If you are using the embedded Harbor registry with your Supervisor, you can migrate the images from the embedded registry to the Harbor registry that you have installed as a Supervisor Service.
Prerequisites
- Verify that Contour and Harbor Supervisor Services are installed on the Supervisor.
- Verify that the DNS that you use with your Supervisor includes and entry of the Harbor FQDN that is mapped to the Envoy service ingress IP.
- Verify that trust is established between the Supervisor and Harbor. If images are being referenced by TKG clusters that run on Supervisors different than the one where Harbor runs, verify that there is trust between these TKG clusters and the Harbor.
Procedure
- Login to the Supervisor as a vCenter Single-Sign-On user.
- Setup network access egress to the Harbor Supervisor Service.
- Create a network policy CRD named allow-all-egress-harbor-supervisor-service on the service namespace of Harbor, which can be named svc-harbor-domain-c9 for example.
apiVersion: networking.k8s.io/v1 kind: NetworkPolicy metadata: name: allow-all-egress-harbor-supervisor-service namespace: svc-harbor-domain-c9 spec: podSelector: matchLabels: app: harbor egress: - {}
- Create a network policy CRD named allow-all-egress-harbor-supervisor-service on the service namespace of Harbor, which can be named svc-harbor-domain-c9 for example.
- Access the secrets of the embedded registry so that you can later add the registry as a replication endpoint to Harbor.
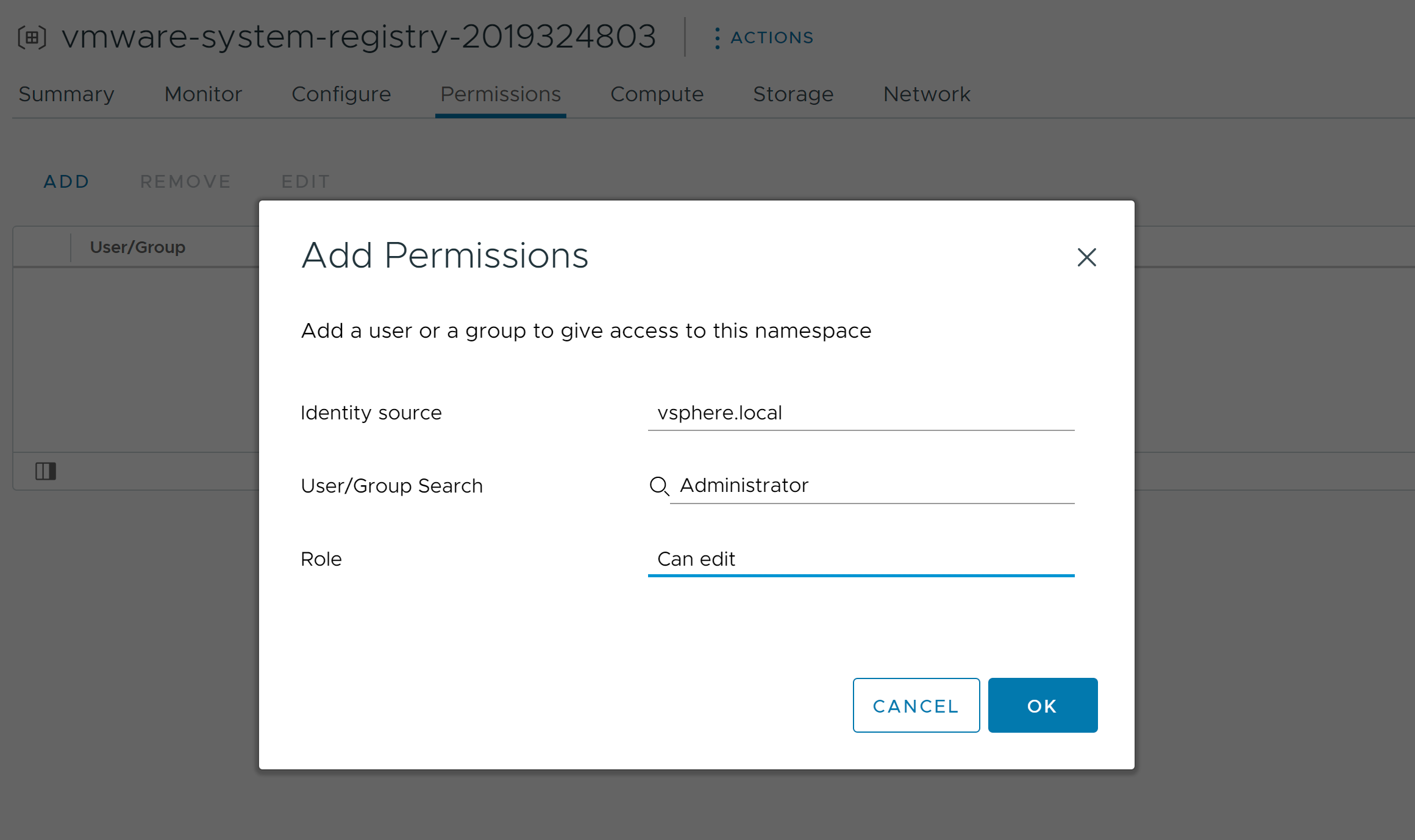
- Grant edit permissions to your administrative vCenter Single Sign-On user on the embedded registry namespace, which could be named for example vmware-system-registry-437393318.
- Access the secrets from the embedded registry namespace.
# kubectl get secrets -n vmware-system-registry-437393318 harbor-437393318-controller-registry -o yaml apiVersion: v1 data: harborAdminPassword: UDNSak4wQk5VbFlrY1VZeVprUmpKQT09 harborAdminUsername: WVdSdGFXND0= harborPostgresPassword: TlRoS1ZHeEFLa1lrVkdjaGN6aGtXZz09 kind: Secret ...
- Decode the user name and the password.
# echo 'WVdSdGFXND0=' | base64 -d | base64 -d admin # echo 'UDNSak4wQk5VbFlrY1VZeVprUmpKQT09' | base64 -d | base64 -d ?tc7@MRV$qF2fDc$
- Grant edit permissions to your administrative vCenter Single Sign-On user on the embedded registry namespace, which could be named for example vmware-system-registry-437393318.
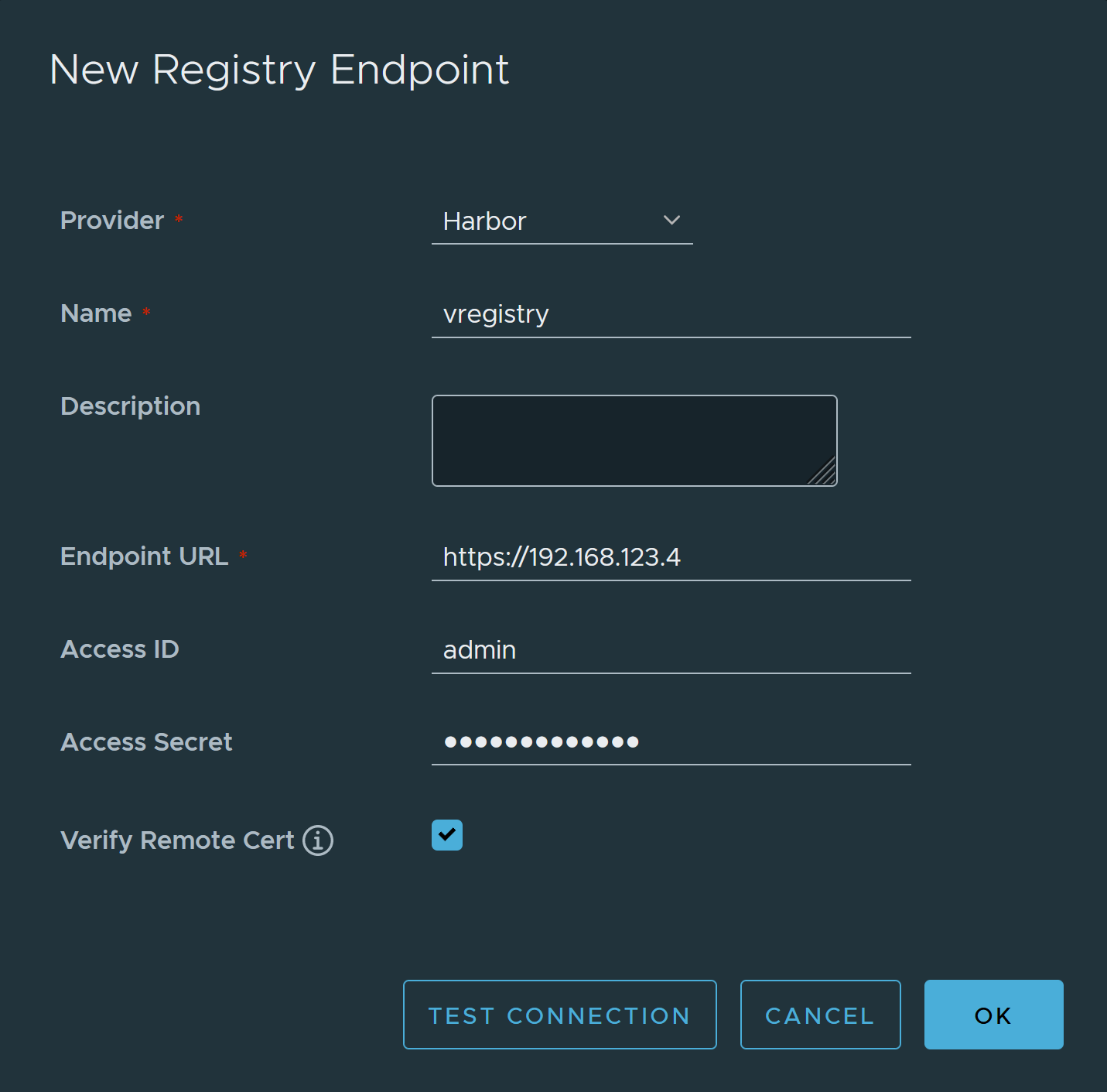
- Add a replication endpoint and replication rule for the embedded registry to the Harbor Supervisor Service.
- Login as root to the UI of the Harbor Supervisor Service.
- Click Registries and click New Endpoint.
- Select Replications tab and click New Replication Rule.
Fill in the following settings, by leaving the rest with default values:
- Name - Provide a name for the rule.
- Replication mode - Select Pull-based.
- Source registry - Select the registry endpoint that you have added.
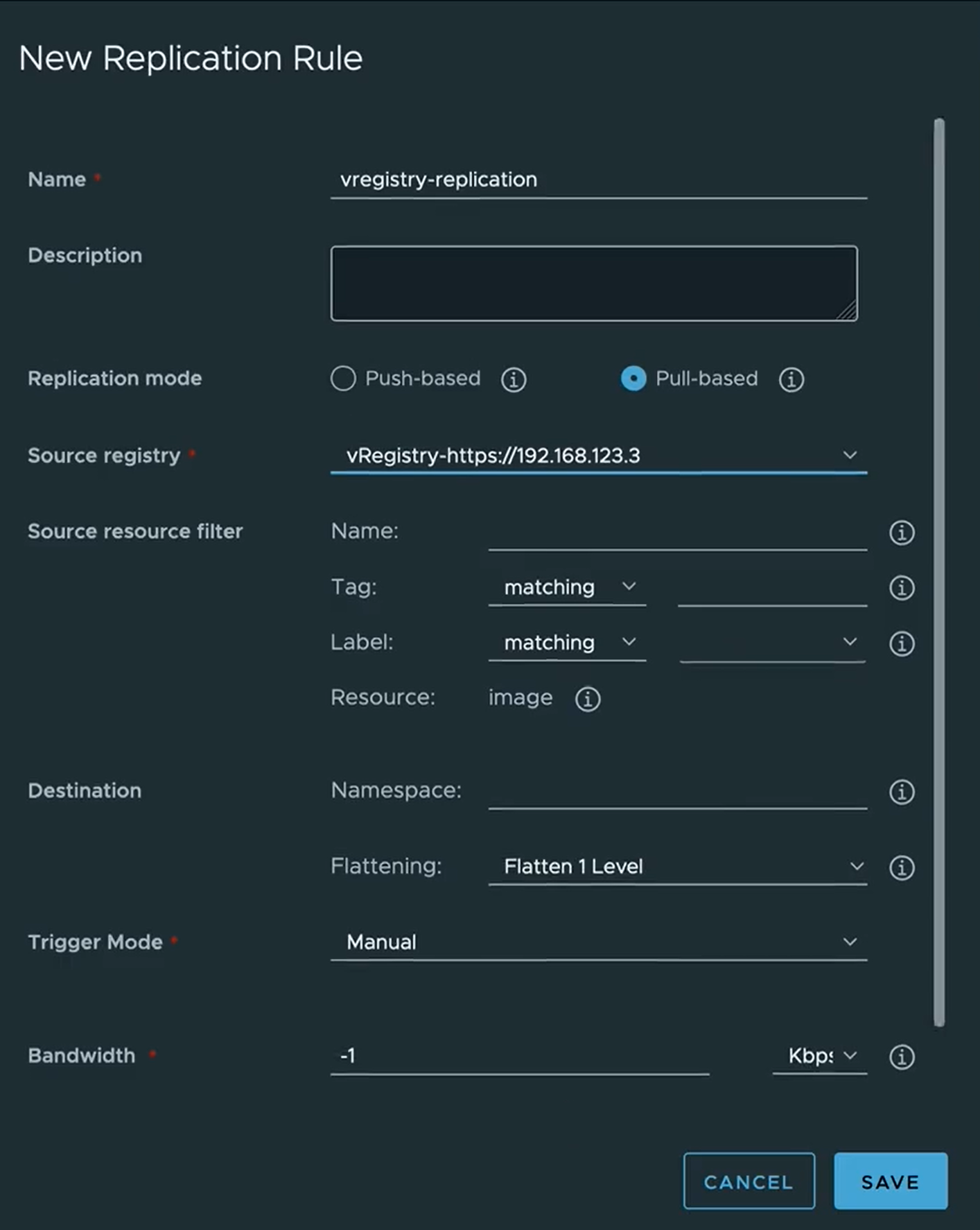
- Click Save.
- Select the newly-created replication rule and click Replicate.