After you upgrade to Workspace ONE Access 20.01.0.0, you might need to configure certain settings.
Apply Security Patch HW-137959
After you upgrade, apply the security patch HW-137959 for this specific upgrade version. See VMware KB article 85254 HW-137959: VMSA-2021-0016 for Workspace ONE Access, VMware Identity Manager (CVE-2021-22002, CVE-2021-22003).
Configuring Workspace ONE Access Connector Instances
- The connector version you use with the Workspace ONE Access 20.01 service can vary. When appropriate, migrate your connector instances to the Workspace ONE Access 20.01 connector, which is available solely for Windows systems. See Migrating to Workspace ONE Access 20.01 Connectors.
However, if you are using Virtual Apps or plan to use Virtual Apps in the future, do not migrate to 20.01 connector instances.
Important: Citrix, Horizon Connection Server, and ThinApp integrations are not available with the Workspace ONE Access 20.01 connector.- To use ThinApp packaged applications, use the VMware Identity Manager connector (Linux) version 2018.8.1.0.
- To use other Virtual Apps, such Horizon desktops and applications or Citrix published resources, use the VMware Identity Manager connector (Windows) version 19.03.
Log4j Configuration Files
If any log4j configuration files in a Workspace ONE Access 20.01 instance were edited, new versions of the files are not automatically installed during the upgrade. However, after the upgrade, the logs controlled by those files will not work.
To resolve this issue:
- Log in to the virtual appliance.
- Search for log4j files with the .rpmnew suffix.
find / -name "*log4j.properties.rpmnew"
- For each file found, copy the new file to the corresponding old log4j file without the .rpmnew suffix.
Save the Workspace ONE UEM Configuration
Saving the Workspace ONE UEM configuration populates the Device Services URL for the catalog. Perform this task to allow new end users to enroll and manage their devices.
- Log in to the Workspace ONE Access console.
- Select .
- In the Workspace ONE UEM Configuration section, click Save.
Cluster ID in Secondary Data Center
Beginning with VMware Identity Manager 3.3, cluster IDs are used to identify the nodes in a cluster.
If your Workspace ONE Access 20.01 deployment includes a secondary data center, you might need to change the cluster ID of the secondary data center after upgrade.
VMware Identity Manager detects and assigns a cluster ID automatically when a new service appliance is powered up. For a multiple data center deployment, each cluster must be identified with a unique ID.
All appliances that belong to a cluster have the same cluster ID and a cluster typically consists of three appliances.
When you set up the secondary data center, verify that the cluster ID is unique to the data center. If a cluster ID is not unique to the data center, verify that each node has the Elasticsearch discovery-idm plugin installed and edit the cluster ID manually as described in the instructions that follow. You only need to perform these actions once and only on the secondary data center.
- Verify that each node has the Elasticsearch discovery-idm plugin.
- Log in to the virtual appliance.
- Use the following command to check if the plugin is installed.
/opt/vmware/elasticsearch/bin/plugin list
- If the plugin does not exist, use the following command to add it.
/opt/vmware/elasticsearch/bin/plugin install file:///opt/vmware/elasticsearch/jars/discovery-idm-1.0.jar
- Log in to the Workspace ONE Access console.
- Select the tab.
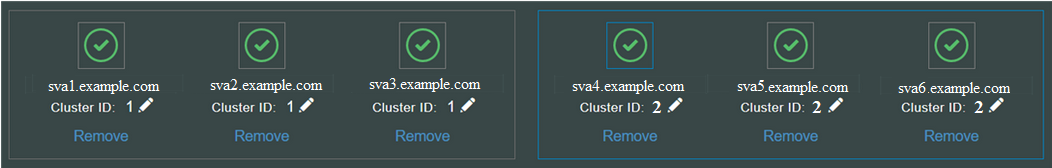
- In the top panel, locate the cluster information for the secondary data center cluster.
- Update the cluster ID of all the nodes in the secondary data center to a different number than the one used in the first data center.
For example, set all the nodes in the secondary data center to 2, if the first data center is not using 2.
- Verify that the clusters in both the primary and secondary data centers are formed correctly.
Follow these steps for each node in the primary and secondary data centers.
- Log in to the virtual appliance.
- Run the following command:
curl 'http://localhost:9200/_cluster/health?pretty'
If the cluster is configured correctly, the command returns a result similar to the following example:
{ "cluster_name" : "horizon", "status" : "green", "timed_out" : false, "number_of_nodes" : 3, "number_of_data_nodes" : 3, "active_primary_shards" : 20, "active_shards" : 40, "relocating_shards" : 0, "initializing_shards" : 0, "unassigned_shards" : 0, "delayed_unassigned_shards" : 0, "number_of_pending_tasks" : 0, "number_of_in_flight_fetch" : 0 }
Cache Service Setting in Secondary Data Center Appliances
If you set up a secondary data center, Workspace ONE Access 20.01 instances in the secondary data center are configured for read-only access with the "read.only.service=true" entry in the /usr/local/horizon/conf/runtime-config.properties file. After you upgrade such an appliance, the service fails to start.
| sva1.example.com |
| sva2.example.com |
| sva3.example.com |
- Log in to a virtual appliance in the secondary data center as the root user.
For this example, log in to sva1.example.com.
- Edit the /usr/local/horizon/conf/runtime-config.properties file as indicated in the substeps that follow.
You might be able to edit an existing entry, or you can add a new entry. If applicable, uncomment entries that are commented out.
- Set the value of the
cache.service.typeentry toehcache.cache.service.type=ehcache
- Set the value of the
ehcache.replication.rmi.serversentry to the fully qualified domain names (FQDN) of the other nodes in the secondary data center. Use a colon:as the separator.
For this example, configure the entry as follows.
ehcache.replication.rmi.servers=sva2.example.com:sva3.example.com
- Set the value of the
- Restart the service.
service horizon-workspace restart
- Repeat the preceding steps on the remaining nodes in the secondary data center.
For this example, the remaining nodes to configure are sva2.example.com and sva3.example.com.
Citrix Integration
For Citrix integration in VMware Identity Manager 3.3, all external connectors must be version 2018.8.1.0 for Linux (the connector version in the 3.3 release) or later.
You must also use Integration Broker 3.3. Upgrade is not available for Integration Broker. Uninstall the old version, then install the new version.
Changes in Past Releases
For changes in past releases, see Upgrading to VMware Identity Manager 19.03.0.0 (Linux).