vCenter Single Sign-On allows vSphere components to communicate with each other through a secure token mechanism.
- STS (Security Token Service).
- SSL for secure traffic.
- Authentication of human users through Active Directory or OpenLDAP.
- Authentication of solution users through certificates.
vCenter Single Sign-On Handshake for Human Users
The following illustration shows the handshake for human users.

- A user logs in to the vSphere Client with a user name and password to access the vCenter Server system or another vCenter service.
The user can also log in without a password and check the Use Windows session authentication check box.
- The vSphere Client passes the login information to the vCenter Single Sign-On service, which checks the SAML token of the vSphere Client. If the vSphere Client has a valid token, vCenter Single Sign-On then checks whether the user is in the configured identity source (for example, Active Directory).
- If only the user name is used, vCenter Single Sign-On checks in the default domain.
- If a domain name is included with the user name (DOMAIN\user1 or user1@DOMAIN), vCenter Single Sign-On checks that domain.
- If the user can authenticate to the identity source, vCenter Single Sign-On returns a token that represents the user to the vSphere Client.
- The vSphere Client passes the token to the vCenter Server system.
- vCenter Server checks with the vCenter Single Sign-On server that the token is valid and not expired.
- The vCenter Single Sign-On server returns the token to the vCenter Server system, using the vCenter Server Authorization Framework to allow user access.
vCenter Single Sign-On Handshake for Solution Users
Solution users are sets of services that are used in the vCenter Server infrastructure, for example, the vCenter Server or vCenter Server extensions. VMware extensions and potentially third-party extensions might also authenticate to vCenter Single Sign-On.
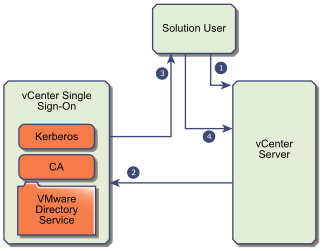
- The solution user attempts to connect to a vCenter service.
- The solution user is redirected to vCenter Single Sign-On. If the solution user is new to vCenter Single Sign-On, it has to present a valid certificate.
- If the certificate is valid, vCenter Single Sign-On assigns a SAML token (bearer token) to the solution user. The token is signed by vCenter Single Sign-On.
- The solution user is then redirected to vCenter Single Sign-On and can perform tasks based on its permissions.
- The next time the solution user has to authenticate, it can use the SAML token to log in to vCenter Server.
By default, this handshake is automatic because VMCA provisions solution users with certificates during startup. If company policy requires third-party CA-signed certificates, you can replace the solution user certificates with third-party CA-signed certificates. If those certificates are valid, vCenter Single Sign-On assigns a SAML token to the solution user. See Use Custom Certificates With vSphere.
Supported Encryption
AES encryption, which is the highest level of encryption, is supported. The supported encryption affects security when vCenter Single Sign-On uses Active Directory as an identity source.
It also affects security any time an ESXi host or vCenter Server is joined to Active Directory.