Compromised Device Detection with Health Attestation
Health Attestation scans devices during startup for failures in device integrity. Use Health Attestation to detect compromised Windows Desktop devices while managed under Workspace ONE UEM.
In both BYOD and Corporate-Owned device deployments, it is important to know that devices are healthy when accessing corporate resources. The Windows Health Attestation Service accesses device boot information from the cloud through secure communications. This information is measured and checked against related data points to ensure that the device booted up as intended and is not victim to security vulnerabilities or threat. Measurements include Secure Boot, Code Integrity, BitLocker, and Boot Manager.
Workspace ONE UEM enables you to configure the Windows Health Attestation service to ensure device compliance. If any of the enabled checks fail, the Workspace ONE UEM compliance policy engine applies security measures based on the configured compliance policy. This functionality allows you to keep your enterprise data secure from compromised devices. Since Workspace ONE UEM pulls the necessary information from the device hardware and not the OS, compromised devices are detected even when the OS kernel is compromised.
Configure the Health Attestation for Windows Desktop Compliance Policies
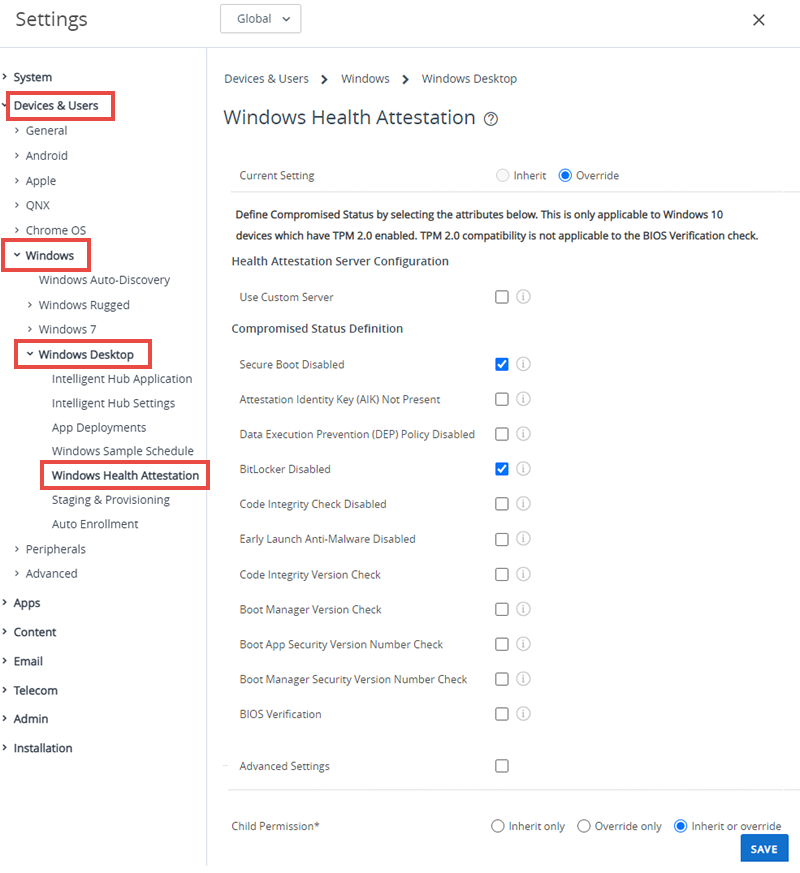
Keep your devices secured by using Windows Health Attestation Service for compromised device detection. This service allows Workspace ONE UEM to monitor the device integrity during startup and take corrective actions.
-
Navigate to Groups & Settings > All Settings > Devices & Users > Windows > Windows Desktop > Windows Health Attestation.
-
Select Use Custom Server if you are using a custom on-premises server running Health Attestation. Enter the Server URL.
-
Configure the Health Attestation settings:
Settings Descriptions Use Custom Server Select to configure a custom server for Health Attestation.
This option requires a server running Windows Server 2016 or newer.
Enabling this option displays the Server URL text box.Server URL Enter the URL for your custom Health Attestation server. Secure Boot Deactivated Enable to flag compromised device status when Secure Boot is deactivated on the device.
Secure Boot forces the system to boot to a factory trusted state. When Secure Boot is enabled, the core components used to boot the machine must have the correct cryptographic signatures that the OEM trusts. The UEFI firmware verifies the trust before it allows the machine to start. Secure boot prevents the startup if any it detects any tampered files.Attestation Identity Key (AIK) Not Present Enable to flag compromised device status when the AIK is not present on the device.
Attestation Identity Key (AIK) is present on a device, it indicates that the device has an endorsement key (EK) certificate. It can be trusted more than a device that does not have an EK certificate.Data Execution Prevention (DEP) Policy Deactivated Enable to flag compromised device status when the DEP is deactivated on the device.
The Data Execution Prevention (DEP) Policy is a memory protection feature built into the system level of the OS. The policy prevents running code from data pages such as the default heap, stacks, and memory pools. DEP is enforced by both hardware and software.BitLocker Deactivated Enable to flag compromised device status when BitLocker encryption is deactivated on the device. Code Integrity Check Deactivated Enable to flag compromised device status when the code integrity check is deactivated on the device.
Code integrity is a feature that validates the integrity of a driver or system file each time it is loaded into memory. Code integrity checks for unsigned drivers or system files before they load into the kernel. The check also scans for users with administrative privileges running system files modified by malicious software.Early Launch Anti-Malware Deactivated Enable to flag compromised device status when the early launch anti-malware is deactivated on the device.
Early launch anti-malware (ELAM) provides protection for the computers in your network when they start up and before third-party drivers initialize.Code Integrity Version Check Enable to flag compromised device status when the code integrity version check fails. Boot Manager Version Check Enable to flag compromised device status when the boot manager version check fails. Boot App Security Version Number Check Enable to flag compromised device status when the boot app security version number does not meet the entered number. Boot Manager Security Version Number Check Enable to flag compromised device status when the boot manager security version number does not meet the entered number. Advanced Settings Enable to configure advance settings in the Software Version Identifiers section. -
Select Save.
Parent topic: Compliance Policies