The data collector interacts with vCenter Server, vCloud Director, Storage Resource Manager (SRM), and public cloud instances, and pushes the data to the VMware Telco Cloud Service Assurance.
Remote Collector manger is deployed on bare metal with Docker installed. Remote DCF uses the VMware Telco Cloud Service Assurance harbor repository for the collector images.
Prerequisites
- Verify that you have deployed Docker (24, 25, or 26 version) on the remote VM and Docker is running and exposed on local
unix://var/run/docker.sock.
- Ensure the reachability to the remote VM from the VMware Telco Cloud Service Assurance K8s cluster.
- Ensure that the remote VM has sufficient resources to deploy the Data Collectors and Collector manager. For more information, see the VMware Telco Cloud Service Assurance Sizing Sheet.
- Ensure that the Remote Collector manager is always created on the target VM, and only one Remote Collector Manager per target VM.
- Verify that you have the Docker permission to create network, volumes, and containers.
- Ensure that firewall is configured to allow communication between VMware Telco Cloud Service Assurance and remote data collection VM for Control and Data Paths. Inbound and Outbound communication must be allowed for the following paths:
Procedure
- For Docker login, perform the following procedure according to the registry type:
- When registry type is Harbor:
- Log in to VMware Telco Cloud Service Assurance Harbor Registry and add certificates into the remote VM.
- Copy the
setup_harbor.sh file from the VMware Telco Cloud Service Assurance bundle./root/tcx-deployer/scripts/remoteCollectorManager/setup_harbour.sh
The following is an example of the setup_harbor.sh file.
#!/bin/bash
# Harbor on the deployment K8s cluster
HARBOR_IP="<harbor-repo-ip>"
HARBOR_PORT="<harbor-repo-port>"
# Download the Harbor SSL certificate
echo -n | openssl s_client -showcerts -connect $HARBOR_IP:$HARBOR_PORT 2>/dev/null | sed -ne '/-BEGIN CERTIFICATE-/,/-END CERTIFICATE-/p' > harbor.crt
if [ $HARBOR_PORT -eq 443 ] ; then
HARBOR_CERT_DIR=$HARBOR_IP
else
HARBOR_CERT_DIR=$HARBOR_IP:$HARBOR_PORT
fi
# Add the certificate to the Docker certificate store
sudo mkdir -p /etc/docker/certs.d/$HARBOR_CERT_DIR/
sudo mv harbor.crt /etc/docker/certs.d/$HARBOR_CERT_DIR/ca.crt
# Restart the Docker daemon to ensure that it uses the new SSL certificate
sudo systemctl restart docker
- Modify the following parameters in the
setup_harbor.sh script before running.
- Change the permission of the
setup_harbor.sh file:chmod +X setup_harbor.sh
- Execute the following command:
bash setup_harbor.sh
- Log in to the harbor repository.
Note: Use the harbor user name password from
VMware Telco Cloud Service Assurance installer config.
Once the login is successful, following message aapears: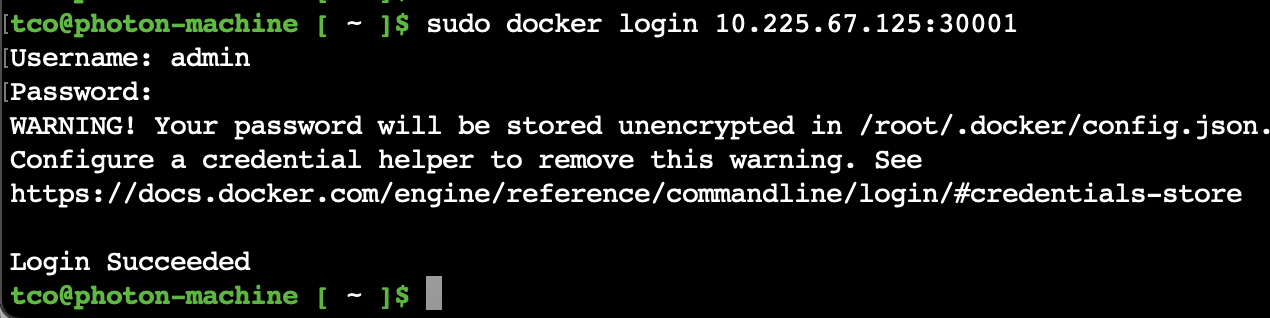
- When registry type is Azure Container Repository:
- Log in to Azure Container Repository using command docker login <acr-url>.
 If error related to certificate appears, you can import the certificate (
If error related to certificate appears, you can import the certificate (setup_harbor.sh) using the step 2 (a) (ii):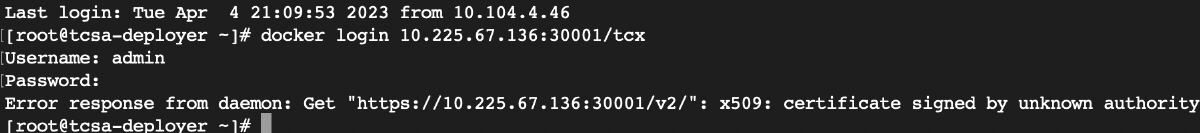
- Copy the
remote_env.properties file from the VMware Telco Cloud Service Assurance bundle.
/root/tcx-deployer/scripts/remoteCollectorManager/remote_env.properties
The following is an example of the remote_env.properties file.
# MANDATORY Properties
REGISTRY_URL=10.X.X.X:30001/tcx
REGISTRY_USERNAME=admin
REGISTRY_PASSWORD='*******'
REMOTE_IP=10.XX.XX.XX
TCSA_IP=10.225.XX.XX
TCSA_PORT=30002
TCSA_USERNAME=admin
TCSA_PASSWORD='********'
REGISTRY_TYPE=harbor
KAFKA_IP=10.225.XX.XX
KAFKA_PORT=32092
# OPTIONAL Properties Use if you want to override Default Values
DC_NAME=remote-10.225.XX.XX
Note:
- Ensure that the
REGISTRY_URL is the same registry URL provided in values.yaml file, while deploying VMware Telco Cloud Service Assurance.
- DC_NAME is the name of the Datacenter which can only have these special characteres: [ . ],[ - ],[ _ ].
- Copy the
run_remote_collector.sh script the VMware Telco Cloud Service Assurance bundle.
/root/tcx-deployer/scripts/remoteCollectorManager/run_remote_collector.sh
The following is an example of the run_remote_collector.sh script.
#!/bin/bash
#Variables For Script
ENV_PROPERTIES_FILE=$(pwd)/remote_env.properties
#Path to the tls certificates. If the certificates do not exist in the location provided, The remote collector will create it.
TLS_CERTIFICATE_PATH=$(pwd)/remote/certs
#Path to the custom packages. If the custom_packages directory does not exist in the location provided, The remote collector will create it.
CUSTOM_PACKAGE_PATH=$(pwd)/remote/custom_packages
#please Donot change the Following variables
NETWORK_NAME=internal-collector-network
source $ENV_PROPERTIES_FILE
#Regex pattern for DC_NAME [a-zA-Z0-9.-_]
PATTERN="^[a-zA-Z0-9]([-_.a-zA-Z0-9]{0,61}[a-zA-Z0-9])?$"
echo "$DC_NAME"
if [[ ! "$DC_NAME" =~ $PATTERN ]]; then
echo "DC_NAME does not match the pattern. DC_NAME can start and end with alphanumeric character and special character are . - _ in-between only"
exit 1
fi
TCSA_URL=https://$TCSA_IP:$TCSA_PORT
echo "Get Remote Collector Manager Image from TCSA"
access_token=$(curl -k --location --request POST $TCSA_URL/auth/realms/NGINX/protocol/openid-connect/token --header 'Content-Type: application/x-www-form-urlencoded' --data-urlencode 'grant_type=password' --data-urlencode 'client_id=operation-ui' --data-urlencode 'username='$TCSA_USERNAME --data-urlencode 'password='$TCSA_PASSWORD | sed "s/{.\"access_token\":\"\([^\"]\).*}/\1/g")
image_id=$(curl -k --header "Authorization: Bearer $access_token" $TCSA_URL/dcc/v1/remote/images |grep '"image"' | sed 's/.: "\(.\)".*/\1/')
echo $image_id
if [ -z "$image_id" ]
then
echo "Remote Collector manager Image is not available please make sure you have Entered correct TCSA_URL, TCSA_USERNAME and TCSA_PASSWORD";
exit 1
fi
echo "Fetched the Remote Collector manager Image Name From TCSA done"
echo "Create Internal Network if required"
# Check if the network already exists
if ! docker network inspect $NETWORK_NAME >/dev/null 2>&1; then
# If the network doesn't exist, create it
docker network create $NETWORK_NAME --driver bridge
fi
# checking if container already exists
docker ps -a --filter "name=collector-manager" | grep "collector-manager" > /dev/null
if [ $? -eq 0 ]; then
echo "collector-manager already exists please stop and remove the conatiner"
exit 1
fi
echo "creating the Remote Collector manager Container with Name : collector-manager"
docker_id="$(docker run -d -p 443:443 -v /var/run/docker.sock:/var/run/docker.sock --env-file ${ENV_PROPERTIES_FILE} -e TCSA_PASSWORD=${TCSA_PASSWORD} -e REGISTRY_PASSWORD=${REGISTRY_PASSWORD} -v ${TLS_CERTIFICATE_PATH}:/etc/nginx/certs -v ${CUSTOM_PACKAGE_PATH}:/app/custom_packages --network internal-collector-network --restart unless-stopped --name collector-manager $image_id)"
# check if container is up
if [ $? -eq 0 ] ; then
echo "collector-manager started successfully please check the logs using docker logs -f collector-manager"
else
echo "collector-manager failed to start please check logs docker logs collector-manager"
fi
- Change the permissions of
remote_collector.sh file:
chmod +X run_remote_collector.sh
- Execute the
remote_collector.sh script:
bash run_remote_collector.sh

 If error related to certificate appears, you can import the certificate (
If error related to certificate appears, you can import the certificate (