Integrate Mutual TLS and Ingress Capabilities with a third-party certificate authority (CA)
You can integrate mutual TLS and ingress with third-party certificate authorities for certificate management to enable secure service-to-service communication within a Space and user-to-service communication into a Space.
Integrate the Vault certificate authority
To integrate the Vault CA:
- In Tanzu Platform hub, scroll down to Application Platform.
- Go to Application Spaces > Capabilities.
- Click on the Capability Ingress.
- Select the cluster group to which you want to install the Capability.
-
Select Advanced Configuration > YAML to enter Vault endpoint details.
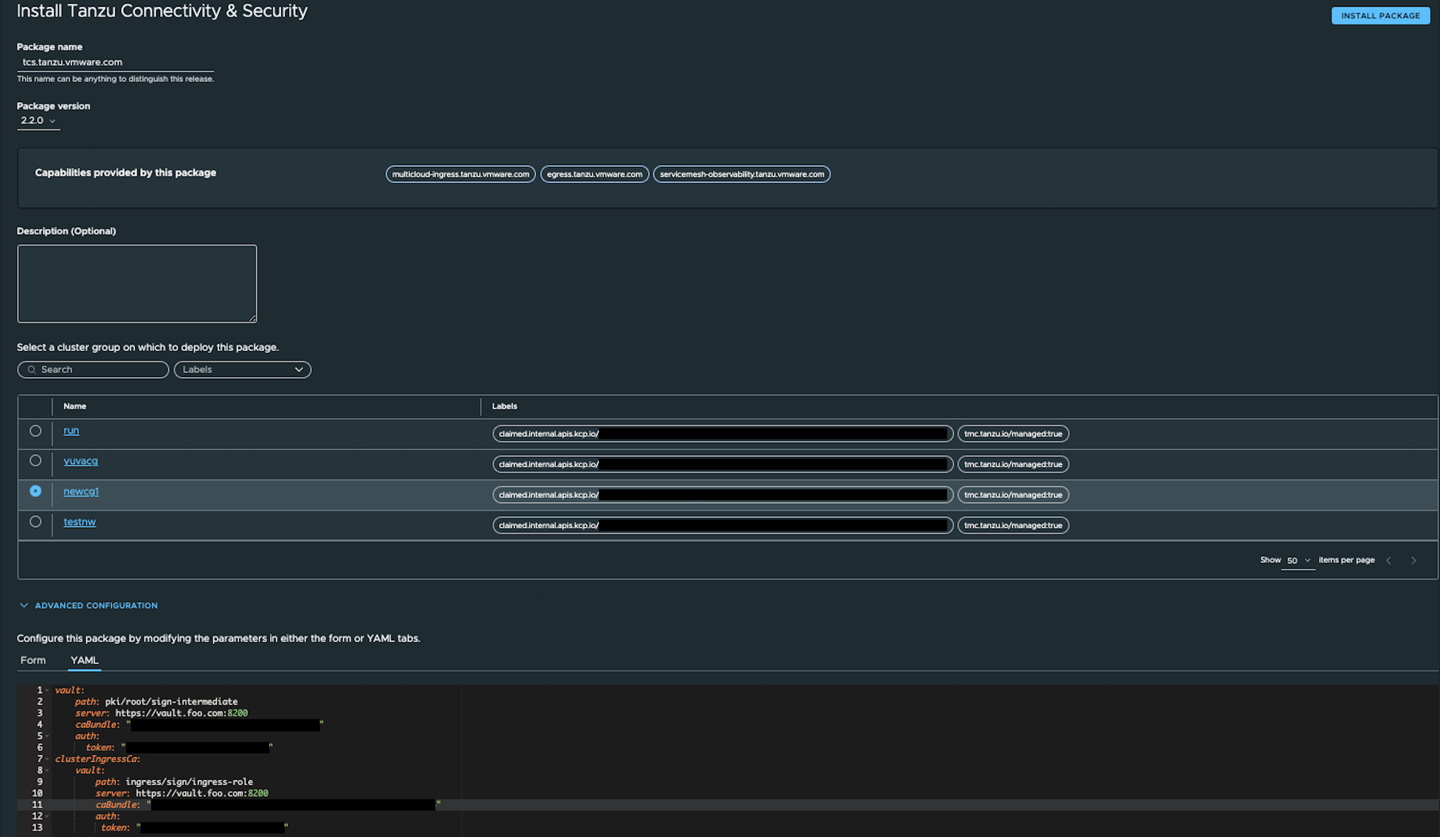
Sample Input for vault CA:
# This vault section is considered for mTLS vault: # path: signing endpoint path. Here 'root' is fixed. path: pki/root/sign-intermediate # server: URL where vault CA is hosted server: https://vault.foo.com:8200/ # caBundle: Required if server endpoint is with https caBundle: <base64 encoded ca bundle> # auth: Token/Secret for API access auth: token: <base64 encoded api access token> # This clusterIngressCa:vault section is considered for ingress TLS clusterIngressCa: vault: # path: signing endpoint path. Here 'sign' is fixed. path: ingress/sign/ingress-role # server: URL where vault CA is hosted server: https://vault.foo.com:8200/ # caBundle: Required if server endpoint is with https caBundle: <base64 encoded ca bundle> # Required if server endpoint is with https # auth: Token/Secret for API access auth: token: <base64 encoded api access token> -
Click Install Package.
Integrate a Space-managed self-signed certificate
By default, a Space-managed self-signed certificate is considered for mTLS when the Ingress Capability is deployed without any CA credentials input. To integrate a Space-managed self-signed certificate:
- In Tanzu Platform hub, scroll down to Application Platform.
- Go to Application Spaces > Capabilities.
- Click on the Capability Ingress.
- Select the cluster group to which you want to install the Capability.
- Click Install Package.