The ESXi system is designed so that you can connect some groups of virtual machines to the internal network, others to the external network, and still others to both—all on the same host. This capability is an outgrowth of basic virtual machine isolation coupled with a well-planned use of virtual networking features.
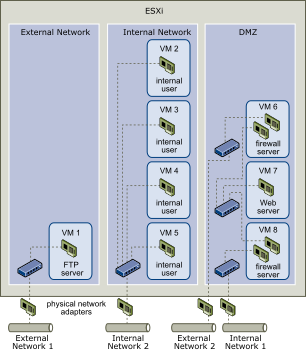
In the figure, the system administrator configured a host into three distinct virtual machine zones: FTP server, internal virtual machines, and DMZ. Each zone serves a unique function.
FTP Server Zone
Virtual Machine 1 is configured with FTP software and acts as a holding area for data sent to and from outside resources such as forms and collateral localized by a vendor.
This virtual machine is associated with an external network only. It has its own virtual switch and physical network adapter that connect it to External Network 1. This network is dedicated to servers that the company uses to receive data from outside sources. For example, the company uses External Network 1 to receive FTP traffic from vendors and allow vendors access to data stored on externally available servers though FTP. In addition to servicing Virtual Machine 1, External Network 1 services FTP servers configured on different ESXi hosts throughout the site.
Because Virtual Machine 1 does not share a virtual switch or physical network adapter with any virtual machines in the host, the other resident virtual machines cannot transmit packets to or receive packets from the Virtual Machine 1 network. This restriction prevents sniffing attacks, which require sending network traffic to the victim. More importantly, an attacker cannot use the natural vulnerability of FTP to access any of the host’s other virtual machines.
Internal Network Zone
Virtual Machines 2 through 5 are reserved for internal use. These virtual machines process and store company-private data such as medical records, legal settlements, and fraud investigations. As a result, the system administrators must ensure the highest level of protection for these virtual machines.
These virtual machines connect to Internal Network 2 through their own virtual switch and network adapter. Internal Network 2 is reserved for internal use by personnel such as claims processors, in-house lawyers, or adjustors.
Virtual Machines 2 through 5 can communicate with one another through the virtual switch and with internal virtual machines elsewhere on Internal Network 2 through the physical network adapter. They cannot communicate with externally facing machines. As with the FTP server, these virtual machines cannot send packets to or receive packets from the other virtual machines’ networks. Similarly, the host’s other virtual machines cannot send packets to or receive packets from Virtual Machines 2 through 5.
DMZ Zone
Virtual Machines 6 through 8 are configured as a DMZ that the marketing group uses to publish the company’s external website.
This group of virtual machines is associated with External Network 2 and Internal Network 1. The company uses External Network 2 to support the Web servers that use the marketing and financial department to host the corporate website and other Web facilities that it hosts to outside users. Internal Network 1 is the conduit that the marketing department uses to publish its content to the corporate Web site, post downloads, and maintain services like user forums.
Because these networks are separate from External Network 1 and Internal Network 2, and the virtual machines have no shared points of contact (switches or adapters), there is no risk of attack to or from the FTP server or the internal virtual machine group.
Advantages of Using Virtual Machine Zones
By capitalizing on virtual machine isolation, correctly configuring virtual switches, and maintaining network separation, you can house all three virtual machine zones on the same ESXi host and be confident that there will be no data or resource breaches.
The company enforces isolation among the virtual machine groups by using multiple internal and external networks and making sure that the virtual switches and physical network adapters for each group are separate from those of other groups.
Because none of the virtual switches straddle virtual machine zones, you succeed in eliminating the risk of packet leakage from one zone to another. A virtual switch, by design, cannot leak packets directly to another virtual switch. The only way for packets to travel from one virtual switch to another is under the following circumstances:
- The virtual switches are connected to the same physical LAN.
- The virtual switches connect to a common virtual machine, which might be used to transmit packets.
Neither of these conditions occur in the sample configuration. If you want to verify that no common virtual switch paths exist, you can check for possible shared points of contact by reviewing the network switch layout in the vSphere Client.
To safeguard the resources of virtual machines, configure a resource reservation and a limit for each virtual machine, which lowers the risk of DoS and DDoS attacks. You can further protect the ESXi host and virtual machines by installing software firewalls at the front and back ends of the DMZ. Finally, ensure that the host is behind a physical firewall, and configure the networked storage resources so that each has its own virtual switch.