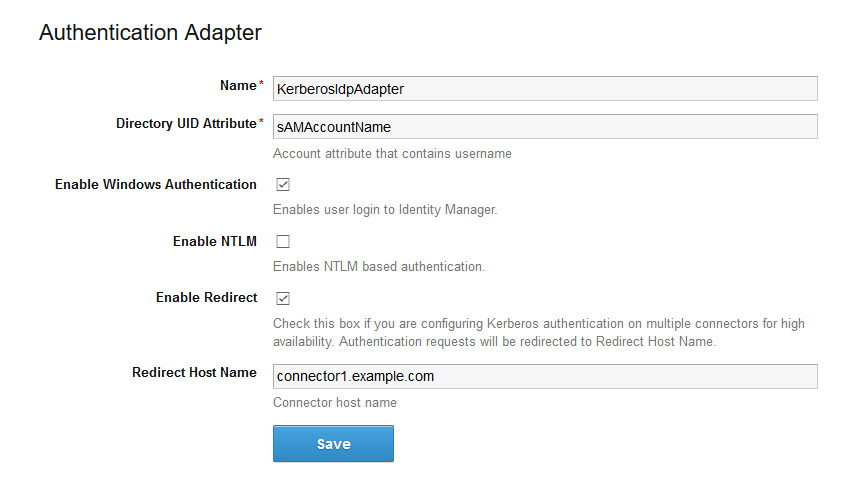
Configure and enable the KerberosIdpAdapter on the VMware Identity Manager Connector. If you have deployed a cluster for high availability, configure and enable the adapter on all the connectors in your cluster.
Important: Authentication adapters on all the connectors in your cluster must be configured identically. The same authentication methods must be configured on all the connectors.
For more information about configuring Kerberos authentication, see the VMware Identity Manager Administration Guide.
Prerequisites
- The connector must be joined to the Active Directory domain.
- The connector host name must match the Active Directory domain to which the connector is joined. For example, if the Active Directory domain is sales.example.com, the connector host name must be connectorhost.sales.example.com.
If you cannot assign a hostname that matches the Active Directory domain structure, you need to configure the connector and Active Directory manually. See the Knowledge Base for information.
Procedure
What to do next
- Ensure that each connector on which the KerberosIdpAdapter is enabled has a trusted SSL certificate. You can obtain the certificate from your internal certificate authority. Kerberos authentication does not work with self-signed certificates.
Trusted SSL certificates are required regardless of whether you enable Kerberos on a single connector or on multiple connectors for high availability.
- Set up high availability for Kerberos authentication, if necessary. Kerberos authentication is not highly available without a load balancer.