Topic provided by VMware
This topic describes how to enable the SecurityContextDeny admission controller for VMware Tanzu Kubernetes Grid Integrated Edition (TKGI) clusters.
Note: Support for SecurityContextDeny admission controller has been removed in TKGI v1.18. The SecurityContextDeny admission controller has been deprecated, and the Kubernetes community recommends the controller not be used. Pod security admission (PSA) is the preferred method for providing a more secure Kubernetes environment. For more information about PSA, see Pod Security Admission in TKGI.
About the SecurityContextDeny Admission Plugin
The SecurityContextDeny admission controller plugin will deny any pod that attempts to set certain escalating Security Context fields.
In Kubernetes, a security context defines privilege and access control settings for a pod or container. The securityContext field is a PodSecurityContext object. For more information, see Set the security context for a Pod in the Kubernetes documentation.
When to Enable the SecurityContextDeny Admission Plugin
The SecurityContextDeny admission plugin must be enabled if a cluster does not use pod security admission (PSA) to restrict the set of values a security context can take. See Pod Security Admission in TKGI for more information.
PSA is the preferred method for providing a more secure Kubernetes environment. However, PSA has administrative overhead. Enabling the SecurityContextDeny is a stopgap method of providing a more secure Kubernetes environment when it is not feasible to use PSA. If you plan to use PSA in the future, consider enabling the SecurityContextDeny admission plugin as an interim security measure.
Impact of Enabling the SecurityContextDeny Admission Plugin
This section describes the impact of enabling the SecurityContextDeny admission control plugin for new and existing cluster plans.
New Cluster. If you enable the SecurityContextDeny admission plugin in a plan and deploy a new Kubernetes cluster based on that plan, cluster users will not be able to create securityContext capabilities on that cluster.
Existing Cluster. If you enable the SecurityContextDeny admission plugin in a plan and update a Kubernetes cluster, cluster users will no longer be able to create securityContext capabilities on that cluster. This assumes you enable Upgrade all clusters errand or update your cluster individually through the TKGI Command Line Interface (TKGI CLI).
Enabling the SecurityContextDeny Admission Plugin
To enable the SecurityContextDeny admission plugin:
- In the TKGI tile, select the desired Plan, such as Plan 1.
- At the bottom of the configuration panel, select the SecurityContextDeny option.
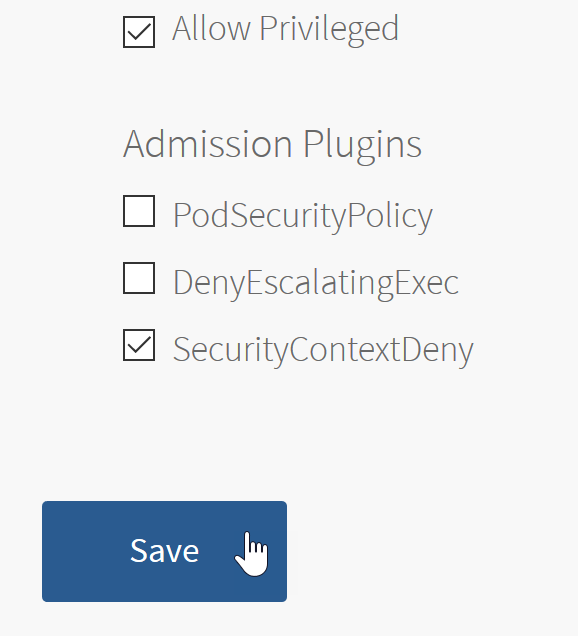
- Click Save.
- On the Installation Dashboard, click Review Pending Changes.
- For Tanzu Kubernetes Grid Integrated Edition, verify that Upgrade all clusters errand is enabled.
- Click Apply Changes to deploy the cluster with the admission plugin enabled.
Alternatively, instead of enabling Upgrade all clusters errand, you can upgrade individual Kubernetes clusters through the TKGI Command Line Interface (TKGI CLI). For instructions on upgrading individual Kubernetes clusters, see Upgrading Clusters.