STIG hardening for TKG Ubuntu hosts
By default, all Tanzu Kubernetes Grid (TKG) cluster nodes run Ubuntu v20.04. You can build Ubuntu 20.04 machine images for Tanzu Kubernetes Grid that are hardened to address STIG benchmarks. You can use the hardened image as a template for the management and workload cluster nodes that it creates.
To build a custom STIG hardened image, follow the steps in the Linux Custom Machine Images TKG documentation.
NoteUse the Ubuntu 20.04 STIG hardening Ansible playbook provided in the VMware dod-compliance-and-automation GitHub repository as a custom role in Build a Linux Image.
Ubuntu 20.04 STIG hardening results
The STIG hardening process for Ubuntu changes the security scans for TKG v2.1.1 cluster nodes. The following screen captures show the scan results for out-of-box TKG cluster notes and the scan results after hardening.
Scan results for hardened TKG v2.1 cluster nodes:
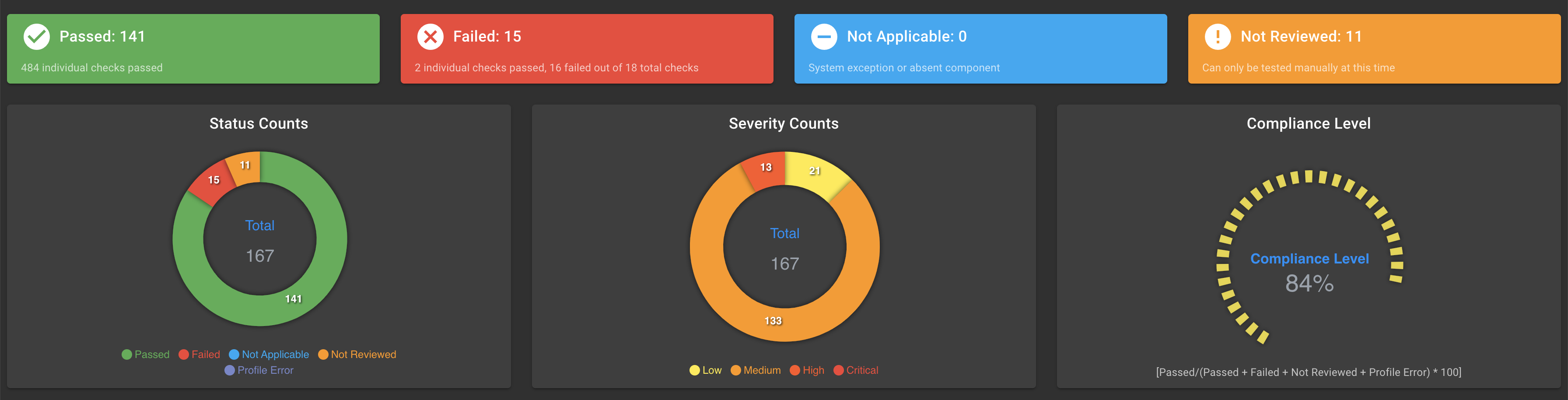
STIG results and exceptions for Ubuntu 20.04
Some Ubuntu processes/features are not hardened. The following table lists the hardening results and exceptions. The table also provides an explanation for the exception and a resolution.
| VID | Finding Title | Exception / Explanation |
|---|---|---|
| V-238197 | The Ubuntu operating system must enable the graphical user log in banner to display the Standard Mandatory DoD Notice and Consent Banner before granting local access to the system through a graphical user log in. | GUI not installed |
| V-238198 | The Ubuntu operating system must display the Standard Mandatory DoD Notice and Consent Banner before granting local access to the system through a graphical user log in. | GUI not installed |
| V-238199 | The Ubuntu operating system must retain a user’s session lock until that user reestablishes access using established identification and authentication procedures. | GUI not installed |
| V-238201 | The Ubuntu operating system must map the authenticated identity to the user or group account for PKI-based authentication. | Cluster VM do not use pam-pkcs11 |
| V-238208 | The Ubuntu operating system must require users to reauthenticate for privilege escalation or when changing roles. | <user> requires sudo to run cloud-init.ubuntu for AWS AMI |
| V-238229 | The Ubuntu operating system, for PKI-based authentication, must validate certificates by constructing a certification path (which includes status information) to an accepted trust anchor. | Cluster VM do not use pam-pkcs11 |
| V-238232 | The Ubuntu operating system must electronically verify PersonalIdentity Verification (PIV) credentials. | Cluster VM do not use pam-pkcs11 |
| V-238233 | The Ubuntu operating system for PKI-based authentication, must implement a local cache of the revocation data in case there is an issue with accessing revocation information through the network. | Cluster VM do not use pam-pkcs11 |
| V-238306 | The Ubuntu operating system audit event multiplexor must be configured to off-load audit logs onto a different system or storage media from the system being audited. | Site-specific control |
| V-238307 | The Ubuntu operating system must immediately notify the SA and ISSO (at a minimum) when allocated audit record storage volume reaches 75% of the repository maximum audit record storage capacity. | space_left setting cannot be determined at image build time |
| V-238321 | The Ubuntu operating system must have a crontab script running weekly to offload audit events of standalone systems. | Site-specific control |
| V-238328 | The Ubuntu operating system must be configured to prohibit or restrict the use of functions, ports, protocols, and/or services, as defined in the PPSM CAL and vulnerability assessments. | Network protection is provided by VPC for perimeter protection and iptables for container networks |
| V-238331 | The Ubuntu operating system must automatically remove or deactivate emergency accounts after 72 hours. | Manual verification |
| V-238332 | The Ubuntu operating system must set a sticky bit on all public directories to prevent unauthorized and unintended information transferred through shared system resources. | Directories failing the test are container directories. |
| V-238335 | Ubuntu operating systems handling data requiring data at rest protections must employ cryptographic mechanisms to prevent unauthorized disclosure and modification of the information at rest. | Encryption of data at rest is handled by the IaaS |
| V-238361 | The Ubuntu operating system must allow the use of a temporary password for system logons with an immediate change to a permanent password. | Manual verification |
| V-238362 | The Ubuntu operating system must be configured such that Pluggable Authentication Module (PAM) prohibits the use of cached authentications after one day. | Cluster VM do not use pam-pkcs11 |
| V-238364 | The Ubuntu operating system must only allow the use of DoD PKI-established certificate authorities for verification of the establishment of protected sessions. | Customer can use BYOI to remove existing CAs and add DoD CA to the image |
| V-238365 | Ubuntu operating system must implement cryptographic mechanisms to prevent unauthorized modification of all information at rest. | Encryption of data at rest is handled by the IaaS |
| V-238366 | Ubuntu operating system must implement cryptographic mechanisms to prevent unauthorized disclosure of all information at rest. | Encryption of data at rest is handled by the IaaS |
| V-238367 | The Ubuntu operating system must configure the uncomplicated firewall to rate-limit impacted network interfaces. | Status listings checks must be preformed manually |
| V-238379 | The Ubuntu operating system must deactivate the x86 Ctrl-Alt-Delete key sequence if a graphical user interface is installed. | GUI not installed |
| V-252704 | The Ubuntu operating system must deactivate all wireless network adapters. | Wireless networking is not used |