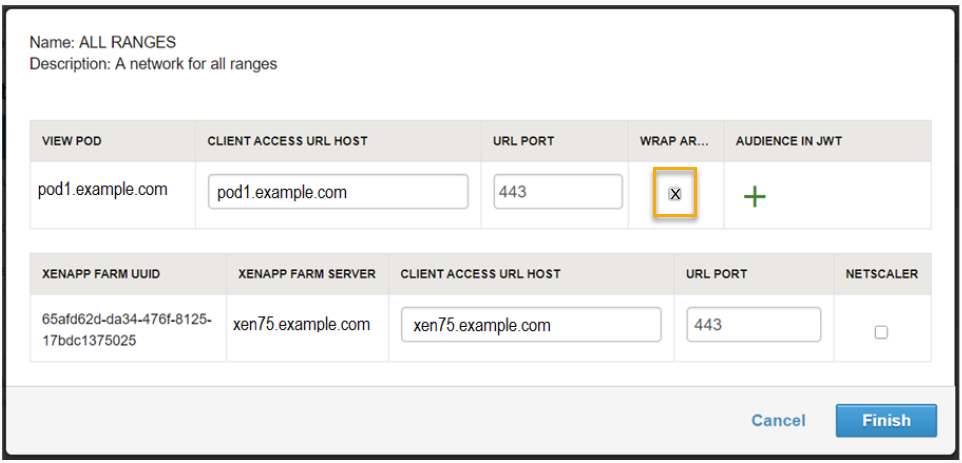
When the VMware Identity Manager service is integrated with a validating gateway, such as F5, the Wrap Artifact in JWT setting must be enabled in the VMware Identity Manager service to authenticate Horizon resources assigned to users.
When Wrap Artifact in JWT is enabled to authenticate a Horizon resource launch request, the VMware Identity Manager service generates a digitally signed JWT token that includes the SAML artifact to allow for verification.
This JWT token is sent to the validating gateway in the DMZ. The gateway validates the JWT token from VMware Identity Manager and extracts the SAML artifact value from the token. The gateway forwards the request with the real SAML artifact value to the Horizon Connector Server. The Connector Server verifies the request and the user is signed in to the Horizon resource.
If Wrap Artifact in JWT is not enabled, the validating gateway does not pass the artifact to the Horizon Connect Server for validation and authentication fails.
Prerequisites
The validating gateway configured with the following VMware Identity Manger details.
- SSL Certificate
- OAuth2 client ID and secret
- VMware Identity Manager validation endpoint URL
Procedure
What to do next
The unique audience names that you add here must also be added to the validating gateway configuration.