This topic explains how to configure single sign-on (SSO) between Azure Active Directory (Azure AD) and VMware Tanzu Kubernetes Grid Integrated Edition.
Prerequisites
To configure Azure AD to designate Tanzu Kubernetes Grid Integrated Edition as a service provider, you must have an Azure AD Global Administrator account.
Configure SAML in Azure AD
To configure Azure AD as a SAML identity provider for Tanzu Kubernetes Grid Integrated Edition, do the following:
-
Log in to Azure AD as a Global Administrator.
-
Navigate to Azure Active Directory.
-
Under Create, click Enterprise application.

-
Under Add your own app, select Non-gallery application. Enter a Name and click Add.
-
Navigate to Azure Active Directory > Enterprise applications.
-
Click your app and then click Single sign-on.
-
Under Select a single sign-on method, select SAML.

-
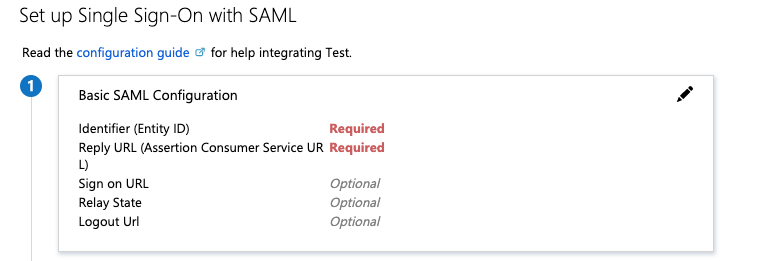
Under Set up Single Sign-On with SAML, click the pencil icon for Basic SAML Configuration.
-
Configure the following fields:
Field Instructions Identifier (Entity ID) Enter TKGI-API:8443.
For example:api.tkgi.example.com:8443
Reply URL Enter https://TKGI-API:8443/saml/SSO/alias/TKGI-API:8443.
For example:https://api.tkgi.example.com:8443/saml/SSO/alias/api.tkgi.example.com:8443Sign on URL Enter https://TKGI-API:8443/saml/SSO/alias/TKGI-API:8443.
For example:https://api.tkgi.example.com:8443/saml/SSO/alias/api.tkgi.example.com:8443Note: VMware recommends that you use the default settings for the fields that are not referenced in the above table.
-
Click the pencil icon for User Attributes & Claims.
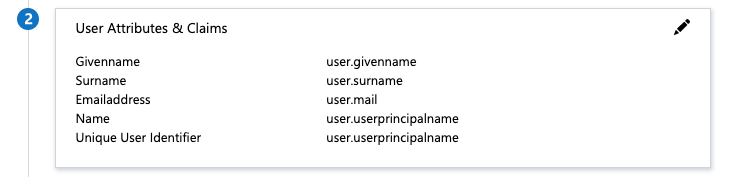
-
Configure your user attributes and claims by doing the procedures in How to: Customize claims issued in the SAML token for enterprise applications in the Microsoft Azure documentation. By default, Tanzu Kubernetes Grid Integrated Edition uses the
EmailAddressname identifier format. -
Configure your group attributes and claims by doing the procedures in the Configure group claims for SAML applications using SSO configuration section of Configure group claims for applications with Azure Active Directory (Public Preview) in the Microsoft Azure documentation.
-
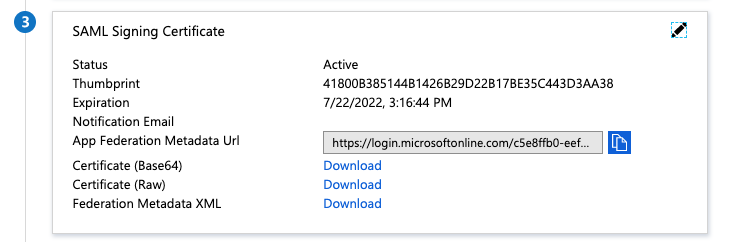
Under SAML Signing Certificate, copy and save the link address for App Federation Metadata Url or download Federation Metadata XML. You use the Azure AD metadata to configure SAML in the Tanzu Kubernetes Grid Integrated Edition tile. For more information, see Connecting Tanzu Kubernetes Grid Integrated Edition to a SAML Identity Provider.