The CNF global permission enforcement system allows you to assign and enforce global permissions.
CNF permission enforcement aims at running the HELM commands in the context of a restricted service account. This restricted service account requires minimum permissions to perform the LCM operations. The limited-service account created based on namespace access only might not be adequate as it does not provide access to cluster-level resources.
The following diagram illustrates the CNF permission enforcement system.
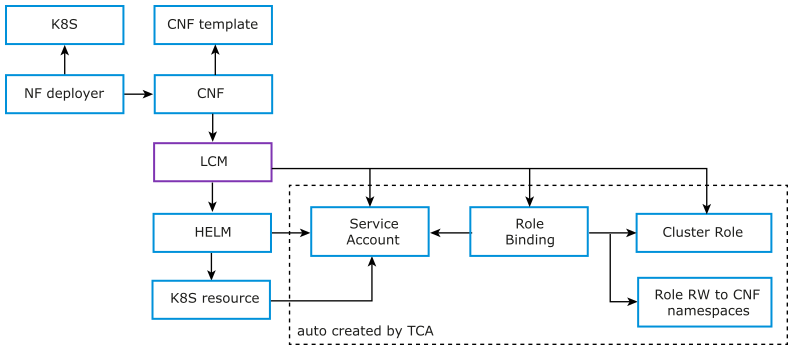
An LCM operation comprises the following steps:
- TCA communicates with the target VIM and preconfigures it if required.
- TCA creates a service account with the necessary permissions (role bindings + roles and cluster roles).
This step ensures that the CNF does not access any other resource than the one allowed by the role binding.
- TCA triggers HELM with the created service account.
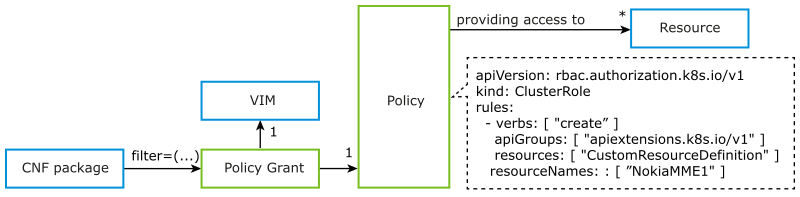
A virtual infrastructure administrator assigns the required privileges by extending the RBAC permission model with policy and policy grants, which is illustrated in the following diagram.