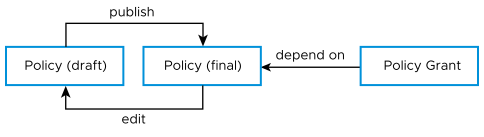
A Kubernetes policy defines a set of permissions that are required in addition to the Read-Write access to the namespaces of the CNF. As a user with access to the CNF package, you can create a policy. When you create a policy, you only define the requirement for specific permissions. The virtual infrastructure administrator grants permission by creating a policy grant. A policy grant links the policy and VIM with a CNF package. A policy grant may also link with a specific CNF instance or a CNF LCM operation.
| Privilege | Policy Template | Policy Grant |
|---|---|---|
| System Administrtor | Read-Write | Read-Write |
| Virtual Infrastructure Administrtor | Read-Write | Read-Write |
| Virtual Infrastructure Audit | Read-Write | Read-Only |
| Virtual Infrastructure Consume | Read-Write | Read-Only |
- The draft policy is automatically deleted if you do not finalize it before the expiration date.
- After granting a policy, it can no longer be edited or deleted.
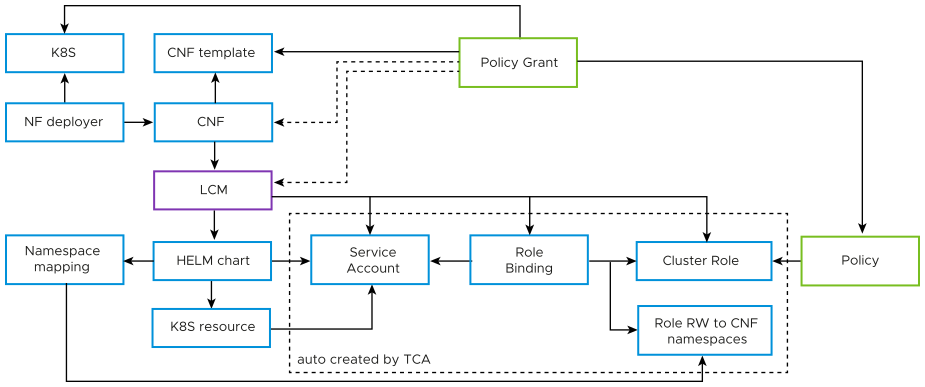
The policy and policy grant are used during LCM operations to prepare the context in which HELM is executed. Before executing a HELM operation, TCA creates or updates a service account and its corresponding roles, cluster roles, or role bindings to represent a context in which the CNF should be running. Based on policies and policy grants, TCA creates a set of CNF-specific roles or cluster roles and role bindings. These will make it possible for the service account to access global resources. Roles are created based on HELM to namespace mapping in the instantiated VNF to provide Read-Write access to the namespaces in which the CNF resides. These service accounts reside on a TCA-specific namespace and are labeled with the policy grant ID or the CNF instance ID. Proper labeling of the service accounts allows you to update or delete them when you no longer require them.