VMware supplies an underlying virtualization plane with vSphere, vSAN, and NSX. They provide virtualized infrastructure for compute, storage, and networking.
To protect the foundation of the virtualization plane, vSphere establishes a fully-abstracted virtualization layer by using the VMware ESXi™ hypervisor, which prevents virtual workloads from accessing or cutting through to the underlying hardware.
The holistic security architecture of ESXi achieves this goal by providing security mechanisms at multiple layers:
Secure isolation of virtual machines at the virtualization layer. This includes secure instruction isolation, memory isolation, device isolation, and managed resource usage and network isolation.
Configurable secure management of the virtualized environment. This includes secure communication between virtualization components through SSL; host protection using lockdown mode; and least privilege by a fine-grained, role-based access-control mechanism.
Secure deployment of the ESXi software on servers through use of various platform-integrity mechanisms such as digitally signed software packages and Intel Trusted Platform Module (TPM)–based trusted boot.
Rigorous secure software development life cycle that enables developers to create software using secure design and coding principles such as minimum attack surface, least privilege, and defense in depth.
Keeping the virtualization fabric up-to-date
vSphere Lifecycle Manager (also called VMware vSphere® Update Manager™ ) centralizes the patch and version management for VMware vSphere and supports VMware ESXi hosts and VMs. Using vSphere Lifecycle Manager (LCM), you can upgrade and patch ESXi hosts, install and update third-party software on hosts, and upgrade Virtual Machine (VM) hardware and VMware Tools™.
LCM works either automatically or manually. A telecommunication operator typically runs LCM manually to check for host patches and extensions at regular intervals. For more information, see About vSphere Lifecycle Manager.
Delivering critical security patches for quick deployment
VMware Security Advisories documents the remediations for security vulnerabilities that are reported in VMware products. VMware Security Response Policy outlines the commitments for resolving vulnerabilities in VMware products. VMware releases a fix for the reported vulnerability in one or more of these forms:
A new major or minor release of the affected VMware product
A new maintenance or update release of the affected VMware product
A patch that can be applied on top of the affected VMware product
Instructions to download and install an update or patch for a third-party software component that is part of the VMware product installation
A corrective procedure or workaround to modify the VMware product configuration and mitigate the vulnerability
Updating the virtualization fabric without affecting the network
You can update the VMware Telco Cloud Infrastructure layer without affecting its availability by leverage feature within the vSphere software platform.
You can also update the VMware Telco Cloud Infrastructure layer without affecting Virtual Network Functions (VNFs) if they have a built-in fail-over capability, an active-active pattern, or another pattern that allows them to be moved with automation.
Feature within the vSphere software platform such as VMware DRS (Distributed Resource Scheduler) uses automation to move these VNFs from one set of hosts to another, accelerating the remediation process by determining the optimum number of hosts that can enter maintenance mode simultaneously based on current cluster conditions and demands without affecting the availability of the fabric or the VNFs running in the fabric.
To ensure that the VNF fabric are updated without affecting the network, CSPs require their vendors to supply VNFs with either a built-in failover capability or vSphere HA support as a failover mechanism.
Locking down hypervisors to restrict access
The security of ESXi hosts can be increased by keeping them in the lockdown mode. In the lockdown mode, operations are performed through vCenter Server by default. The Lockdown mode can be used to increase the security of an ESXi host by limiting the access allowed to the host. For more information, see Lockdown Mode.
In addition, the vSphere Web Client and the VMware Host Client™ let you open and close firewall ports for each service or allow traffic from specific IP addresses. For more information, see Incoming and Outgoing Firewall Ports for ESXi Hosts.
Adding only known hosts to the fabric
In a VMware environment, you can use host profiles and Preboot Execution Environment (PXE) to improve security by enforcing consistent security configurations and ensuring that only trusted software is loaded on ESXi hosts.
Host profiles in VMware allow administrators to create standard configurations for ESXi hosts in a vSphere environment. These profiles can include security settings such as password policies, firewall rules, and network security configurations. By enforcing these standardized configurations across all ESXi hosts, administrators can ensure that security settings are consistent and up-to-date, reducing the risk of misconfigurations or security vulnerabilities.
Preboot Execution Environment (PXE) is a network boot protocol that allows a computer to boot from a server on the network rather than from its own hard drive. In the context of virtualization, PXE can be used to deploy virtual machines (VMs) to ESXi hosts. By using PXE to deploy VMs, administrators can ensure that the VMs are deployed with the latest security updates and configurations. This can reduce the risk of deploying VMs with outdated or vulnerable software. In addition, PXE can be used in combination with secure boot technologies to ensure that only trusted software is loaded on the ESXi host. Secure boot technologies, such as Unified Extensible Firmware Interface (UEFI) Secure Boot and Trusted Platform Module (TPM), can verify the integrity of the boot process and prevent the loading of unauthorized or malicious software.
Adding only attested hosts to the fabric
VMware uses a technology called Trusted Platform Module (TPM) to cryptographically attest hosts. A TPM is a microchip that is built into the computer's motherboard and is used to store cryptographic keys and measurements of the host's hardware and software configuration.
By using TPM-based attestation, VMware can ensure that only trusted hosts are allowed onto the network, and that the configuration of the hosts is consistent with a known and secure baseline. This helps to prevent unauthorized access, data breaches, and other security threats.
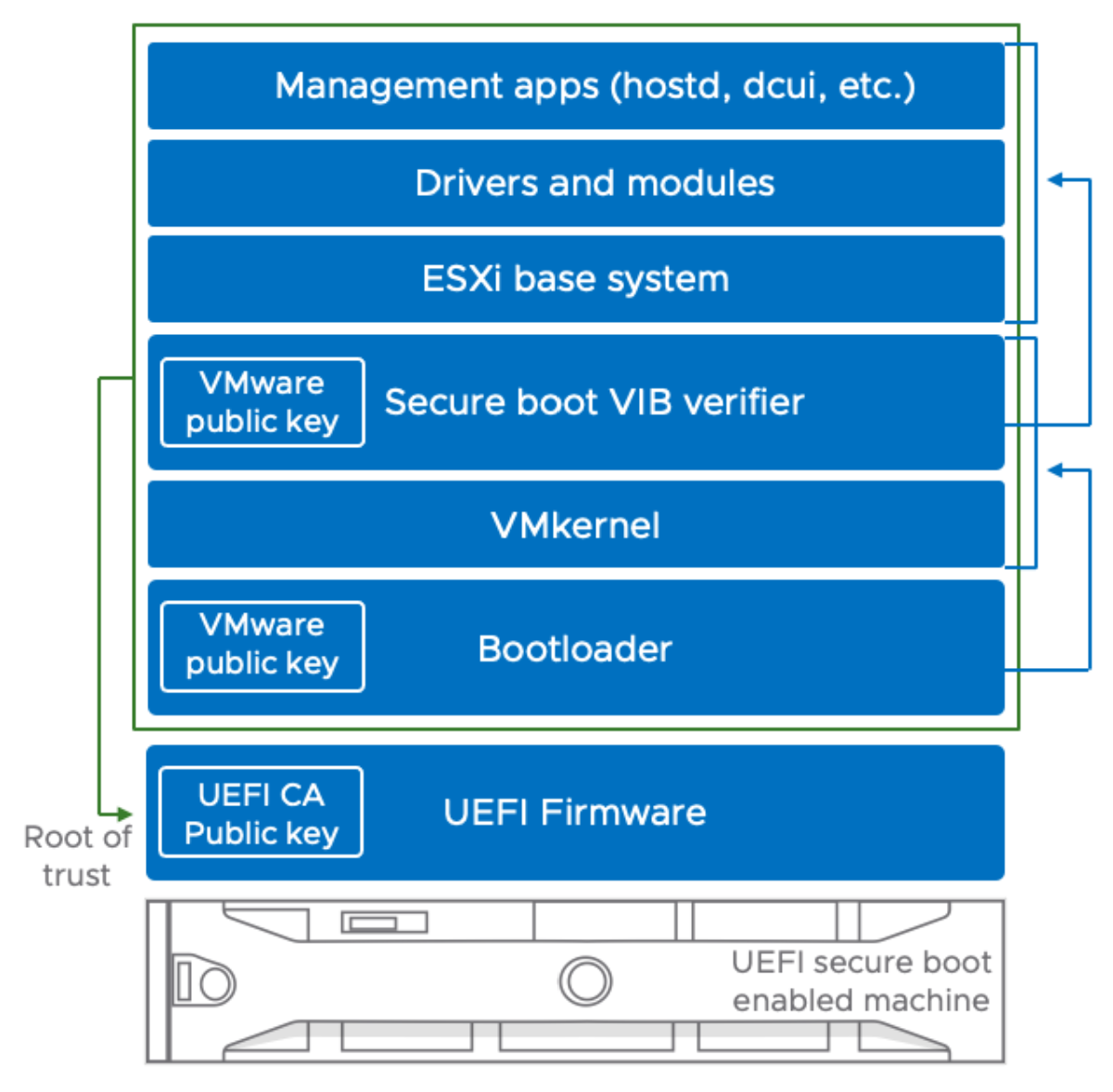
As a security best practice, CSPs must use hardware roots-of-trust to support Secure Boot technology for physical hosts. Secure boot is part of the UEFI firmware standard. With secure boot enabled, a machine does not load a UEFI driver or application unless the operating system bootloader is cryptographically signed. VMware Telco Cloud support ESXi secure boot if it is enabled in the hardware. VMware recommends that you deploy hardware that supports and uses hardware roots-of-trust.
With secure boot enabled, the boot sequence is as follows.
The ESXi bootloader uses a VMware public key to verify the signature of the kernel and a small subset of the system that includes a secure boot VIB verifier.
The VIB verifier checks every vSphere Installation Bundle (VIB) package that is installed on the system.
At this point, the entire System Boot with the root of trust in certificates that are part of the UEFI firmware.
Segmenting internal and external network traffic
VMware NSX segments internal and external network traffic in the virtualization fabric by implementing virtual firewalls and micro-segmentation. In addition, by incorporating third-party firewalls, you can enhance your virtual environment's security posture and protect your virtual machines from various types of cyber threats, including malware, unauthorized access, and data breaches. You must choose a reputable third-party firewall vendor that offers the features and functionalities that meet your organization's security requirements.
Virtual firewalls can be combined with micro-segmentation to separate all types of traffic, VMs, and workloads.
NSX micro-segmentation is a network security technology that allows you to divide a virtual data center and its workloads into smaller, more granular segments for better security and isolation. These segments are created using virtual firewalls and other security controls to provide network traffic filtering and policy enforcement between segments. You can then apply security controls to each segment, restricting an attacker’s ability to move to another segment or workload. This approach can reduce the attack surface of your virtualized environment, prevent lateral movement of threats within the network, and limit the impact of a security breach by containing it within a smaller segment of the network.
Micro-segmentation uses the following capabilities to reduce risk and improve security:
Distributed stateful firewalling: Protects each application running in the data center with application-level gateways that are applied on a per-workload basis.
Topology-agnostic segmentation: Protects each application with a firewall independent of the underlying network topology.
Centralized ubiquitous policy control of distributed services: Controls access with a centralized management plane.
Granular unit-level controls implemented by high-level policy objects: Creates a security perimeter for each application without relying on VLANs.
Network-based isolation: Implements logical network overlays through virtualization.
Policy-driven unit-level service insertion and traffic steering: Helps monitor network traffic.
The micro-segmentation capabilities of NSX also meet the security recommendations for protecting virtualized workloads, as outlined in NIST Special Publication 800-125B, Secure Virtual Network Configuration for VM Protection.
Storing secrets and keys in secure hardware-backed storage
An external Key Management Server (KMS) provides the keys for encrypting VMs in vSphere and the vSAN datastore.
Using an external KMS allows for greater security, as the keys are stored in a separate, hardware-backed system that is designed specifically for secure key storage. This helps to protect against unauthorized access to the keys, which are critical for maintaining the confidentiality and integrity of the encrypted data.
However, setting up and maintaining an external KMS can require significant effort and investment, as it involves obtaining and configuring robust third-party hardware to store the keys. Also, Operators must follow proper security protocols and procedures to ensure the ongoing security and integrity of the key management process.