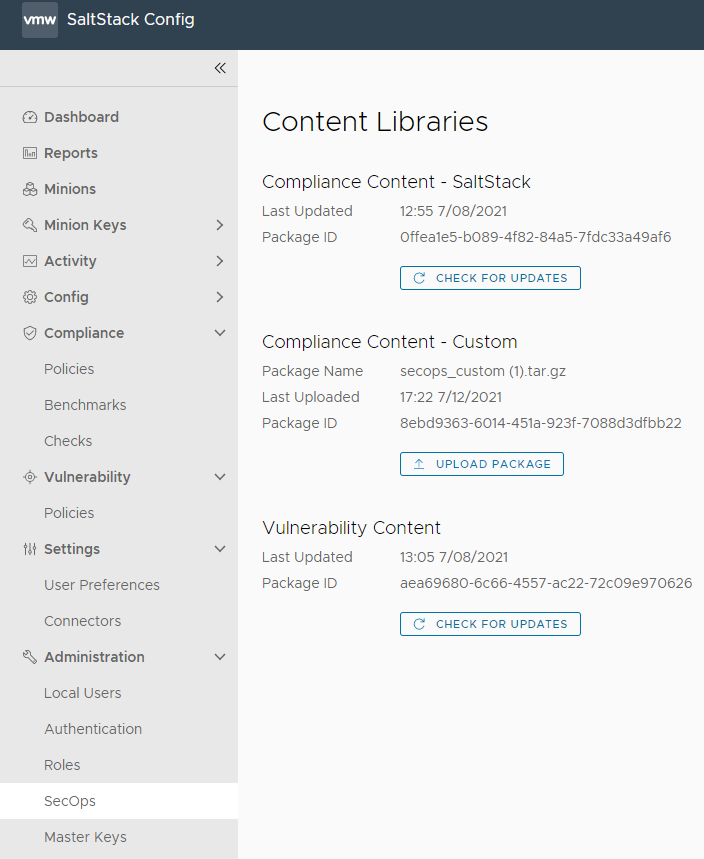
SaltStack Config uses an automated process to search for the latest security advisories along with the software packages or versions to fix nodes that are impacted by those vulnerabilities. This content is built and updated continuously in the vulnerability library.
When a new advisory or remediation is available, SaltStack Config bundles the library into a tarball and makes it available for download to SaltStack SecOps Vulnerability customers. By default, SaltStack Config checks for new content daily.
The vulnerability library tarball is encrypted before it is made available to SaltStack SecOps Vulnerability customers to ensure data integrity. A SaltStack SecOps Vulnerability license comes with the necessary keys to decrypt the tarball once it is downloaded. When SaltStack SecOps Vulnerability ingests a new tarball, it may take 15-20 minutes to get the latest content, which can impact performance. If you use the default process to update the vulnerability library, you should expect this performance delay the first time you download this content after installing and activating SaltStack SecOps Vulnerability. Then, when a new tarball is available for download, it is ingested and updated. However, you can experience the 15-20 minute delay during ingestion again, depending on the timing of the update. You can reduce the possibility of this delay by updating the vulnerability library manually. To update the content manually, click . Under Vulnerability Content click Check for updates.