CIS Results and Exceptions
This topic shows default-level CIS (v1.6.1) scan results for Tanzu Kubernetes Grid (TKG) class-based workload clusters deployed by a standalone management cluster, and describes exception handling that can improve the scan results.
For standard processes to further harden TKG workload clusters, see STIG and NSA/CISA Hardening.
For CIS results and exceptions for plan-based (legacy) workload clusters, see Hardening Results in the TKG v2.2 documentation.
CIS Scan Results and Exceptions
CIS scan results for class-based workload clusters deployed without the additional Kubernetes or OS hardening described in Hardening Class-Based Workload Clusters:
Kubernetes Scan Results:
Control plane nodes:
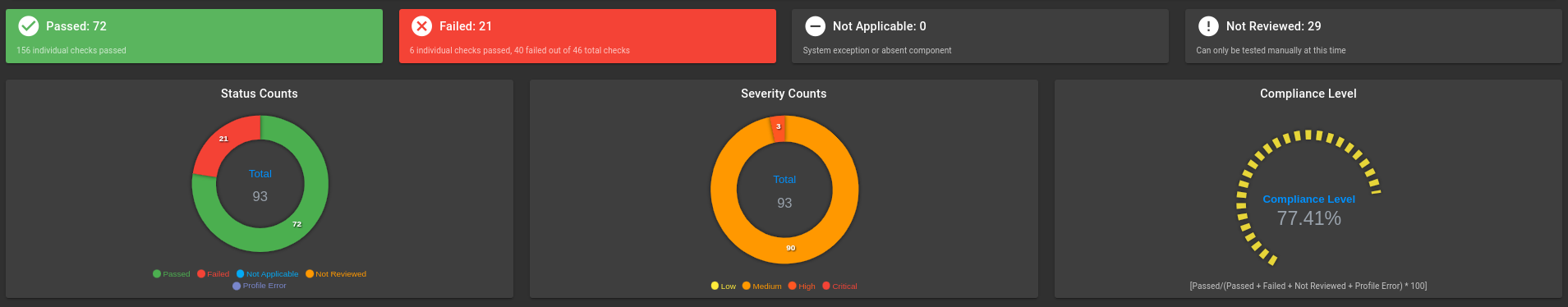
Worker nodes:
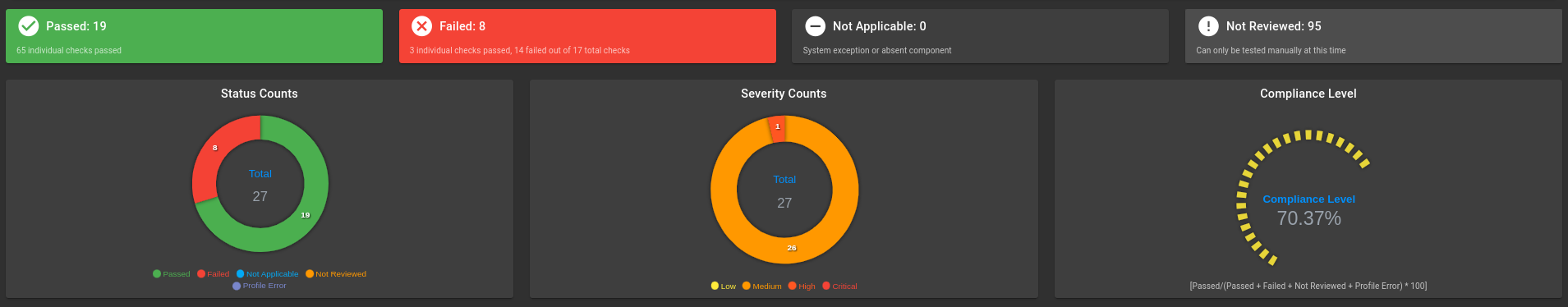
Ubuntu OS 20.04 Scan Results:
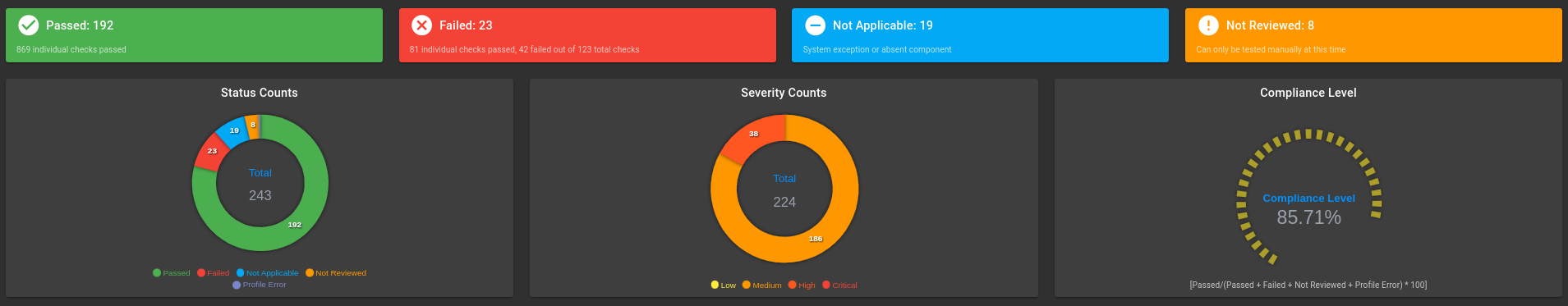
Default CIS Exceptions
CIS Exceptions for Ubuntu OS 20.04 in class-based TKG clusters without additional Kubernetes or OS hardening:
| CIS ID | CIS Description | Reason | Workaround |
|---|---|---|---|
| C-1.1.17 | Ensure separate partition exists for /home | Partition /home not mounted separated, only one root partition is created. | Need to create the node and replace preseed of Ubuntu in image-builder |
| C-1.1.18 | Ensure /home partition includes the nodev option | Partition /home not mounted separated, only one root partition is created. | Need to create the node and replace preseed of Ubuntu in image-builder |
| C-1.4.4 | Ensure authentication required for single user mode | ClusterAPI VM does not set the password for root, customers must login via SSH with capv and sudo instead. | Not applicable |
| C-1.9 | Ensure updates, patches, and additional security software are | This requires a regular creation of the image, whereas in TKG, images are immutable and may live a long time. | Not Applicable |
| C-2.3 | Ensure nonessential services are removed or masked | Manual testing must be executed and analyzed. | Users must check with lsof -i -P -n | grep -v “(ESTABLISHED)” |
| C-3.2.2 | Ensure IP forwarding is disabled | IP Forwarding is required by Antrea and Kube-proxy | Not Applicable |
| C-3.5.1.1 | Ensure ufw is installed | Universal Firewall is not installed by default | Iptables is the being used instead and controls related to it are the compensating controls |
| C-3.5.1.2 | Ensure iptables-persistent is not installed with ufw | Universal Firewall is not installed by default | Iptables is the being used instead and controls related to it are the compensating controls |
| C-3.5.1.3 | Ensure ufw service is enabled | Universal Firewall is not installed by default | Iptables is the being used instead and controls related to it are the compensating controls |
| C-3.5.1.4 | Ensure ufw loopback traffic is configured | Universal Firewall is not installed by default | Iptables is the being used instead and controls related to it are the compensating controls |
| C-3.5.1.5 | Ensure ufw outbound connections are configured | Universal Firewall is not installed by default | Iptables is the being used instead and controls related to it are the compensating controls |
| C-3.5.1.6 | Ensure ufw firewall rules exist for all open ports | Universal Firewall is not installed by default | Iptables is the being used instead and controls related to it are the compensating controls |
| C-3.5.1.7 | Ensure ufw default deny firewall policy | Universal Firewall is not installed by default | Iptables is the being used instead and controls related to it are the compensating controls |
| C-3.5.2.1 | Ensure nftables is installed | Nftables is not install by default | Iptables is the being used instead and controls related to it are the compensating controls |
| C-3.5.2.10 | Ensure nftables rules are permanent | Nftables is not install by default | Iptables is the being used instead and controls related to it are the compensating controls |
| C-3.5.2.2 | Ensure ufw is uninstalled or disabled with nftables | Universal Firewall and nftables are not installed by default | Iptables is the being used instead and controls related to it are the compensating controls |
| C-3.5.2.3 | Ensure iptables are flushed with nftables | Nftables is not installed by default | Iptables is the being used instead and controls related to it are the compensating controls |
| C-3.5.2.4 | Ensure a nftables table exists | Nftables is not installed by default | Iptables is the being used instead and controls related to it are the compensating controls |
| C-3.5.2.5 | Ensure nftables base chains exist | Nftables is not installed by default | Iptables is the being used instead and controls related to it are the compensating controls |
| C-3.5.2.6 | Ensure nftables loopback traffic is configured | Nftables is not installed by default | Iptables is the being used instead and controls related to it are the compensating controls |
| C-3.5.2.7 | Ensure nftables outbound and established connections are configured | Nftables is not installed by default | Iptables is the being used instead and controls related to it are the compensating controls |
| C-3.5.2.8 | Ensure nftables default deny firewall policy | Nftables is not installed by default | Iptables is the being used instead and controls related to it are the compensating controls |
| C-3.5.2.9 | Ensure nftables service is enabled | Nftables is not installed by default | Iptables is the being used instead and controls related to it are the compensating controls |
| C-3.5.3.2.2 | Ensure iptables outbound and established connections are configured | Required when IPv4 DENY iptables rules exists | Not applicable |
| C-3.5.3.2.4 | Ensure iptables firewall rules exist for all open ports | Required when IPv4 DENY iptables rules exists | Not applicable |
| C-3.5.3.3.2 | Ensure ip6tables outbound and established connections are configured | Required when IPv6 DENY iptables rules exists | Not applicable |
| C-3.5.3.3.4 | Ensure ip6tables firewall rules exist for all open ports | Required when IPv6 DENY iptables rules exists | Not applicable |
| C-4.2.1.3 | Ensure logging is configured (Manual check) | Rsyslog is being applied | Check /etc/rsyslog.d/50-default.conf |
| C-4.2.1.5 | Ensure rsyslog is configured to send logs to a remote log host | Real-time logs offload is provided by the fluentbit package. | Install and configure fluentbit package |
| C-4.3 | Ensure logrotate is configured (Manual check) | Logrotate is enabled | Check /etc/logrotate.d/rsyslog |
| C-6.1.1 | Audit system file permissions (Manual) | This is a continuous check where customers can use dpkg to check for files integrity in the system | Use dpkg –verify <package_name> |
CIS Exceptions with OS Hardening
CIS exceptions for Ubuntu OS 20.04 in class-based TKG clusters with custom hardened VM images created by running Image Builder with the ansible_user_vars settings for CIS hardening described in Build a Linux Image:
| CIS ID | CIS Description | Reason | Workaround |
|---|---|---|---|
| C-1.3.1 | Ensure AIDE is installed | AIDE is not installed or enabled by default | Must recreate the node with install_aide=true enabled. |
| C-1.3.2 | Ensure filesystem integrity is regularly checked | AIDE is not installed or enabled by default | Must recreate the node with install_aide=true enabled |
| C-2.1.1.2 | Ensure systemd-timesyncd is configured | Chrony is being used by default | To use timesyncd recreate the node with install_chrony=false and install_systemd_timesyncd=true. |
| C-2.1.1.4 | Ensure ntp is configured | Chrony is being installed as an alternative. | Chrony is enabled as compensating control |
CIS Exceptions with Kubernetes Hardening
CIS exceptions for Kubernetes in class-based TKG clusters with Kubernetes hardened using the configuration file variable settings listed in CIS Hardening:
| CIS ID | CIS Description | Reason | Workaround |
|---|---|---|---|
| C-1.2.6 | Ensure that the –kubelet-certificate-authority argument is set as appropriate | Customer must provide a custom CA. | This can be resolved by setting APISERVER_EXTRA_ARGS. |
| C-1.2.12 | Ensure that the admission control plugin AlwaysPullImages is set | This can be resolved by setting SECURITY_IMAGE_POLICY_PULL_ALWAYS (vSphere only) or APISERVER_EXTRA_ARGS. Follow the Admission Controller instructions. | |
| C-1.2.27 | Ensure that the –service-account-lookup argument is set to true | This can be resolved by setting APISERVER_EXTRA_ARGS. | |
| C-1.2.33 | Ensure that the –encryption-provider-config argument is set as appropriate | Customer must enable encryption at rest. | This can be resolved by setting APISERVER_EXTRA_ARGS. Follow the Encryption as rest instructions. |
| C-1.3.1 | Ensure that the –terminated-pod-gc-threshold argument is set as appropriate | This can be resolved by setting KUBE_CONTROLLER_MANAGER_EXTRA_ARGS. | |
| C-1.3.6 | Ensure that the RotateKubeletServerCertificate argument is set to true. | This can be resolved by setting KUBE_CONTROLLER_MANAGER_EXTRA_ARGS. | |
| C-4.2.3 | Ensure that the –client-ca-file argument is set as appropriate | This can be resolved by setting WORKER_KUBELET_EXTRA_ARGS. | |
| C-4.2.6 | Ensure that the –protect-kernel-defaults argument is set to true | This can be resolved by setting WORKER_KUBELET_EXTRA_ARGS. | |
| C-4.2.10 | Same as CNTR-K8-001470 in STIG Results and Exceptions |