The management plane for an Open RAN can be protected in three ways: its architecture, administration network, and the access solution and privileges of administrators.
An architecture with a secure management plane establishes the foundation for isolating management elements, including the administrative network, from other aspects of the virtual infrastructure and for successfully controlling and monitoring administrative access.
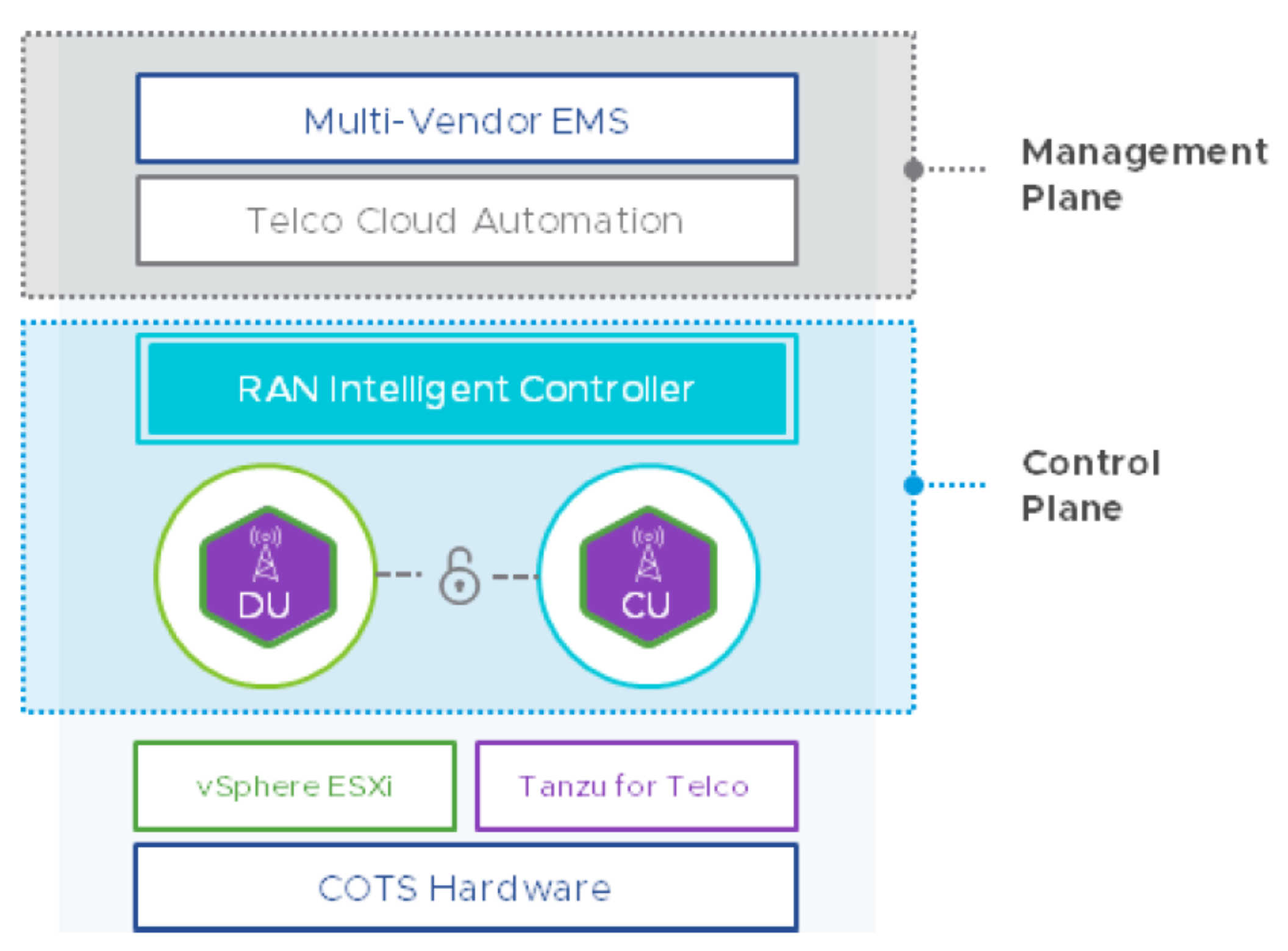
In architecting the management plane, operators can use inter-related and interoperable solutions from VMware not only to manage their virtualized and containerized RAN infrastructure but also to manage security measures in the RAN management plane:
VMware Telco Cloud Automation
VMware vSphere
In addition, for managing cloud native functions and cloud network functions, VMware infrastructure integrates at strategic points with Kubernetes and other cloud native technologies. For example, Telco Cloud Automation can securely deploy and orchestrate cloud native workloads on Kubernetes.
Architecture of the management plane and its protection
The architecture of the management tier is the foundation for isolating management functions from the operator’s network. To enhance security, the management plane is segmented into discrete zones, thereby preventing movement across the plane and restricting access to and exfiltration of network data. Management functions are critical security functions that require additional security controls. Operators must regularly scan the management network to detect anomalies in configurations and operations.
With Telco Cloud Platform RAN, you can manage the RAN virtualization fabric through a central orchestration tool: VMware Telco Cloud Automation. Telco Cloud Platform RAN uses secure, encrypted channels to administer VMs, VNFs, and the ESXi hypervisor. VMware Telco Cloud Automation controls access with authentication and multi-tenant role-based access control.
For more information about designing, isolating, and protecting the RAN management plane, see the VMware Telco Cloud Reference Architecture guide.
Protecting virtualization of critical security functions
In its findings of telecom security analysis, the NCSC emphasizes the protection of security-critical functions. Security-critical functions include orchestration systems for virtualization, management systems such as jump boxes, firewalls protecting a security zone, directory services such as Active Directory for authentication and access control, IPSec security gateways, and monitoring and auditing systems.
Because of the importance of the virtualization plane to telecom networks, the management and orchestration of those networks require additional security. The NCSC considers these management functions as security-critical functions. These functions must take place in a trusted location secured by the following:
Two-factor authentication
Role-based access control that uses the principles of separation of duties and least privilege
According to the NCSC summary, Operators use security-critical functions to enforce security controls in their networks and mitigate risk. As risks are mitigated, the options available to attackers are reduced and the security-critical functions become the primary focus of attack. The TSRs define additional controls for security-critical functions to ensure that they are resilient to targeted attacks from determined attackers.
It is crucial to limit the attack surface of security-critical functions. To reduce risk, you can isolate security functions in their own trust domains.
Establishing trust domains
Virtualized infrastructure plays a strong role in segmenting workloads into trusted domains to reduce the risk of a breach spreading from a compromised host to others. When you set up components of the management plane, such as VMware Telco Cloud Automation, you can do so in a trusted location segmented from the rest of the virtualization fabric.
By establishing the management plane in a separate domain from the virtualization plane, you can protect the management plane and critical security functions with firewalls, microsegmentation, and other measures.
Securing access to the management plane
The UK’s NCSC provides several principles that drive requirements for securing user access to the management plane. Operators must tightly control access to the management plane by using the principles of least privilege and separation of duties. Each user must be authenticated with multi-factor authentication (MFA).
The security of the orchestration system is significant. Access to Telco Cloud Automation is secured with role-based access control to limit access to NFVO, VNFM, VNF Designer, and the API. Other components of the VMware management plane, such as vSphere and vCenter, can authenticate and authorize users with Microsoft Active Directory or LDAP. Multi-factor authentication can be added for ESXi and vCenter.