This topic describes how to configure single sign-on (SSO) between Okta and VMware Tanzu Kubernetes Grid Integrated Edition (TKGI).
Prerequisites
To configure Okta to designate Tanzu Kubernetes Grid Integrated Edition as a service provider, you must have the following:
- An Okta Single-Sign On admin account
- An app with SAML 2.0 enabled in Okta
Configure SAML in Okta
To configure Okta as a SAML identity provider for Tanzu Kubernetes Grid Integrated Edition, do the following:
-
Log in to Okta as an admin.
-
Navigate to your app and click Sign On.
-
Under Settings, click Edit, and select SAML 2.0.
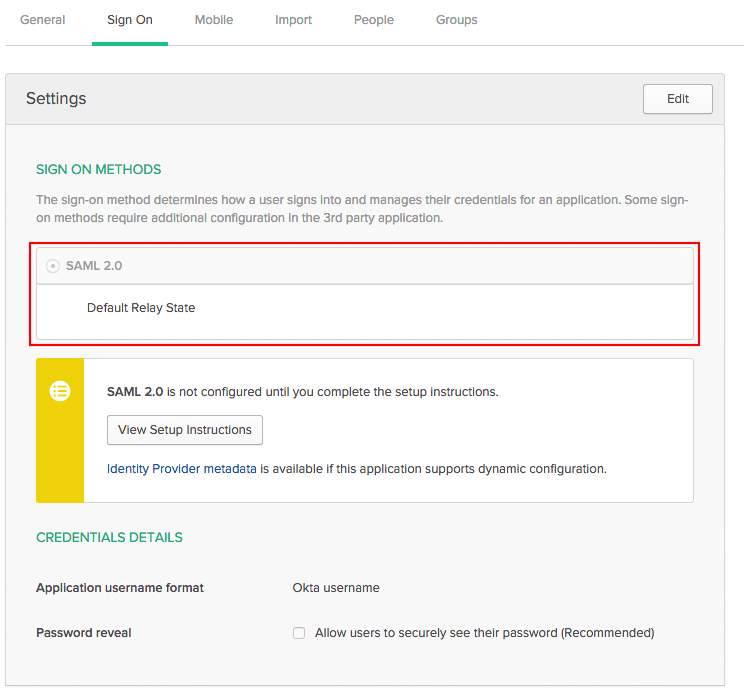
-
Click the General tab.
-
Under SAML Settings, click the Edit button followed by the Next button.
-
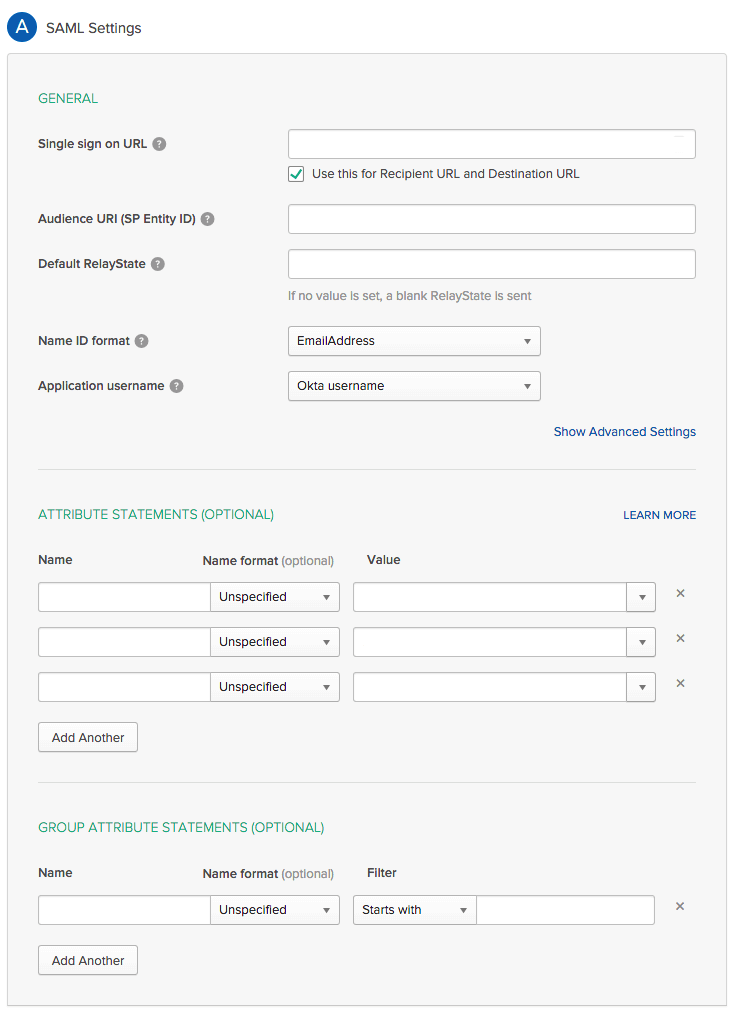
Configure the fields as follows:
Field Instructions Single sign on URL Enter https://TKGI-API:8443/saml/SSO/alias/TKGI-API:8443.
For example:https://api.tkgi.example.com:8443/saml/SSO/alias/api.tkgi.example.com:8443Use this for Recipient URL and Destination URL Ensure this check box is enabled. Audience URI (SP Entity ID) Enter TKGI-API:8443.
For example:api.tkgi.example.com:8443Name ID format Select a name identifier format. By default, Tanzu Kubernetes Grid Integrated Edition uses EmailAddress.Attribute Statements Enter any attribute statements that you want to map to users in the ID token.
In Tanzu Kubernetes Grid Integrated Edition you can define first name, last name, and email attributes.Group Attribute Statements Enter any group attribute statements that you want to map to users in the ID token. In Okta, these are groups that users belong to. You can use filters to define which groups are passed to Tanzu Kubernetes Grid Integrated Edition. Note: VMware recommends using the default settings for the fields that are not referenced in the above table.
-
Click the Next button followed by the Finish button.
-
(Optional) If you want to enable multi-factor authentication (MFA), you can add a SSO policy rule to your app. To enable MFA, do the procedure in Add Sign On policies for applications in the Okta documentation.
-
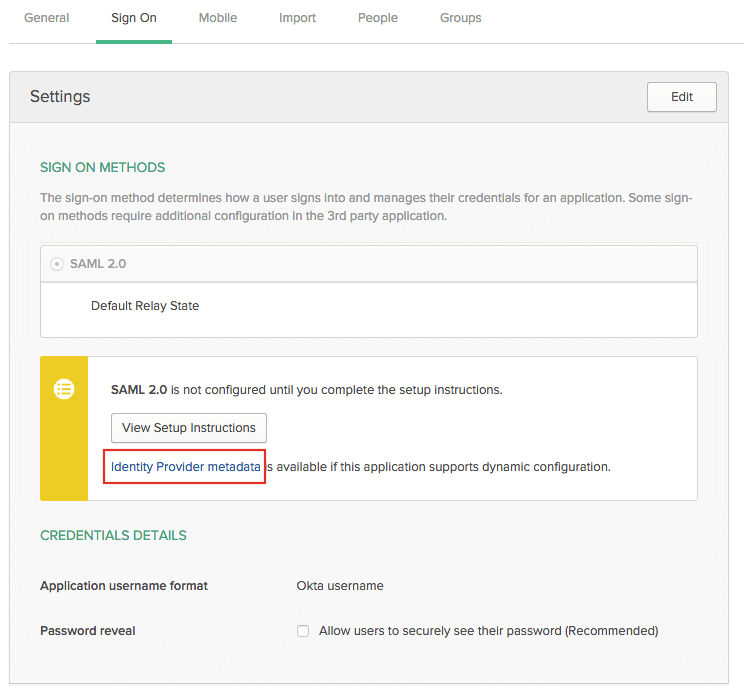
Click Identity Provider metadata to download the metadata, or copy and save the link address of the Identity Provider metadata.
-
Use the Okta metadata you retrieved in the above step to configure SAML in the Tanzu Kubernetes Grid Integrated Edition tile. See Connecting Tanzu Kubernetes Grid Integrated Edition to a SAML Identity Provider.