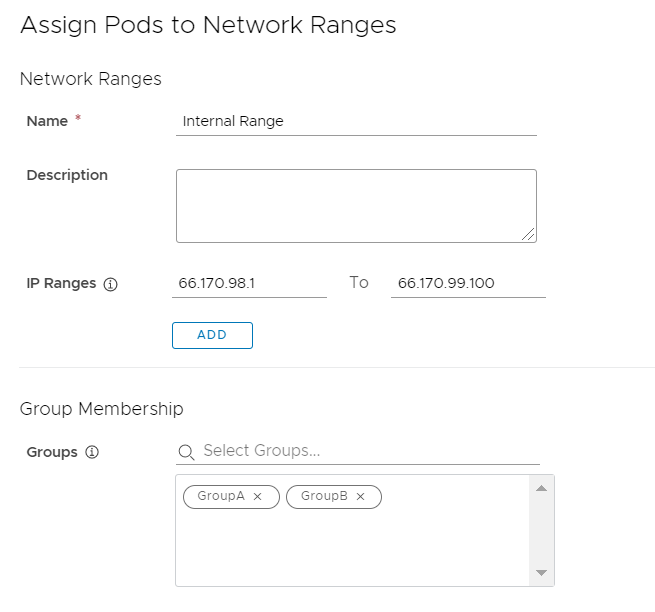
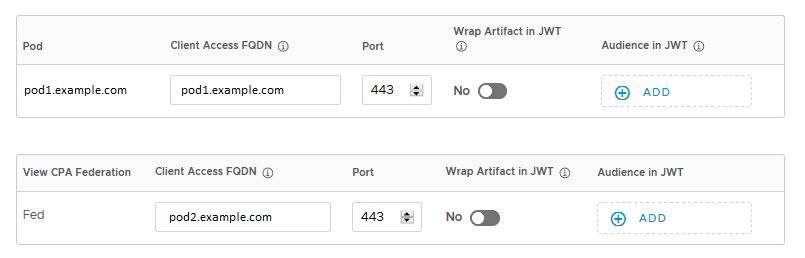
As part of integrating Workspace ONE Access and Horizon, you specify Client Access FQDNs for network ranges so that users connect to the correct Horizon server based on their network range. Additionally, you can filter users by specifying user groups for each network range.
When you create a Horizon virtual apps collection, the wizard guides you to the Network Ranges tab to configure the Client Access FQDNs for the pods and pod federation in the collection. After creating the collection, you can edit the Client Access FQDNs at any time from the Network Ranges tab.
All network ranges in your tenant must have Client Access FQDNs set for Horizon pods and pod federations. If a network range does not have a Client Access FQDN defined, users accessing Horizon resources through that network range cannot launch their assigned applications and desktops. Make sure that whenever you create new network ranges, you also edit the virtual apps collections to add Client Access FQDNs for Horizon pods and pod federations to the new network range.
You can configure Client Access FQDNs in Workspace ONE Access in the following ways:
- Use only network ranges to direct users to the appropriate Client Access FQDNs.
Create multiple network ranges and specify Client Access FQDNs for each network range. Do not select any user groups for the network ranges. All users will be directed to Client Access FQDNs based on the network range from which they are accessing their assigned Horizon apps and desktops.
For example, you can create separate network ranges for internal and external access and specify the appropriate Client Access FQDNs for each range.
- Use both network ranges and groups to direct users to the appropriate Client Access FQDNs.
Create multiple network ranges and specify Client Access FQDNs for each range. Also select user groups for the network ranges. For users to be able to launch Horizon apps and desktops from a Client Access FQDN, their client IP address must match the network range and they must belong to at least one of the groups selected for the network range. If no groups are selected for a network range, all users whose client IP address matches the network range can launch apps and desktops from that network range's Client Access FQDN.
For example, you can create separate network ranges for internal and external access and filter users for each range based on whether they belong to a permanent employee group or a temporary employee group.
Note: If you do not want to create multiple network ranges, you can configure user groups on the default ALL RANGES network range for each virtual apps collection. Only users that belong to one of the selected groups will be able to launch Horizon apps and desktops from the ALL RANGES Client Access FQDN.For example, you can create different virtual apps collections for pods in different regions, create user groups by region, and select the appropriate user groups for the ALL RANGES network range for each collection.
If you configure overlapping network ranges, Workspace ONE Access applies the following rules to find the best match for the user:
- If the user’s client IP address matches multiple ranges and no groups are specified for any of the network ranges, then the network range that was created most recently is used to determine the Client Access FQDN for the user.
- If the user's client IP address matches multiple network ranges and the user’s groups match only one of those network ranges, then the network range that matches both the client IP address and groups is used to determine the Client Access FQDN for the user.
- If the client IP address matches multiple network ranges and the user belongs to one or more groups in all those network ranges, then the network range that has the most user group matches is used to determine the Client Access FQDN for the user.
- If the client IP address matches multiple network ranges and the number of user groups that match is identical across multiple network ranges, then the network range that was created most recently is used to determine the Client Access FQDN for the user.
Prerequisites
A Super Admin role, or a custom role that can perform the Manage Settings action in the Identity and Access Management service, is required to create and edit network ranges.