In VMware Integrated OpenStack, cloud administrators manage permissions through users, groups, and project definitions and datapath isolation across the compute, storage, and networking.
Allowing multiple users to share the VMware SDDC environment while ensuring complete separation is a key feature of VMware Integrated OpenStack. VIO offers ways to share virtual resources between tenants but maintains complete separation where needed.
VIO performs tenant isolation in various ways including:
Keystone API and Dashboard authentication and authorization
Private images in Glance Image Catalog
Network traffic isolation between user groups using VRF
Compute isolation
The following figure illustrates how a fully integrated VMware Integrated OpenStack Compute Zone, Project and Tenant Virtual Data Center (Tenant VDC), NSX-T segments, and Tier-1 gateways can be leveraged to provide a multitenant environment for deploying VNFs.

This section describes the user isolation using Keystone. The subsequent sections describe resource isolation as part of the OpenStack services design.
Identity
The OpenStack Keystone Identity service provides a single point of integration for managing authentication, authorization, and a catalog of services. After a user is authenticated with Keystone, an authorization token is returned by the identity service. An end-user can use the authorization token to access other OpenStack services based on the authorization rules (policy.json). The Identity service user database can be internal or integrated with some external user management systems.
As an alternative to maintaining an independent local keystone user database, VIO provides the capability to reference the enterprise Active Directory (AD) Lightweight Directory Authentication Protocol (LDAP) services for authentication. In addition to LDAP, Federated identity integration with SAML2 or OIDC with external Identity providers are also possible.
OpenStack Projects
Projects in OpenStack are equal to tenants in Telco Cloud Infrastructure. A project is an administrative container where telco workloads are deployed and managed.
An OpenStack project maps to a group of users and groups. OpenStack has a construct called Quotas that allows you to set an upper limit for resources such as vCPUs, memory, number of instances, networks, ports, subnets, and so on. Quotas are configured at the OpenStack Project level. The values used for quotas have no direct reference to the existing infrastructure capacity. Quotas on OpenStack are configured independent of the underlying platform. Quotas are enforced at OpenStack services such as Nova, Neutron, Cinder, and Glance.
Domains are a high-level grouping for projects, users, and groups. Domains can be used as a way to delegate management of OpenStack resources. A user can be a member of multiple domains if an appropriate assignment is granted. Keystone provides a default domain called Default. For most Telco use cases, a single Domain is more than sufficient for the user and group isolation.
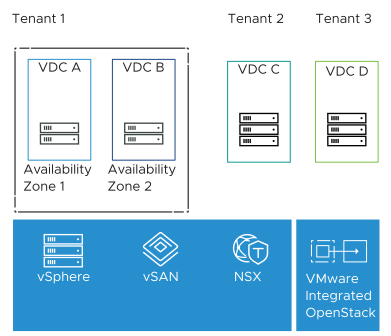
Tenant VDC
A Tenant VDC allows the creation of virtual data centers for tenants under different compute nodes that offer specific SLA levels for each telco workload. While quotas on projects set limits on the OpenStack resources, Tenant VDCs allow limits and reservations on a specific class of resources or compute nodes based on the existing capacity and provide resource guarantees for tenants. The vSphere platform enforces limits and guarantees resources allocated to a tenant on a given compute node and completely avoids noisy neighbor scenarios in a multitenant environment. The following three types of policies are supported:
Pay-as-you-go
Reservation Pool
Allocation Pool
Tenancy Design Recommendations
Design Recommendation |
Design Justification |
Design Implication |
|---|---|---|
Integrate VIO Identity service with an external user database such as AD. |
|
Requires a deep understanding of the corporate user directory structure to onboard only required users into VIO. |
Use OpenStack domain only in scenarios where the delegate management access to users and groups outside of the traditional Cloud Admin role is required. Otherwise, use OpenStack projects to provide Tenant isolation. |
|
None |
Use Tenant VDCs to guarantee resources for tenants and avoid noisy neighbor scenarios |
|
When using Tenant VDC, create a new default V DC with no reservation and map all default flavors to the new VDC. |
Avoid updating OpenStack policy.json if there are alternative ways to accomplish the same task. |
|
None |