The Check Point Management Server should accept API access from the Collector IP address.
You can set up the access from Check Point SmartConsole application. Go to , and in the Management API Setting window, select All IP addresses.
If Check Point MDS is added as data-source, vRealize Network Insight fetches data from all the user-defined domains and the global domain.
vRealize Network Insight uses Check Point public Web API for fetching the data from the Check Point management server. If the VSX gateway is attached to the management server, we use SSH-based CLI commands to fetch the VSX-managed Virtual System VS routing table to support display of the VS gateway in the VM-VM path.
- If a non-VSX physical gateway is attached to the management server, the user should have read-write access privileges for the Web API. This is required to fetch the gateway routes for using the
run scriptWeb API for the VM-VM path computation. - If a VSX gateway is attached to the management server, the user should have the SSH access with the same password. In addition, the user should have access to the CLI command
vsx_util view_vs_conf. This command is used to fetch the VSX gateway routes for the VM-VM path computation. - For MDS server IP as data-source, the user should have the Web API access to all domains including the MDS domain and the global domain. It is required to fetch rules, policy packages and other data from all the domains.
Check Point. Some of the queries for Check Point are as follows:
| Entities in Check Point | Keywords | Queries |
|---|---|---|
| IPset | |
|
| Grouping | Check Point Network Group |
|
| Service/ Service Group |
|
|
| Access Layer | Check Point Access Layer |
Check Point Policy where Access Layer = <> |
| Domain | Check Point Domain |
|
| Gateways and Gateway Cluster |
|
Check Point Gateway Cluster where Policy Package = <> |
| Policy Package | Check Point Policy package |
|
| Policy | Check Point Policy |
|

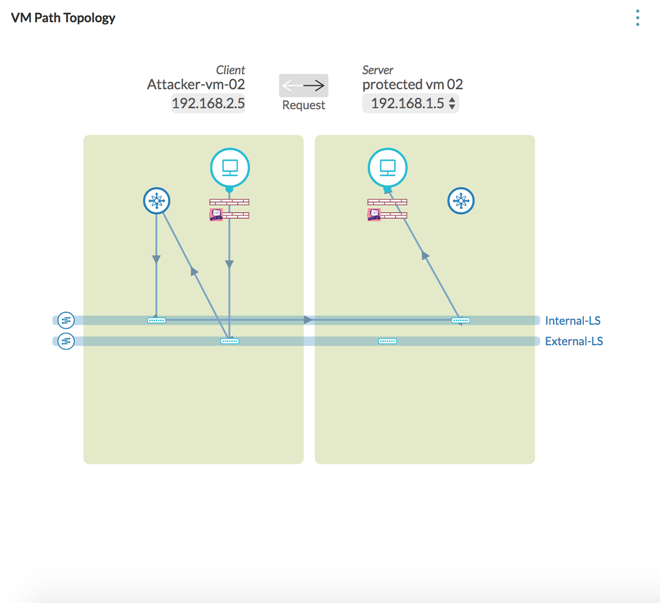
- The NSX fabric agent is not found on the ESX for the Check Point gateway.
- The Check Point service VM is not found.
- The Check point gateway
sicstatus is not communicating. - The discovery and update events features for the Check Point entities like address range, networks, policies, groups, policy package, service, service group, and so on