You configure vSphere Trust Authority services to attest your ESXi hosts, which then become capable of performing trusted cryptographic operations.
vSphere Trust Authority uses remote attestation for ESXi hosts to prove the authenticity of their booted software. Attestation verifies that the ESXi hosts are running authentic VMware software, or VMware-signed partner software. Attestation relies on measurements that are rooted in a Trusted Platform Module (TPM) 2.0 chip installed in the ESXi host. In vSphere Trust Authority, an ESXi can access encryption keys and perform cryptographic operations only after it has been attested.
vSphere Trust Authority Glossary
vSphere Trust Authority introduces specific terms and definitions that are important to understand.
| Term | Definition |
|---|---|
| VMware vSphere® Trust Authority™ | Specifies a set of services that enables a Trusted Infrastructure. It is responsible for ensuring that ESXi hosts are running trusted software and for releasing encryption keys only to trusted ESXi hosts. |
| vSphere Trust Authority Components | The vSphere Trust Authority components are:
|
| Attestation Service | Attests the state of a remote ESXi host. Uses TPM 2.0 to establish a hardware root of trust, and verifies software measurements against a list of administrator approved ESXi versions. |
| Key Provider Service | Encapsulates one or more key servers and exposes Trusted Key Providers that can be specified when encrypting virtual machines. Currently, key servers are limited to the KMIP protocol. |
| Trusted Infrastructure | A Trusted Infrastructure consists of:
Note: You must use separate
vCenter Server systems for the Trust Authority Cluster and the Trusted Cluster.
|
| Trust Authority Cluster | Consists of a vCenter Server cluster of ESXi hosts that run the vSphere Trust Authority components (the Attestation Service and the Key Provider Service). |
| Trust Authority Host | An ESXi host running vSphere Trust Authority components (the Attestation Service and the Key Provider Service). |
| Trusted Cluster | Consists of a vCenter Server cluster of Trusted ESXi hosts that are remotely attested by the Trust Authority Cluster. Although not strictly required, a configured Key Provider Service greatly increases the value provided by a Trusted Cluster. |
| Trusted Host | An ESXi host whose software has been validated by the Trust Authority Cluster Attestation Service. This host runs workload virtual machines that can be encrypted using Key Providers published by the Trust Authority Cluster Key Provider Service. |
| vSphere Encryption for Virtual Machines | With vSphere Virtual Machine Encryption, you can create encrypted virtual machines and encrypt existing virtual machines. vSphere Virtual Machine Encryption was introduced in vSphere 6.5. See vSphere Encryption Keys and Key Providers for differences in how key providers handle encryption keys. |
| Trusted Key Provider | A Key Provider that encapsulates a single encryption key on a key server. Access to the encryption key requires the Attestation Service to acknowledge that the ESXi software has been verified on the Trusted Host. |
| Standard Key Provider | A Key Provider that gets encryption keys directly from a key server, and distributes keys to the required hosts in a data center. Previously referred to in vSphere as KMS Cluster. |
| Key Server | A KMIP key management server (KMS) that is associated with a Key Provider. |
| Workload vCenter Server | The vCenter Server that manages and is used to configure one or more Trusted Clusters. |
vSphere Trust Authority Basics
With vSphere Trust Authority, you can:
- Provide ESXi hosts with a hardware root of trust and remote attestation capabilities
- Restrict encryption key management by releasing keys only to attested ESXi hosts
- Create a more secure administrative environment for managing trust
- Centralize management of multiple key servers
- Continue to perform cryptographic operations on virtual machines but with an enhanced level of encryption key management
In vSphere 6.5 and 6.7, virtual machine encryption depends on vCenter Server to obtain encryption keys from a key server and push them to ESXi hosts as needed. vCenter Server authenticates with the key server by using client and server certificates, which are stored in VMware Endpoint Certificate Store (VECS). Encryption keys that are sent from the key server pass through vCenter Server memory to the required ESXi hosts (with data encryption provided by TLS over the wire). In addition, vSphere depends on privilege checks in vCenter Server to validate user permissions and enforce key server access restrictions. Although this architecture is secure, it does not address the potential for a compromised vCenter Server, a rogue vCenter Server administrator, or a management or configuration error that might result in leaked or stolen secrets.
In vSphere 7.0 and later, vSphere Trust Authority addresses these problems. You can create a trusted computing base, which consists of a secure, manageable set of ESXi hosts. vSphere Trust Authority implements a remote attestation service for the ESXi hosts you want to trust. Furthermore, vSphere Trust Authority improves upon TPM 2.0 attestation support (added to vSphere beginning in the 6.7 release), to implement access restrictions on encryption keys and so better protect virtual machine workload secrets. In addition, vSphere Trust Authority allows only authorized Trust Authority administrators to configure vSphere Trust Authority services, and configure Trust Authority hosts. The Trust Authority administrator can be the same user as the vSphere administrator user, or a separate user.
In the end, vSphere Trust Authority enables you to run your workloads in a more safe and secure environment by:
- Detecting tampering
- Disallowing unauthorized changes
- Preventing malware and modifications
- Limiting sensitive workloads to run only on a verified, safe hardware and software stack
vSphere Trust Authority Architecture
The following figure shows a simplified view of the vSphere Trust Authority architecture.
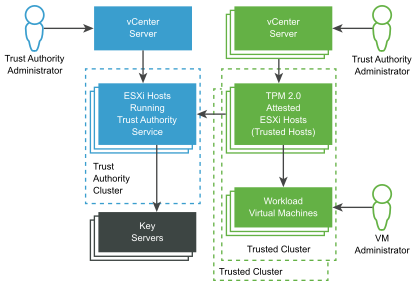
In this figure:
- vCenter Server systems
Separate vCenter Server systems manage the Trust Authority Cluster and Trusted Clusters.
- Trust Authority Cluster
Consists of the ESXi hosts that run the vSphere Trust Authority components.
- Key Servers
Store encryption keys that are used by the Key Provider Service when encryption operations are performed. The key servers are external to vSphere Trust Authority.
- Trusted Clusters
Consist of the ESXi Trusted Hosts, which have been remotely attested with a TPM, and that run encrypted workloads.
- Trust Authority Administrator
Administrator who is a member of the vCenter Server TrustedAdmins group, and configures the Trusted Infrastructure.
vSphere Trust Authority enables flexibility in how you designate Trust Authority administrators. The Trust Authority administrators in the figure can be separate users. It is also possible for the Trust Authority administrators to be the same user, using credentials that are linked across the vCenter Server systems. In this case, it is the same user and the same TrustedAdmins group.
- VM Administrator
Administrator who has been granted privileges to manage the encrypted workload virtual machines on the Trusted Hosts.