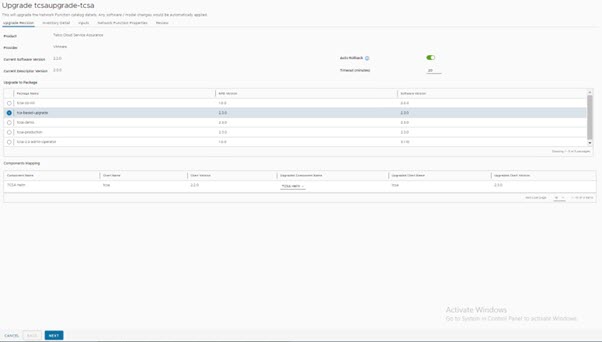
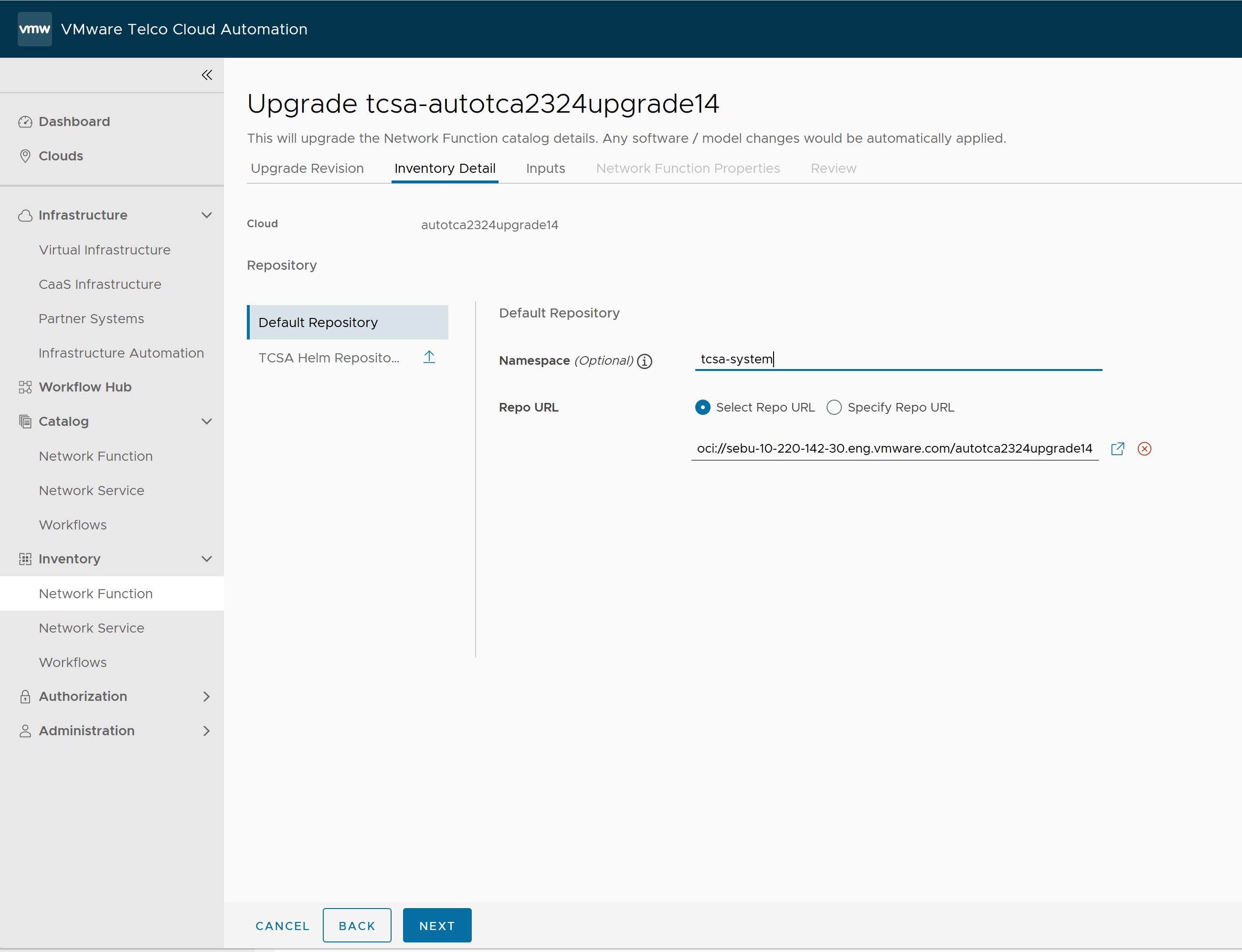
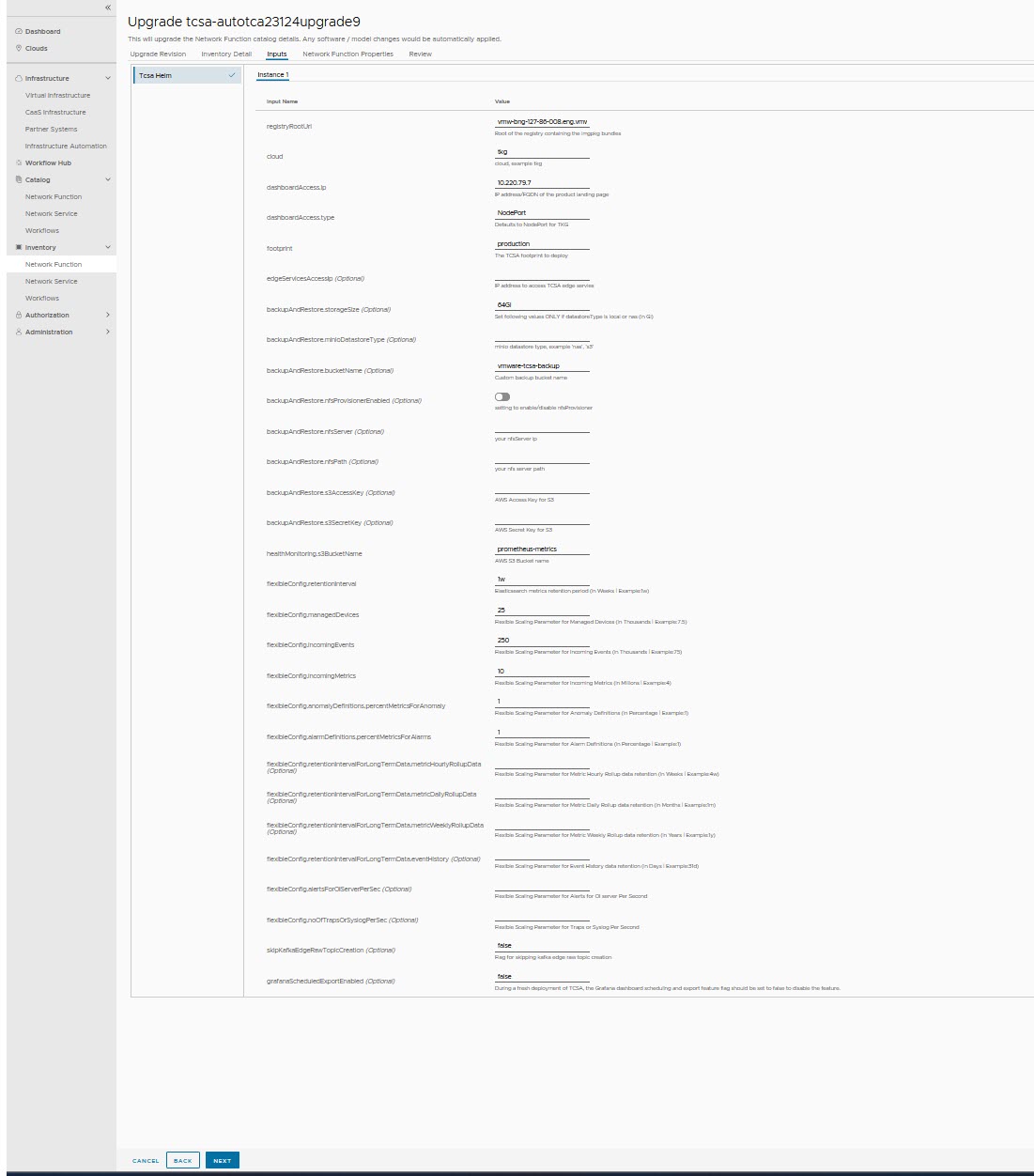
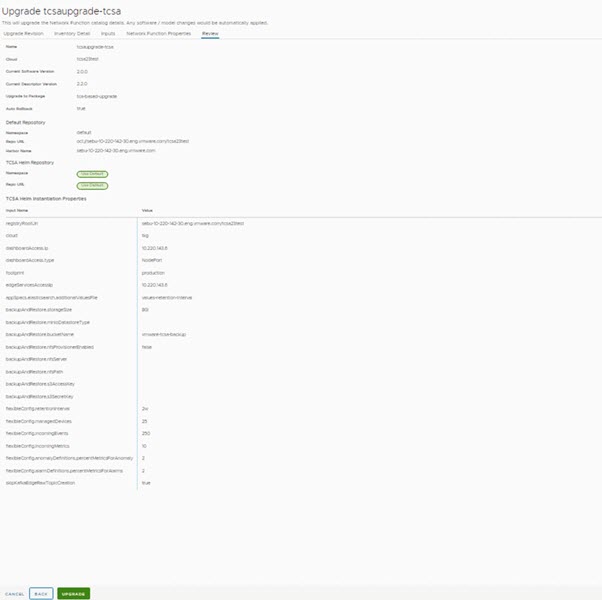
In this section, you can find information on how to upgrade the tcsa CNF.
Procedure
What to do next
After the VMware Telco Cloud Service Assurance upgrade is successful, follow the steps mentioned in the Post Upgrade topic.
After perfoming the steps in the
Post Upgrade, you must upgrade all the remote data collector managers. For more information, see
Upgrading Remote Collector Manager.
Note:
- If you do not have a remote data collector manager then you can skip this step.
- If the user wants to enable the Grafana Schedule and Export Reports post the deployment, then follow the procedure mentioned in the Optional feature : Enabling Grafana Schedule and Export Reports Feature section.
After perfoming the steps in the Upgrading Remote Collector Manager, you must upgrade the domain managers as mentioned in the Upgrade Domain Manager topic.
Note: If there are any SSL Handshake errors and the discovery fails in the Domain Managers while discovering VMware Aria Operations,
VMware Telco Cloud Automation, Cisco ACI, VCD, and VIMS after upgrading the Domain Manager and
VMware Telco Cloud Service Assurance Core then to regenerate the Kafka Edge Certificate follow the procedure given in the
SSL Handshake Error Post TCSA and Domain Manager Upgrade topic given in the
VMware Telco Cloud Service Assurance Troubleshooting Guide.