VMware Tanzu Operations Manager supports Amazon Elastic Block Store (EBS) encryption for Tanzu Operations Manager deployments on AWS. You can use this feature to meet data-at-rest encryption requirements or as a security best practice.
This feature uses AWS Key Management Service (KMS).
Enabling EBS encryption only encrypts Linux VMs. The Microsoft Windows VMs deployed with VMware Tanzu Application Service for VMs (TAS for VMs) for Windows are not encrypted.
By following the procedures in this topic, you can use full disk encryption for all persistent disks on the following VMs:
- BOSH and all present and future VMs
- The Tanzu Operations Manager VM
There is no performance penalty for using encrypted EBS volumes. VMware recommends that all users of Tanzu Operations Manager on AWS enable encryption.
Before you enable EBS encryption with KMS, you might need to update your AWS policy. For more information, see Add additional AWS policies.
Enable encryption for BOSH Director
To enable EBS encryption:
-
Go to Tanzu Operations Manager Installation Dashboard.
-
Click the BOSH Director tile.
-
Click AWS Config to open the AWS Management Console Config pane.
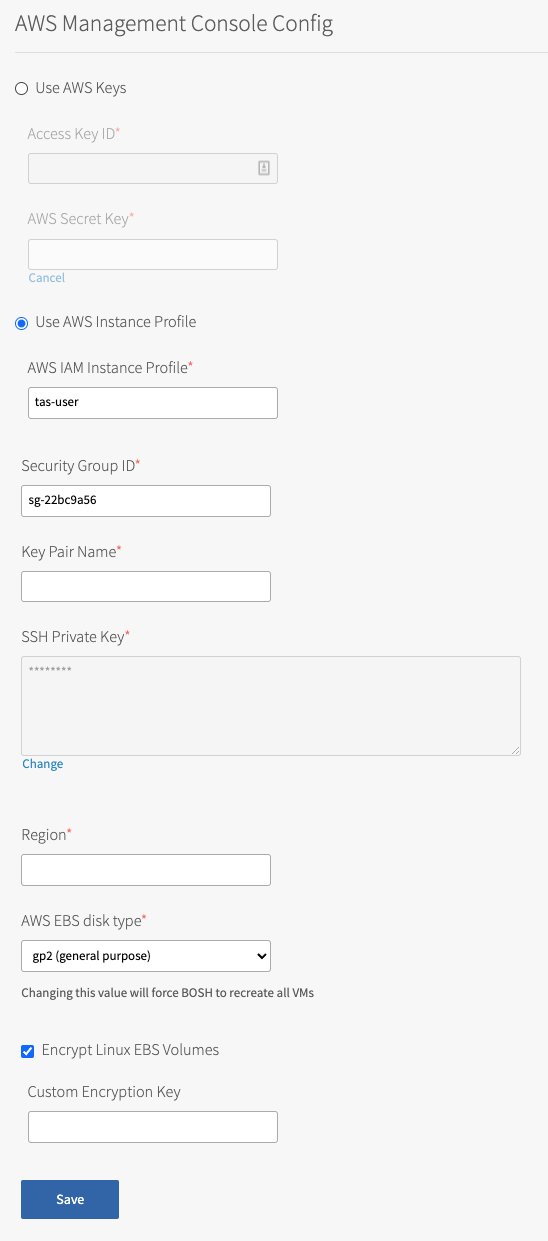
-
Select the Encrypt Linux EBS Volumes check box.
Encrypt Linux EBS Volumes is a global setting. When enabled, the Encrypt Linux EBS Volumes check box enables encryption on all Linux VMs deployed by BOSH for all product tiles. Windows VMs are not encrypted.
-
(Optional) Enter a Custom Encryption Key. You can create an encryption key in the IAM section of your AWS Management Console. Look for the Amazon Resource Name (ARN) and copy that value. The ARN must look similar to the following:
arn:aws:kms:us-east-1:123456789012:
key/12345678-9012-3456-7890-123456789012 ``` If you leave the text box blank, the encryption key defaults to the Amazon account key. For more information about creating your own encryption key, see Creating Keys and Viewing Keys in the AWS documentation.
<p> AWS rotates your KMS automatically each year. For more information, see <a href="https://docs.aws.amazon.com/kms/latest/developerguide/rotate-keys.html">Rotating AWS KMS Keys</a> in the AWS Documentation.</p>
-
Click Save.
-
(Optional) Ignore this series of steps if you are making your first deployment. Otherwise, you need to reset your VMs so that they can encrypt Linux EBS volumes. To encrypt all current BOSH and BOSH-deployed VMs:
If you need help with the following advanced steps, contact Support.
- Encrypt the BOSH Director VM:
- SSH into the Tanzu Operations Manager VM with the BOSH CLI. For more information about SSHing with BOSH, see BOSH SSH in Advanced Troubleshooting with the BOSH CLI.
- Go to the
/var/tempest/workspaces/default/deploymentsdirectory in the SSHed Tanzu Operations Manager VM. - Back up your
bosh-state.jsonfile elsewhere in case you want to restore the file. - Edit
bosh-state.jsonto removecurrent_stemcell_idandstemcellsvalues. For example, enter"current_stemcell_id": ""and"stemcells": [].
- Encrypt BOSH-created VMs:
- Enter the
bosh stemcellsandbosh deploymentscommands into the command line. Record the stemcell names that BOSH-deployed VMs are using. Encrypt BOSH-deployed VMs - Go to the
var/tempest/stemcellsfolder in the SSHed Tanzu Operations Manager VM. - Enter the
bosh upload-stemcell STEMCELL_NAME --fixcommand into the command line for each stemcell to enforce the BOSH Director, encrypt the stemcells, and re-upload them.
- Enter the
- Reset Persistent Disks and Recreate VMs:
- Click Director Config.
- Enable Recreate VMs deployed by the BOSH Director.
- Enable Recreate BOSH Director VM.
- Enable Recreate All Persistent Disks.
- Click Save.
- Encrypt the BOSH Director VM:
-
Return to the Tanzu Operations Manager Installation Dashboard.
-
Click Review Pending Changes.
-
Click Apply Changes and review any reported errors. The following example error message lists jobs that cannot be encrypted due to unsupported instance types.
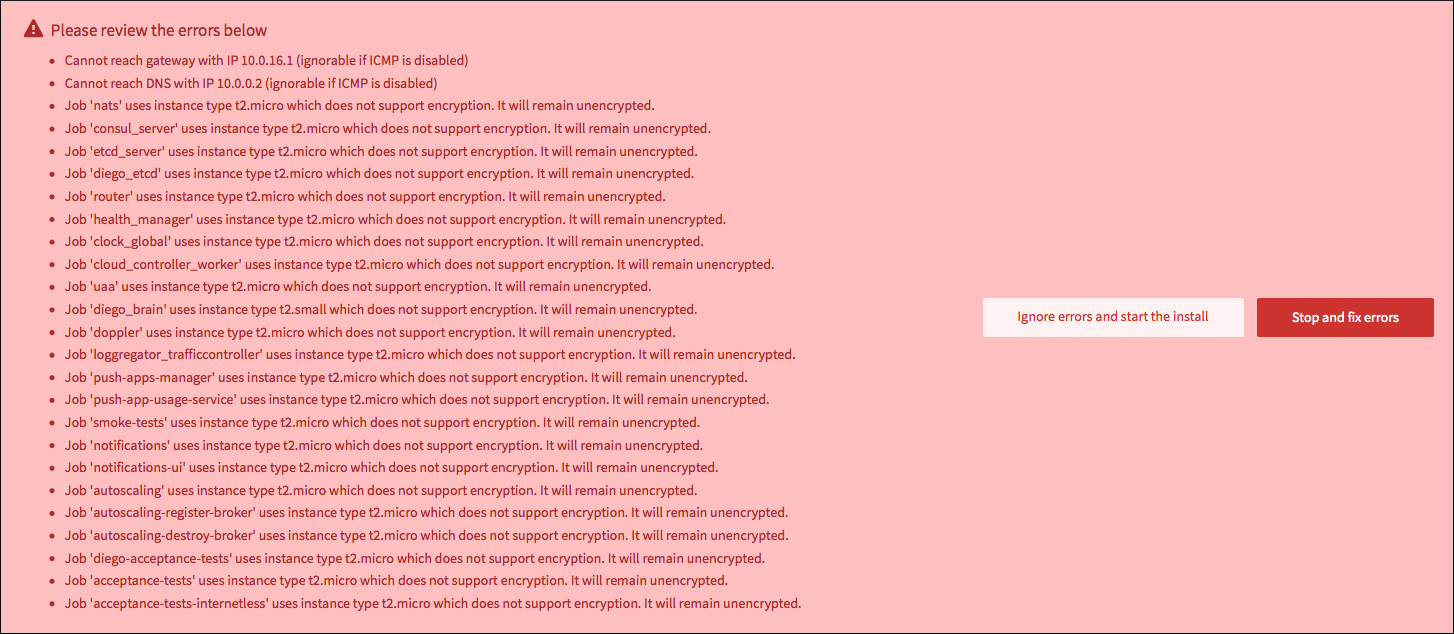
If you find a job that can be encrypted in the error list, modify the instance type for that job in the Resource Config page of the TAS for VMs tile. Select an instance type that supports encryption. VMware recommends using
t3.large. -
After you make your changes in TAS for VMs, return to the Tanzu Operations Manager Installation Dashboard.
-
Click Review Pending Changes.
-
Click Apply Changes.
After you activate or deactivate the Encrypt Linux EBS Volumes check box, click Review Pending Changes, and click Apply Changes, Tanzu Operations Manager recreates all existing persistent VM disks.
Enable encryption for Tanzu Operations Manager
To encrypt the Tanzu Operations Manager VM, you must manually re-launch Tanzu Operations Manager with a new Amazon Machine Image (AMI). For more information, see Step 1: Launch a Tanzu Operations Manager AMI in Deploying Tanzu Operations Manager on AWS.