Setting up AWS Account
Depending on the type, you can configure Tanzu CloudHealth to populate complete cost and usage information for your AWS account.
Configuring AWS Payer Account
An AWS payer account is a designated billing account to which one or more additional accounts can be linked. The billing contact for the account receives a statement that summarizes the charges for all its linked accounts. For more information, see Paying Bills for Multiple Accounts Using Consolidated Billing. Use the following steps to set up an AWS payer account in Tanzu CloudHealth:
Step 1 - Enable Cost and Usage Report
Create CUR in AWS Console
Note: As of now, Tanzu CloudHealth does not support CUR 2.0, the new format of CUR export. On configuring new CURs, you must select the Legacy CUR Export option.
AWS Cost and Usage Reports (CUR) provide comprehensive data about your costs, including those related to product, pricing, and usage. For more information, see AWS Cost and Usage Reports.
In order to take advantage of these new features, configure your AWS account to create a CUR and make it available for consumption by the platform.
- In the AWS Console navigate to your profile name and click Account.
- From the left menu, select Cost & Usage Reports and click Create report.
- Navigate the configuration wizard, ensuring that you make the following entries and selections.
- Report Name: Use an easily identifiable name, for example,
cloudhealth-hourly-cur. - Check the box next to Include Resource ID.
- Check the box next to Automatically refresh your Cost & Usage Report when charges are detected for previous months with closed bills.
- S3 Bucket: Under Configure S3 Bucket click Configure. You can either create a bucket or select an existing one. It must be a unique bucket name and region. Review the policy that is generated for the bucket, check the box to accept this as the default policy, and click Save.
- Report path prefix: Enter a unique prefix.
- Time granularity: Select Hourly.
- Report versioning: Select Create new report version.
- Compression: Select GZIP.
- Click Review and Complete.
Enable Legacy Reports
The monthly statement from the legacy reports, is one way we can map your Tanzu CloudHealth account name to your AWS account name. If you skip this step, the Amazon name associated with your account may be blank in Tanzu CloudHealth platform.
- From the left menu, choose Preferences > Billing preferences.
- For Detailed billing reports (legacy), click Edit.
- Select Legacy reports delivered to S3.
- Select Configure and S3 bucket to activate. In the pop-up from there, select Select an existing S3 bucket, and use the same bucket you used in the previous step.
- Click Next, review and confirm the policy, and click Save.
- Select all reports under Report activation and click Activate.
Configure Cost Allocation Tags
Tanzu CloudHealth extracts the tags and resource IDs from your billing artifact and automatically allocates costs for your taggable AWS services. To support the derivation of asset and tag data from the CUR, you must configure the AWS Account to include Cost Allocation Tags in the CUR artifacts.
Note: Tanzu CloudHealth recommends adding each tag key you use for perspective grouping as a Cost Allocation Tag. For more information, see Using Cost Allocation Tags
- In the AWS Console, navigate to the AWS Billing dashboard.
- From the left menu, choose Cost Allocation Tags.
- Select the tags that you want to activate.
- Click Activate.
It can take up to 24 hours for activation of the selected tags.
Enable the CUR in Tanzu CloudHealth
- Navigate to select Setup > Accounts > AWS and edit the AWS account for which the CUR should be enabled. Enable the CUR only for Consolidated or Standalone accounts.
- In the Cost and Usage Report section, enter the following information.
- Bucket Name: Name of S3 bucket that stores the hourly CUR data.
- Report Path: The path to the CUR, and the name of the CUR, separated by a slash. Tanzu CloudHealth uses the information you provide in these fields to access your CUR. Inaccuracies in these values can cause errors when Tanzu CloudHealth attempts to access the reports. To locate accurate values for these fields, navigate to the Billing & Cost Management Dashboard in the AWS Console. From the left menu, select Cost & Usage Reports. Click the name of the report to view the bucket name and report path.
- Update the policy associated with the IAM role for this account to grant permission to access and read the CUR. Click Generate Policy to produce a new IAM policy. If the policy is not updated, Tanzu CloudHealth will be unable to access the bucket and read the CUR reports stored inside it.
- In the IAM Access Policy dialog box, click Select All and copy the contents to the clipboard.
- Switch to the AWS Console and navigate to Services > Security, Identity & Compliance > IAM. From the left menu, select Policies and locate the IAM Access Policy you are using for the Tanzu CloudHealth platform.
- In the Permissions tab, click JSON and click Edit policy.
- Paste the policy you copied from the platform into the editor, and Save the policy.
- In the Tanzu CloudHealth platform, return to the AWS account you were editing and click Save Account.
Step 2 - Set up Read-Only IAM Role using IAM service
Create a read-only IAM role within the AWS Console for the target account. Then add these credentials to the platform. The default AWS Read-Only policy provides read access to data, such as S3 objects, and is therefore discouraged from being used.
- Log in to the AWS Console for the targeted account as a user who has permission to create an IAM role.
- Navigate to Services > Security, Identity, & Compliance > IAM. From the left menu, select Policies and click Create Policy.
- Switch to the JSON tab.
- In a separate browser window, log in to the Tanzu CloudHealth platform. From the menu, select Setup > Accounts > AWS and open the AWS account you created previously.
- Enter the name of the billing bucket you created and click Generate Policy. The bucket name is included in the resulting policy.
- The IAM Access Policy dialog box appears. Click Select All and copy the contents to the clipboard.
- Return to the AWS Console and paste the policy into the JSON tab. Then click Review Policy.
- Name the policy (e.g., CHTPolicy), provide a description, and click Create policy.
- In the AWS Console, from the left menu, select Roles and click Create role.
- On the Select trusted entity page, choose AWS account.
- Select Another AWS account. In the Account ID field, enter
454464851268, which is the ID of the secure Tanzu CloudHealth-managed account. - Select the Require external ID Option. From the Tanzu CloudHealth platform, copy the Tanzu CloudHealth generated External ID from the account setup form. This ID is unique for each Tanzu CloudHealth customer so that you can reuse it across all your accounts.
- Paste this copied ID in the External ID field in the AWS Console.
- Leave the checkbox for Require MFA cleared because the IAM role will be used to provide programmatic access to the Tanzu CloudHealth platform. Click Next.
- On the Add Permissions page, set the filter to customer managed and choose the Tanzu CloudHealth policy you created. Click Next.
- Enter a name and description for the role and click Create Role.
- From the IAM > Roles page, select the role you just created. Copy the value of RoleARN to the clipboard.
- Return to the AWS Account Setup page in the Tanzu CloudHealth platform. In the API section, paste the Role ARN value.
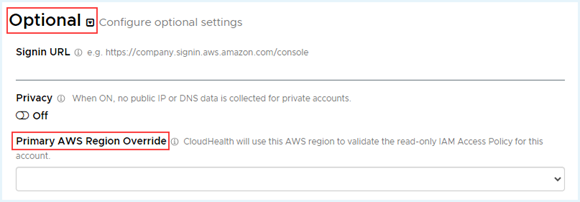
- By default, Tanzu CloudHealth validates the read-only IAM policy with the us-east-1 AWS region. If you do not have access to the us-east-1 region, you must select a different region for validation. Under Optional, select the desired region from the Primary AWS Region Override dropdown.
- Click Save Account.
Tanzu CloudHealth validates your account and begins collecting data. If there are issues with any information you provided, an error message appears.
Step 3 - Enable AWS Console Integration (Optional)
View asset details in the AWS Console through links from the Tanzu CloudHealth platform In the Tanzu CloudHealth platform, instances have links that allow you to view them in the AWS Console. These links are set up by enabling AWS Console integration from the Tanzu CloudHealth platform.

- Navigate to select Setup > Accounts > AWS.
- From the list of AWS accounts, edit the account for which you want to add AWS Console integration.
- In a separate browser window, login to the AWS Console.
- From the menu, select Security, Identity, & Compliance > IAM.
- From IAM Dashboard > AWS Account, copy the IAM User Sign-In URL into the clipboard.
- Back in the Tanzu CloudHealth platform, expand the Optional section of the account setup form. Paste the URL in the Signin URL field.
- Click Save Account to enable AWS Console integration.
Step 4 - Enable CloudWatch (Optional)
Install and configure the AWS CloudWatch Agent in your EC2 Instances so that the agent can start collecting metrics from those instances Repeat the following steps for each account you want to enable CloudWatch metrics for.
- Follow the instructions in AWS documentation to install and configure the AWS CloudWatch Agent in your EC2 Instances so that the agent can start collecting metrics from those instances. This process comprises the following high-level steps.
- Installing and configuring the CloudWatch Agent
- Creating IAM roles and users for use with the CloudWatch Agent
- Creating a CloudWatch Agent configuration file For detailed instructions, see AWS documentation on Collecting Metrics and Logs from Amazon EC2 Instances and On-Premises Servers with the CloudWatch Agent.
- Navigate to select Setup > AWS Accounts and edit each account for which you want to enable CloudWatch metrics collection.
- Expand the Optional section of the account setup form and switch on the CloudWatch option.
- Select the frequency at which the CloudWatch Runtime Cycle should run. Higher frequencies will incur greater cost due to increased API calls.
- In order to enable Tanzu CloudHealth to collect CloudWatch metrics from additional namespaces, select one or more namespaces from the list. Namespaces allow you to organize your CloudWatch metrics, which you can utilize for rightsizing your EC2 Instances using the Tanzu CloudHealth Platform.
- Update the policy associated with the IAM role for this account to grant Tanzu CloudHealth permission to read your CloudWatch metrics. Click Generate Policy to produce a new IAM policy.
- In the IAM Access Policy dialog box, click Select All and copy the contents to the clipboard.
- In a separate browser window, log in to the AWS Console as an administrator and navigate to Services > Security, Identity, & Compliance > IAM. From the left menu, select Policies and locate the IAM Access Policy you are using for the Tanzu CloudHealth Platform.
- In the Permissions tab, click JSON and paste the policy you copied from the Tanzu CloudHealth platform into the editor. Then click Save.
- In the Tanzu CloudHealth Platform, return to the AWS account you were editing and click Save Account. Tanzu CloudHealth validates the account and starts collecting data. If there are issues, a warning message appears. AWS CloudWatch metrics begin appearing in the Tanzu CloudHealth platform after about 24 hours.
The spend-based asset collection feature considerably changes the initial asset collection time for a newly added account and service. Once a new asset or service is billed, it could take a minimum of 24 hours to appear in the Tanzu CloudHealth reports. After the initial delay, the platform continues to update the asset or service details as per the standard collection frequency.
Step 5 - Enable CloudTrail (Optional)
CloudTrail is a service that provides an audit log for all API access to AWS. Tanzu CloudHealth can collect CloudTrail data to help you identify who launched or shut down infrastructure or made security changes across your infrastructure.
Typically, a single CloudTrail bucket collects logs for multiple accounts. Here are two scenarios to consider:
- If each of your accounts has its own bucket, enable CloudTrail for each account.
- If multiple accounts are feeding a single bucket, first enable CloudTrail for the account containing the bucket, and then enable CloudTrail for each account that feeds into the bucket.
Enable an AWS Account for a CloudTrail Bucket
- In the AWS Console, navigate to the CloudTrail service. In Dashboard, click the trail name to find the Name and Prefix for the S3 bucket configured to store the CloudTrail logs.
- In the General details section, click Edit . The dialog box shows the name of the S3 bucket and any custom Log file prefix that is configured.

- In a separate browser window, log in to the Tanzu CloudHealth platform. From the menu, select Setup > AWS Accounts and edit each account that contains a CloudTrail bucket.
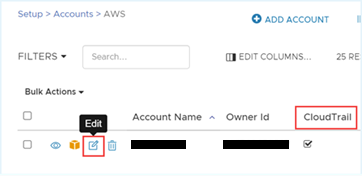
- Expand the Optional section of the account setup form and switch on the CloudTrail option.

- Enter the CloudTrail Bucket Name and CloudTrail Account Prefix (if you configured a custom prefix).
- Update the policy associated with the IAM role for this account to grant permission to read from the CloudTrail bucket. Click Generate Policy to produce a new IAM policy that grants access to the bucket entered in the previous step.
- In the IAM Access Policy dialog box, click Select All and copy the contents to the clipboard.
- Switch to the AWS Console and paste the policy in the Policy Document field. Then click Apply Policy.
- Switch back to the Tanzu CloudHealth platform and click Save Account.
Tanzu CloudHealth validates the account and starts collecting data. If there are issues, a warning message appears. CloudTrail events begin appearing in the Tanzu CloudHealth platform after about 15-30 minutes. More stable accounts tend to have few events.
Note:
- Tanzu CloudHealth collects all events from 12:00 GMT on the day when the account is configured.
- If each of your AWS accounts has its own CloudTrail bucket, repeat steps 1-9 for each AWS account. If each of your AWS accounts feeds into a single bucket, proceed to the next section.
Enable all AWS Accounts in your Organization for a CloudTrail Bucket (Optional)
- In the AWS Console, navigate to the CloudTrail service. In Dashboard, click the trail name to find the Name and Prefix of the S3 bucket configured to store the CloudTrail logs.
- In the General details section, click Edit.
- Select Enable for all accounts in my organization to change the CloudTrail file path in your S3 bucket. An Organization ID gets added to the CloudTrail file path. For example, if the default CloudTrail bucket file path is
AWSLogs/[OWNER_ID]/CloudTrail/..., then it would change toAWSLogs/[ORGANIZATION_ID]/[OWNER_ID]/CloudTrail. - Click Save changes.
To enable trails for an organization, each AWS account must be configured individually with a CloudTrail Prefix set as AWSLogs/ORGANIZATION_ID. To do this,
- Log in to the to the Tanzu CloudHealth platform in a separate browser window.
- Navigate to Setup > AWS and click the edit icon next to the Account Name.
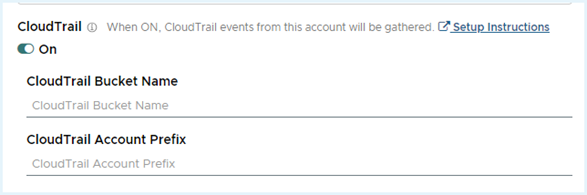
- In the Edit account page, expand the Optional section, and click the CloudTrail toggle switch on.
- Add CloudTrail Bucket Name.
- Set the CloudTrail Account Prefix field as
AWSLogs/ORGANIZATION_ID. - Click Save Account.
Note: You must set the CloudTrail Bucket Name and Account Prefix fields for every account in your organization, without any leading or trailing characters. Failing to add a prefix to an account will result in the account showing a Warning status.
CloudTrail Setup for Additional AWS Accounts
Typically, CloudTrail is set up in AWS with multiple accounts feeding a single S3 CloudTrail bucket. You can think about the bucket as a file tree. Each account has a root location in the tree that is designated by the AWS Account ID. Beneath the root is the folder structure that contains the CloudTrail log files organized by date.
Tanzu CloudHealth uses the AWS Account ID to scan the known CloudTrail bucket for the events for each account.
- In the Tanzu CloudHealth platform, from the menu, select Setup > AWS Accounts and edit the additional AWS account for which CloudTrail logs are being collected.
- Expand the Optional section of the account setup form and switch on the CloudTrail option.
- Enter the CloudTrail Bucket Name. You do not need to update the IAM policy for accounts other than the ones where CloudTrail buckets are located.
- Click Save Account.
Tanzu CloudHealth validates the account and starts collecting data. If there are issues, a warning message appears. CloudTrail events begin appearing in the Tanzu CloudHealth platform after about 15-30 minutes. More stable accounts tend to have few events.
Note: Tanzu CloudHealth collects all events from 12:00 GMT on the day when the account is configured.
Configuring a AWS Payer Account with CloudFormation
Step 1 - Enable Cost and Usage Report
Follow the instructions in the section above on Enable Cost and Usage Report to enable reports.
Step 2 - Set Up Read-Only IAM Role using CloudFormation
Tanzu CloudHealth leverages AWS CloudFormation to deploy the necessary resources that provide Tanzu CloudHealth with the appropriate IAM permissions inside your AWS environment. Template and stack are two important components of CloudFormation. A template is a simple JSON text file where you describe all your AWS resources, and stacks are single units that manage resources defined within the template.
Follow these steps to create IAM role and permissions via CloudFormation:
Deploying CloudFormation Stacks in the AWS Payer Account
Prerequisite
- AWS user needs sufficient privileges to deploy a CloudFormation template that creates IAM resources.
- Tanzu CloudHealth requires Cost and Usage setup inside your AWS console.
- Tanzu CloudHealth tenancy external ID. To get this ID, go to Tanzu CloudHealth > Setup > Accounts > AWS. Copy the external ID from the AWS account configuration page and paste it into a text document.
- Download the following CloudFormation templates to provide Tanzu CloudHealth access to your AWS account and billing bucket. Run the following templates in your AWS account via CloudFormation as either a Stack for your payer account and/or StackSet for your linked accounts.
- Tanzu CloudHealth AWS Configuration Template - Required to create a role for Tanzu CloudHealth and provides read-only access to the AWS services that Tanzu CloudHealth supports.
- Bucket Permission Policy Template – Required to get access to S3 buckets that contain your AWS Cost and Usage reports, and any optional bucket where you wish to upload the Tanzu CloudHealth reports.
- Tanzu CloudHealth AWS Automated Actions Template (Optional) - Provides Tanzu CloudHealth with the necessary permissions to take action inside your AWS environment. Note that you can deploy this automated access template as a stack to targeted accounts as well.
Deploying CloudHealth-AWS Configuration Template
Creates a Tanzu CloudHealth role and read-only policy for AWS services that Tanzu CloudHealth supports.
- Log into your AWS payer account.
- Go to Services > Management & Governance > CloudFormation and select Create Stack - With new resources (standard).
- In the Specify template section, select Upload a template file and click Choose file.
- Upload the CloudHealth-AWS-Configuration-Template and click Next.
Note: If you have added the template to the S3 bucket, you can provide the Object URL of the S3 bucket containing the template. - On the next page, enter a unique Stack Name.
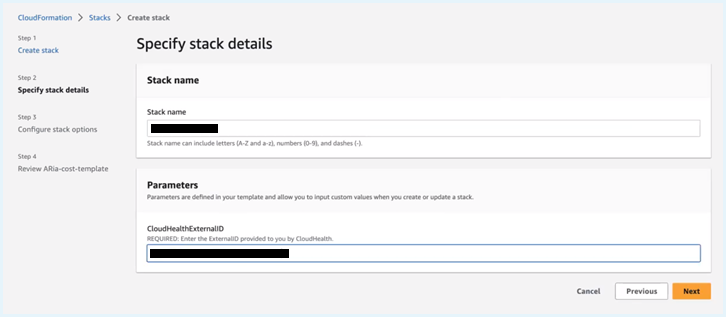
- In the Parameters section, enter the Tanzu CloudHealth External ID- the 30-digit number you copied into the text document. Click Next.
- Configure stack options if required (e.g., apply Key Value pair). This is an optional step. Click Next.
- Review the stack details, and in the Capabilities section, click I acknowledge that AWS CloudFormation might create IAM resources with custom names.
- Click Submit.
- Verify that the newly created stack reaches a Create_Complete status. This process should take a few minutes.
- Open the newly created stack, and from the Outputs tab, copy the RoleARN number into the text document.
Deploying AWS Bucket Access Policy Template
Deploying the CloudHealth-AWS-Bucket-Access-Template as a stack attaches a supplemental policy to the IAM role that you created in the previous step by using the CloudHealth-AWS-Configuration-Template.
- In the AWS Console, go to Services > Management & Governance > CloudFormation and select Create Stack - With new resources (standard).
- In the Specify template section, select Upload a template file and click Choose file.
- Upload the CloudHealth-AWS-Bucket-Access-Template and click Next.
. Note: If you have added the template to the S3 bucket, you can provide the Object URL of the S3 bucket containing the template. - On the next page, enter a unique Stack Name.
- In the Parameters section, enter the CURBucketName- the S3 bucket name where you have saved the CUR files and CURBucket path. (Refer to Create S3 bucket)
- Click Next.
- Configure stack options if required (e.g., apply Key Value pair). This is an optional step. Click Next.
- Review the stack details, and in the Capabilities section, click I acknowledge that AWS CloudFormation might create IAM resources with custom names.
- Click Submit.
- Verify that the newly created stack reaches a Create_Complete status. This process should take a few minutes.

- Open the newly created stack, and from the Outputs tab, copy the S3 bucket name and path into the text document.
At this point, you have created two Stacks in your AWS account which created a Tanzu CloudHealth IAM role, permissions policy, and an additional policy to access your CUR data from the S3 bucket.
Create StackSet to Access All Your Organizational Accounts
To create the same resource set up in each linked account under your organization account, you need to run the template as a StackSet. You will use the same CloudHealth-AWS-Configuration-Template you used while creating the stack in the previous step. Using this template as StackSet deploys IAM resources that give the Tanzu CloudHealth platform read-only access to all the Tanzu CloudHealth supported services.
Note: The StackSet, by default, is configured to automatically deploy resources to all linked AWS accounts in your organization.
- In the AWS CloudFormation console, select StackSets from the left navigation pane.
- Click Create StackSet.
- On the Choose a template page, continue with the pre-selected options in the Permissions and Prerequisite - Prepare template section.
- Upload the CloudHealth-AWS-Bucket-Access-Template and click Next.
Note: If you have added the template to the S3 bucket, you can provide the Object URL of the S3 bucket containing the template. - On the Specify StackSet details page, enter a StackSet name and description.

- In the Parameters section, enter the CloudHealthExternalID - the 30-digit number you copied into the text document. Click Next.
- Optionally, on the Configure StackSet options page, apply a Key-Value pair via Tags, and click Next.
- On the Set deployment options page, specify only one region of your choice (for example, us-east-1).
Note that in the future, if you add an account to your organization, the StackSet will automatically deploy the Tanzu CloudHealth permissions to the new account. Similarly, if you remove an account from your organization, the StackSet automatically deletes the Tanzu CloudHealth permissions from the account. However, you can change this default behavior using the Auto Deployment options.
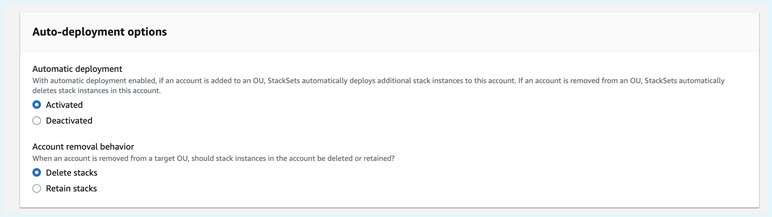
- In the Deployment options,
- For Maximum concurrent accounts, specify the maximum number of accounts in which the AWS CloudFormation can deploy your stack simultaneously.
- For Failure tolerance, specify the maximum number of stack deployment failures that can occur per region. Beyond the set threshold, CloudFormation automatically stops the stack deployment. Stack deployment to an account fails if the account is deprecated or suspended.

- Click Next.
- Review your selection, click I acknowledge that AWS CloudFormation might create IAM resources with custom names, and click Submit.
On the StackSet details page, you can check the progress and status of the creation of the stacks in your StackSet.
Configure AWS IAM Roles in the Tanzu CloudHealth platform
Once you set all the required permissions in the AWS console, you need to configure the permissions in the Tanzu CloudHealth platform.
- In the Tanzu CloudHealth platform, return to your AWS payer account you copied the external ID from (Navigate to Setup > Accounts > AWS).
- Enter the Role ARN you copied from the CloudFormation stack created in your payer account by deploying CloudHealth-AWS Configuration template.
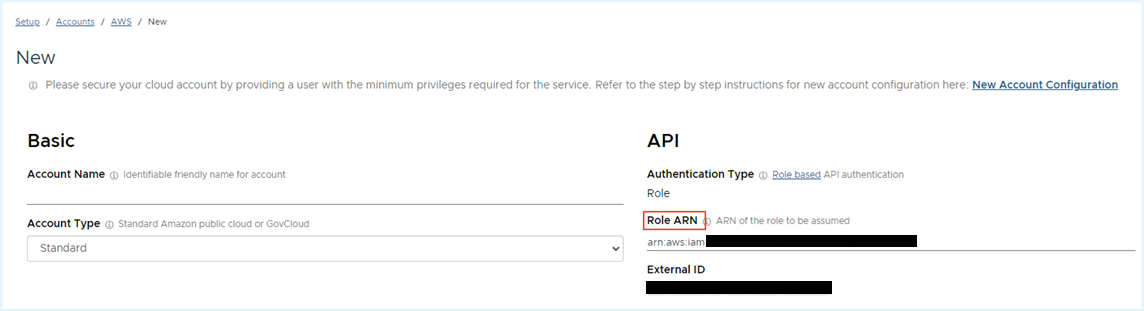
- In the Cost and Usage Report section, add the S3 Bucket Name and Report path you copied after deploying the AWS Bucket Access Policy Template.
- By default, Tanzu CloudHealth validates the read-only IAM policy with the us-east-1 AWS region. If you do not have access to the us-east-1 region, you must select a different region for validation. Under Optional, select the desired region from the Primary AWS Region Override dropdown.
- If you are using the Automated CloudFormation template, select the Automation dropdown to open the list of automation permissions. For each service you included as automated in your saved copy of the template, switch the permission to On.

- If you do not manually switch on a service’s permission, Tanzu CloudHealth won’t be able to automate that service even if you included that service in the Automated CloudFormation template.
- Click Save Account.
Note:
- After the payer account is configured, Tanzu CloudHealth processes the billing artifact with your AWS cost and usage data. This process usually takes a day. Once it’s complete, Tanzu CloudHealth derives all the linked accounts.
- You can manually add Role ARN for each linked account in the Tanzu CloudHealth platform or you can use the Enable AWS Account API to update all linked accounts.
Configuring a Linked AWS Account
Set up Tanzu CloudHealth for gathering information from an account linked to a consolidated billing account. Note that, an account can only ever be linked to one consolidated bill at any time.
Step 1 - Set Up Read-Only IAM Role for Linked Account
Create a read-only IAM role within the AWS Console along with read-only access policy to all AWS services Tanzu CloudHealth supports. Then add these credentials in the Tanzu CloudHealth platform. You can set up the IAM permissions through one of the following configurations:
- Option 1 - Via CloudFormation template
- Option 2 - Via IAM service
Option 1 - Create IAM Permissions via CloudFormation
Tanzu CloudHealth leverages AWS CloudFormation to deploy the necessary resources that provide Tanzu CloudHealth with the appropriate IAM permissions inside your AWS environment. Template and stack are two important components of CloudFormation. A template is a simple JSON text file where you describe all your AWS resources, and stacks are single units that manage resources defined within the template.
Follow these steps to create IAM role and permissions via CloudFormation:
Deploy CloudFormation Stacks in the AWS Payer Account
Prerequisite
- AWS user needs sufficient privileges to deploy a CloudFormation template that creates IAM resources.
- Tanzu CloudHealth requires Cost and Usage setup inside your AWS console.
- Tanzu CloudHealth tenancy external ID. To get this ID, go to Tanzu CloudHealth > Setup > Accounts > AWS. Copy the external ID from the AWS account configuration page and paste it into a text document.
- Download the following CloudFormation templates to provide Tanzu CloudHealth access to your AWS account and billing bucket. Run the following templates in your AWS account via CloudFormation as either a Stack for your payer account and/or StackSet for your linked accounts.
- Tanzu CloudHealth AWS Configuration Template - Required to create a role for Tanzu CloudHealth and provides read-only access to the AWS services that Tanzu CloudHealth supports.
- Bucket Permission Policy Template – Required to get access to S3 buckets that contain your AWS Cost and Usage reports, and any optional bucket where you wish to upload the Tanzu CloudHealth reports.
- Tanzu CloudHealth AWS Automated Actions Template (Optional) - Provides Tanzu CloudHealth with the necessary permissions to take action inside your AWS environment. Note that you can deploy this automated access template as a stack to targeted accounts as well.
Deploying CloudHealth-AWS Configuration Template
Creates a Tanzu CloudHealth role and read-only policy for AWS services that Tanzu CloudHealth supports.
- Log into your AWS payer account.
- Go to Services > Management & Governance > CloudFormation and select Create Stack - With new resources (standard).
- In the Specify template section, select Upload a template file and click Choose file.
- Upload the CloudHealth-AWS-Configuration-Template and click Next.
Note: If you have added the template to the S3 bucket, you can provide the Object URL of the S3 bucket containing the template. - On the next page, enter a unique Stack Name.

- In the Parameters section, enter the Tanzu CloudHealth External ID- the 30-digit number you copied into the text document. Click Next.
- Configure stack options if required (e.g., apply Key Value pair). This is an optional step. Click Next.
- Review the stack details, and in the Capabilities section, click I acknowledge that AWS CloudFormation might create IAM resources with custom names.
- Click Submit.
- Verify that the newly created stack reaches a Create_Complete status. This process should take a few minutes.
- Open the newly created stack, and from the Outputs tab, copy the RoleARN number into the text document.
Deploying AWS Bucket Access Policy Template
Deploying the CloudHealth-AWS-Bucket-Access-Template as a stack attaches a supplemental policy to the IAM role that you created in the previous step by using the CloudHealth-AWS-Configuration-Template.
- In the AWS Console, go to Services > Management & Governance > CloudFormation and select Create Stack - With new resources (standard).
- In the Specify template section, select Upload a template file and click Choose file.
- Upload the CloudHealth-AWS-Bucket-Access-Template and click Next.
Note: If you have added the template to the S3 bucket, you can provide the Object URL of the S3 bucket containing the template. - On the next page, enter a unique Stack Name.
- In the Parameters section, enter the CURBucketName- the S3 bucket name where you have saved the CUR files and CURBucket path.
- Click Next.
- Configure stack options if required (e.g., apply Key Value pair). This is an optional step. Click Next.
- Review the stack details, and in the Capabilities section, click I acknowledge that AWS CloudFormation might create IAM resources with custom names.
- Click Submit.
- Verify that the newly created stack reaches a Create_Complete status. This process should take a few minutes.

- Open the newly created stack, and from the Outputs tab, copy the S3 bucket name and path into the text document.
At this point, you have created two Stacks in your AWS account which created a Tanzu CloudHealth IAM role, permissions policy, and an additional policy to access your CUR data from the S3 bucket.
Create StackSet to Access All Your Organizational Accounts
To create the same resource set up in each linked account under your organization account, you need to run the template as a StackSet. You will use the same CloudHealth-AWS-Configuration-Template you used while creating the stack in the previous step. Using this template as StackSet deploys IAM resources that give the Tanzu CloudHealth platform read-only access to all the Tanzu CloudHealth supported services.
Note: The StackSet, by default, is configured to automatically deploy resources to all linked AWS accounts in your organization.
- In the AWS CloudFormation console, select StackSets from the left navigation pane.
- Click Create StackSet.
- On the Choose a template page, continue with the pre-selected options in the Permissions and Prerequisite - Prepare template section.
- Upload the CloudHealth-AWS-Bucket-Access-Template and click Next.
Note: If you have added the template to the S3 bucket, you can provide the Object URL of the S3 bucket containing the template. - On the Specify StackSet details page, enter a StackSet name and description.

- In the Parameters section, enter the CloudHealthExternalID - the 30-digit number you copied into the text document. Click Next.
- Optionally, on the Configure StackSet options page, apply a Key-Value pair via Tags, and click Next.
- On the Set deployment options page, specify only one region of your choice (for example, us-east-1).
Note that in the future, if you add an account to your organization, the StackSet will automatically deploy the Tanzu CloudHealth permissions to the new account. Similarly, if you remove an account from your organization, the StackSet automatically deletes the Tanzu CloudHealth permissions from the account. However, you can change this default behavior using the Auto Deployment options.

- In the Deployment options,
- For Maximum concurrent accounts, specify the maximum number of accounts in which the AWS CloudFormation can deploy your stack simultaneously.
- For Failure tolerance, specify the maximum number of stack deployment failures that can occur per region. Beyond the set threshold, CloudFormation automatically stops the stack deployment. Stack deployment to an account fails if the account is deprecated or suspended.

- Click Next.
- Review your selection, click I acknowledge that AWS CloudFormation might create IAM resources with custom names, and click Submit.
On the StackSet details page, you can check the progress and status of the creation of the stacks in your StackSet.
Configure AWS IAM Roles in the Tanzu CloudHealth platform
Once you set all the required permissions in the AWS console, you need to configure the permissions in the Tanzu CloudHealth platform.
- In the Tanzu CloudHealth platform, return to your AWS payer account you copied the external ID from (Navigate to Setup > Accounts > AWS).
- Enter the Role ARN you copied from the CloudFormation stack created in your payer account by deploying CloudHealth-AWS Configuration template.

- In the Cost and Usage Report section, add the S3 Bucket Name and Report path you copied after deploying the AWS Bucket Access Policy Template.
- By default, Tanzu CloudHealth validates the read-only IAM policy with the us-east-1 AWS region. If you do not have access to the us-east-1 region, you must select a different region for validation. Under Optional, select the desired region from the Primary AWS Region Override dropdown.

- If you are using the Automated CloudFormation template, select the Automation dropdown to open the list of automation permissions. For each service you included as automated in your saved copy of the template, switch the permission to On.
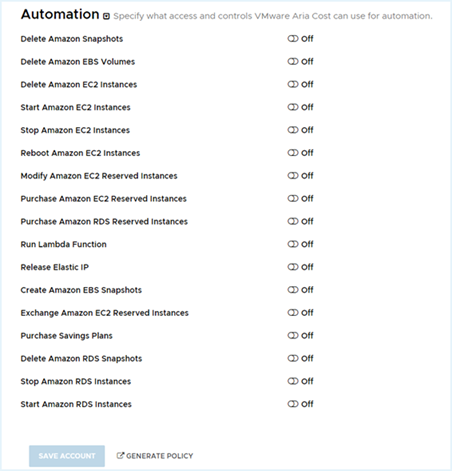
- If you do not manually switch on a service’s permission, Tanzu CloudHealth won’t be able to automate that service even if you included that service in the Automated CloudFormation template.
- Click Save Account.
Note:
- After the payer account is configured, Tanzu CloudHealth processes the billing artifact with your AWS cost and usage data. This process usually takes a day. Once it’s complete, Tanzu CloudHealth derives all the linked accounts.
- You can manually add Role ARN for each linked account in the Tanzu CloudHealth platform or you can use the Enable AWS Account API to update all linked accounts.
Option 2 - Create IAM Permissions via IAM Role
Note: Setting up a read-only IAM Role is recommended over setting up a read-only IAM User, while both approaches are supported in the Tanzu CloudHealth platform.
Create a read-only IAM role within the AWS Console for the target account. Then add these credentials in the Tanzu CloudHealth platform.
The default AWS Read-Only policy provides read access to data, such as S3 objects, and is therefore discouraged from being used.
- Login to the AWS Console for the targeted account as a user who has permission to create an IAM role.
- Navigate to Services > IAM. From the left menu, select Policies and click Create Policy.
- Switch to the JSON tab.
- In a separate browser window, login to the Tanzu CloudHealth platform. From the menu, select Setup > Accounts > AWS. Then click Add Account.
- The new account setup form, name the account and add a description so that you can identify it later in the Tanzu CloudHealth platform.
- Click Generate Policy. The bucket name is included in the resulting policy. The IAM Access Policy dialog box appears. Click Select All and copy the contents to the clipboard.
- Return to the AWS Console and paste the policy in the JSON tab. Then click Review Policy.
- Name the policy (e.g., CHTPolicy), provide a description, and click Create policy.
- In the AWS Console, from the left menu, select Roles and click Create role.
- Name the role (e.g., Tanzu CloudHealth) and click Next.
- On the Create role > Trust page, select Another AWS Account.
- Enter the following information in the setup form.
- Account ID: Enter
454464851268, which is the ID of the secure Tanzu CloudHealth-managed account. - Select option to require an External ID. Copy the External ID that Tanzu CloudHealth generated for you in the Account Setup form. This ID is unique for each Tanzu CloudHealth customer, so you can reuse it across all your accounts. Paste this ID in the External ID field in the AWS Console.
- Leave the checkbox for Require MFA cleared because the IAM role will be used to provide programmatic access to the Tanzu CloudHealth platform. Then click Next.
- On the Create role > Permissions page, set the Filter field to Customer managed and choose the Tanzu CloudHealth policy you created. Click Next.
- On the Create role > Review page, enter a name and description for the role. Click Create role. From the Role Summary page, copy the value of Role ARN to the clipboard.
- Return to the AWS Account Setup page in the Tanzu CloudHealth platform. In the API section paste the Role ARN value.
- By default, Tanzu CloudHealth validates the read-only IAM policy with the us-east-1 AWS region. If you do not have access to the us-east-1 region, you must select a different region for validation. Under Optional, select the desired region from the Primary AWS Region Override dropdown.
- Click Save Account. Tanzu CloudHealth validates your account and begins collecting data. If there are issues with any information you provided, an error message appears.
Step 2 - Enable AWS Console Integration (Optional)
View asset details in the AWS Console through links from the Tanzu CloudHealth Platform In the Tanzu CloudHealth platform, instances have links that allow you to view them in the AWS Console.

These links are set up by enabling AWS Console integration from the Tanzu CloudHealth platform.
- Navigate to select Setup > Accounts > AWS.
- From the list of AWS accounts, edit the account for which you want to add AWS Console integration.
- In a separate browser window, login to the AWS Console.
- From the menu, select Security, Identity, & Compliance > IAM.
- From IAM Dashboard > AWS Account, copy the IAM User Sign-In URL into the clipboard.
- Return to the Tanzu CloudHealth platform, expand the Optional section of the account setup form. Paste the URL in the Signin URL field.
- Click Save Account to enable AWS Console integration.
Configuring a GovCloud Account
To configure a GovCloud account, you will need to create two accounts in both the AWS management console and Tanzu CloudHealth.
Create Accounts in AWS
GovCloud accounts must be associated with either a Consolidated or Standalone account. Therefore, you need to create two accounts within AWS.
- Configure a Commercial account to receive the Detailed Billing Record/Cost and Usage Report. This configuration will be like any normal AWS account setup but should ideally be left empty and not used for any other purpose besides supporting GovClod Assets accounts. The commercial account will act as a parent account to the actual GovCloud Asset account.
- Configure an Assets account that contains the infrastructure of your organization. This is the actual GovCloud account that will reside within any of the special GovCloud AWS regions. This account holds the infrastructure, but reporting cannot be pulled directly from these accounts. Therefore, a separate Commercial account is required. For more details, see AWS GovCloud (US) Billing and Payment.
Create Accounts in Tanzu CloudHealth
You need to create two accounts within Tanzu CloudHealth.
- A commercial account that will be either Standalone or Consolidated - All billing and usage will appear as though it originated from the configured Commercial GovCloud account in AWS. This account should be set up in Tanzu CloudHealth as a Standard account type.
- An empty account that will be linked to the commercial account. This empty account will hold the infrastructure and will be linked to the Assets AWS account. This account should be set up in Tanzu CloudHealth as a GovCloud account type.
If you are planning to have Tanzu CloudHealth monitor a GovCloud account that will be linked into a consolidated bill, follow these guidelines:
- Proactively set up an empty Amazon account for each GovCloud account.
- Associate the GovCloud account with the empty account.
- Link the empty account to your consolidated bill.
These steps enable the GovCloud activity to be reported within your consolidated billing records with a different account. Otherwise, activity is reported with the Account ID of the consolidated bill.
Complete the following steps to Set up a GovCloud Account in Tanzu CloudHealth:
Step 1- Configure a Commercial Account
A commercial account that will be either Standalone or Consolidated.
- Login to the Tanzu CloudHealth platform. From the menu, select Setup > Accounts > AWS. Then click Add Account.
- Add appropriate Account Name that is to be used for reporting or billing, and select Account Type as Standard. For the best security, the Authentication Type is selected as Role by default.
- Click Save Account.
Billing settings can potentially be populated but will most likely be blank as this account will generally be linked to a consolidated account.
Step 2 - Configure an Asset Account
This empty account will hold the infrastructure and will be linked to the Assets AWS account.
Create a GovCloud Account in the Tanzu CloudHealth platform
- Log in to the Tanzu CloudHealth platform and go to Setup > Accounts > AWS. Then click Add Account.
- Enter a friendly account name that you can identify later in the Tanzu CloudHealth platform. Select Account Type as GovCloud The Authentication Type is selected as User by default.
- Click Generate Policy.
- In the IAM Access Policy dialog box, click Select All and copy the policy contents to the clipboard. Later, you will need to paste the policy into the JSON tab in the AWS console. It is recommended not to use the default AWS Read-Only policy because it provides read access to data, such as S3 objects.
- Click Close.
Create an IAM Policy in AWS Console
- Log in to the AWS Console for the targeted account as a user who has permission to create an IAM user.
- Navigate to Services > IAM. From the left menu, select Policies and click Create Policy.
- Click the JSON tab and paste the IAM Access Policy you copied from the AWS account setup page in the Tanzu CloudHealth platform.
- Click Review Policy. Give it an appropriate Name and Description, and click Create Policy.
Add a Read-Only IAM User
If you are setting up a standard account, while both approaches are supported in the Tanzu CloudHealth platform, a read-only IAM Role is recommended over a read-only IAM User. For GovCloud accounts, only a read-only IAM user is supported.
- In the AWS Console, navigate to Services > IAM. From the left menu, select Users and click Add user.
- Enter a User name and select the Programmatic access checkbox. Click Next: Permissions.
- Click Attach existing policies directly, and select the policy that you just created.
- Click Next: Tags. Optionally, you can add key-value pairs to your IAM user.
- Click Next: Review. Review your changes and click Create user.
- Click the user name from the list and navigate to the Security credentials tab.
- Click Create access key, and click download .csv file to save the Access key and Secret key to a CSV file on your computer.
- Store the access key .csv file in a secure location. Once the dialog box closes, you will not be able to access the secret access key again.
- The newly created access key will be active by default.
- Click Close.
- Return to the AWS Account Setup page in the Tanzu CloudHealth platform where you are configuring the GovCloud account.
- Copy and paste the values of the Access Key and Secret Key from the .csv file that you stored previously. Leave the billing settings blank.
- Click Save Account.