Tanzu Application Service 2.13 Compliance and Hardening
Tanzu Application Service Compliance and Hardening provides a recommended security baseline. It is your starting point for building and understanding the security posture of the environment on which you deploy Tanzu Application Service. It provides you the guidance for hardening Tanzu Application Service (TAS for VMs) to achieve an Authority to Operate (ATO).
TAS for VMs releases are continuously validated against the Defense Information Systems Agency Security Technical Implementation Guides (DISA STIG), Cybersecurity and Infrastructure Security Agency (CISA) and the National Security Agency (NSA) framework, and the National Institute of Standards and Technology (NIST) guidelines.
Disclaimer
Following the hardening guidance provided in this document may not be effective in all cases and could affect the functionality of your software and applications. It is your responsibility to test STIG settings and hardening guidelines to ensure that your application still functions properly while maintaining the security of the system.
Intended audience
The information provided in this document is intended for the Information System Security Officer/Manager (ISSO/ISSM) who is responsible for ensuring the implementation of security controls. The included artifacts allow the ISSO/ISSM to understand the vendor best practices that will enable their security plan and risk analysis for authorization decisions. Administrators can use the information to locate the hardened images and security updates.
Risk management framework
The Risk Management Framework (RMF) provides a process that integrates security, privacy, and cyber supply chain risk management activities into the system development life cycle. Based on the RMF, the following sections show the general workflow you would follow to reach ATO.
VMware supports the Risk Management Framework (RMF) process by providing artifacts and information to support the creation of your accreditation package. The following highlights the steps in the RMF process the artifacts support.
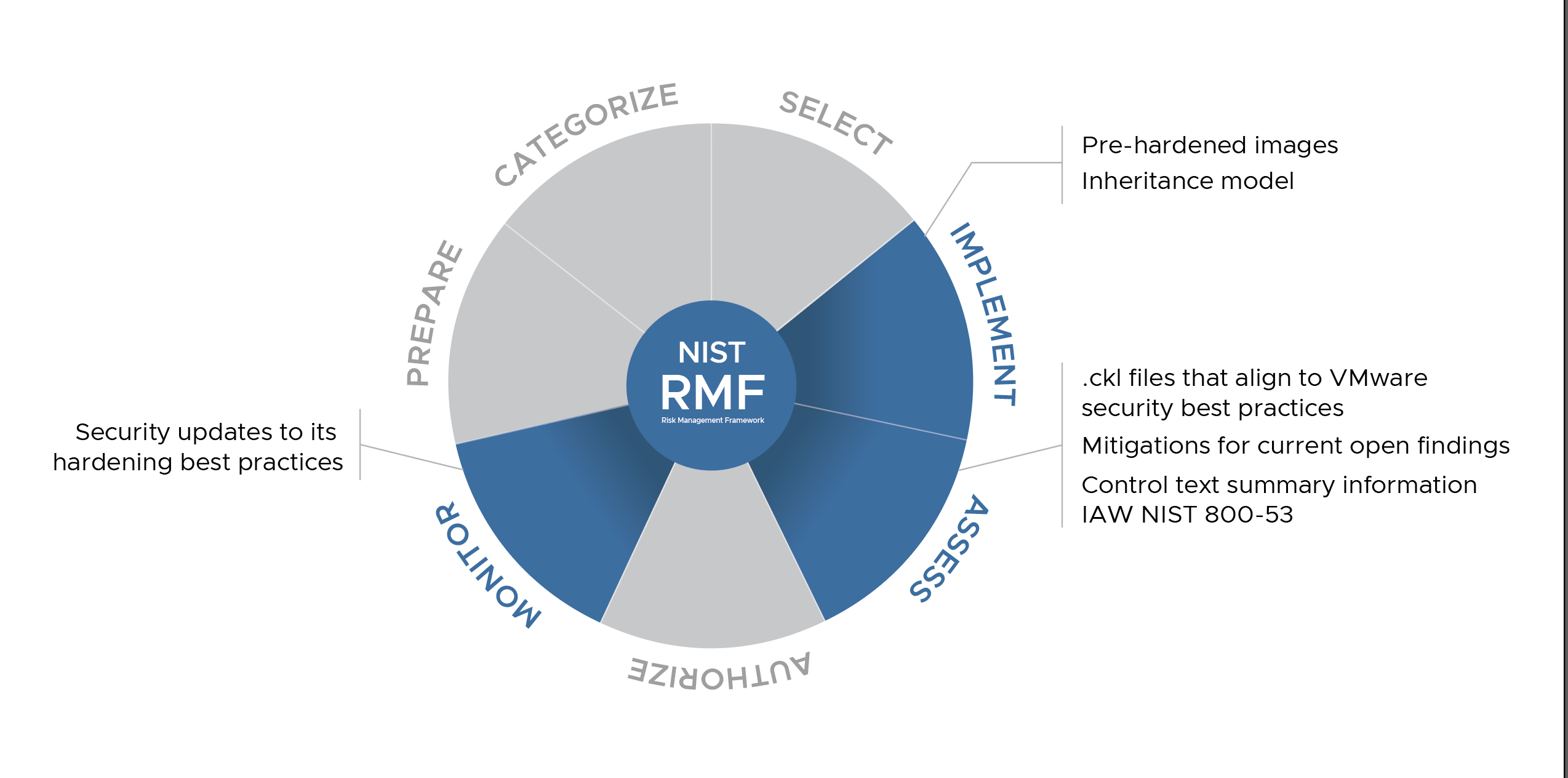
Implement
The following topics provide the steps you perform to harden your Tanzu Application Service (TAS for VMs) foundation. The STIG hardening documentation include the hardening results and exceptions. In addition, VMware provides TAS for VMs compliance artifacts that you can use as tools to achieve your compliance goals.
Assess
During the RMF Assess step, cybersecurity personnel can use the checklists (.ckl), mitigation and control text to fill out your accreditation package. Keep in mind that this data represents VMware best practices, and your individual implementation may differ. Verify all security settings in your production environment to support the functionality of your system. TAS for VMs is hardened to the following STIGs:
VMware provides Compliance Scanner for Tanzu that allows the operator to scan TAS for VMs against STIG and other Compliance benchmarks
Results of hardening TAS for VMs to VMware best practices
The following checklist files align to VMware security best practices:
Mitigation for current open findings
The following provide mitigation for current open findings:
Ports
For information about ports, see Ports, protocols, and services management(PPSM).
Extended Licensing support
For information on Ubuntu Xenial extended licensing support, contact VMware Tanzu Support Hub.
-
As of June 2021, Ubuntu Xenial stemcells are in Extended Security Maintenance (ESM). For more information, refer to the Ubuntu lifecycle and release cadence.
VMware has a commercial agreement with Canonical to continue providing secure and patched Xenial stemcells through April 2024, but only for Tanzu-related products.
VMware Tanzu only supports the stemcells available here: Stemcells (Ubuntu Xenial).
The Ubuntu Bionic stemcell is available here: Ubuntu Bionic (18.04).
Note: The Ubuntu Bionic stemcell is not supported by Tanzu-related products.
Monitor
VMware continuously monitors our products for security-relevant events and configuration changes that negatively affect security posture. For security updates, see the Tanzu Application Service release notes.