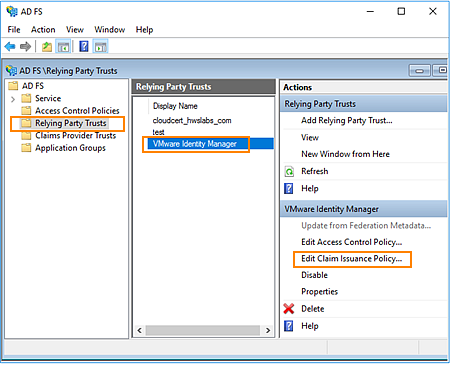
As the claims issuer (or identity provider), AD FS sends security tokens containing authentication claims to VMware Workspace ONE Access. Relying party claim rules define the content of these claims and transform them into a format that VMware Workspace ONE Access can recognize and consume.
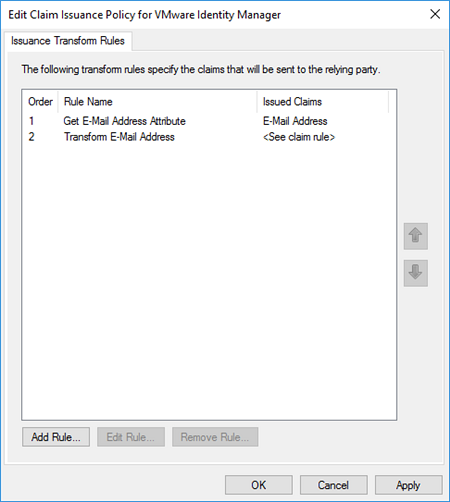
You must configure two claim rules for VMware Workspace ONE Access as the relying party. The first rule directs AD FS to look up the LDAP email address attribute for the requesting user and to send this attribute as the claim. The second rule transforms this claim into the SAML-based email address attribute expected by VMware Workspace ONE Access.