A cloned, encrypted virtual machine is encrypted with the same keys unless you change them. To change keys, you can use the vSphere Client, the PowerCLI, or the API. If you use the PowerCLI or the API, you can clone the encrypted virtual machine and change keys in one step.
You can perform the following operations during clone.
- Create an encrypted virtual machine from an unencrypted virtual machine or template virtual machine.
- Create a decrypted virtual machine from an encrypted virtual machine or template virtual machine.
- Recrypt the destination virtual machine with different keys from that of source virtual machine.
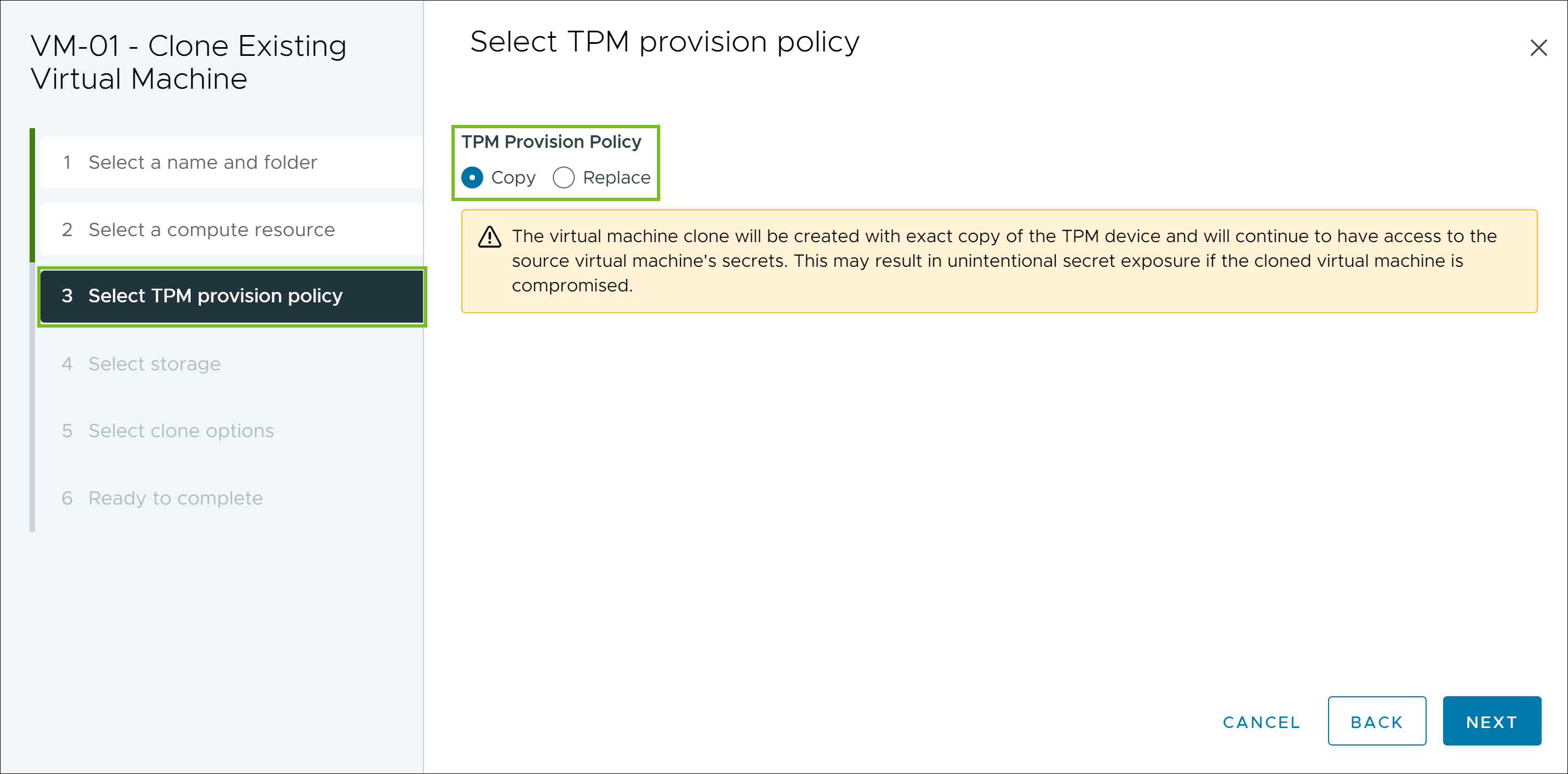
- In vSphere 8.0 and later, selecting the Replace option for a virtual machine with a vTPM starts with a new, blank vTPM, which gets its own secrets and identity.
Note: vSphere 8.0 and later includes the
vpxd.clone.tpmProvisionPolicy advanced setting to make the default clone behavior for vTPMs to be "replace."
You can create an instant clone virtual machine from an encrypted virtual machine with the caution that the instant clone shares the same key with the source virtual machine. You cannot recrypt keys on either the source or the instant clone virtual machine.
To use the API to clone encrypted machines, see vSphere Web Services SDK Programming Guide.
Prerequisites
- A key provider must be configured and enabled.
- Create an encryption storage policy, or use the bundled sample, VM Encryption Policy.
- Required privileges (applies to all key providers):
- If the host encryption mode is not enabled, you also must have privileges.