There are two parts to enable Session MFA with SAML. First you will set up the SAML configuration in the Workspace ONE UEM console and then you will configure your Identity Provider (IDP) settings for use with VMware Tunnel.
Part 1: Configuring the VMware Tunnel SAML Settings in the Workspace ONE UEM console
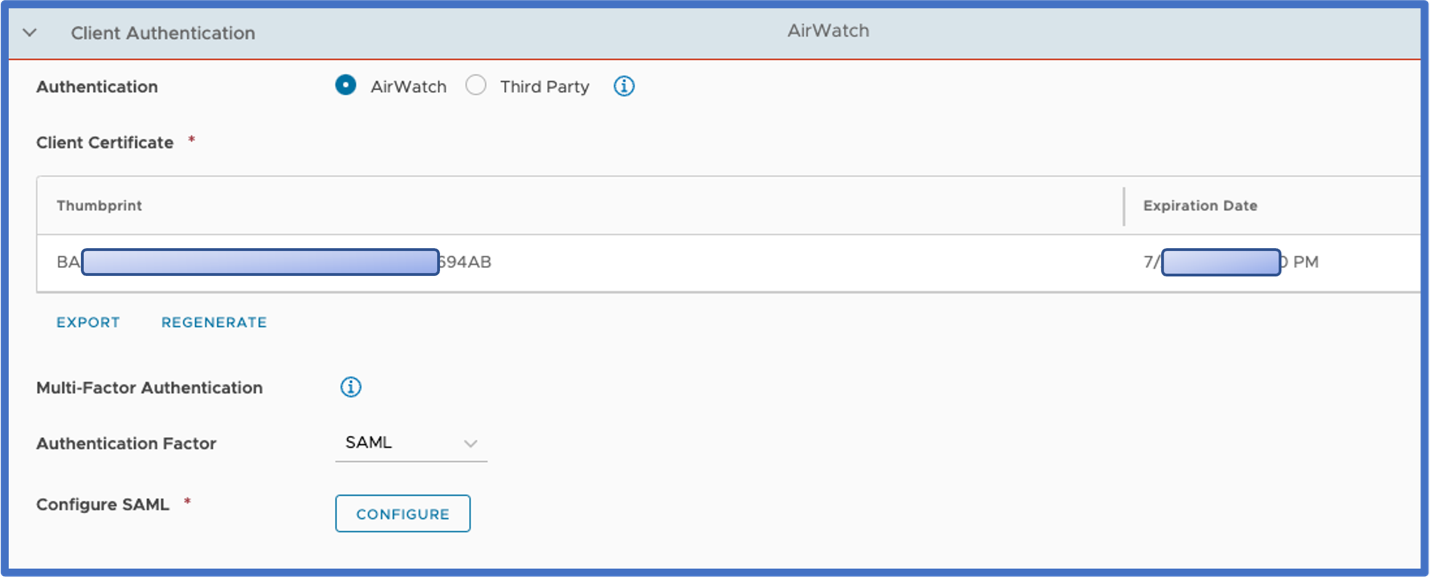
Client Authentication:
Enabling SAML authentication within the VMware Tunnel configuration.
- In UEM 2302 and later, the MFA settings under the Client Authentication sections are available by default.
- For UEM version 2212, this feature is behind a feature flag. Please enable Feature Flag: TunnelMultiFactorAuthenticationFeatureFlag
- This will enable the Multi-factor Authentication option under the Client Authentication section.
- For UEM version 2212, this feature is behind a feature flag. Please enable Feature Flag: DTRDeliveryToTunnelServerFeatureFlag
Steps to setup SAML authentication:
- Select SAML from the dropdown menu as the Authentication factor.
- Click 'Configure' to upload the IDP metadata. The metadata file type should be .XML
- Enter the Application ID as setup on IDP
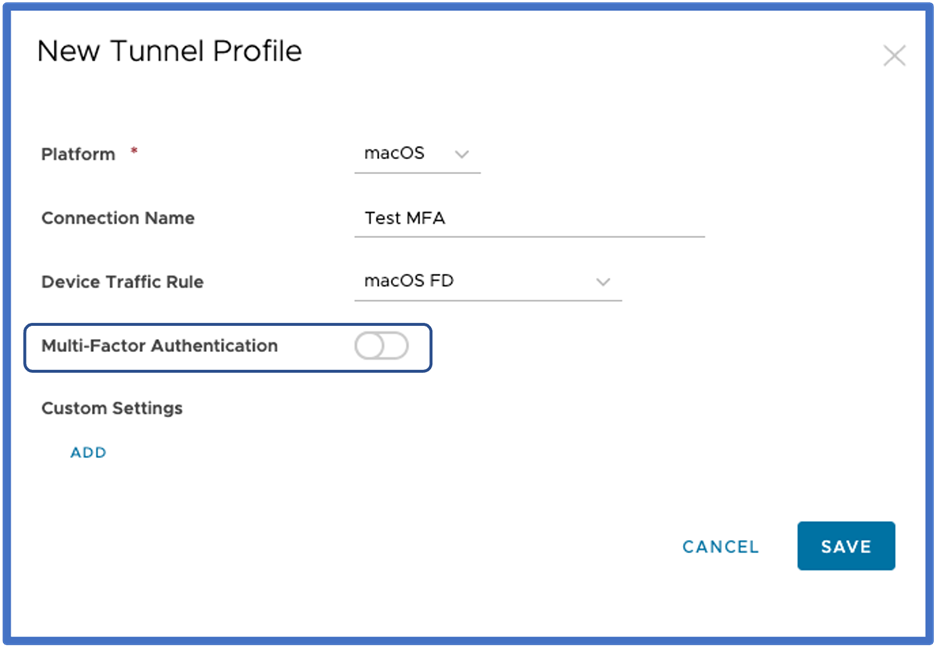
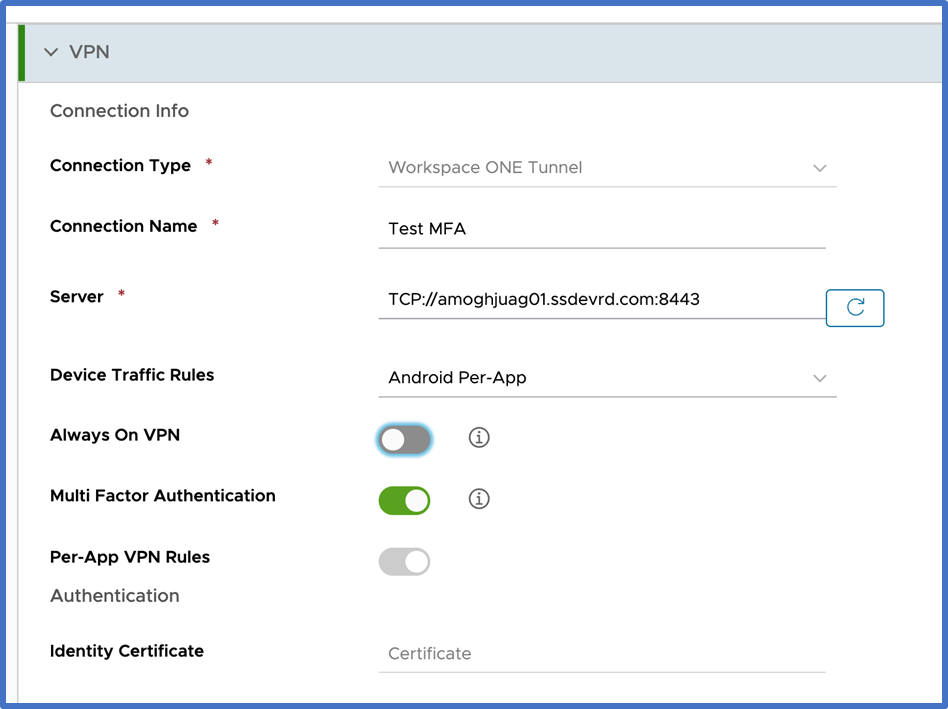
VMware Tunnel Profile:
Session Multi-Factor Authentication (MFA) is available for the Windows client in both Managed and Unmanaged modes. For the macOS client MFA is available in Unmanaged mode. This feature is also a Technical Preview for the Android, and iOS clients in Managed mode.
This feature is currently available only on the Windows and macOS clients in Standalone mode. Please refer to the VMware Tunnel Profile for Standalone Enrollment sections above for information on configuring the standalone Windows and macOS profiles.
The VMware Tunnel profiles of clients that support Session MFA will have a toggle to enable MFA. Once MFA is enabled and the profile saved, all clients that receive this profile will be enabled for MFA. If no toggle is visible, thi smeans that client does not support Session MFA in that specific mode.
- In UEM 2302 and later, this MFA toggle is available by default.
- For UEM version 2212, this feature is behind a feature flag for the Desktop Standalone profiles. You will need to enable Feature Flag: MacOsWindowsTunnelMultiFactorAuthenticationFeatureFlag.
DTR Configuration:
Windows:
- No action required.
Full Device Tunnel Mode:
- If the Default Rule is TUNNEL, add a Rule with Rank 1 to Bypass the IDP-related domains.
- Configure other rules per requirement.
- If the default rule is BYPASS, no additional action is required.
macOS:
- No action required.
The macOS client in Standalone mode currently does not support Per-App Tunnel mode.
Optional Custom Settings:
| Key | Value | Notes |
|---|---|---|
| mfa_session_timeout | 0 | This value is time in minutes. Time for which a continuous connection to the Tunnel server will be established before the session is terminated. A new session will be established immediately if further traffic needs to be tunneled and user will be prompted for SAML authentication |
Part 2: IDP Configurations
We currently support Workspace ONE Access, OKTA, and Microsoft Azure IDPs. Support for other IDPs is on our roadmap. Here is how to setup your VMware Workspace ONE Access tenant for use with VMware Tunnel for this feature.
- Log in to Workspace ONE Access Admin page
- Select Resources
- Select New
- Update the Name & Description
- Upload the tunnel icon if required
- Click Next
- Configuration
- Set the authentication type to SAML 2.0 and configuration type to Manual
- Update the Single Sign-On URL to:
HTTPS://{TunnelserverHostname}:65535/tunnel - Update the Recipient URL to:
HTTPS://{TunnelServerHostname}:65535/tunnel- TunnelServerHostname is the public FQDN for the tunnel server
- This is the same hostname configured with the UEM console for the Tunnel configuration.
- Set the Application ID to VMwareWS1Tunnel
- You may provide a different Application ID. Please enter the same Application ID while uploading the SAML Metadata within WS1 UEM.
- Access Policies
- Select the access policy as desired
- Save and assign the application to the user or user group
- Select New
- Log in to Workspace ONE Access Admin page
- Select Resources
- Select Settings section
- Select SAML Metadata under SaaS Apps
- Click on copy URL for IDP metadata
- Save the SAML metadata
OKTA
- Log in to the OKTA Admin page
- Select Applications
- Application→ Create App Integration→ SAML 2.0
- Click on Next
- Provide "App name"
- Upload the App logo if required
- Check options "Do not display application icon to users" and "Do not display application icon in the OKTA Mobile app"
- This is not mandatory but recommended best practice to disable for Tunnel MFA workflow.
- Click on Next
- Update the Single Sign-On URL to
HTTPS://{TunnelServerHostname}:65535/tunnel- TunnelServerHostname is the public FQDN for the tunnel server
- Update the Audience URI (SP Entity ID) to VMwareWS1Tunnel
- You may provide a different Application ID. Please enter the same Application ID while uploading the SAML Metadata within WS1 UEM.
- Update the Default RelayState to
HTTPS://{TunnelServerHostname}:65535/tunnel- TunnelServerHostname is the public FQDN for the tunnel server
- Keep the Name ID format to unspecified
- Choose the Application username based on your requirement (or keep it to the OKTA username)
- Click Finish
- Click on assignment and assign the application to the user or groups
Steps to retrieve the SAML Metadata
- Log in to the OKTA Admin page
- Select Applications
- Select the application created for the Tunnel SAML MFA
- Select Sign on, scroll down
- Under SAML Signing certificates
- Click on the action drop-down for the active certificate Type ( SHA-1 or SHA-2)
- Select View IDP metadata
- Save the SAML metadata based on the console version
- Under SAML Signing certificates
Microsoft Azure
- Log in to the Azure Admin page
- Select Azure Active Directory
- Select Enterprise applications
- Click on New Application
- Click on Create your own application
- Provide a name for your application
- Select "Integrate any other application you don't find in the gallery (Non-gallery)"
- Click Create
- Select Single Sign-on under Manage
- Select SAML
- Click on Edit for Basic SAML Configuration
- Add the Identifier (Entity ID) as VMwareWS1Tunnel
- You may provide a different Application ID. Please enter the same Application ID while uploading the SAML Metadata within WS1 UEM.
- Update the Reply URL (Assertion Consumer Service URL) to HTTPS://{TunnelServerHostname}:65535/tunnel
- TunnelServerHostname is the public FQDN for the tunnel server
- Add the Sign-on URL and Relay State to HTTPS://{TunnelServerHostname}:65535/tunnel or leave it blank as it is not mandatory
- TunnelServerHostname is the public FQDN for the tunnel server
- Click on Save
- Select Users and Groups
- Assign the application to the user or groups
- Log in to the Azure Admin page
- Select Azure Active Directory
- Select Enterprise applications
- Select Single Sign-on under Manage
- Under SAML Certificates
- Download the Federation Metadata XML
- Under SAML Certificates