STIG Results and Exceptions
This topic shows default-level STIG (V1R8) scan results for Tanzu Kubernetes Grid (TKG) workload clusters deployed by a standalone management cluster, and describes exception handling that can improve the scan results.
For standard processes to further harden TKG workload clusters, see STIG and NSA/CISA Hardening.
Hardening Class-Based Workload Clusters
STIG scan results for class-based workload clusters deployed without the additional Kubernetes or OS hardening described in Hardening Class-Based Workload Clusters.
Default Photon OS 5 STIG Exceptions
Photon OS 5 Scan Results:
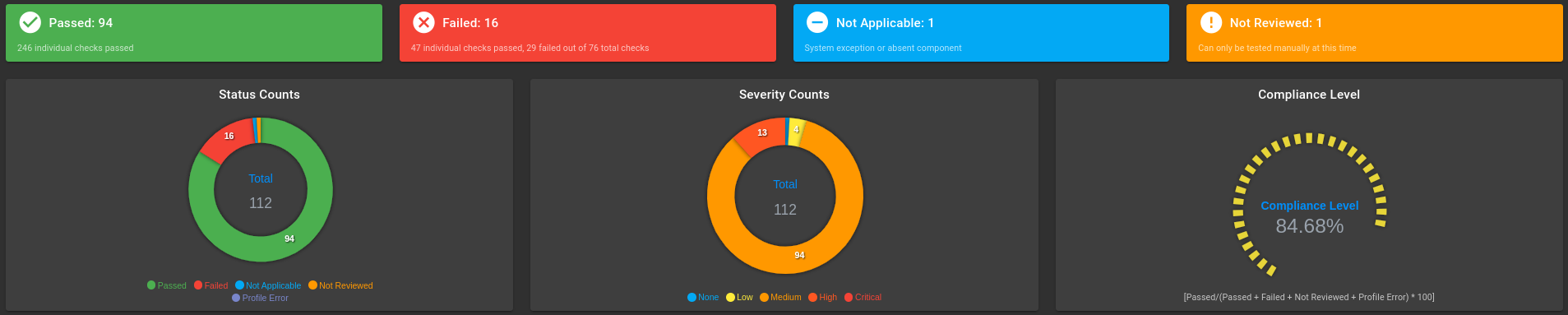
STIG Exceptions documentation and compensating controls for Photon OS 5 in class-based TKG clusters:
| STIG ID | Description | Reason | Workaround |
|---|---|---|---|
| PHTN-50-000005 | The Photon operating system must display the Standard Mandatory DOD Notice and Consent Banner before granting local or remote access to the system. | Not applicable | Enable with run_sshd_banner and run_etc_issue_dod options |
| PHTN-50-000013 | The Photon operating system must have the OpenSSL FIPS provider installed to protect the confidentiality of remote access sessions. | Photon FIPS is not enabled by default. | Enable with run_openssl_fips_install and run_openssl_fips options |
| PHTN-50-000046 | The Photon operating system must require authentication upon booting into single-user and maintenance modes. | Not recommended | Enable with run_grub_boot_password option |
| PHTN-50-000111 | The Photon operating system must off-load audit records onto a different system or media from the system being audited. | Real-time logs offload is provided by the fluentbit package. | Install and configure fluentbit package |
| PHTN-50-000121 | The Photon operating system must be configured to synchronize with an authoritative DOD time source. | NTP servers must be configured separately | Follow the instructions on this KB article |
| PHTN-50-000182 | The Photon operating system must implement NIST FIPS-validated cryptography for the following: to provision digital signatures, to generate cryptographic hashes, and to protect unclassified information requiring confidentiality and cryptographic protection in accordance with applicable federal laws, Executive Orders, directives, policies, regulations, and standards. | Photon FIPS is not enabled by default. | Enable with run_fips_boot_enable option |
| PHTN-50-000231 | The Photon operating system must not perform IPv4 packet forwarding. | Not applicable | IPv4 forwarding is required for TKG components |
| PHTN-50-000237 | The Photon operating system must configure AIDE to detect changes to baseline configurations. | AIDE is not enabled by default | Enable with run_aide_config option |
Default Ubuntu 2x.04 STIG Exceptions
Ubuntu OS 2x.04 Scan Results:
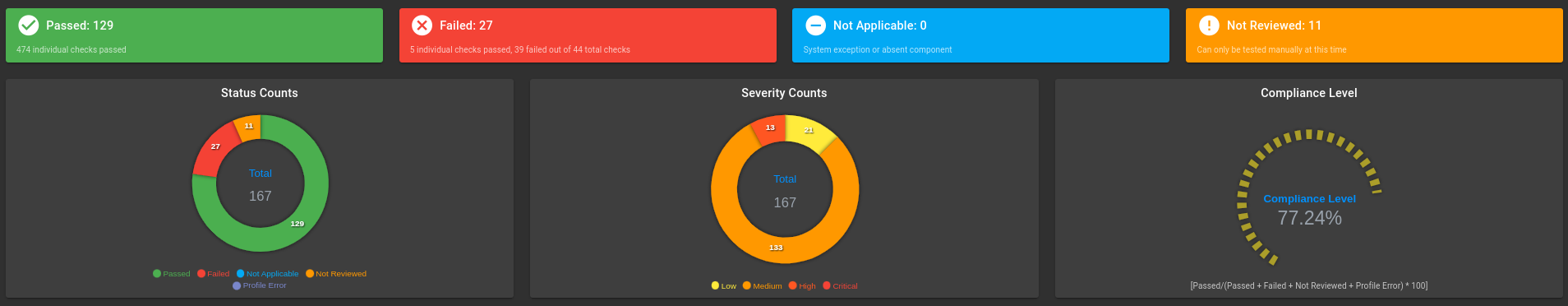
STIG Exceptions documentation and compensating controls for Ubuntu OS 2x.04 in class-based TKG clusters:
| STIG ID | STIG Description | Reason | Workaround | |
|---|---|---|---|---|
| V-238197 | The Ubuntu operating system must enable the graphical user logon banner to display the Standard Mandatory DoD Notice and Consent Banner before granting local access to the system via a graphical user logon. | GUI is NOT installed on TKG | Not applicable | |
| V-238198 | The Ubuntu operating system must display the Standard Mandatory DoD Notice and Consent Banner before granting local access to the system via a graphical user logon. | GUI is NOT installed on TKG | Not applicable | |
| V-238199 | The Ubuntu operating system must retain a user’s session lock until that user reestablishes access using established identification and authentication procedures. | GUI is NOT installed on TKG | Not applicable | |
| V-238201 | The Ubuntu operating system must map the authenticated identity to the user or group account for PKI-based authentication. | ClusterAPI VM does not support pam-pkcs11 for authentication | Not applicable | |
| V-238229 | The Ubuntu operating system, for PKI-based authentication, must validate certificates by constructing a certification path | ClusterAPI VM does not support pam-pkcs11 for authentication | Not applicable | |
| V-238232 | The Ubuntu operating system must electronically verify Personal Identity Verification (PIV) credentials. | ClusterAPI VM does not support pam-pkcs11 for authentication | Not applicable | |
| V-238233 | The Ubuntu operating system for PKI-based authentication, must implement a local cache of revocation data in case of the inability to access revocation information via the network. | ClusterAPI VM does not support pam-pkcs11 for authentication | Not applicable | |
| V-238306 | The Ubuntu operating system audit event multiplexor must be configured to off-load audit logs onto a different system or storage media from the system being audited. | Real-time logs offload is provided by the fluentbit package. | Install and configure fluentbit package | |
| V-238307 | The Ubuntu operating system must immediately notify the SA and ISSO (at a minimum) when allocated audit record storage volume reaches 75% of the repository maximum audit record storage capacity. | TKG does not support remote email integration by default | Install prometheus and configure prometheus alerting | |
| V-238321 | The Ubuntu operating system must have a crontab script running weekly to offload audit events of standalone systems. | Real-time logs offload is provided by the fluentbit package. | Install and configure fluentbit package | |
| V-238331 | The Ubuntu operating system must automatically expire temporary accounts within 72 hours. | Emergency accounts are not supported and should not exist on TKG since the box is immutable. Capv is an infrequently used account. | Not applicable | |
| V-238335 | Ubuntu operating systems handling data requiring “data at rest” protections must employ cryptographic mechanisms to prevent unauthorized disclosure and modification of the information at rest. | ClusterAPI VM does not support disk encryption | FS must encrypted on VSAN | |
| V-238336 | The Ubuntu operating system must deploy Endpoint Security for Linux Threat Prevention (ENSLTP). | TKG does not support the installation of third party licensed McAffee software | Not applicable | |
| V-238356 | The Ubuntu operating system must, for networked systems, compare internal information system clocks at least every 24 hours with a server which is synchronized to one of the redundant United States Naval Observatory (USNO) time servers, or a time server designated for the appropriate DoD network (NIPRNet/SIPRNet), and/or the Global Positioning System (GPS). | NTP servers must be configured separately | Follow the instructions on this KB article | |
| V-238361 | The Ubuntu operating system must allow the use of a temporary password for system logons with an immediate change to a permanent password. | Password is not supported on TKG, access is made via SSH and keys installed via CAPI. | Not applicable | |
| V-238362 | The Ubuntu operating system must be configured such that Pluggable Authentication Module (PAM) prohibits the use of cached authentications after one day. | This requires smart card authentication. TKG does not support this setup. | Not applicable | |
| V-238365 | Ubuntu operating system must implement cryptographic mechanisms to prevent unauthorized modification of all information at rest. | ClusterAPI VM does not support disk encryption | FS must encrypted on VSAN | |
| V-238366 | Ubuntu operating system must implement cryptographic mechanisms to prevent unauthorized disclosure of all information at rest. | ClusterAPI VM does not support disk encryption | FS must encrypted on VSAN | |
| V-238367 | The Ubuntu operating system must configure the uncomplicated firewall to rate-limit impacted network interfaces. | Rate Limit for NIC is configured using UFW, this firewall is inactive on TKG and not supported. | Not applicable | |
| V-238379 | The Ubuntu operating system must disable the x86 Ctrl-Alt-Delete key sequence if a graphical user interface is installed. | GUI is NOT installed on TKG | Not applicable |
STIG Exceptions with BYOI OS Hardening
STIG exceptions for Ubuntu OS 2x.04 in class-based TKG clusters with custom (Bring Your Own Image) hardened OVA, created by running Image Builder with the ansible_user_vars settings for STIG hardening described in Build a Linux Image:
| STIG ID | STIG Description | Reason | Workaround |
|---|---|---|---|
| V-238214 | The Ubuntu operating system must display the Standard Mandatory DoD Notice and Consent Banner before granting any local or remote connection to the system. | The DoD SSH banner is not installed by default, but a workaround presents a way to enable it. | Must recreate the node with install_sshd_login_banner=true enabled. |
| V-238216 | The Ubuntu operating system must configure the SSH daemon to use Message Authentication Codes (MACs) employing FIPS 140-2 | Ubuntu FIPS is not supported. | Not supported. |
| V-238217 | The Ubuntu operating system must configure the SSH daemon to use FIPS-140-2 approved ciphers | Ubuntu FIPS is not supported. | Not supported. |
| V-238236 | The Ubuntu operating system must be configured so that the script which runs each 30 days or less to check file integrity is the default one. | AIDE is not installed or enabled by default | Must recreate the node with install_aide=true enabled and copy the example script: sudo cp -f /usr/share/aide/config/cron.daily/aide /etc/cron.daily/aide |
| V-238303 | The Ubuntu operating system must use cryptographic mechanisms to protect the integrity of audit tools. | AIDE is not installed or enabled by default | Must recreate the node with install_aide=true enabled. |
| V-238358 | The Ubuntu operating system must notify designated personnel if baseline configurations are changed in an unauthorized manner. | AIDE is not installed or enabled by default | Must recreate the node with install_aide=true enabled. |
| V-238363 | The Ubuntu operating system must implement NIST FIPS-validated | AIDE is not installed or enabled by default | Must recreate the node with install_aide=true enabled. |
| V-238364 | The Ubuntu operating system must use DoD PKI-established certificate authorities for verification of the establishment of protected sessions. | DoD Certificate Authority chain is not installed by default | Customers running on a DoD network must install the CA chain, and recreate the node with remove_existing_ca_certs=true |
| V-238371 | The Ubuntu operating system must use a file integrity tool to verify correct operation of all security functions. | AIDE is not installed or enabled by default | Must recreate the node with install_aide=true enabled. |
| V-238372 | The Ubuntu operating system must notify designated personnel if baseline configurations are changed in an unauthorized manner | AIDE is not installed or enabled by default | Must recreate the node with install_aide=true enabled. |
STIG Exceptions with Kubernetes Hardening
Kubernetes Scan Results:
Control plane nodes:
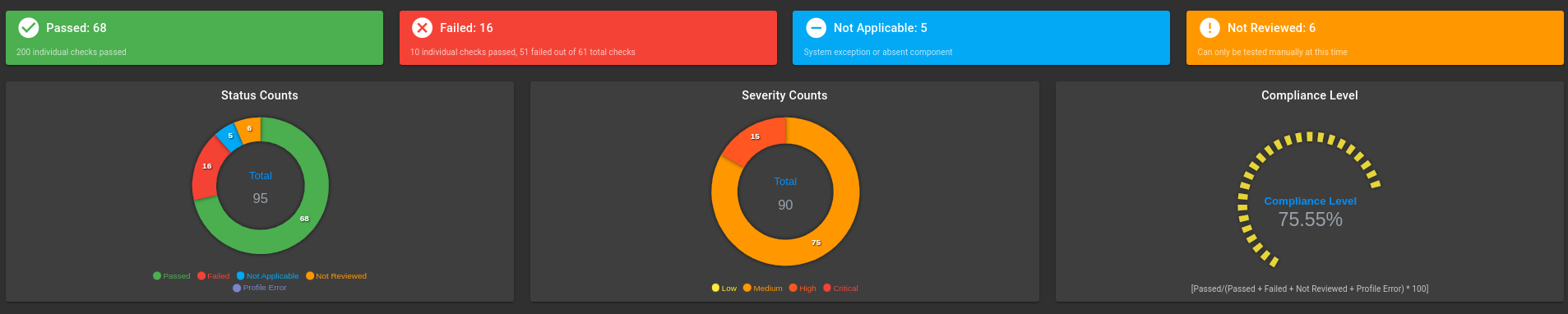
Worker nodes:
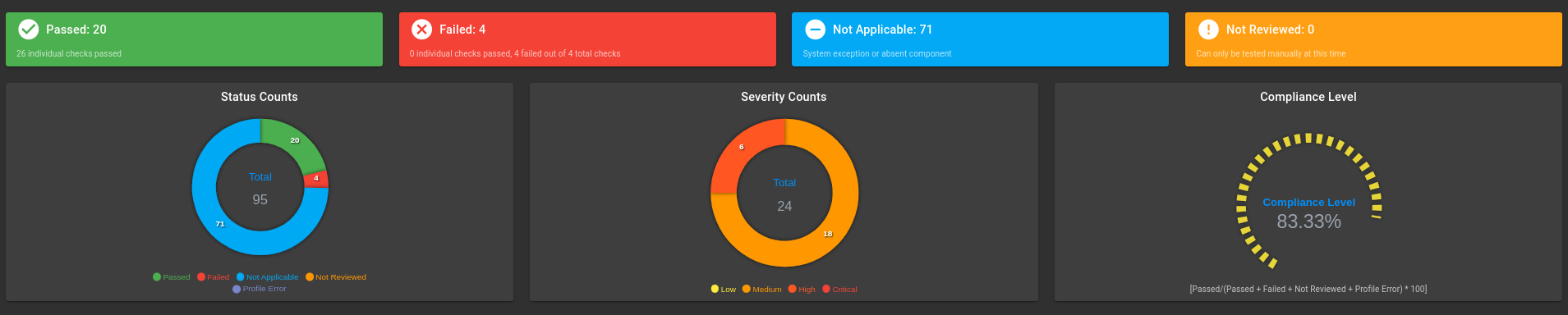
STIG exceptions for Kubernetes in class-based TKG clusters with Kubernetes hardened using the configuration file variable settings listed in STIG Hardening:
| STIG ID | STIG Description | Reason | Workaround |
|---|---|---|---|
| V-242376 | The Kubernetes Controller Manager must use TLS 1.2, at a minimum, to protect the confidentiality of sensitive data during electronic dissemination. | This can be resolved by setting SECURITY_MINIMUM_TLS_PROTOCOL. Valid values tls_1.2 or tls_1.3. |
|
| V-242377 | The Kubernetes Scheduler must use TLS 1.2, at a minimum, to protect the confidentiality of sensitive data during electronic dissemination. | This can be resolved by setting SECURITY_MINIMUM_TLS_PROTOCOL. Valid values tls_1.2 or tls_1.3. |
|
| V-242378 | The Kubernetes API Server must use TLS 1.2, at a minimum, to protect the confidentiality of sensitive data during electronic dissemination. | This can be resolved by setting SECURITY_MINIMUM_TLS_PROTOCOL. Valid values tls_1.2 or tls_1.3. |
|
| V-242390 | The Kubernetes API server must have anonymous authentication disabled. | This can be resolved by setting APISERVER_EXTRA_ARGS. | |
| V-242403 | Kubernetes API Server must generate audit records that identify what type of event has occurred, identify the source of the event, contain the event results, identify any users, and identify any containers associated with the event. | This can be resolved by setting ENABLE_AUDIT_LOGGING: true | |
| V-242409 | Kubernetes Controller Manager must disable profiling. | This is set by default. To manually override this default set KUBE_CONTROLLER_MANAGER_EXTRA_ARGS | |
| V-242414 | The Kubernetes cluster must use non-privileged host ports for user pods. | The vmware-system and tkg-system namespace are special namespaces with static ports required for system functioning. | Firewall or Network Policies may be used to limit traffic for these services. |
| V-242415 | Secrets in Kubernetes must not be stored as environment variables. | AVI (TKG default load balancer) by default manages its secret for its CA in an environment variable. | There are not workarounds for this at the moment. |
| V-242418 | The Kubernetes API server must use approved cipher suites. | This can be resolved by setting APISERVER_EXTRA_ARGS. | |
| V-242425 | Kubernetes Kubelet must enable tls-cert-file for client authentication to secure service. | RotateServerCertificates requires serving certificates to be manually approved. The user can manually enable this, approve the certificates, and then apply this setting to the kubelets. | |
| V-242434 | Kubernetes Kubelet must enable kernel protection. | This can be resolved by setting the worker node and control plane KUBELET_EXTRA_ARGS. | |
| V-242445 | The Kubernetes component etcd must be owned by etcd. | To provision clusters, Tanzu Kubernetes Grid uses Cluster API which, in turn, uses the kubeadm tool to provision Kubernetes. kubeadm makes etcd run containerized as a static pod, therefore the directory does not need to be set to a particular user. | |
| V-242468 | The Kubernetes API Server must prohibit communication using TLS version 1.0 and 1.1, and SSL 2.0 and 3.0. | This can be resolved by setting APISERVER_EXTRA_ARGS | |
| V-254800 | Kubernetes must have a Pod Security Admission control file configured. | OPA Gatekeeper is a viable alternative and allows for finer grained pod security. |
Hardening Plan-Based (Legacy) Workload Clusters
STIG scan results for plan-based (legacy) TKG workload clusters hardened as described in Hardening Plan-Based Workload Clusters are:
-
Control Plane
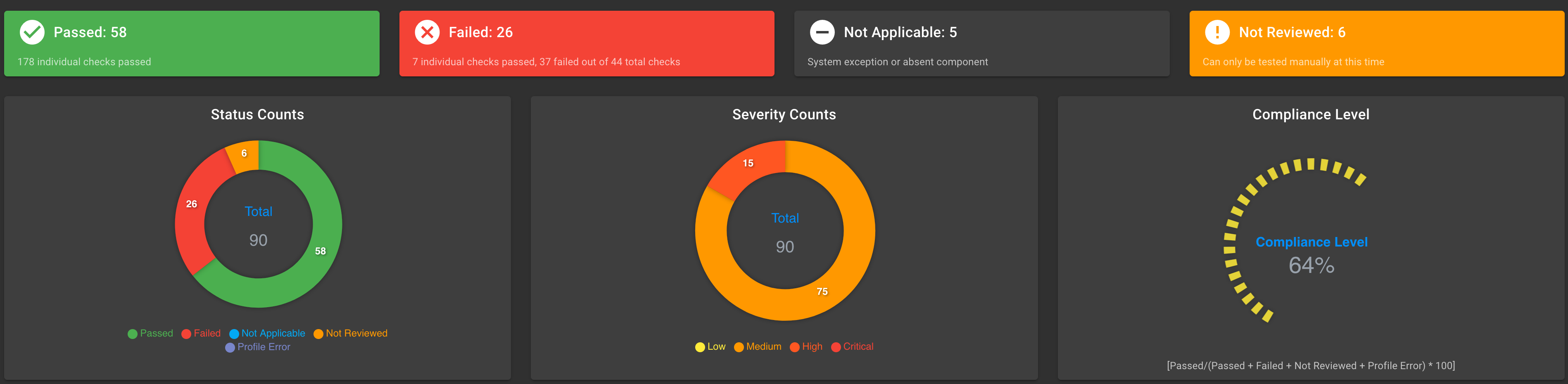
-
Worker Nodes
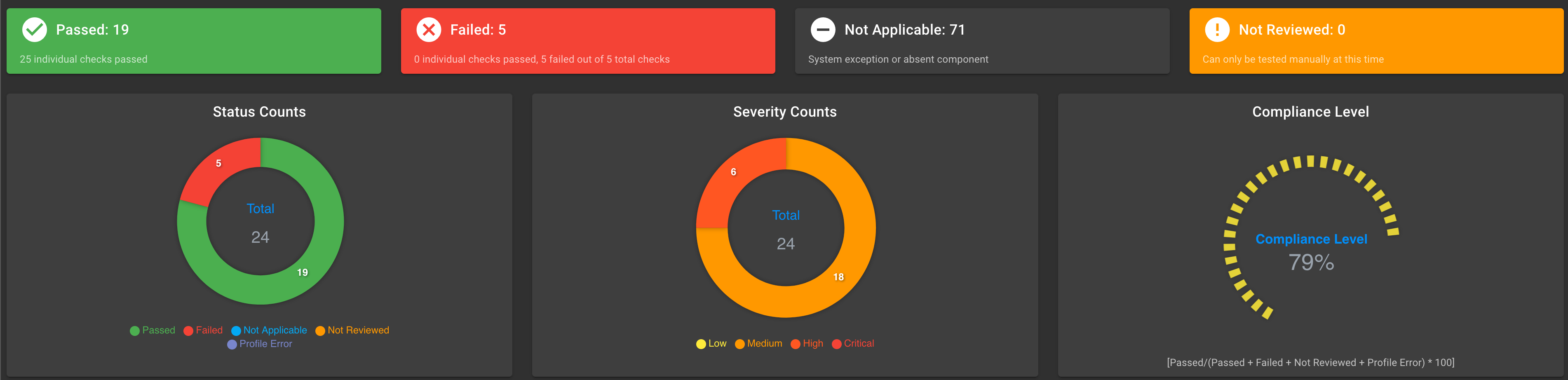
STIG Results and Exceptions for Plan-Based Cluster Control Plane
| VID | Finding Title | Compliant by default? | Can be Resolved? | Explanation/Exception |
|---|---|---|---|---|
| V-242376 | The Kubernetes Controller Manager must use TLS 1.2, at a minimum, to protect the confidentiality of sensitive data during electronic dissemination. | No | Yes | This can be resolved with a ytt overlay |
| V-242377 | The Kubernetes Scheduler must use TLS 1.2, at a minimum, to protect the confidentiality of sensitive data during electronic dissemination. | No | Yes | This can be resolved with a ytt overlay |
| V-242378 | The Kubernetes API server must use TLS 1.2, at a minimum, to protect the confidentiality of sensitive data during electronic dissemination. | No | Yes | This can be resolved with a ytt overlay |
| V-242379 | The Kubernetes etcd must use TLS to protect the confidentiality of sensitive data during electronic dissemination. | No | Yes | This can be resolved with a ytt overlay |
| V-242380 | The Kubernetes etcd must use TLS to protect the confidentiality of sensitive data during electronic dissemination. | Yes | ||
| V-242381 | The Kubernetes Controller Manager must create unique service accounts for each work payload. | Yes | ||
| V-242382 | The Kubernetes API server must enable Node,RBAC as the authorization mode. | Yes | ||
| V-242383 | User-managed resources must be created in dedicated namespaces. | Yes | ||
| V-242384 | The Kubernetes Scheduler must have secure binding. | Yes | ||
| V-242385 | The Kubernetes Controller Manager must have secure binding. | Yes | ||
| V-242386 | The Kubernetes API server must have the insecure port flag disabled. | No | No | Exception --insecure-port flag has been removed in Kubernetes v1.24+ |
| V-242387 | The Kubernetes Kubelet must have the read-only port flag disabled. | Yes | ||
| V-242388 | The Kubernetes API server must have the insecure bind address not set. | Yes | ||
| V-242389 | The Kubernetes API server must have the secure port set. | Yes | ||
| V-242390 | The Kubernetes API server must have anonymous authentication disabled. | No | No | Exception RBAC authorization is enabled on the API server (V-242382), it is generally considered reasonable to allow anonymous access to the API server for health checks and discovery purposes when RBAC is enabled |
| V-242391 | The Kubernetes Kubelet must have anonymous authentication disabled. | Yes | ||
| V-242392 | The Kubernetes kubelet must enable explicit authorization. | Yes | ||
| V-242393 | Kubernetes Worker Nodes must not have sshd service running. | Yes | ||
| V-242394 | Kubernetes Worker Nodes must not have the sshd service enabled. | No | No | Exception ssh is restricted to only the bastion server and is needed to enable serving certificates and install monitoring tools. Also this is not a worker node |
| V-242395 | Kubernetes dashboard must not be enabled. | Yes | ||
| V-242396 | Kubernetes Kubectl cp command must give expected access and results. | Yes | ||
| V-242397 | The Kubernetes kubelet static PodPath must not enable static pods. | No | No | Exception TKG utilizes the staticPodPath to launch numerous components so it can not be disabled |
| V-242398 | Kubernetes DynamicAuditing must not be enabled. | Yes | ||
| V-242399 | Kubernetes DynamicKubeletConfig must not be enabled. | Yes | ||
| V-242400 | The Kubernetes API server must have Alpha APIs disabled. | Yes | ||
| V-242401 | The Kubernetes API server must have an audit policy set. | Yes | ||
| V-242402 | The Kubernetes API server must have an audit log path set. | Yes | ||
| V-242403 | Kubernetes API server must generate audit records that identify what type of event has occurred, identify the source of the event, contain the event results, identify any users, and identify any containers associated with the event. | Yes | ||
| V-242403 | Kubernetes API server must generate audit records that identify what type of event has occurred, identify the source of the event, contain the event results, identify any users, and identify any containers associated with the event. | Yes | ||
| V-242403 | Kubernetes API server must generate audit records that identify what type of event has occurred, identify the source of the event, contain the event results, identify any users, and identify any containers associated with the event. | Yes | ||
| V-242403 | Kubernetes API server must generate audit records that identify what type of event has occurred, identify the source of the event, contain the event results, identify any users, and identify any containers associated with the event. | Yes | ||
| V-242403 | Kubernetes API server must generate audit records that identify what type of event has occurred, identify the source of the event, contain the event results, identify any users, and identify any containers associated with the event. | Yes | ||
| V-242403 | Kubernetes API server must generate audit records that identify what type of event has occurred, identify the source of the event, contain the event results, identify any users, and identify any containers associated with the event. | Yes | ||
| V-242404 | Kubernetes Kubelet must deny hostname override. | No | No | Exception This is needed for public cloud Kubernetes clusters. |
| V-242405 | The Kubernetes manifests must be owned by root. | Yes | ||
| V-242406 | The Kubernetes kubelet configuration file must be owned by root. | Yes | ||
| V-242407 | The Kubernetes kubelet configuration file must be owned by root. | Yes | ||
| V-242408 | The Kubernetes manifests must have least privileges. | Yes | ||
| V-242409 | Kubernetes Controller Manager must disable profiling. | No | Yes | This can be resolved with a ytt overlay |
| V-242410 | The Kubernetes API server must enforce ports, protocols, and services(PPS) that adhere to the Ports, Protocols, and Services Management CategoryAssurance List (PPSM CAL). | No | No | Exception Manual Review - Handled by PPSM monitoring solution |
| V-242411 | The Kubernetes Scheduler must enforce ports, protocols, and services(PPS) that adhere to the Ports, Protocols, and Services Management CategoryAssurance List (PPSM CAL). | No | No | Exception Manual Review - Handled by PPSM monitoring solution |
| V-242412 | The Kubernetes Controllers must enforce ports, protocols, and services(PPS) that adhere to the Ports, Protocols, and Services Management CategoryAssurance List (PPSM CAL). | No | No | Exception Manual Review - Handled by PPSM monitoring solution |
| V-242413 | The Kubernetes etcd must enforce ports, protocols, and services (PPS)that adhere to the Ports, Protocols, and Services Management Category AssuranceList (PPSM CAL). | No | No | Exception Manual Review - Handled by PPSM monitoring solution |
| V-242414 | The Kubernetes cluster must use non-privileged host ports for user pods. | No | No | Exception Manual Review - Handled by PPSM monitoring solution |
| V-242415 | Secrets in Kubernetes must not be stored as environment variables. | Yes | ||
| V-242416 | Kubernetes Kubelet must not disable timeouts. | No | Yes | This can be resolved with a ytt overlay |
| V-242417 | Kubernetes must separate user functionality. | No | No | Exception Manual Review |
| V-242418 | The Kubernetes API server must use approved cipher suites. | Yes | ||
| V-242419 | Kubernetes API server must have the SSL Certificate Authority set. | Yes | ||
| V-242420 | Kubernetes Kubelet must have the SSL Certificate Authority set. | Yes | ||
| V-242421 | Kubernetes Controller Manager must have the SSL Certificate Authority set. | Yes | ||
| V-242422 | Kubernetes API server must have a certificate for communication. | Yes | ||
| V-242423 | Kubernetes etcd must enable client authentication to secure service. | Yes | ||
| V-242424 | Kubernetes Kubelet must enable tls-private-key-file for client authentication to secure service. |
No | Yes | This can be enabled manually after the feature gate for the controller manager and kubelet, RotateServerCertificates, is added to the overlay along with the client-ca-file defined in the kubelet and the kubelet-certificate-authority defined in the api-server. Once the cluster starts with the aforementioned enabled the certificates can be manually approved as kubelet-serving certificates are not auto approved and then the kubelet configs can be modified to include tls-private-key-file and tls-cert-file both pointing at the newly create kubelet-server-current.pem file. Then simply restart the kubelet |
| V-242425 | Kubernetes Kubelet must enable tls-cert-file for client authentication to secure service. |
No | Yes | This can be enabled manually after the feature gate for the controller manager and kubelet, RotateServerCertificates, is added to the overlay along with the client-ca-file defined in the kubelet and the kubelet-certificate-authority defined in the api-server. Once the cluster starts with the aforementioned enabled the certificates can be manually approved as kubelet-serving certificates are not auto approved and then the kubelet configs can be modified to include tls-private-key-file and tls-cert-file both pointing at the newly create kubelet-server-current.pem file. Then simply restart the kubelet |
| V-242426 | Kubernetes etcd must enable client authentication to secure service. | Yes | ||
| V-242427 | Kubernetes etcd must have a key file for secure communication. | Yes | ||
| V-242428 | Kubernetes etcd must have a certificate for communication. | Yes | ||
| V-242429 | Kubernetes etcd must have the SSL Certificate Authority set. | Yes | ||
| V-242430 | Kubernetes etcd must have a certificate for communication. | Yes | ||
| V-242431 | Kubernetes etcd must have a key file for secure communication. | Yes | ||
| V-242432 | Kubernetes etcd must have peer-cert-file set for secure communication. | Yes | ||
| V-242433 | Kubernetes etcd must have a peer-key-file set for secure communication. | Yes | ||
| V-242434 | Kubernetes Kubelet must enable kernel protection. | No | Yes | This can be resolved after creating either a custom AMI or setting up the host’s properly ahead of time and then enabling it via a ytt overlay |
| V-242435 | Kubernetes must prevent non-privileged users from executing privileged functions to include disabling, circumventing, or altering implemented security safeguards/countermeasures or the installation of patches and updates. | Yes | ||
| V-242435 | Kubernetes must prevent non-privileged users from executing privileged functions to include disabling, circumventing, or altering implemented security safeguards/countermeasures or the installation of patches and updates. | Yes | ||
| V-242435 | Kubernetes must prevent non-privileged users from executing privileged functions to include disabling, circumventing, or altering implemented security safeguards/countermeasures or the installation of patches and updates. | Yes | ||
| V-242436 | The Kubernetes API server must have the ValidatingAdmissionWebhook enabled. | Yes | ||
| V-242437 | Kubernetes must have a pod security policy set. | No | No | Exception OPA Gatekeeper is the recommended solution for Pod Security after the deprecation of Pod Security Policies |
| V-242438 | Kubernetes API server must configure timeouts to limit attack surface. | Yes | ||
| V-242439 | Kubernetes API server must disable basic authentication to protect information in transit. | Yes | ||
| V-242440 | Kubernetes API server must disable token authentication to protect information in transit. | Yes | ||
| V-242441 | Kubernetes endpoints must use approved organizational certificate and key pair to protect information in transit. | Yes | ||
| V-242442 | Kubernetes must remove old components after updated versions have been installed. | No | No | Exception Manual Review |
| V-242443 | Kubernetes must contain the latest updates as authorized by IAVMs,CTOs, DTMs, and STIGs. | Yes | ||
| V-242444 | The Kubernetes component manifests must be owned by root. | Yes | ||
| V-242445 | The Kubernetes component etcd must be owned by etcd. | No | No | Exception The data directory (/var/lib/etcd) is owned by root:root.To provision clusters, Tanzu Kubernetes Grid uses Cluster API which, in turn, uses the kubeadm tool to provision Kubernetes. kubeadm makes etcd run containerized as a static pod, therefore the directory does not need to be set to a particular user. kubeadm configures the directory to not be readable by non-root users. |
| V-242446 | The Kubernetes conf files must be owned by root. | Yes | ||
| V-242447 | The Kubernetes Kube Proxy must have file permissions set to 644 or more restrictive. | No | No | Exception Kubeconfig for kube-proxy is a symlink. The base file is 0644 or less permissive. Manual Review |
| V-242448 | The Kubernetes Kube Proxy must be owned by root. | Yes | ||
| V-242449 | The Kubernetes Kubelet certificate authority file must have file permissions set to 644 or more restrictive. | Yes | ||
| V-242450 | The Kubernetes Kubelet certificate authority must be owned by root. | Yes | ||
| V-242451 | The Kubernetes component PKI must be owned by root. | Yes | ||
| V-242452 | The Kubernetes kubelet config must have file permissions set to 644 or more restrictive. | Yes | ||
| V-242453 | The Kubernetes kubelet config must be owned by root. | Yes | ||
| V-242454 | The Kubernetes kubeadm must be owned by root. | Yes | ||
| V-242455 | The Kubernetes kubelet service must have file permissions set to 644 or more restrictive. | Yes | ||
| V-242456 | The Kubernetes kubelet config must have file permissions set to 644 or more restrictive. | Yes | ||
| V-242457 | The Kubernetes kubelet config must be owned by root. | Yes | ||
| V-242458 | The Kubernetes API server must have file permissions set to 644 or more restrictive. | Yes | ||
| V-242459 | The Kubernetes etcd must have file permissions set to 644 or more restrictive. | Yes | ||
| V-242460 | The Kubernetes admin.conf must have file permissions set to 644 or more restrictive. | Yes | ||
| V-242461 | Kubernetes API server audit logs must be enabled. | Yes | ||
| V-242462 | The Kubernetes API server must be set to audit log max size. | Yes | ||
| V-242463 | The Kubernetes API server must be set to audit log maximum backup. | Yes | ||
| V-242464 | The Kubernetes API server audit log retention must be set. | Yes | ||
| V-242465 | The Kubernetes API server audit log path must be set. | Yes | ||
| V-242466 | The Kubernetes PKI CRT must have file permissions set to 644 or more restrictive. | Yes | ||
| V-242467 | The Kubernetes PKI keys must have file permissions set to 600 or more restrictive. | Yes | ||
| V-242468 | The Kubernetes API server must prohibit communication using TLS version 1.0 and 1.1, and SSL 2.0 and 3.0. | No | Yes | This can be resolved with a ytt overlay |
STIG Results and Exceptions for Plan-Based Cluster Workers
| VID | Finding Title | Compliant by default? | Can be Resolved? | Explanation/Exception |
|---|---|---|---|---|
| V-242387 | The Kubernetes Kubelet must have the read-only port flag disabled. | Yes | ||
| V-242391 | The Kubernetes Kubelet must have anonymous authentication disabled. | Yes | ||
| V-242392 | The Kubernetes kubelet must enable explicit authorization. | Yes | ||
| V-242393 | Kubernetes Worker Nodes must not have sshd service running. | Yes | ||
| V-242394 | Kubernetes Worker Nodes must not have the sshd service enabled. | No | No | Exception ssh is restricted to only the bastion server and is needed to enable serving certificates and install monitoring tools |
| V-242396 | Kubernetes Kubectl cp command must give expected access and results. | Yes | ||
| V-242397 | The Kubernetes kubelet static PodPath must not enable static pods. | No | No | Exception staticPodPath is needed for TKG to install properly as several of the pods in the tkg-system are defined there |
| V-242398 | Kubernetes DynamicAuditing must not be enabled. | Yes | ||
| V-242399 | Kubernetes DynamicKubeletConfig must not be enabled. | Yes | ||
| V-242400 | The Kubernetes API server must have Alpha APIs disabled. | Yes | ||
| V-242404 | Kubernetes Kubelet must deny hostname override. | No | No | Exception hostname-override is needed for public cloud deployments of Kubernetes |
| V-242406 | The Kubernetes kubelet configuration file must be owned by root. | Yes | ||
| V-242407 | The Kubernetes kubelet configuration file must be owned by root. | Yes | ||
| V-242416 | Kubernetes Kubelet must not disable timeouts. | No | Yes | This can be resolved with a ytt overlay |
| V-242420 | Kubernetes Kubelet must have the SSL Certificate Authority set. | Yes | ||
| V-242425 | Kubernetes Kubelet must enable tls-cert-file for client authentication to secure service. | No | Yes | This can be enabled manually after the feature gate for the controller manager and kubelet, RotateServerCertificates, is added to the overlay along with the client-ca-file defined in the kubelet and the kubelet-certificate-authority defined in the api-server. Once the cluster starts with the aforementioned enabled the certificates can be manually approved as kubelet-serving certificates are not auto approved and then the kubelet configs can be modified to include tls-private-key-file and tls-cert-file both pointing at the newly create kubelet-server-current.pem file. Then simply restart the kubelet |
| V-242434 | Kubernetes Kubelet must enable kernel protection. | No | Yes | This can be resolved after creating either a custom AMI or setting up the host’s properly ahead of time and then enabling it via a ytt overlay |
| V-242449 | The Kubernetes Kubelet certificate authority file must have file permissions set to 644 or more restrictive. | Yes | ||
| V-242450 | The Kubernetes Kubelet certificate authority must be owned by root. | Yes | ||
| V-242451 | The Kubernetes component PKI must be owned by root. | Yes | ||
| V-242452 | The Kubernetes kubelet config must have file permissions set to 644 or more restrictive. | Yes | ||
| V-242453 | The Kubernetes kubelet config must be owned by root. | Yes | ||
| V-242454 | The Kubernetes kubeadm must be owned by root. | Yes | ||
| V-242455 | The Kubernetes kubelet service must have file permissions set to 644 or more restrictive. | Yes | ||
| V-242456 | The Kubernetes kubelet config must have file permissions set to 644 or more restrictive. | Yes | ||
| V-242457 | The Kubernetes kubelet config must be owned by root. | Yes | ||
| V-242466 | The Kubernetes PKI CRT must have file permissions set to 644 or more restrictive. | Yes |