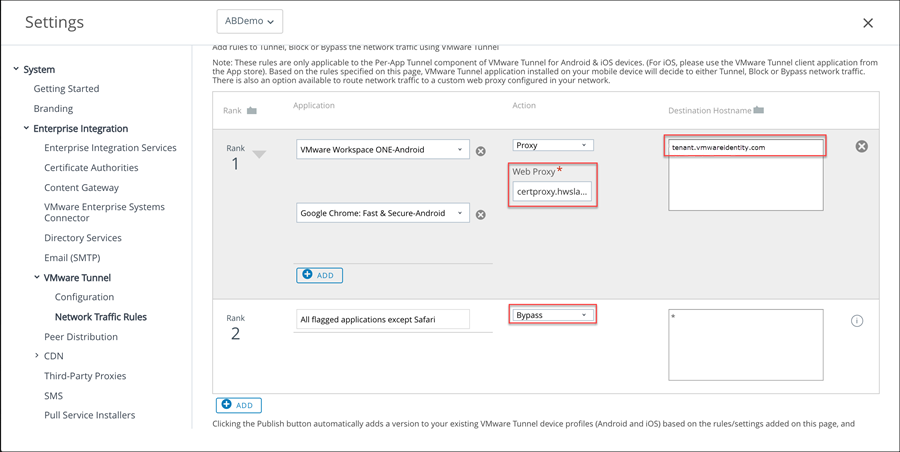
Configure the network traffic rules so that the Workspace ONE Tunnel client routes traffic to the web proxy for Android devices.
You list the Android apps that are configured with the per app VPN option to the traffic rules and configure the proxy server address and the destination host name.
Configure the device traffic rules to control how devices handle traffic from specified applications. Device traffic rules force the Workspace ONE Tunnel app to send traffic through the tunnel, block all traffic to specified domains, bypass the internal network straight to the Internet, or send traffic to a web proxy site.
See the Workspace ONE Access and Hub Services SaaS IP address ranges used for network configuration (68035) article for the list of available Workspace ONE Access SaaS environments with corresponding domains.
For detailed information about creating network traffic rules, see the VMware Tunnel guide.
Prerequisites
- VMware Tunnel is configured with the per-app tunnel component activated.
- Microsoft Intune Company Portal app configured to use the Device Traffic Rules with Android Mobile SSO.
- Android VPN profile created.
- Per-App VPN enabled for each Android app that is added to the Network Traffic rules.
Procedure
- In the Workspace ONE UEM console, navigate to > .
- In the Device Traffic Rules tab, configure the device traffic rules settings as described in the VMware Tunnel Guide. Specific to the Mobile SSO for Android configuration, configure the following settings.
- Default Action. This rule is automatically configured and applies to all applications except Safari. The default action is always applied last.
| Option |
Description |
| Tunnel |
Set the action to Tunnel if VPN access is required for Mobile SSO for Android. All apps, except Safari, on the device configured for Per App VPN send network traffic through the tunnel. |
| Bypass |
Set the Action to Bypass if VPN access is not required for Mobile SSO with Android. All apps, except Safari, on the device configured for Per App VPN bypass the tunnel and connect to the Internet directly.
Important: With this implementation, no traffic is sent to the Tunnel server when the Tunnel client is used only for single sign-on.
|
After the default rule is updated and the action is set to
Bypass, a network traffic rule is added and configured for Android single sign-on.
- Select Add to create additional rules as required.
- Select the up and down arrows to rearrange the ranking of your network traffic rules. The default rule is the last rule in the ranking.
- In the Application column, add the Android apps that are configured with the per app VPN profile.
Note: If Microsoft Office 365 is deployed with the Microsoft Intune Company Portal app, make sure that you add the Microsoft Company Portal app to the list of apps in the Device Traffic Rules.
- For tenants hosted in the cloud, in the Action column, select Proxy and specify the web proxy information. Enter as certproxy.domain. For example, certproxy.workspaceoneaccess.com:5262.
In the Destination Host Name column, enter your destination
Workspace ONE Access host name. Enter as
<tenant>.workspaceoneaccess.com. For example,
myco.workspaceoneaccess.com. The
VMware Tunnel client routes the traffic to the HTTPS proxy from the
Workspace ONE Access host name.
- For on premises, in the Action column, select Proxy and specify the web proxy information. Enter the Workspace ONE Access host name and port. For example, login.example.com:5262.
Note: For on-premises deployments, if you are providing external access to the
Workspace ONE Access host, the firewall port 5262 (configurable) must be opened between devices on the Internet and the
Workspace ONE Access host allowing Layer 4 TCP SSL passthrough on the load balancer/reverse proxy.
- Click Save.
What to do next
Publish these rules. After the rules are published, the device receives an updated VPN profile and the Workspace ONE Tunnel application is configured to enable SSO.
Go to the Workspace ONE Access console and configure Mobile SSO for Android in the Built-in Identity Provider page.