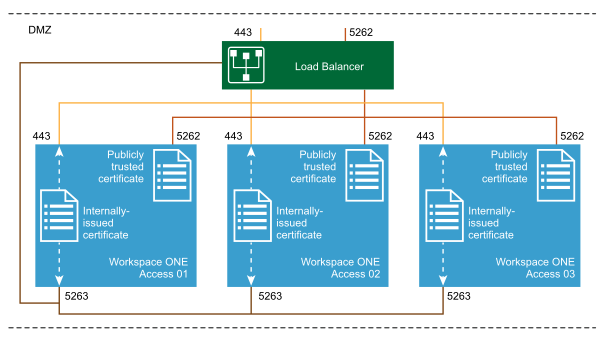
For Android certificate authentication, the cert proxy service runs on the Workspace ONE Access node as an independent service to receive connections on port 5262 and proxy the connections to the Workspace ONE Access service on port 443 for authentication.
The HTTPS 443 traffic for Workspace ONE Access can be either set to Layer 7 SSL offloading on the load balancer/reverse proxy or allowed to SSL passthrough as Layer 4 TCP to the backend server. When 443 traffic is configured with SSL passthrough, the publicly trusted certificate is shared between the Workspace ONE Access service on port 443 and the CertProxy service on port 5262. No additional configuration is needed.
If the HTTPS traffic is SSL offloaded on the load balancer/reverse proxy, the Workspace ONE Access service uses a self-signed certificate for trust which is generated during the application installation process. Because 5262 must be set to SSL Layer 4 TCP with SSL passthrough that requires a publicly trusted SSL certificate, this leads to a certificate mismatch between the two services running on the host. To circumvent this problem, the CertProxy service requires a secondary port 5263 configured on the server. Port 5263 shares the same self-signed certificate as the one running on the Workspace ONE Access service. Configuring the additional port 5263 allows the communication to be secured and trusted throughout the Mobile SSO process for Androids while also allowing HTTPS traffic decryption on the load balancer.
Deciding Between SSL Re-Encryption and SSL Offloading for HTTP 443 Traffic
The following is a decision matrix to help you set up the cert proxy service with the Workspace ONE Access service.
In this matrix, SAN certificates are defined as a certificate containing the Workspace ONE Access VIP FQDN and each node machine FQDN. The FQDN is in the format of a non-routable domain/sub-domain. Based on your VMware design use the matrix to determine if port 5263 is configured.
| Public Namespace | DMZ Namespace | Certificate Type | Load Balancer Requirement | Cert Proxy Port 5263 Required |
|---|---|---|---|---|
| Shared Namespace (.com / .com) | ||||
| example.com | example.com | Wildcard, SAN | SSL Re-encryption required | No |
| example.com | example.com | Single Host CN | SSL Re-encryption required | Yes |
| example.com | example.com | Wildcard, SAN | SSL Passthrough required | No |
| Disjointed Namespace (.com / .dmz) | ||||
| example.com | example.dmz | Wildcard, Single Host CN | SSL Re-encryption required | Yes |
| example.com | example.dmz | SAN | SSL Re-encryption required | No |
| example.com | example.dmz | SAN | SSL Passthrough required | No |