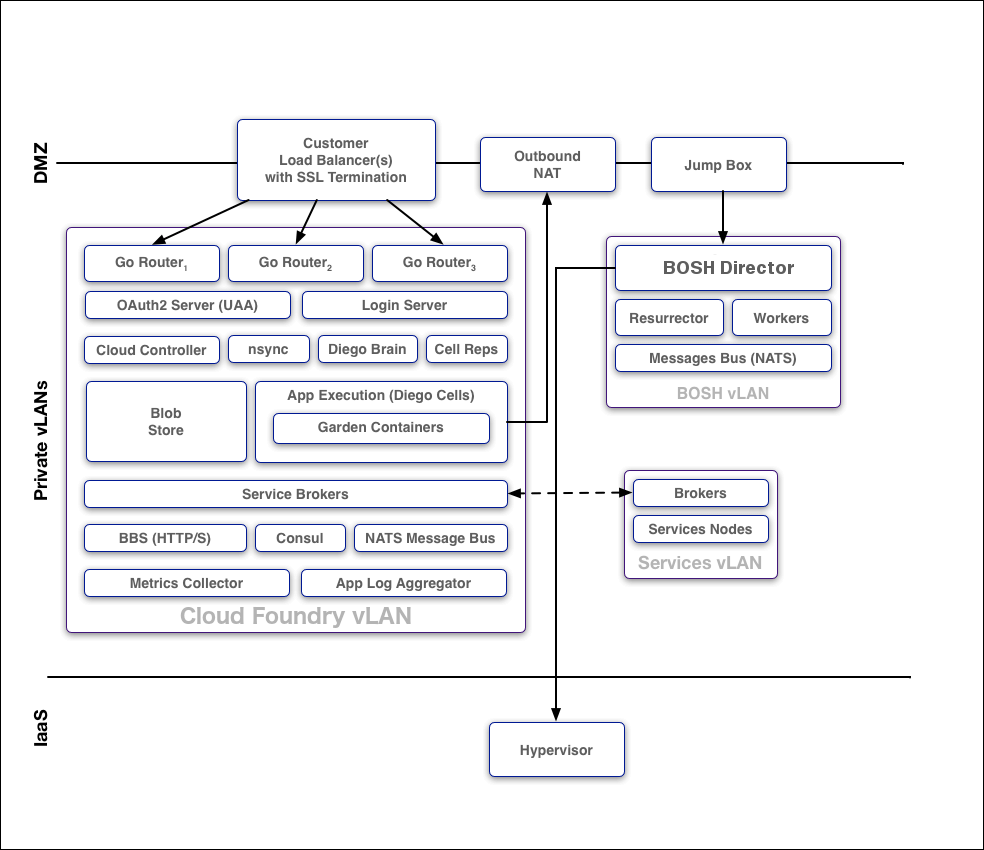
The above diagram shows the following components:
- DMZ
- Customer Load Balancers with SSL Termination
- Outbound NAT
- Jumpbox
- Private vLANs
- Cloud Foundry vLAN
- Three Go Routers
- OAuth2 Server (UAA)
- Login Server
- Cloud Controller
- nsync
- Diego Brain
- Cell Reps
- Blob Store
- App Execution (Diego Cells) with Garden Containers
- Service Brokers
- BBS (HTTP/S)
- Consul
- NATS Message Bus
- Metrics Collector
- App Log Aggregator
- BOSH vLAN
- BOSH Director
- Resurrector
- Workers -Message Bus (NATS)
- Services vLAN
- Brokers
- Services Nodes
- IaaS
- Hypervisor
The diagram above shows the following communications:
-
Customer Load Balancers send communication to the three Go Routers
-
Outbound NAT communicates with Hypervisor
-
BOSH Director communicates with the App Execution (Diego Cells)
-
Service Brokers in Cloud Foundry vLAN communicates with Brokers in Services vLAN
Protocols
All traffic from the public internet to the Cloud Controller and UAA happens over HTTPS. Inside the boundary of the system, components communicate over a publish-subscribe (pub-sub) message bus NATS, HTTP, and SSL/TLS.
BOSH
Operators deploy TAS for VMs with BOSH. The BOSH Director is the core orchestrating component in BOSH: it controls VM creation and deployment, as well as other software and service lifecycle events. You use HTTPS to ensure secure communication to the BOSH Director.
VMware recommends that you deploy the BOSH Director on a subnet that is not publicly accessible, and access the BOSH Director from a jumpbox on the subnet or through VPN.
BOSH includes the following functionality for security:
-
Communicates with the VMs it launches over NATS. Because NATS cannot be accessed from outside TAS for VMs, this ensures that published messages can only originate from a component within your deployment.
-
Provides an audit trail through the
bosh tasks --allandbosh tasks --recent=VALUEcommands.bosh tasks --allreturns a table that shows all BOSH actions taken by an operator or other running processes.bosh tasks --recent=VALUEreturns a table of recent tasks, withVALUEbeing the number of recent tasks you want to view. -
Allows you to set up individual login accounts for each operator. BOSH operators have root access.
Important BOSH does not encrypt data stored on BOSH VMs. Your IaaS might encrypt this data.
Isolation segments
Isolation segments provide dedicated pools of resources to which apps can be deployed to isolate workloads. Using isolation segments separates app resources as completely as if they were in different TAS for VMs deployments but avoids redundant management components and unneeded network complexity.
You can designate isolation segments for exclusive use by orgs and spaces within TAS for VMs. This guarantees that apps within the org or space use resources that are not also used by other orgs or spaces. For more information, see Orgs, Spaces, Roles, and Permissions.
Customers can use isolation segments for different reasons, including:
-
To follow regulatory restrictions that require separation between different types of apps. For example, a health care company might not be able to host medical records and billing systems on the same machines.
-
To dedicate specific hardware to different isolation segments. For example, to ensure that high-priority apps run on a cluster of high-performance hosts.
-
To separate data on multiple clients, to strengthen a security story, or offer different hosting tiers.
In TAS for VMs, the Cloud Controller database (CCDB) identifies isolation segments by name and GUID, for example 30dd879c-ee2f-11db-8314-0800200c9a66. The isolation segment object has no internal structure beyond these two properties at the TAS for VMs level, but BOSH associates the name of the isolation segment with Diego Cells, through their placement_tag property.
This diagram shows how isolation segments keep apps running on different pools of Diego Cells, and how the Diego Cells communicate with each other and with the management components: 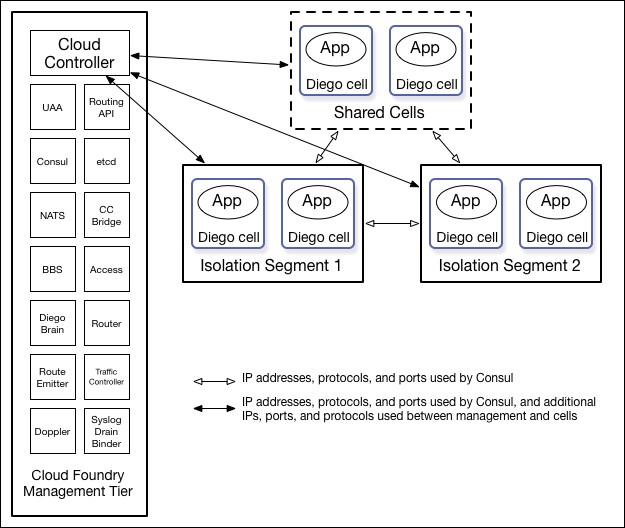
For more information about how to create and manage isolation segments in an Tanzu Operations Manager deployment, see Installing Isolation Segment and Managing Isolation Segments.
For API commands related to isolation segments, see Isolation Segments in the Cloud Controller API(CAPI) Reference.
Authentication and authorization
User Account and Authentication (UAA) is the central identity management service for TAS for VMs and its various components.
UAA acts as an OAuth2 Authorization Server and issues access tokens for apps that request platform resources. The tokens are based on the JSON Web Token and are digitally signed by UAA.
Operators can use SAML to connect to an external user store and enable single sign-on for users into the TAS for VMs platform.
Standard TAS for VMs deployments based on cf-deployment provide a UAA client cf that can be used to create OAuth 2 tokens using the Password Grant Flow for TAS for VMs users that are needed to access the CF API. This UAA client is also used by the CF CLI. The UAA client cf doesn’t require a client_secret.
Managing user access with Role-Based Access Control
Apps that users deploy to TAS for VMs exist within a space. Spaces exist within orgs. To view and access an org or a space, a user must be a member of it. TAS for VMs uses role-based access control (RBAC), with each role granted permissions, see Orgs, Spaces, Roles, and Permissions.
For more information, see Getting Started with Apps Manager and Managing User Roles using Apps Manager.
Security for service broker integration
The Cloud Controller authenticates every request with the Service Broker API using HTTP or HTTPS, depending on which protocol that you specify during broker registration. The Cloud Controller rejects any broker registration that does not contain a username and password.
Service instances bound to an app contain credential data. Users specify the binding credentials for user-provided service instances, while third-party brokers specify the binding credentials for managed service instances. The VCAP_SERVICES environment variable contains credential information for any service bound to an app. TAS for VMs constructs this value from encrypted data that it stores in the CCDB. For more information about user-provided service instances, see User-Provided Service Instances.
The selected third-party broker controls how securely to communicate managed service credentials.
A third-party broker might offer a dashboard client in its catalog. Dashboard clients require a text string defined as a client_secret. TAS for VMs does not store this secret in the CCDB. Instead, TAS for VMs passes the secret to the UAA component for verification using HTTP or HTTPS.
Managing software vulnerabilities
TAS for VMs manages software vulnerability using releases and BOSH stemcells. New TAS for VMs releases are created with updates to address code issues, while new stemcells are created with patches for the latest security fixes to address any underlying operating system issues.
Ensuring security for app artifacts
TAS for VMs secures both the code and the configuration of an app using the following functionality:
-
App developers push their code using the TAS for VMs API. TAS for VMs secures each call to the TAS for VMs API using the UAA and SSL.
-
The Cloud Controller uses RBAC to ensure that only authorized users can access a particular app.
-
The Cloud Controller stores the configuration for an app in an encrypted database table. This configuration data includes user-specified environment variables and service credentials for any services bound to the app.
-
TAS for VMs runs the app inside a secure container. For more information, see Container Security.
-
TAS for VMs operators can configure network traffic rules to control inbound communication to and outbound communication from an app. For more information, see the Network Traffic Rules section of the Container Security topic.
Security event logging and auditing
For operators, TAS for VMs provides an audit trail through the bosh tasks command. This command shows all actions that an operator has taken with the platform. Additionally, operators can redirect TAS for VMs component logs to a standard syslog server using the syslog_daemon_config propery in the metron_agent job of cf-release.
For users, TAS for VMs records an audit trail of all relevant API invocations of an app. The Cloud Foundry Command Line Interface (cf CLI) command cf events returns this information.
Recommendations for running a secure deployment
To help run a secure deployment, VMware recommends:
-
Configure UAA clients and users using a BOSH manifest. Limit and manage these clients and users as you would any other kind of privileged account.
-
Deploy within a VLAN that limits network traffic to individual VMs. This reduces the possibility of unauthorized access to the VMs within your BOSH-managed cloud.
-
Enable HTTPS for apps and SSL database connections to protect sensitive data transmitted to and from apps.
-
Ensure that the jumpbox is secure, along with the load balancer and NAT VM.
-
Encrypt stored files and data within databases to meet your data security requirements. Deploy using industry standard encryption and the best practices for your language or framework.
-
Prohibit promiscuous network interfaces on the trusted network.
-
Review and monitor data sharing and security practices with third-party services that you use to provide additional functionality to your app.
-
Store SSH keys securely to prevent disclosure, and promptly replace lost or compromised keys.
-
Use TAS for VMs’s RBAC model to restrict your users’ access to only what is necessary to complete their tasks.
-
Use a strong passphrase for both your TAS for VMs user account and SSH keys.
-
Use the IPsec for VMware Tanzu to encrypt IP data traffic within your deployment.
Compliance
For information about compliance in TAS for VMs, see the following topics:- NIST Controls and VMware Tanzu Application Service for VMs: Provides a dedicated site that assesses TAS for VMs against NIST SP 800-53(r4) Controls.
- General Data Protection Regulation: Provides an overview of the General Data Protection Regulation (GDPR) and where TAS for VMs might store personal data.
Security for apps and services
This section links to topics that describe how TAS for VMs and TAS for VMs users manage security for apps and service instances.
- App Security Groups: Describes how App Security Groups (ASGs) work and how to manage them in TAS for VMs.
- Configuring SSH Access for TAS for VMs: Explains how to configure TAS for VMs to allow SSH access to app instances for debugging.
- Restricting App Access to Internal TAS for VMs Components: Details how to create ASGs, rules that allow internal outgoing communications from all apps in TAS for VMs, or the apps running in the same space.
- Configuring App Security Groups for Email Notifications: Describes how to define an ASG to enable app-generated notifications.
-
Trusted System Certificates: Explains where apps can find trusted system certificates.
-
Managing Access to Service Plans: Describes how to enable or disable access to service plans for a subset of users.
-
Delivering Service Credentials to an App: Describes how to bind apps to service instances, which generate the credentials that enable the apps to use the service.
-
Managing Service Keys: Explains how to create and manage service keys that enable apps to use service instances.