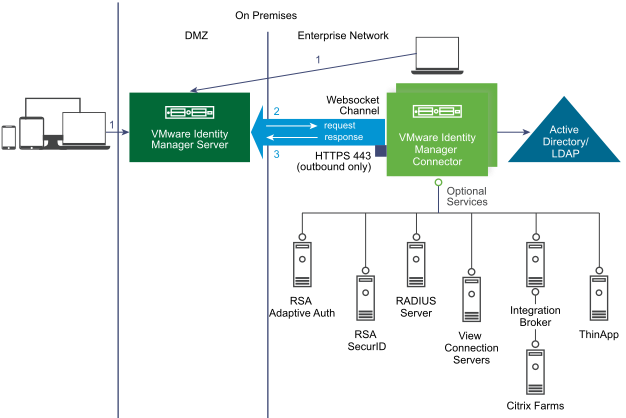
In this model, you install the VMware Identity Manager virtual appliance in the DMZ. You also install a standalone VMware Identity Manager connector virtual appliance in outbound-only connection mode in the enterprise network. This model does not include any Workspace ONE UEM components.
User and group sync from your enterprise directory and user authentication are handled by the standalone VMware Identity Manager connector. The connector can also sync resources, such as Horizon 7 desktops and applications, to the VMware Identity Manager service.
Port Requirements
- Inbound 443 (HTTPS)
- Inbound 88 (TCP/UDP) - iOS SSO only
- Inbound 5262 (HTTPS) - Android SSO only
- Inbound CertAuthSSLPassthroughPort (HTTPS) - Certificate authentication configured on embedded connector only. The default port is 7443.
VMware Identity Manager connector is installed in outbound-only connection mode and does not require inbound port 443 to be opened. The connector communicates with the VMware Identity Manager service through a Websocket-based communication channel.
For the complete list of ports used, see Deploying VMware Identity Manager in the DMZ and Deploying VMware Identity Manager Connector in the Enterprise Network.
Supported Authentication Methods
This deployment model supports all authentication methods. Some of these authentication methods do not require the connector and are managed directly by the service through the Built-in identity provider.
- Password - uses the connector
- RSA Adaptive Authentication - uses the connector
- RSA SecurID - uses the connector
- RADIUS - uses the connector
- Certificate - uses the embedded connector
- VMware Verify - through the Built-in identity provider
- Mobile SSO (iOS) - through the Built-in identity provider
- Mobile SSO (Android) - through the Built-in identity provider
- Inbound SAML through a third-party identity provider
Supported Directory Integrations
You can integrate the following types of enterprise directories with the VMware Identity Manager service in this deployment model:
- Active Directory over LDAP
- Active Directory, Integrated Windows Authentication
- LDAP Directory
If you plan to integrate an LDAP directory, see the limitations in "Integrating with LDAP Directories" in Directory Integration with VMware Identity Manager.
Alternatively, you can use the following methods to create users in the VMware Identity Manager service:
- Create local users directly in the VMware Identity Manager service.
- Use Just-in-Time provisioning to create users in the VMware Identity Manager service dynamically at login, using SAML assertions sent by a third-party identity provider.
Supported Resources
You can integrate the following types of resources with the VMware Identity Manager service in this deployment model:
- Web applications
- Horizon 7, Horizon 6, or View desktop and application pools
- Horizon Cloud applications and desktops
- Citrix-published resources
- ThinApp packaged applications
Additional Information
- Deploying VMware Identity Manager in the DMZ and Deploying VMware Identity Manager Connector in the Enterprise Network
- Directories
- Directory Integration with VMware Identity Manager
- "Using Local Directories" in VMware Identity Manager Administration
- "Just-in Time User Provisioning" in VMware Identity Manager Administration
- "Configuring User Authentication in VMware Identity Manager" in VMware Identity Manager Administration
- Setting up Resources in VMware Identity Manager