This topic describes how you can customize role-based access control (RBAC) in VMware Tanzu Operations Manager to manage which operators in your organization can make deployment changes, view credentials, and manage user roles.
For information about configuring Tanzu Operations Manager to use internal authentication or SAML authentication, see the BOSH Manager configuration topic for your IaaS:
Roles in Tanzu Operations Manager
The following graphic illustrates the roles you can assign to determine which operators in your organization make deployment changes, view credentials, and manage user roles in Tanzu Operations Manager. Full details are also shown in the following table.
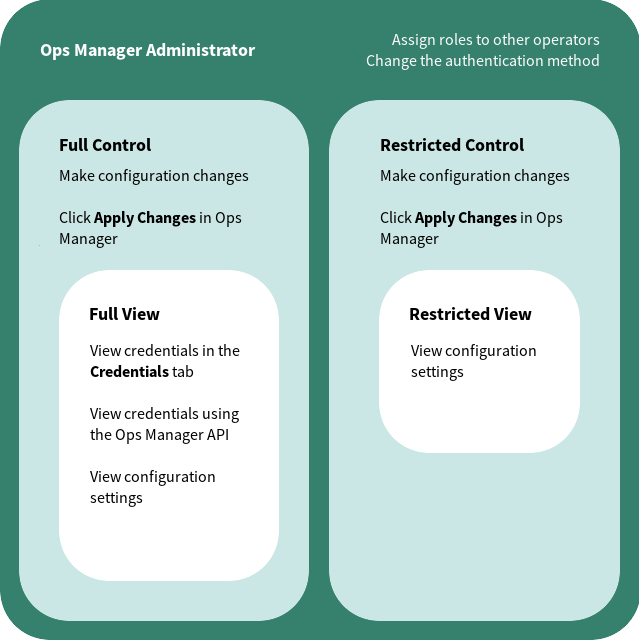
Tanzu Operations Manager admins can use these roles to meet the security needs of their organization. The roles provide a range of privileges that are appropriate for different types of users. For example, assign either Restricted Control or Restricted View to an operator to prevent access to all Tanzu Operations Manager credentials.
For more information about each role, see the following table:
| Tanzu Operations Manager Role | Role Definition | UAA Scope |
|---|---|---|
| Tanzu Operations Manager Administrator | Admins can make configuration changes, click Review Pending Changes and Apply Changes in Tanzu Operations Manager, view credentials in the Credentials tab and Tanzu Operations Manager API endpoints, change the authentication method, and assign roles to other operators. | opsman.admin |
| Full Control | Operators can make configuration changes, click Review Pending Changes and Apply Changes in Tanzu Operations Manager, and view credentials in the Credentials tab and Tanzu Operations Manager API endpoints. | opsman.full_control |
| Restricted Control | Operators can make configuration changes and click Review Pending Changes and Apply Changes in Tanzu Operations Manager. They cannot view credentials in the Credentials tab or Tanzu Operations Manager API endpoints. | opsman.restricted_control |
| Full View | Operators can view Tanzu Operations Manager configuration settings and view credentials in the Credentials tab and Tanzu Operations Manager API endpoints. They cannot make configuration changes or click Apply Changes. | opsman.full_view |
| Restricted View | Operators can view Tanzu Operations Manager configuration settings. They cannot make configuration changes or view credentials in the Credentials tab or Tanzu Operations Manager API endpoints. | opsman.restricted_view |
To assign one of the preceding roles to an operator, see Manage roles with internal authentication or Manage roles with SAML authentication.
When you install a new Tanzu Operations Manager instance, all existing users have the Tanzu Operations Manager Administrator role by default.
Simultaneous Tanzu Operations Manager admins
Tanzu Operations Manager allows multiple admins to log in to Tanzu Operations Manager simultaneously and make changes.
The interface does not provide visibility to other admins who are logged in. VMware recommends that admins communicate with each other and coordinate their changes.
Precedence for Apply Changes
If two admins are working at the same time, the admin who first clicks Apply Changes takes precedence. Tanzu Operations Manager overwrites all configurations made by other admins during deployment.
VMware recommends coordinating changes between admins to avoid overwriting configurations.
If you are having deployment issues or changes to your Tanzu Operations Manager are not persisting correctly, confirm that your work is not conflicting with an automated admin.
Enable RBAC in Tanzu Operations Manager after upgrade
When you install a new instance of Tanzu Operations Manager, RBAC is permanently enabled by default.
If your organization has operators who are devoted to managing certain services like VMware Tanzu SQL [MySQL], you can use RBAC to assign those services operators a more restricted role.
If you upgrade from an older Tanzu Operations Manager instance, you must enable RBAC and assign roles to users before they can access Tanzu Operations Manager. If you do not assign any roles to a user, they cannot log in to Tanzu Operations Manager.
Do not assign roles before you enable RBAC. Changing UAA authentication settings causes deletion of the roles.
Enable RBAC with internal authentication
If you upgrade from an earlier version of Tanzu Operations Manager and use internal authentication:
-
Log in to the Tanzu Operations Manager Installation Dashboard.
-
From the user account menu, click Settings.
-
Click Advanced.
-
Click Enable RBAC. When the confirmation dialog box appears, click Confirm and Logout.
Enabling RBAC is permanent. You cannot undo this action. When you upgrade Tanzu Operations Manager, your RBAC settings remain configured. This dialog does not appear if RBAC is already configured. With new instances of Tanzu Operations Manager, RBAC is permanently configured by default.
Enable RBAC with SAML authentication
If you upgrade from an earlier version of Tanzu Operations Manager and are using SAML authentication, follow the procedures in these sections to enable RBAC. To enable RBAC in Tanzu Operations Manager when using SAML authentication, you must configure groups in SAML for admins and non-admins, and then map the admin group to Tanzu Operations Manager.
Step 1: Configure SAML groups
To gather information from your SAML dashboard:
-
Log in to your SAML provider dashboard.
-
Create or identify the name of the SAML group that contains Tanzu Operations Manager admin users.
-
Identify the groups attribute tag you configured for your SAML server.
Step 2: Enable RBAC in Tanzu Operations Manager
Follow the procedure in Enable RBAC with internal authentication to configure Tanzu Operations Manager to recognize your SAML admin user group.
When RBAC is enabled, only users with the Tanzu Operations Manager Administrator role can edit the SAML configuration.
Create user accounts in Tanzu Operations Manager
To assign RBAC roles to operators, you must first create user accounts for them.
In addition to user accounts, you can create a client account to add to Tanzu Operations Manager. Client accounts manage automation tasks, such as upgrade scripts, log management, and other behaviors that might be negatively impacted if managed by a user account. You can add a client account either before initial deployment or to an existing deployment.
For more information about user and client accounts, see Creating and managing Tanzu Operations Manager user and client accounts.
Manage RBAC roles in Tanzu Operations Manager
You can assign the roles defined in Roles in Tanzu Operations Manager to determine which operators in your organization can make deployment changes, view credentials, and manage user roles in Tanzu Operations Manager.
Manage roles with internal authentication
If you configured Tanzu Operations Manager to use internal authentication, you can configure roles using the UAA Command Line Interface (UAAC). For more information, see Creating and managing users with the UAA CLI (UAAC).
To use the UAAC to configure roles:
-
Target your UAA server and log in as an admin by running:
uaac target https://OPS-MANAGER-DOMAIN/uaa uaac token owner getWhere
OPS-MANAGER-DOMAINis the domain of your Tanzu Operations Manager deployment. -
When prompted, enter these credentials, leaving Client secret blank:
Client ID: opsman Client secret: User name: USERNAME Password: PASSWORDWhere:
USERNAMEis your user name.PASSWORDis your password.
-
To assign a role to a user, run one of these commands:
-
Tanzu Operations Manager Administrator:
uaac member add opsman.admin USERNAMEWhere
USERNAMEis the user to which you want to assign the role. -
Full Control:
uaac member add opsman.full_control USERNAMEWhere
USERNAMEis the user to which you want to assign the role. -
Restricted Control:
uaac member add opsman.restricted_control USERNAMEWhere
USERNAMEis the user to which you want to assign the role. -
Full View:
uaac member add opsman.full_view USERNAMEWhere
USERNAMEis the user to which you want to assign the role. -
Restricted View:
uaac member add opsman.restricted_view USERNAMEWhere
USERNAMEis the user to which you want to assign the role.
-
Manage roles with SAML authentication
If you configured Tanzu Operations Manager with SAML authentication, you can assign non-admin user roles using UAAC. To assign non-admin user roles:
-
Target your UAA server and log in as an admin by running:
uaac target https://OPS-MANAGER-DOMAIN/uaa uaac token sso getWhere
OPS-MANAGER-DOMAINis the domain of your Tanzu Operations Manager deployment. -
When prompted, enter Client ID and Passcode, leaving Client secret blank:
Client ID: opsman Client secret: Passcode: UAA-PASSCODEWhere
UAA-PASSCODEis the passcode you retrieved in the previous step. -
Run:
uaac group map SAML-GROUP --name 'OPS-MANAGER-SCOPE' --origin 'saml'Where:
SAML-GROUPis the name of the SAML group to which the user belongs.OPS-MANAGER-SCOPEis the Tanzu Operations Manager UAA scope you want to assign to the user. To determine which UAA scope to use, see the table in Roles in Tanzu Operations Manager.
-
Add new and existing users to the appropriate SAML groups in the SAML provider dashboard. Users must log out of both Tanzu Operations Manager and the SAML provider for role changes to take effect.
Manage roles with LDAP authentication
If you configured Tanzu Operations Manager with LDAP authentication, you can assign non admin user roles using UAAC. To assign non-admin user roles:
-
Target your UAA server and log in as an admin by running:
uaac target https://OPS-MANAGER-DOMAIN/uaa uaac token sso getWhere
OPS-MANAGER-DOMAINis the domain of your Tanzu Operations Manager deployment. -
When prompted, enter Client ID and Passcode, leaving Client secret blank:
Client ID: opsman Client secret: Passcode: UAA-PASSCODEWhere
UAA-PASSCODEis the passcode you retrieved in the previous step. -
Run:
uaac group map LDAP-GROUP --name 'OPS-MANAGER-SCOPE'Where:
LDAP-GROUPis the name of the LDAP group to which the user belongs.OPS-MANAGER-SCOPEis the Tanzu Operations Manager UAA scope you want to assign to the user. To determine which UAA scope to use, see the table in Roles in Tanzu Operations Manager.
-
Add new and existing users to the appropriate LDAP groups in the LDAP provider dashboard. You must log out of both Tanzu Operations Manager and the LDAP provider for role changes to take effect.