SaltStack SecOps Compliance is an IT infrastructure security and compliance solution that combines security with IT operations all in a single platform. Its security library contains the latest security standards based on industry best practice hardening guides such as CIS, and more. It uses the library to not only assess your infrastructure security, but also to remediate noncompliant systems instantly.
To use SaltStack SecOps Compliance, first define a policy, then scan systems against the policy. The scan detects non-compliant systems, and allows you to remediate issues instantly. Additionally, you can enter exemptions and specify user permissions to ensure all paths to remediation are customized for your organization’s needs.
This section describes how to use SaltStack SecOps Compliance in the SaltStack Config user interface. However, you can also use SaltStack SecOps Compliance through the API (RaaS). See the API (RaaS) RPC endpoint documentation or contact an administrator for assistance.
SaltStack SecOps Compliance harnesses Salt’s powerful configuration management and remote execution capabilities to bring all of your infrastructure assets to compliance with a range of industry-wide security benchmarks. It integrates with SaltStack Config to apply security measures at scale, while respecting custom exemptions based on your organization’s needs.
Policies
To secure your infrastructure assets with SaltStack SecOps Compliance, start by defining policies. SaltStack SecOps Compliance provides different industry benchmarks to choose from including checks for CIS and more. For more on defining policies, see Building a policy.
Each benchmark includes a collection of security checks. You can choose to apply all available checks for a given benchmark, or use only a subset of available checks. Using a subset of checks is useful for customizing SaltStack SecOps Compliance for your unique infrastructure needs, for example if remediating a given check poses the risk of breaking a known dependency. For more on benchmarks and checks, see Compliance policies.
Assessments and remediation
SaltStack SecOps Compliance uses your compliance policy as the basis for assessing your infrastructure’s security. Following each assessment, SaltStack SecOps Compliance provides a report highlighting any noncompliant systems, along with the recommended remediation. See Running an assessment.
Following an assessment, you can remediate any non-compliant nodes. For convenience, SaltStack SecOps Compliance allows you to remediate all at once, or remediate only a subset of either nodes or checks. For more on remediation, see Remediating all checks.
Customization
To customize SaltStack SecOps Compliance for your organization’s needs, you can exempt certain checks and nodes from remediation. You can also insert variable values to enforce requirements that are stricter than industry standards. For more on exemptions, see Adding exemptions.
Another customization method is to configure user permissions to allow only certain users to remediate, while allowing others to assess or define policies. This offers you complete control over every action taken. For more on permissions, see Roles and permissions.
Building a policy
- In the SaltStack SecOps Compliance home page, click Create policy.
- Enter the policy name and select a target to apply the policy to. Then click Next.
Note:
A target is the group of minions, across one or many Salt masters, that a job’s Salt command applies to. A Salt master can also be managed like a minion and can be a target if it is running the minion service. Minions are nodes running the minion service, which can listen to commands from a Salt master and perform the requested tasks. See Minions for more information.
- In the Benchmarks tab, select all benchmarks you want to include in the policy, then click Next.
If no benchmarks display, you may need to download compliance content. See Updating the security library or contact your administrator for assistance.
Note:When working with Windows Server benchmarks, make sure to look closely at the content included in the benchmarks you select. The CIS content for certain benchmarks (notated with a tooltip
 ) is distributed across three different benchmarks as follows:
) is distributed across three different benchmarks as follows:- Domain master content
- Member content
- Domain master and member content
This means that if you want to include all Member content, you must select both the benchmarks for “Member”, and also for “Domain master and member”.
- In the Checks tab, select all checks you want to include in the policy. The available checks are determined by the selected Benchmarks.
To see more details about a check, such as description and the associated remediation, click the double arrows icon
 to open a detail pane.
to open a detail pane.Custom checks include a user icon
 , in contrast with SaltStack checks
, in contrast with SaltStack checks  .
.For more on understanding checks, see Compliance policies.
To filter the list, click the Filter button
 . You can remove active filters by clicking Clear Filters.Note:
. You can remove active filters by clicking Clear Filters.Note:Policies that include many checks might result in long processing times during assessment. This could also delay other processes, such as jobs running, in SaltStack Config. Make sure to include only the checks you need, and account for extra time required to run large assessments.
- Click Next.
- In the Variables tab, enter or modify variables according to your needs, or accept the default values. Then click Next.
Note:
The values you enter define how SaltStack SecOps Compliance performs the selected checks. The default values are recommended. For more on variables, see Compliance policies.
- In the Schedule screen, define schedule frequency and click Save. For more on defining schedule settings, see Compliance policies.
- (Optional) Select Run assessment on save.
- Click Save.
The policy is now saved. If you chose to run an assessment on save, the assessment is now running.
Editing a policy
- In the SaltStack SecOps Compliance home page, select the policy you want to edit.
- In the policy screen, click Edit policy in the upper-right corner.
- Edit the policy as needed and click Save.
Updating the security library
- Click Administration > SecOps on the side menu.
- Under Compliance Content - SaltStack, click Check for updates.
Running an assessment
Policies that include many checks might result in long processing times during assessment. This could also delay other processes, such as jobs running, in SaltStack Config. Make sure to account for extra time required to run large assessments.
- In the SaltStack SecOps Compliance home page, select a policy.
- In the policy home page, click Run assessment. The Activity screen opens.
Completed assessments are listed in the Activity screen along with their status, Job ID (JID), and other information.
Note:During the assessment, no changes are made. You will have the ability to remediate any issues later. See Remediating all checks.
Viewing assessment results
- In the SaltStack SecOps Compliance home page, select a policy.
- The policy home page shows results from the most recent assessment, organized by check.
To filter the list, click the Filter button
 . You can remove active filters by clicking Clear Filters.
. You can remove active filters by clicking Clear Filters.You can also select a column heading to sort results, for example you might sort the Not compliant column to view non-compliant nodes first.
You can select the Minions tab to view assessment results by minion.
Note:Before you can view assessment results, you must first run the assessment. See Running an assessment.
Understanding assessment results
For an assessment results reference, see Assessment results.
Downloading the assessment report
- In the SaltStack SecOps Compliance home page, select a policy to view the latest assessment results.
- In the policy home page, go to the Report tab and click Download.
- In the resulting dropdown, select JSON.
Your web browser begins downloading the report.
Remediating all checks
Once non-compliant systems have been identified, the next step is to remediate. You can choose to remediate individual checks or nodes (referred to as minions), or you can alternatively remediate all checks on all nodes. However, when you run Remediate all, any exempted checks or nodes are not remediated.
To remediate all checks on all minions:
- In the SaltStack SecOps Compliance home page, select a policy to view the most recent assessment results.
- In the Checks tab, click Remediate all in the upper-right corner.
- In the confirmation dialog, click Remediate all.
SaltStack SecOps Compliance begins remediating all checks on all non-compliant nodes. You can track the status of the remediation in the Activity tab.
- Once the remediation is complete, run a new assessment to confirm your systems are now compliant.
Note:
In order to achieve full compliance, you might need to repeat the process of remediating and scanning multiple times, especially if you have run Remediate all against many non-compliant checks. This is because some checks are dependent on the completion of others. For example, one check might require a package that’s deployed by another check before it can be remediated properly.
Remediating by check
- In the policy screen, select a check to open the check description.
- Scroll down past the check description to a list of results from your last assessment. The results are ordered by minion.
If a column header includes a filter icon
 , you can filter the results by that column type. Click the icon and select a filter option from the menu or type the text you want to filter by. You can remove active filters by clicking Clear Filters.
, you can filter the results by that column type. Click the icon and select a filter option from the menu or type the text you want to filter by. You can remove active filters by clicking Clear Filters. - Select all minions you want to remediate for the active check.
- Click Remediate.
Remediating by minion
- In the policy screen, go to the Minions tab and select a minion.
- Select all checks you want to remediate for the active minion.
If a column header includes a filter icon
 , you can filter the results by that column type. Click the icon and select a filter option from the menu or type the text you want to filter by. You can remove active filters by clicking Clear Filters.
, you can filter the results by that column type. Click the icon and select a filter option from the menu or type the text you want to filter by. You can remove active filters by clicking Clear Filters. - Click Remediate.
Adding exemptions
- In the policy screen, select the checks you want to exempt from remediation.
- Click Add exemption.
- Enter the reason for exemption and click Add exemption to confirm. You can always remove the exemptions later if needed.
Exempted items will not be remediated. If a remediation runs against a policy that includes the exempted item, the remediation is skipped for that item.
Note:You can add an exemption either before or after running the assessment. You can also define a customized policy that excludes checks based on your needs. See Building a policy.
Adding exemptions by minion
- In the policy screen, go to the Minions tab.
- Select the minions you want to exempt from remediation.
- Click Add exemption.
- Enter the reason for exemption and click Add exemption to confirm. You can always remove the exemptions later if needed.
Exempted items will not be remediated. If a remediation runs against a policy that includes the exempted item, the remediation is skipped for that item.
Removing an exemption
- In the policy screen, go to the Exemptions tab.
- Scroll up and down the page to view a list of all exemptions.
Note:
There might be more exemptions off-screen when you first open the Exemptions tab. Keep scrolling to the bottom of the screen to view all exemptions.
- Click the dropdown for the exemption you want to remove.
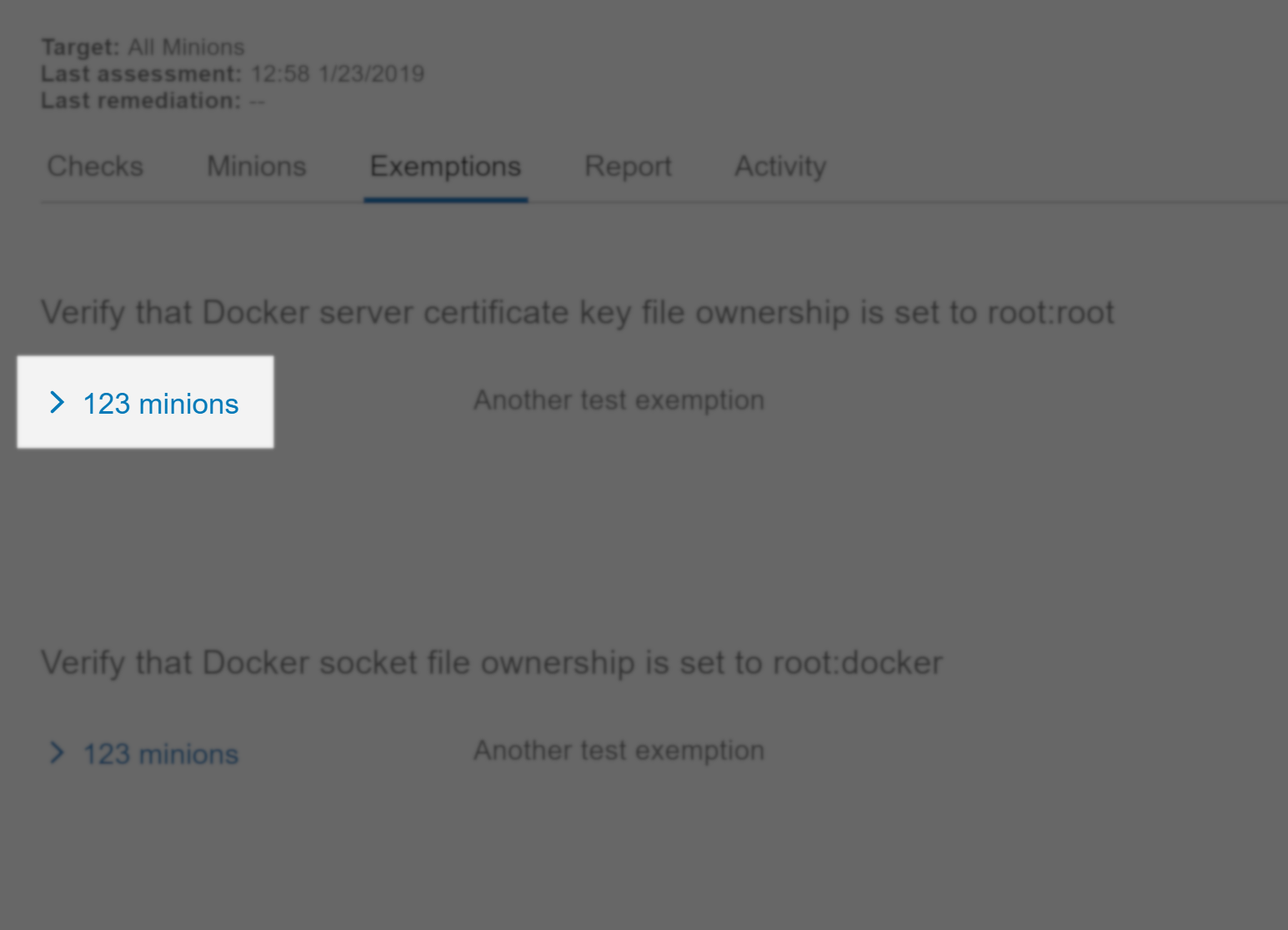
This opens a list of all affected minions.
- Click Remove exemption.
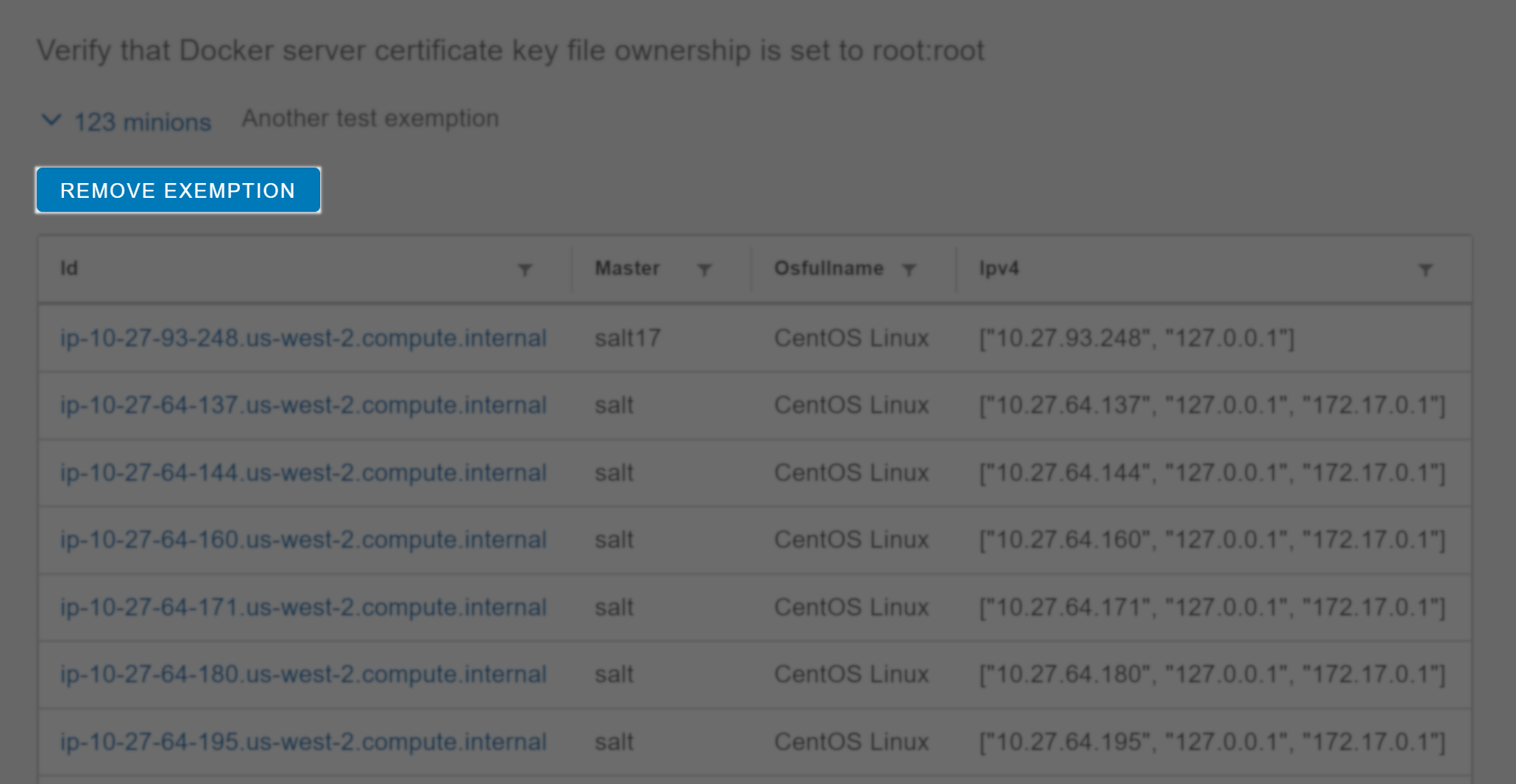
- In the confirmation dialog, click Remove exemption.
Defining SaltStack SecOps Compliance permissions
Go to the permissions editor to modify SaltStack SecOps Compliance permissions. For more on SaltStack Config roles and permissions, see Roles and permissions.
The SaltStack SecOps Compliance content library
The SaltStack SecOps Compliance content library consists of pre-built, industry best-practice security and compliance content, including:
- CIS
Compliance policies
Compliance policies are collections of security checks, and specifications for which nodes each check applies to, in SaltStack SecOps Compliance. Policies can also include schedules, as well as specifications for handling exemptions.
Each component of a security policy is described in more detail below.
Target
A target is the group of minions, across one or many Salt masters, that a job’s Salt command applies to. A Salt master can also be managed like a minion and can be a target if it is running the minion service. When you choose a target in SaltStack SecOps Compliance, you define the nodes you want to run security checks against. You can choose an existing target or create a new one. See Minions for more information.
Benchmarks
Benchmarks are categories of security checks. SaltStack SecOps Compliance benchmarks are defined by widely-accepted experts, while custom benchmarks can be defined by your own organization’s standards. You can use benchmarks to help create a range of different policies optimized for different groups of nodes. For example, you might create an Oracle Linux policy that applies CIS checks to your Oracle Linux minions, and a Docker policy that applies CIS checks to your Docker minions.
See SaltStack SecOps Compliance Custom Content for more on creating custom checks and benchmarks.
SaltStack SecOps Compliance helps simplify the process of defining your security policy by grouping security checks by benchmark.
Checks
A check is a security standard that SaltStack SecOps Compliance assesses for compliance. The SaltStack SecOps Compliance library updates checks frequently as security standards change. In addition to checks included the SaltStack SecOps Compliance content library, you can create your own custom checks. Custom checks include a user icon  , in contrast with SaltStack checks
, in contrast with SaltStack checks  . See SaltStack SecOps Compliance Custom Content for more on creating custom checks and benchmarks.
. See SaltStack SecOps Compliance Custom Content for more on creating custom checks and benchmarks.
Each check includes the following information fields.
- Description
- Brief description of the check.
- Action
- Brief description of the action that will be taken upon remediation.
- Break
- Used for internal testing purposes only. For more information, contact your administrator.
- Global description
- Detailed description of the check.
- Osfinger
- List of osfinger values the check is implemented for. osfinger is found in grains.items for each minion. It identifies the minion’s operating system and major release version. Grains are an interface that derives information about the underlying system. Grains are collected for the operating system, domain name, IP address, kernel, OS type, memory, and many other system properties. For more on grains, see Salt grains reference.
- Profile
- List of configuration profiles for different benchmarks. These configuration profiles target a machine’s different roles within an environment (for example, on a server or a workstation), and different levels of security in contrast with practical use.
- Rationale
- Description of the rationale for implementing the check. This includes reasons why you might want to implement the check.
- Refs
- Compliance cross-references between benchmarks.
- Remediate
- (Not included in all checks) - Value that indicates whether SaltStack SecOps Compliance is capable of remediating noncompliant nodes, as not all checks include specific, actionable remediation steps. For example, SaltStack SecOps Compliance doesn’t remediate CIS 1.1.6: Ensure separate partition exists for /var since no one universal method exists for repartitioning every system. False indicates a check that can’t be remediated. When True (default), this field is not displayed.
- Remediation
- Description of how any noncompliant systems will be remediated, if applicable. Note that some checks don’t include specific, actionable remediation steps. See Remediate above.
- Scored
- CIS benchmark Scored value. Scored recommendations impact the target’s benchmark score, while recommendations that are not scored do not affect the score. True indicates scored and False indicates not scored.
- State file
- Copy of the Salt State that will be applied to execute the check and if applicable, the subsequent remediation.
Variables
Variables in SaltStack SecOps Compliance are used to pass values into the Salt States that make up security checks. For best results, use the default values provided.
For more on Salt States, see the Salt States tutorial.
Schedules
Choose the schedule frequency from Recurring, Repeat Date & Time, Once, or Cron Expression. Additional options are available, depending on the scheduled activity, and on the schedule frequency you choose.
- Recurring
- Set an interval for repeating the schedule, with optional fields for start or end date, splay, and maximum number of parallel jobs.
- Repeat Date & Time
- Choose to repeat the schedule weekly or daily, with optional fields for start or end date, and maximum number of parallel jobs.
- Once
- Specify a date and time to run the job.
- Cron
- Enter a cron expression to define a custom schedule based on Croniter syntax. See the CronTab editor for syntax guidelines. For best results, avoid scheduling jobs fewer than 60 seconds apart when defining a custom cron expression.
Activity status
In your policy home page, the Activity tab shows a list of completed or in-progress assessments and remediations. It includes the following statuses.
| Status | Description |
|---|---|
| Queued | The operation is ready to run, but minions have not yet picked up the task to begin the operation. |
| Completed | The operation has finished running. |
| Partial | The operation is still waiting for some minions to return, though the Salt master has reported that the operation has finished running. Minions are nodes running the minion service, which can listen to commands from a Salt master and perform the requested tasks. The Salt master is a central node used to issue commands to minions. |
You can track all activity in SaltStack Config, including assessments and remediations, in the SaltStack Config main Activity workspace. See Activity.
Assessment results
Refer to the following to understand assessment results. For more on how to access assessment results, see Viewing assessment results.
Return statuses
Following a remediation, SaltStack SecOps Compliance labels each system with one of the following return statuses.
- Compliant
- Setting is in its intended state compared to the standard or benchmark.
- Not compliant
- Setting is not in its intended state compared to the standard or benchmark. Further investigation and possible remediation are recommended.
- Not Applicable
- The setting is not applicable to this system, for example, if a running a CentOS check on AIX.
- Unknown
- Assessment or remediations have not been run.
- Error
- SaltStack SecOps Compliance encountered an error while running the assessment or remediation.