Use case: How do I deploy minions using the API in a Windows environment
The goal of this use case is to programmatically install the Salt minion service on a minion by connecting a Windows VM to your Tanzu Salt environment.
Prerequisites
Before you can deploy a minion using the API in a Windows environment you must:
- Have a Tanzu Salt environment with RaaS deployed.
- Have a Salt master and Salt minion installed.
- Have a Windows VM deployed.
Procedure
-
Verify that the folder etc/salt/cloud.deploy.d on the Salt master contains these files.
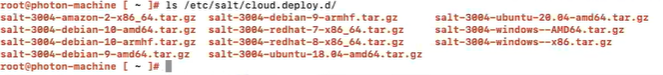
If you do not see the files, contact support.
Note:
Thexxxxin the filename, for example,salt-xxxx-windows–x86.tar.gz, should match the version of the Salt master. To verify the version of the Salt master, run thesalt-master -Vcommand on the Salt master. -
If your environment is air-gapped, complete these steps:
-
Open the RaaS configuration file in
/etc/raas/raas. -
Add these lines to the configuration file:
minion_deployment: airgap_install: true -
Restart the RaaS service using the
service raas restartcommand.Note:
If you are using a hardened Linux VM, there are some situations where scripts cannot be run from/tmpon the VM.- If you are using Automation Assembler version 8.10.2 or higher: Add the
additionalAuthParamsproperty to the Tanzu Salt resource in your cloud template. For more information, see Add the SaltStack resource to the cloud template.
additionalAuthParams: profile: tmp_dir: /var/cache/salt- If you are using Automation Assembler version 8.10.1 or lower: Modify the
/etc/salt/cloud.providers.d/ssc\_saltify\_provider.conffile with
ssc_saltify_provider: driver: saltify tmp_dir: /var/cache/saltIf this configuration file does not exist, create it and add the setting above.
- If you are using Automation Assembler version 8.10.2 or higher: Add the
-
-
In the Salt master’s terminal, install the following libraries by running the
pip3 install pypsexec smbprotocolandpip3 install impacket --ignore-installedcommands. -
To identify the FQDN of the Salt master, run the
salt saltmaster grains.get fqdncommand in the Salt master’s terminal. -
On your Windows machine, verify that the
C: \Windows\System32\drivers\etc\hostsfile is configured with the Salt master’s IP and FQDN. -
Open PowerShell on the Windows machine and run the following command to open the required ports:
Port Commands 445 New-NetFirewallRule -Name “SMB445” - DisplayName “SMB445” -Protocol TCP - LocalPort 445``Enable-Psremoting -
In the Salt master’s terminal, use this command to open ports 4505 and 4506 on the Salt master:
Port Commands 4505-4506 netsh advfirewall firewall add rule name=“Salt” dir=in action=allow protocol=TCP localport=4505-4506See Understanding SaltStack for more information about the Salt communication model.
-
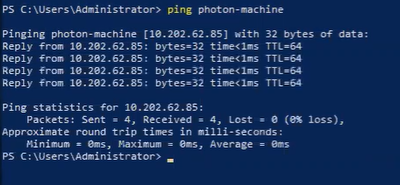
Ensure that the FQDN is configured for the Salt master by running the ping [FQDN] command on your Windows machine.
-
Make this API call using an SSEAPI client with the correct credentials for your environment.
Note:
If you integrated Tanzu Salt with VMware Aria Automation, the VMware Aria Automation service makes this API call for you when you deploy minions using a cloud template.from sseapiclient import APIClient client = APIClient('https://<master-ip>', '<ssc-username>', '<sscpassword>', ssl_validate_cert=False) client.api.minions.deploy_minion( master_id = '<master-id>', host_name_ip = '<prospective minion’s ip>', os = ‘<prospective minion’s os>’, minion_id = '<desired-minion-name-for-prospective-minion>', username = '<ssh-username-for-prospective-minion>', password = '<ssh-password-for-prospective-minion>', )The
deploy.minionfunction begins running in your Tanzu Salt environment. You can verify that the job is running in the Activity tab of the Tanzu Salt user interface or by running the python3 command, followed byclient.api.minions.get_minion_deployments().
The minion was successfully deployed and configured from your Windows environment and API call.
Verify that the minion was deployed successfully by running a test.ping command against the minion using the Run Command window or by running the \\* test.ping and \\* test.versions commands in the Salt master command window.