STIG hardening for TAS for VMs Ubuntu hosts
By default, all Tanzu Application Service (TAS for VMs) 2.x virtual machines (VMs) run Ubuntu v16.04 based stemcell. The stemcells are hardened by default to some STIG specification. The stemcell can be further hardened to Ubuntu 16.04 STIG benchmark using xenial-compliance release
Ubuntu 16.04 STIG hardening results
The STIG hardening process for Ubuntu stemcell changes the compliance scans for TAS for VMs v2.13 VMs. The following screen captures show the scan results for TAS for VMs VMs after hardening.
Scan results for hardened TAS for VMs v2.13 VMs:
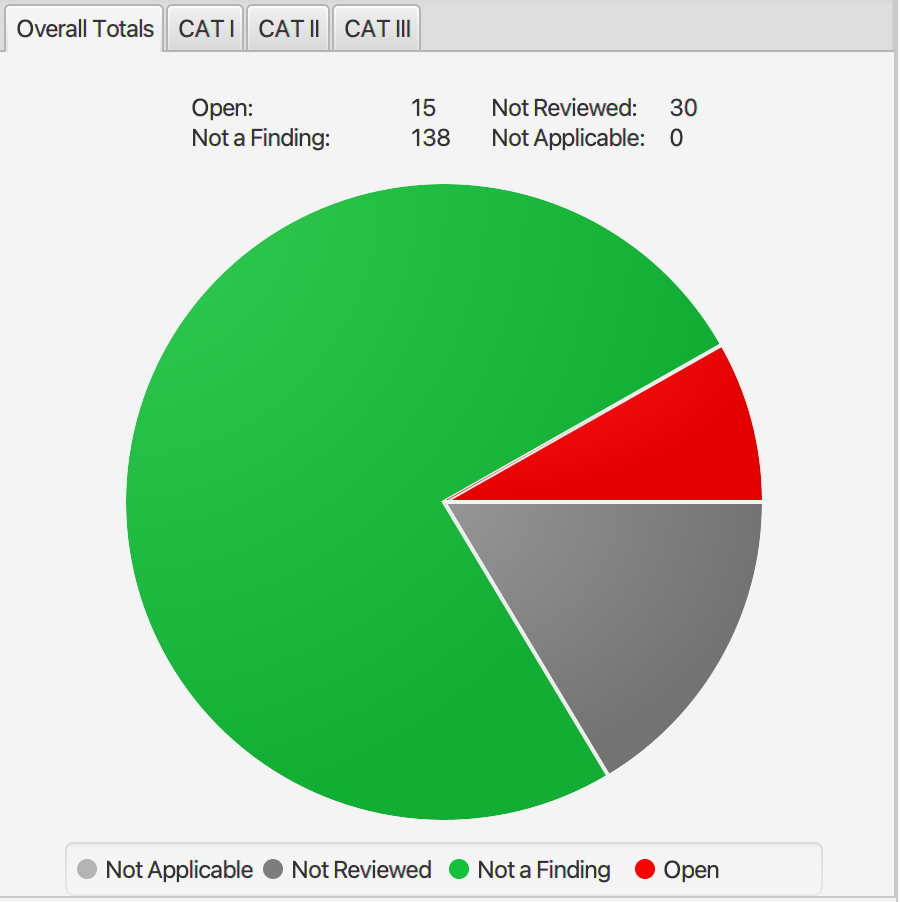
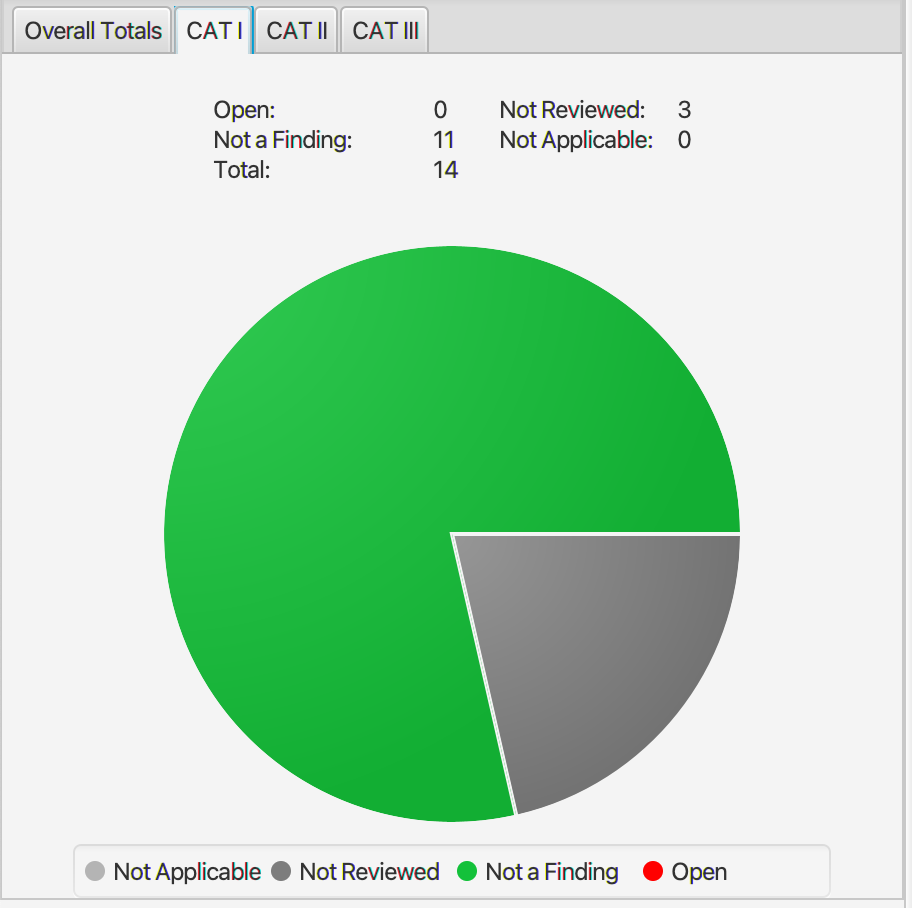
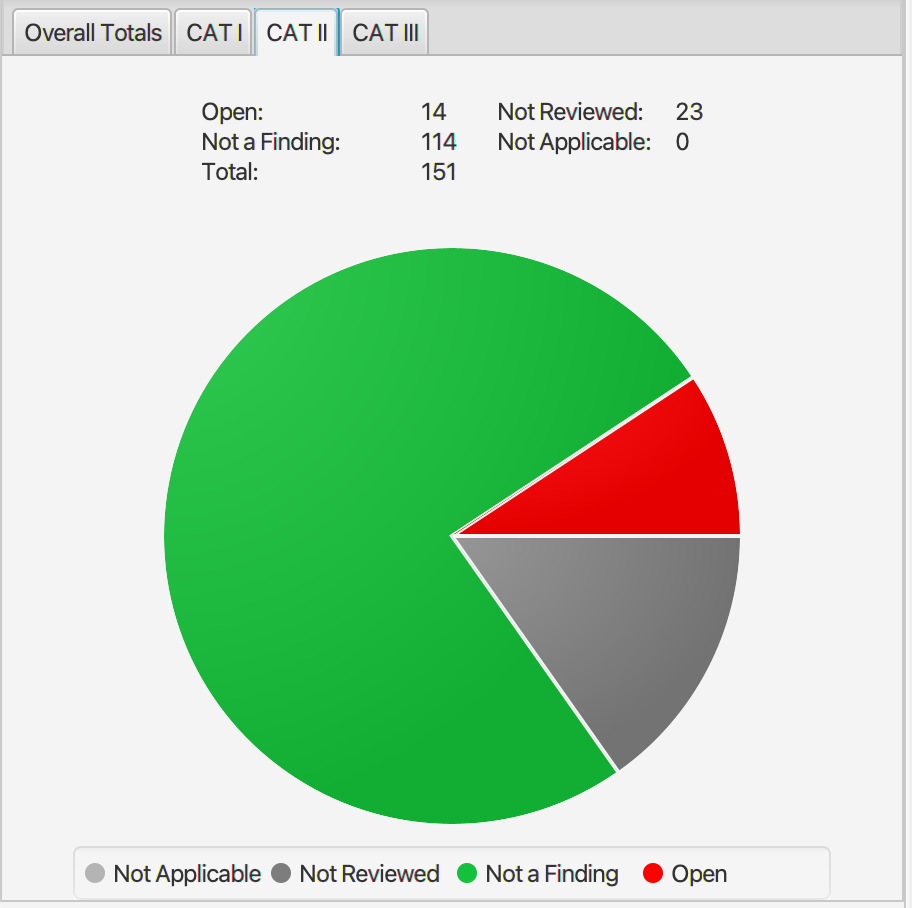
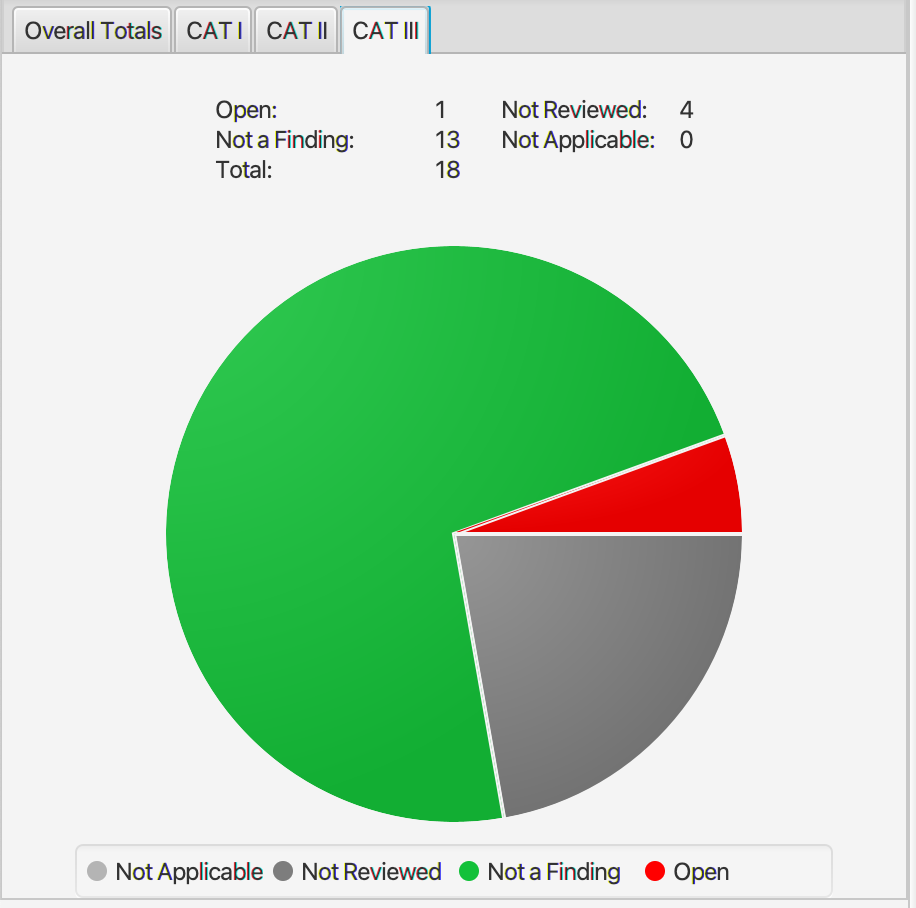
STIG results and exceptions for Ubuntu 16.04 stemcell
Some Ubuntu processes/features are not hardened. The following table lists the hardening results and exceptions. The table also provides an explanation for the exception and a resolution.
| VID | Finding Title | Exception / Explanation |
|---|---|---|
| V-214939 | The Ubuntu operating system must be a vendor supported release. | VMware has a commercial agreement with Canonical to continue providing secure and patched Xenial stemcells through April 2024. See: Notes below table. |
| V-214941 | The Ubuntu operating system must display the Standard Mandatory DoD Notice and Consent Banner before granting local or remote access to the system via a graphical user logon. | GNOME is a GUI for Ubuntu. Stemcells do not have GNOME the package installed. |
| V-214942 | The Ubuntu operating system must display the Standard Mandatory DoD Notice and Consent Banner before granting local or remote access to the system via a command line user logon. | /etc/issue.net is used instead for /etc/issue since VM can only be accessed via ssh |
| V-214943 | The Ubuntu operating system must enable a user session lock until that user re-establishes access using established identification and authentication procedures. | “Note: If the Ubuntu operating system does not have GNOME installed, this requirement is not applicable”. GNOME is a GUI for Ubuntu. Stemcells do not have GNOME the package installed. |
| V-214944 | All users must be able to directly initiate a session lock for all connection types. | “A session lock is a temporary action taken when a user stops work and moves away from the immediate physical vicinity of the information system but does not want to log out because of the temporary nature of the absence. The rule deals with session locks of virtual consoles (using vlock) when accessing a physical machine.” This rule is applicable to virtual consoles on a physical machine. End users do not have physical access to a BOSH deployed VM. |
| V-214945 | Ubuntu operating system sessions must be automatically logged out after 15 minutes of inactivity. | End users cannot initiate a local interactive session because they do not have physical access to a BOSH deployed VM. For remote sessions the timeout is provided by SV-215129r610931. |
| V-214946 | The Ubuntu operating system must limit the number of concurrent sessions to ten for all accounts and/or account types. | BOSH creates a new ephemeral user per session, which is deleted when the session terminates. A BOSH SSH user cannot have more than one concurrent session. |
| V-214947 | The Ubuntu operating system must prevent direct login into the root account. | The password of root is randomised by the bosh-agen on the stemcell on bootstrap and is unusable. |
| V-214948 | The Ubuntu operating system must be configured so that when passwords are changed or new passwords are established, pwquality must be used. | Stemcell uses pam_cracklib.so to enforce password complexity. Additionally, BOSH SSH users are ephemeral. They use key-based login and not password-based login.. |
| V-214949 | The Ubuntu operating system must enforce password complexity by requiring that at least one upper-case character be used. | This setting is in /etc/pam.d/common-password instead of /etc/security/pwquality.conf. |
| V-214950 | The Ubuntu operating system must enforce password complexity by requiring that at least one lower-case character be used. | This setting is in /etc/pam.d/common-password instead of /etc/security/pwquality.conf. |
| V-214951 | The Ubuntu operating system must enforce password complexity by requiring that at least one numeric character be used. | This setting is in /etc/pam.d/common-password instead of /etc/security/pwquality.conf. |
| V-214952 | All passwords must contain at least one special character. | This setting is in /etc/pam.d/common-password instead of /etc/security/pwquality.conf. |
| V-214953 | The Ubuntu operating system must require the change of at least 8 characters when passwords are changed. | BOSH SSH users are ephemeral. They use key-based login and not password-based login. |
| V-214954 | The Ubuntu operating system must encrypt all stored passwords with a FIPS 140-2 approved cryptographic hashing algorithm. | Stemcells use two system users, root and vcap. All BOSH processes run as vcap. This rule is not applicable because no other users are created on BOSH deployed VMs when using the default stemcell configuration. |
| V-214956 | The Ubuntu operating system must employ FIPS 140-2 approved cryptographic hashing algorithms for all created passwords. | Stemcells use two system users, root and vcap. All BOSH processes run as vcap.This rule is not applicable because no other users are created on BOSH deployed VMs when using the default stemcell configuration. |
| V-214960 | Passwords for new users must have a 60-day maximum password lifetime restriction. | BOSH SSH users are ephemeral and use key based-login and not password-based login. |
| V-214962 | Passwords must have a minimum of 15-characters. | BOSH SSH users are ephemeral and use key based-login and not password-based login. |
| V-214964 | The Ubuntu operating system must prevent the use of dictionary words for passwords. | BOSH SSH users are ephemeral and use key based-login and not password-based login. User passwords are not changed on the VM |
| V-214966 | Account identifiers (individuals, groups, roles, and devices) must disabled after 35 days of inactivity. | BOSH SSH users are ephemeral and use key-based login and not password-based login. |
| V-214967 | The Ubuntu operating system must automatically lock an account until the locked account is released by an administrator when three unsuccessful logon attempts. | BOSH SSH users are ephemeral. They use key-based login and not password-based login. |
| V-214968 | Accounts on the Ubuntu operating system that are subject to three unsuccessful logon attempts within 15 minutes must be locked for the maximum configurable period. | BOSH SSH users are ephemeral and use key-based login and not password-based login. |
| V-214969 | The Ubuntu operating system must require users to re-authenticate for privilege escalation and changing roles. | BOSH SSH uses key-based login. SSH users have passwordless sudo privilege. |
| V-214970 | Temporary user accounts must be provisioned with an expiration time of 72 hours or less. | Stemcells do not have temporary accounts. |
| V-214971 | The Ubuntu operating system must enforce a delay of at least 4 seconds between logon prompts following a failed logon attempt. | BOSH SSH users are ephemeral. They use key-based login and not password-based login. |
| V-214972 | Unattended or automatic login via the Graphical User Interface must not be allowed. | “Verify that unattended or automatic login via the GUI is disabled.” BOSH VMs do not have GUI-based logins. |
| V-214973 | The Ubuntu operating system must display the date and time of the last successful account logon upon logon. | BOSH creates a new ephemeral user per session, which is deleted when the session terminates. Due to this there is no mechanism to provide users with feedback on when account accesses last occurred. |
| V-214976 | The Ubuntu operating system must implement NSA-approved cryptography to protect classified information in accordance with applicable federal laws, Executive Orders, directives, policies, regulations, and standards. | Stemcells are not Federal Information Processing Standards (FIPS) compliant. |
| V-214977 | Ubuntu operating systems booted with a BIOS must require authentication upon booting into single-user and maintenance modes. | Stemcells use legacy GRUB. The test is modifed to verfiy for legacy GRUB configuration. |
| V-214978 | Ubuntu operating systems booted with United Extensible Firmware Interface (UEFI) implemented must require authentication upon booting into single-user mode and maintenance. | “efibootmgr: EFI variables are not supported on this system.” Stemcells do not support Unified Extensible Firmware Interface (UEFI). Customer can install efibootmgr to verify. |
| V-214979 | All persistent disk partitions must implement cryptographic mechanisms to prevent unauthorized disclosure or modification of all information that requires at rest protection. | Disk encryption is handled by the IaaS. |
| V-214980 | All public directories must be owned by root to prevent unauthorized and unintended information transferred via shared system resources. | If NFS volume is being used, then files are owned by vcap. |
| V-214981 | All world-writable directories must be group-owned by root, sys, bin, or an application group. | On diego_cell “/var/vcap/data/rep/shared/garden/instance_identity” is owned by vcap. The rep job writes instance certificate and key in to this folder.“/var/vcap/data/grootfs/store/unprivileged/{images,volumes}/
|
| V-214989 | Advance package Tool (APT) must remove all software components after updated versions have been installed. | BOSH handles patching and updating software, and deletes old versions of packages and jobs. |
| V-214995 | The x86 Ctrl-Alt-Delete key sequence in the Ubuntu operating system must be disabled if a Graphical User Interface is installed. | “Verify the Ubuntu operating system is not configured to reboot the system when Ctrl-Alt-Delete is pressed when using a graphical user interface.” Stemcells do not have graphical user interface installed. |
| V-214996 | Default permissions must be defined in such a way that all authenticated users can only read and modify their own files. | The expected umask is 077, the actual is 022. This umask is required for the container runtime runC to function correctly. |
| V-214997 | The Ubuntu operating system must not have unnecessary accounts. | This is a known issue. |
| V-215000 | User accounts with temporary passwords, must require an immediate change to a permanent password after login. | Stemcells use two system users, root and vcap. All BOSH processes run as vcap. This rule is not applicable because no other users are created on BOSH deployed VMs when using the default stemcell configuration. |
| V-215001 | Pluggable Authentication Module (PAM) must prohibit the use of cached authentications after one day. | “Note: If smart card authentication is not being used on the system this item is not applicable.” Stemcells do not support smart card authentication. |
| V-215002 | All files and directories must have a valid owner. | On worker(TKGi), container files (/var/vcap/store/containerd/) fail this test due to kubernetes architecture. |
| V-215003 | All files and directories must have a valid group owner. | On worker(TKGi), container files (/var/vcap/store/containerd/) fail this test due to kubernetes architecture. |
| V-215005 | All local interactive user accounts, upon creation, must be assigned a home directory. | Local interactive users are not created on BOSH VMs. bosh ssh users are assigned home directory in /var/vcap/bosh_ssh/ |
| V-215009 | All local initialization files must have mode 0740 or less permissive. | User initialization files in /home/vcap and for bosh_ssh user in /var/vcap/bosh_ssh/<GUID>/ have permission fo 0644. End user cannot login or sudo as vcap. bosh ssh user is deleted as soon as the ssh session terminates and all associated files under /var/vcap/bosh_ssh/<GUID>/ are also deleted. |
| V-215012 | File systems that contain user home directories must be mounted to prevent files with the setuid and setguid bit set from being executed. | Local interactive users are not created on BOSH VMs. bosh ssh users are assigned home directory in /var/vcap/bosh_ssh/. The home directories are deleted as soon as the ssh session is terminated |
| V-215013 | File systems that are used with removable media must be mounted to prevent files with the setuid and setguid bit set from being executed. | BOSH deployed VMs do not have removable media. |
| V-215018 | The Ubuntu operating system must use a separate file system for /var. | BOSH jobs have permission to read/write to /var/vcap/data and /var/vcap/store directories only. These directories are mounted on a separate file-system |
| V-215022 | The /var/log directory must have mode 0770 or less permissive. | Stemcells have 0771 permissions on /var/log, which is required by the time synchronisation process chrony to list files and folders in the /var/log directory. |
| V-215023 | The /var/log/syslog file must be group-owned by adm. | The /var/log/syslog file must be group-owned by syslog. |
| V-215028 | Library files must be group-owned by root. | /usr/lib/dbus-1.0/dbus-daemon-launch-helper is group-owned by messagebus. |
| V-215034 | The Ubuntu operating system must allocate audit record storage capacity to store at least one weeks worth of audit records, when audit records are not immediately sent to a central audit record storage facility. | Because BOSH deployed VMs are ephemeral, VMware recommends that you forward logs to a remote syslog ingestor. |
| V-215035 | The Ubuntu operating system must notify the System Administrator (SA) and Information System Security Officer (ISSO) (at a minimum) when allocated audit record storage volume reaches 75% of the repository maximum audit record storage capacity. | Because BOSH deployed VMs are ephemeral, VMware recommends that you forward logs to a remote syslog ingestor. |
| V-215038 | The System Administrator (SA) and Information System Security Officer (ISSO) (at a minimum) must be alerted when the audit storage volume is full. | Because BOSH deployed VMs are ephemeral, VMware recommends that you forward logs to a remote syslog ingestor. Setting max_log_file_action=syslog causes disk space to fill up. Stemcells set max_log_file_action=rotate and num_logs = 5 to prevent audit logs from filling up disk space The stemcell setting favours availability to halting. |
| V-215039 | The audit system must take appropriate action when the audit storage volume is full. | VMware recommends that you forward logs to a remote syslog ingestor. Stemcells set max_log_file_action=rotate and num_logs = 5 to prevent audit logs from filling up disk space The stemcell setting favours availability to halting. The stemcell does not have audit event multiplexer installed. |
| V-215040 | The remote audit system must take appropriate action when audit storage is full. | VMware recommends that you forward logs to a remote syslog ingestor. Stemcells set max_log_file_action=rotate and num_logs = 5 to prevent audit logs from filling up disk space The stemcell setting favours availability to halting. The stemcell does not have audit event multiplexer installed. |
| V-215041 | Off-loading audit records to another system must be authenticated. | VMware recommends that you forward logs to a remote syslog ingestor. Stemcells set max_log_file_action=rotate and num_logs = 5 to prevent audit logs from filling up disk space The stemcell setting favours availability to halting. The stemcell does not have audit event multiplexor installed. |
| V-215053 | The audit event multiplexor must be configured to off-load audit logs onto a different system or storage media from the system being audited. | VMware recommends that you forward logs to a remote syslog ingestor. The stemcell does not have audit event multiplexor installed. |
| V-215054 | The audit records must be off-loaded onto a different system or storage media from the system being audited. | VMware recommends that you forward logs to a remote syslog ingestor. The stemcell does not have audit event multiplexor installed. |
| V-215068 | The audit system must be configured to audit any usage of the setxattr system call. | Audit rule for auid=0(root) is missing. End user cannot login as root to execute command. |
| V-215069 | The audit system must be configured to audit any usage of the lsetxattr system call. | Audit rule for auid=0(root) is missing. End user cannot login as root to execute command. |
| V-215070 | The audit system must be configured to audit any usage of the fsetxattr system call. | Audit rule for auid=0(root) is missing. End user cannot login as root to execute command. |
| V-215071 | The audit system must be configured to audit any usage of the removexattr system call. | Audit rule for auid=0(root) is missing. End user cannot login as root to execute command. |
| V-215072 | The audit system must be configured to audit any usage of the lremovexattr system call. | Audit rule for auid=0(root) is missing. End user cannot login as root to execute command. |
| V-215073 | The audit system must be configured to audit any usage of the fremovexattr system call. | Audit rule for auid=0(root) is missing. End user cannot login as root to execute command. |
| V-215093 | Successful/unsuccessful uses of the setfacl command must generate an audit record. | acl packages are not installed on the stemcell. |
| V-215094 | Successful/unsuccessful uses of the chacl command must generate an audit record. | acl packages are not installed on the stemcell. |
| V-215111 | An application firewall must be installed. | Because IP addresses are dynamic in TAS for VMs, Uncomplicated Firewall (UFW) cannot be used to limit traffic between the hosts within TAS. Application Security Groups (ASGs) and perimeter firewalls for the TAS subnet are used instead. iptables is used where necessary. |
| V-215112 | An application firewall must be enabled on the system. | Because IP addresses are dynamic in TAS, Uncomplicated Firewall (UFW) cannot be used to limit traffic between the hosts within TAS. Application Security Groups (ASGs) and perimeter firewalls for the TAS subnet are used instead. iptables is used where necessary. |
| V-215113 | An application firewall must employ a deny-all, allow-by-exception policy for allowing connections to other systems. | Because IP addresses are dynamic in TAS, Uncomplicated Firewall (UFW) cannot be used to limit traffic between the hosts within TAS. Application Security Groups (ASGs) and perimeter firewalls for the TAS subnet are used instead. iptables is used where necessary. |
| V-215114 | The Ubuntu operating system must be configured to prohibit or restrict the use of functions, ports, protocols, and/or services, as defined in the Ports, Protocols, and Services Management (PPSM) Category Assignments List (CAL) and vulnerability assessments. | Because IP addresses are dynamic in TAS, Uncomplicated Firewall (UFW) cannot be used to limit traffic between the hosts within TAS. Application Security Groups (ASGs) and perimeter firewalls for the TAS subnet are used instead. iptables is used where necessary. |
| V-215115 | A sticky bit must be set on all public directories to prevent unauthorized and unintended information transferred via shared system resources. | On worker(TKGi), container files (/var/vcap/data/kubelet/pods/<GUID>) fail this test due to kubernetes architecture. |
| V-215116 | The Ubuntu operating system must compare internal information system clocks at least every 24 hours with a server which is synchronized to an authoritative time source, such as the United States Naval Observatory (USNO) time servers, or a time server designated for the appropriate DoD network (NIPRNet/SIPRNet), and/or the Global Positioning System (GPS). | Default maxpoll for chrony.conf is 10. The polling interval is 2^10 seconds. |
| V-215122 | The Ubuntu operating system must display the Standard Mandatory DoD Notice and Consent Banner before granting local or remote access to the system via a SSH logon and the user must acknowledge the usage conditions and take explicit actions to log on for further access. | /etc/issue.net is used instead for /etc/issue since VM can only be accessed via ssh |
| V-215124 | The Ubuntu operating system must implement DoD-approved encryption to protect the confidentiality of SSH connections. | Stemcells have stronger ciphers. |
| V-215125 | The SSH daemon must be configured to only use Message Authentication Codes (MACs) employing FIPS 140-2 approved cryptographic hash algorithms. | Stemcells have stronger Message Authentication Codes (MACs). |
| V-215130 | The Ubuntu operating system must be configured so that all network connections associated with SSH traffic terminate after a period of inactivity. | ClientAliveInterval is 300 instead of 600. ClientAliveCountMax is set to 1 instead of 0. The effective result of the 2 settings on the stemcell achieve the same result as advised by the STIG |
| V-215131 | The SSH daemon must not allow authentication using known hosts authentication. | Host based authentication is disabled on the stemcell. HostbasedAuthentication is set to “no” /etc/ssh/sshd_config. |
| V-215138 | An application firewall must protect against or limit the effects of Denial of Service (DoS) attacks by ensuring the Ubuntu operating system is implementing rate-limiting measures on impacted network interfaces. | Because IP addresses are dynamic in TAS, Uncomplicated Firewall (UFW) cannot be used to limit traffic between the hosts within TAS. Application Security Groups (ASGs) and perimeter firewalls for the TAS subnet are used instead. iptables is used where necessary. |
| V-215143 | Wireless network adapters must be disabled. | Not applicable for systems that do not have physical wireless network radios. Customers can install iwconfig to validate that there are no wireless network interfaces. |
| V-215156 | The Information System Security Officer (ISSO) and System Administrator (SA) (at a minimum) must have mail aliases to be notified of an audit processing failure. | Note: If postfix is not installed, this is Not Applicable. |
| V-215159 | If the Trivial File Transfer Protocol (TFTP) server is required, the TFTP daemon must be configured to operate in secure mode. | If a TFTP server is not installed, this is Not Applicable. |
| V-215161 | The Ubuntu operating system must have the packages required for multifactor authentication to be installed. | Stemcells do not support multi-factor authentication. |
| V-215162 | The Ubuntu operating system must accept Personal Identity Verification (PIV) credentials. | Stemcells do not support multi-factor authentication. |
| V-215163 | The Ubuntu operating system must implement certificate status checking for multifactor authentication. | Stemcells do not support multi-factor authentication. |
| V-215164 | The Ubuntu operating system, for PKI-based authentication, must validate certificates by constructing a certification path (which includes status information) to an accepted trust anchor. | This rule is for user certificate verification when using smart card based multi-factor authentication. Stemcells do not support multi-factor authentication. |
| V-215165 | The Ubuntu operating system must implement smart card logins for multifactor authentication for access to accounts. | BOSH deployed VMs do not have card readers. |
| V-214982 | A file integrity tool must be installed to verify correct operation of all security functions in the Ubuntu operating system. | Advanced Intrusion Detection Environment (AIDE) is not installed or configured on stemcells. VMware recommends installing File Integrity Monitoring Add-on for TAS for file monitoring. |
| V-214983 | The file integrity tool must perform verification of the correct operation of security functions: upon system start-up and/or restart; upon command by a user with privileged access; and/or every 30 days. | Advanced Intrusion Detection Environment (AIDE) is not installed or configured on stemcells. VMware recommends installing File Integrity Monitoring Add-on for TAS (FIM Add-on) for file monitoring.FIM Add-on and logs in real time. |
| V-214984 | The file integrity tool must be configured to verify Access Control Lists (ACLs). | Advanced Intrusion Detection Environment (AIDE) is not installed or configured on stemcells. VMware recommends installing File Integrity Monitoring Add-on for TAS for file monitoring. |
| V-214985 | The file integrity tool must be configured to verify extended attributes. | Advanced Intrusion Detection Environment (AIDE) is not installed or configured on stemcells VMware recommends installing File Integrity Monitoring Add-on for TAS for file monitoring. |
| V-214986 | The file integrity tool must notify the system administrator when changes to the baseline configuration or anomalies in the operation of any security functions are discovered. | Advanced Intrusion Detection Environment (AIDE) is not installed or configured on stemcells. VMware recommends installing File Integrity Monitoring Add-on for TAS (FIM Add-on) for file monitoring. FIM Add-on logs in real time. |
| V-214987 | The Ubuntu operating system must use cryptographic mechanisms to protect the integrity of audit tools. | Advanced Intrusion Detection Environment (AIDE) is not installed or configured on stemcells. VMware recommends installing File Integrity Monitoring Add-on for TAS for file monitoring. FIM Add-on is configured to monitor audit tools. |
| V-233624 | The Ubuntu operating system SSH daemon must prevent remote hosts from connecting to the proxy display. | BOSH VMs do not run GUI application. x11/xorg packages are not installed on BOSH VMs |
-
As of June 2021, Ubuntu Xenial stemcells are in Extended Security Maintenance (ESM). For more information, refer to the Ubuntu lifecycle and release cadence.
VMware has a commercial agreement with Canonical to continue providing secure and patched Xenial stemcells through April 2024, but only for Tanzu-related products.
VMware Tanzu only supports the stemcells available here: Stemcells (Ubuntu Xenial).
The Ubuntu Bionic stemcell is available here: Ubuntu Bionic (18.04).
Note: The Ubuntu Bionic stemcell is not supported by Tanzu-related products.