To secure your infrastructure assets with SaltStack SecOps Compliance, you must start by defining policies.
SaltStack SecOps Compliance provides different industry benchmarks to choose from including checks for Center for Internet Security (CIS) and more. Each benchmark includes a collection of security checks. You can choose to apply all available checks for a given benchmark, or use only a subset of available checks. Using a subset of checks is useful for customizing SaltStack SecOps Compliance for your unique infrastructure needs, for example if remediating a given check poses the risk of breaking a known dependency.
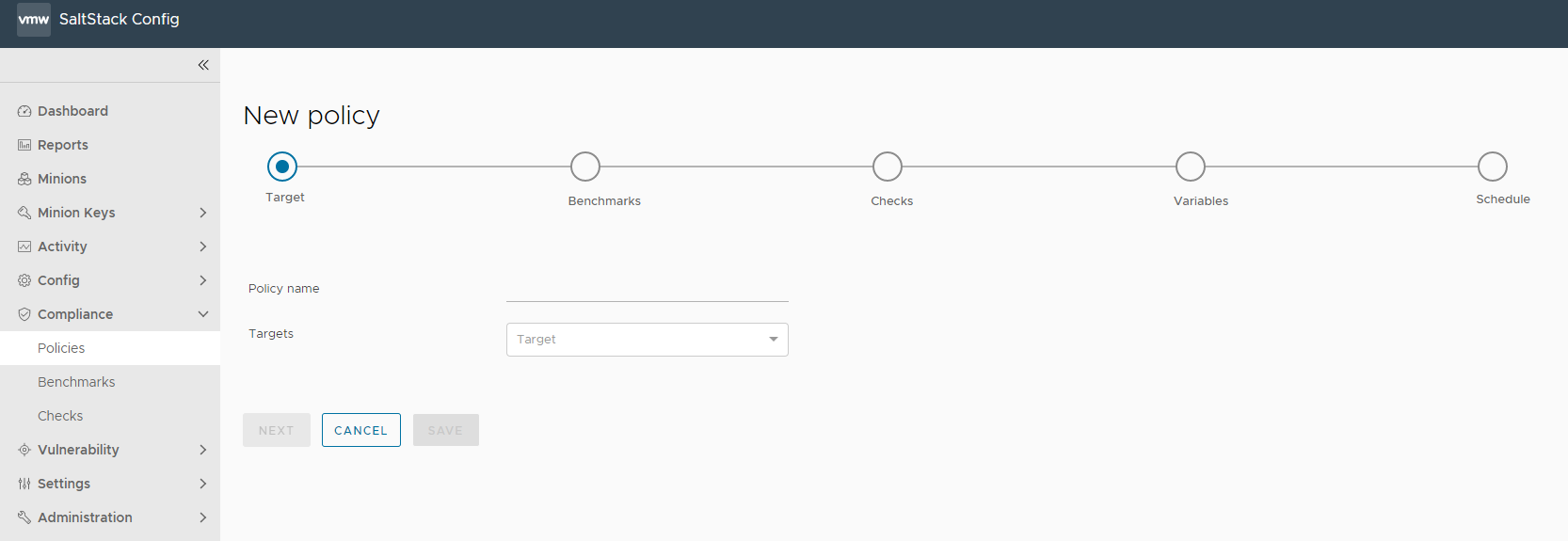
When creating your policy, you must select a target to apply the policy to, along with which benchmarks and checks to run against your system.
To connect to the SDK directly, see vRealize Automation SaltStack Config SecOps.
Target
A target is the group of minions, across one or many Salt masters, that a job’s Salt command applies to. A Salt master is managed similarly to a minion and can be a target if it is running the minion service. When creating a policy and selecting a target, you are defining the nodes that the security checks are run against. You can choose an existing target or create a new one.
For more information, see Minions.
Benchmarks
SaltStack SecOps Compliance simplifies the process of defining your security policy by grouping security checks by benchmark.
Benchmarks are category of security checks. SaltStack SecOps Compliance benchmarks are defined by widely-accepted experts, while custom benchmarks are defined by your own organization’s standards. You can use benchmarks to help create a range of different policies optimized for different groups of nodes. For example, you might create an Oracle Linux policy that applies CIS checks to your Oracle Linux minions, and a Windows policy that applies CIS checks to your Windows minions. For more information on creating custom content, see Creating custom compliance components.
 ) is distributed across three different benchmarks:
) is distributed across three different benchmarks:
- Domain master content
- Member content
- Domain master and member content
Checks
 custom-checks-user-icon, instead of the
custom-checks-user-icon, instead of the
 built-in-checks-shield-icon. For more information on creating custom content, see
Creating custom compliance components. Each check includes several information fields.
built-in-checks-shield-icon. For more information on creating custom content, see
Creating custom compliance components. Each check includes several information fields.
| Information field | Description |
|---|---|
| Description | Description of the check. |
| Action | Description of the action that is performed during remediation. |
| Break | Used for internal testing only. For more information, contact your administrator. |
| Global Description | Detailed description of the check. |
| Osfinger | List of osfinger values that the check is implemented for. Osfinger is found in grains items for each minion to identify the minion's operating system and major release version. Grains are collected for the operating system, domain name, IP address, kernel, OS type, memory, and other system properties. |
| Profile | List of configuration profiles for different benchmarks. |
| Rationale | Description of rationale for implementing the check. |
| Refs | Compliance cross-references between benchmarks. |
| Remediate | Values that indicate if SaltStack SecOps Compliance is capable of remediating noncompliant nodes, as not all checks include specific, actionable remediation steps. |
| Remediation | Description of how any noncompliant systems are remediated, if applicable. |
| Scored | CIS benchmark Scored value. Score recommendations impact the target's benchmark scroe, while recommendation that are not scored do not affect the score. True indicates scored and false indicates not scored. |
| State file | Copy of the Salt state that is applied to perform the check and if applicable, the subsequent remediation. |
| Variables | Variables in SaltStack SecOps Compliance used to pass values into the Salt states that make up security checks. For best results, use the default values.For more information, see How do I use Salt States. |
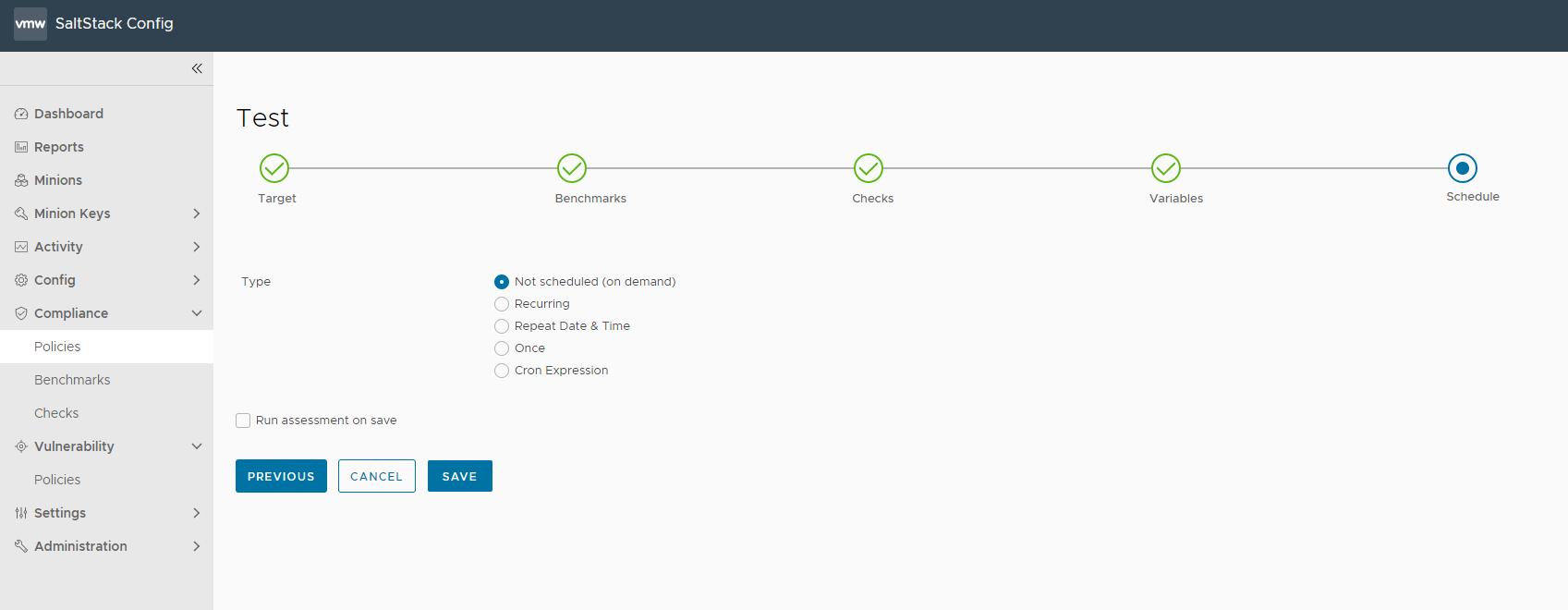
| Schedules | Select the schedule frequency from Recurring, Repeart Date & Time, Once, or Cron Expression. Additional options are available, depending on the scheduled activity, and on the schedule frequency you choose.
Note: In the schedule editor, the terms “Job” and “Assessment” are used interchangeably. When you define a schedule for the policy, you are scheduling the assessment only - not the remediation.
Note: When defining an assessment schedule, you can choose the
Not Scheduled (on demand) option. If you select this option, you choose to run a one-time assessment, and no schedule is defined.
|
Procedure
Results
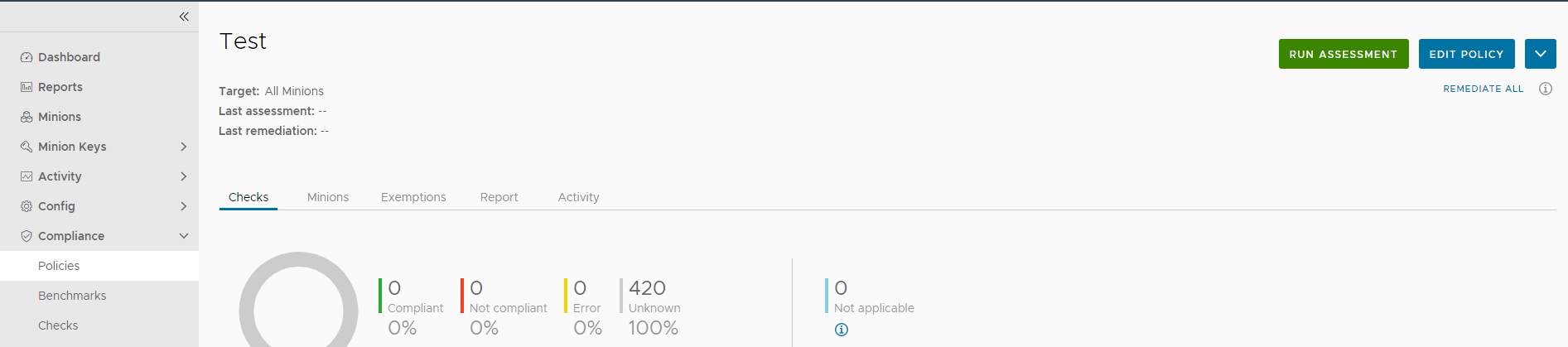
The compliance policy is saved and used to run an assessment. You can edit the policy by selecting the policy from the home page, and clicking Edit Policy.