Identity and Access Management
The topics in this section explain how to configure identity and access management in Tanzu Kubernetes Grid (TKG) with a standalone management cluster.
To enable and configure identity and access management, follow the topics linked below:
About Identity and Access Management
Tanzu Kubernetes Grid (TKG) uses Pinniped to implement authentication and authorization for identity and access management.
Authentication
Tanzu Kubernetes Grid implements user authentication with Pinniped, an open-source authentication service for Kubernetes clusters. Pinniped allows you to plug external OpenID Connect (OIDC) or LDAP identity providers (IdP) into workload clusters, so that you can control user access to those clusters. Pinniped runs automatically as in-cluster services in your management clusters if you enable identity management. For instructions on how to enable identity management in Tanzu Kubernetes Grid, see Configure Identity Management.
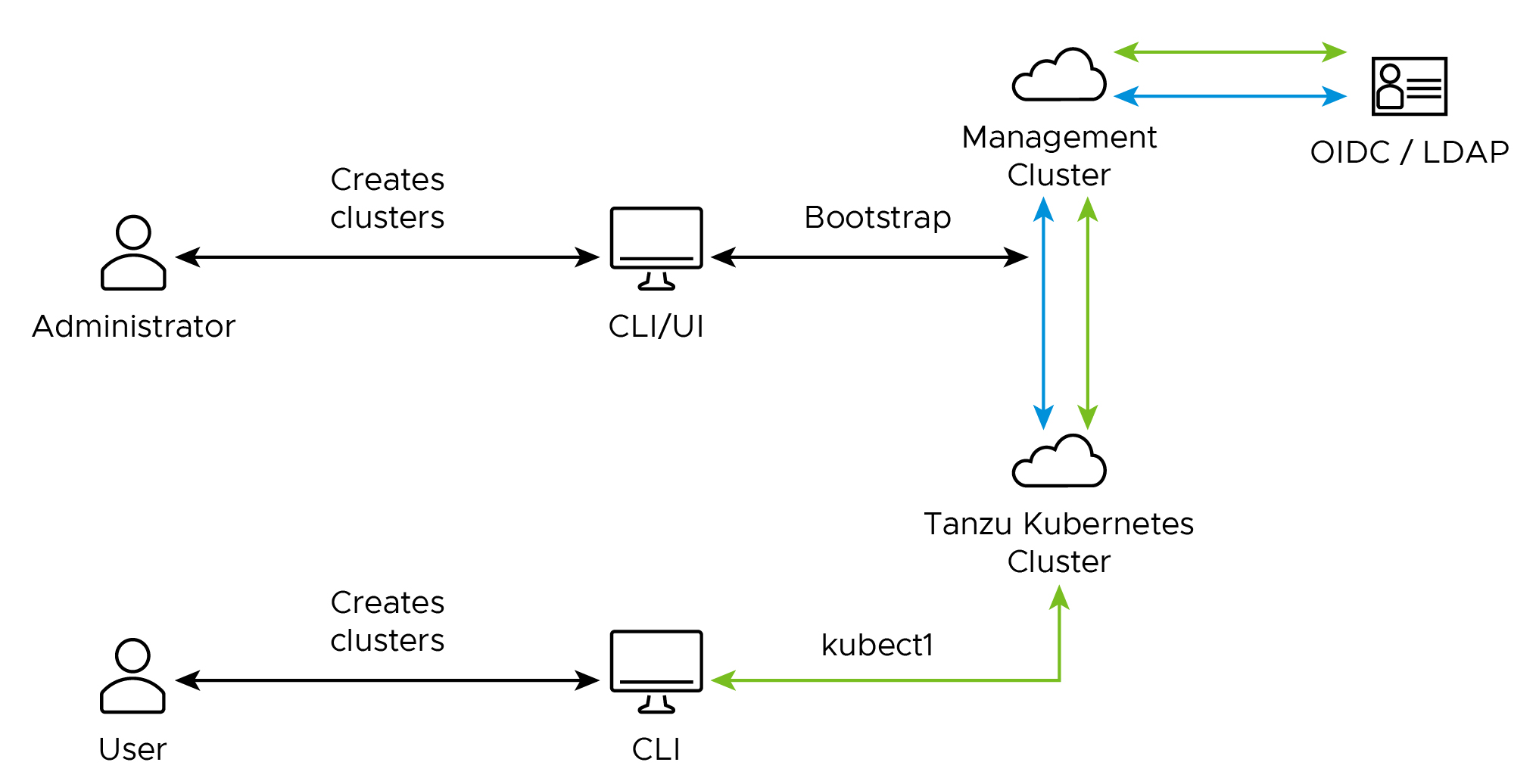
The authentication flow between the management and workload clusters includes the following:
- The Tanzu Kubernetes Grid administrator enables and configures identity management on the management cluster, specifying an external LDAP or OIDC IdP.
- Authentication service components are deployed into the management cluster, using the LDAP or OIDC IdP details specified by the administrator.
- The administrator creates a workload cluster. The workload cluster inherits the authentication configuration from the management cluster.
- The administrator creates a role binding to associate a given user with a given role on the workload cluster.
- The administrator provides the
kubeconfigfor the workload cluster to the user. - A user uses the
kubeconfigto connect to the workload cluster, for example, by runningkubectl get pods --kubeconfig. - The management cluster authenticates the user with the IdP.
- The workload cluster either allows or denies the
kubectl get podsrequest, depending on the permissions of the user’s role.
In the image below, the blue arrows represent the authentication flow between the workload cluster, the management cluster, and the external IdP. The green arrows represent Tanzu CLI and kubectl traffic between the workload cluster, the management cluster, and the external IdP.
Identity Management Components
The diagram below shows the identity management components that Tanzu Kubernetes Grid deploys in the management cluster and in workload clusters when you enable identity management.
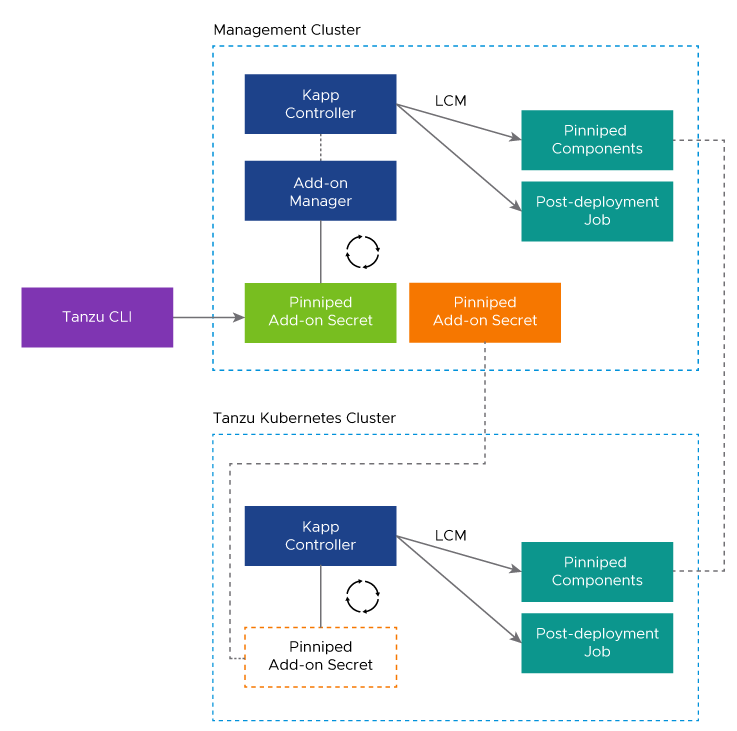
Understanding the diagram:
-
The teal rectangles show the identity management components, which include Pinniped and a post-deployment job in the management cluster and Pinniped and a post-deployment job in the workload cluster.
-
The dark blue rectangles show the components that Tanzu Kubernetes Grid uses to control the lifecycle of the identity management components, which include
tanzu-addons-managerandkapp-controller. -
The light green rectangle shows the Pinniped add-on secret created for the management cluster.
-
The orange rectangle in the management cluster shows the Pinniped add-on secret created for the workload cluster. The secret is mirrored to the workload cluster.
Internally, Tanzu Kubernetes Grid deploys the identity management components as an auto-managed package, pinniped. This package contains the pinniped add-on. When you deploy a management cluster with identity management enabled or enable it as a post-deployment step, the Tanzu CLI creates a Kubernetes secret for the pinniped add-on in the management cluster. tanzu-addons-manager reads the secret, which contains your IdP configuration information, and instructs kapp-controller to configure the pinniped add-on using the configuration information from the secret.
The Tanzu CLI creates a separate pinniped add-on secret for each workload cluster that you deploy from the management cluster. All secrets are stored in the management cluster. For more information, see Auto-Managed Packages.
Authorization
Tanzu Kubernetes Grid uses role-based access control (RBAC) authorization. For instructions on how to configure RBAC, see Configure RBAC.