This topic tells you how to set up PingFederate as your identity provider by configuring SAML integration in both Single Sign‑On for VMware Tanzu Application Service and PingFederate.
Overview
To set up PingFederate as your identity provider through SAML integration:
- Set up SAML in Single Sign‑On
- Configure the Connection
- Configure Browser SSO
- Configure Assertion Creation
- Configure Protocol Settings
- Configure Credentials
Set up SAML in Single Sign‑On
To set up SAML in Single Sign‑On, follow the steps in Configure SAML Settings.
Configure the Connection
To configure the connection:
-
Sign in as a PingFederate admin.
-
Navigate to your identity provider configurations by clicking on the IDP Configuration tab.
-
Under SP Connections, click Create New

-
Select the Browser SSO Profiles connection template on the Connection Type tab and click Next.
-
Select Browser SSO on the Connection Options tab and click Next.
-
Select File as the method for importing metadata and click Choose file to choose the SSO metadata on the Import Metadata tab. Click Next.

-
Review the information about the Metadata Summary tab and click Next.
-
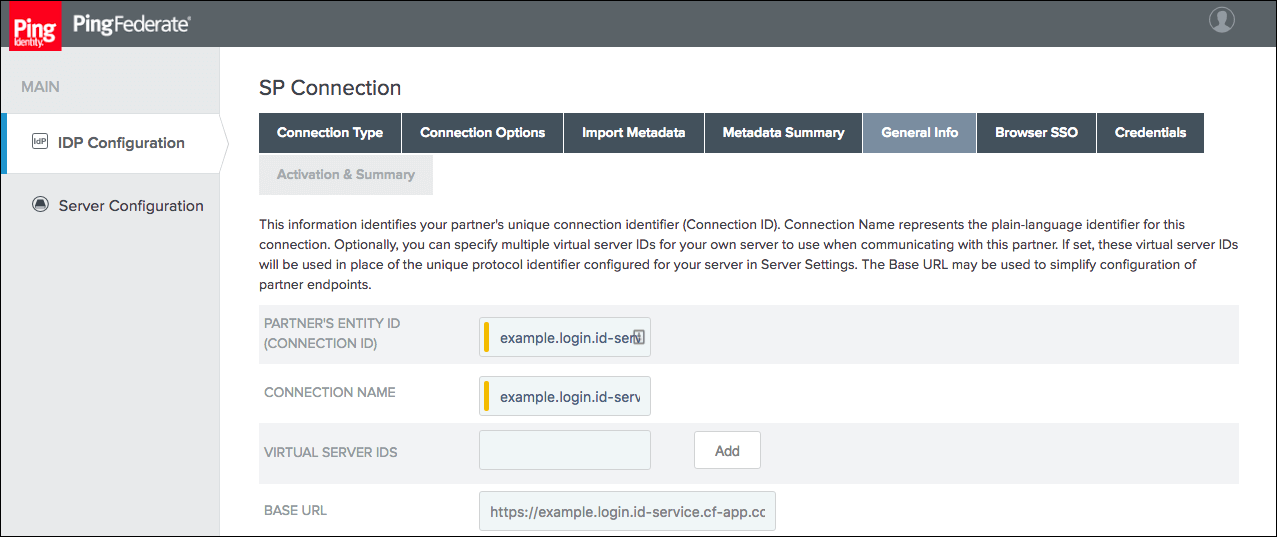
Ensure that the Partner’s Entity ID, Connection Name, and Base URL fields pre-populate based on the metadata. Click Next.
Configure Browser SSO
To configure browser SSO:
-
Click Configure Browser SSO on the Browser SSO tab.
-
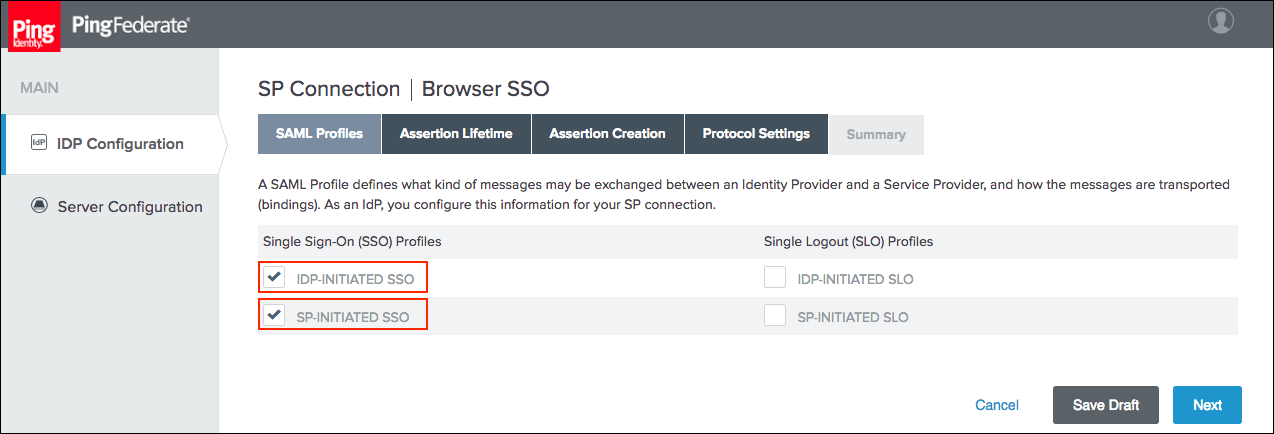
Select the IdP-Initiated SSO and SP-Initiated SSO options on the SAML Profiles tab and click Next.
-
Enter your desired assertion validity time from on the Assertion Lifetime tab and click Next.
-
(Optional) Select IdP-Initiated SLO and SP-Initiated SLO options if you want to enforce Single Logout.
Configure Assertion Creation
To configure assertion creation:
-
Click Configure Assertion Creation on the Assertion Creation tab.
-
Choose the Standard option on the Identity Mapping tab and click Next.
-
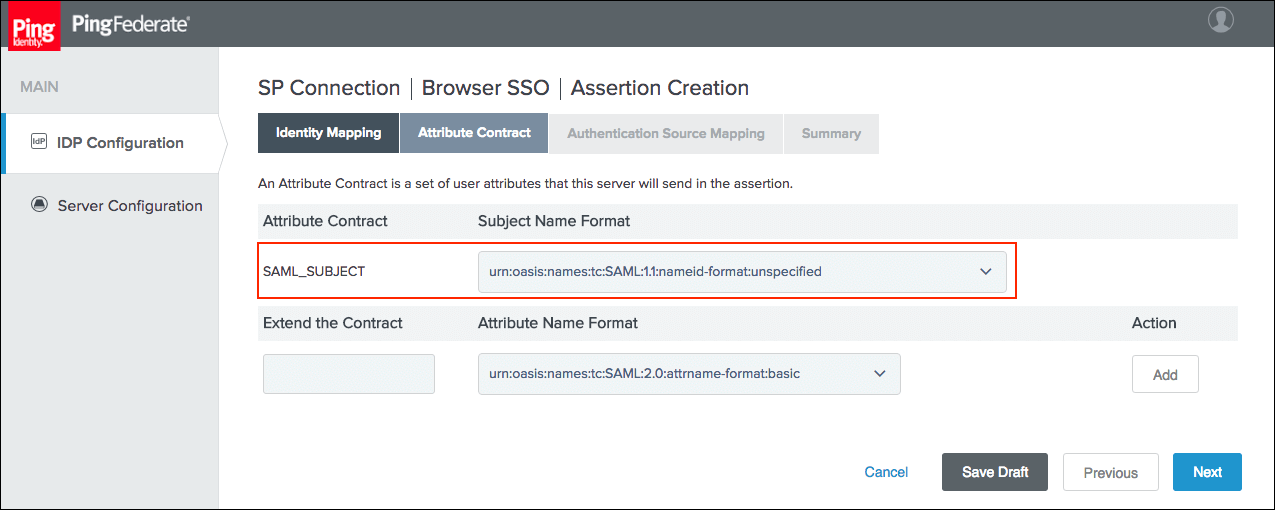
Select a Subject Name Format for the SAML_SUBJECT on the Attribute Contract tab and click Next.
-
Click Map New Adapter Instance on the Authentication Source Mapping tab.
-
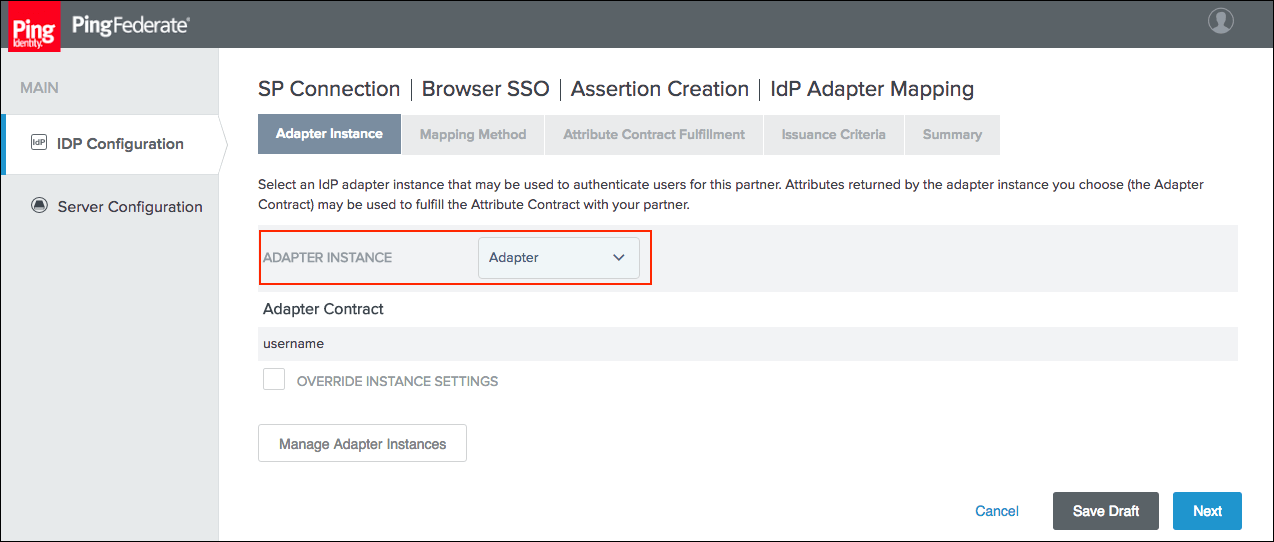
Select an Adapter Instance and click Next. The adapter must include the user’s email address.
-
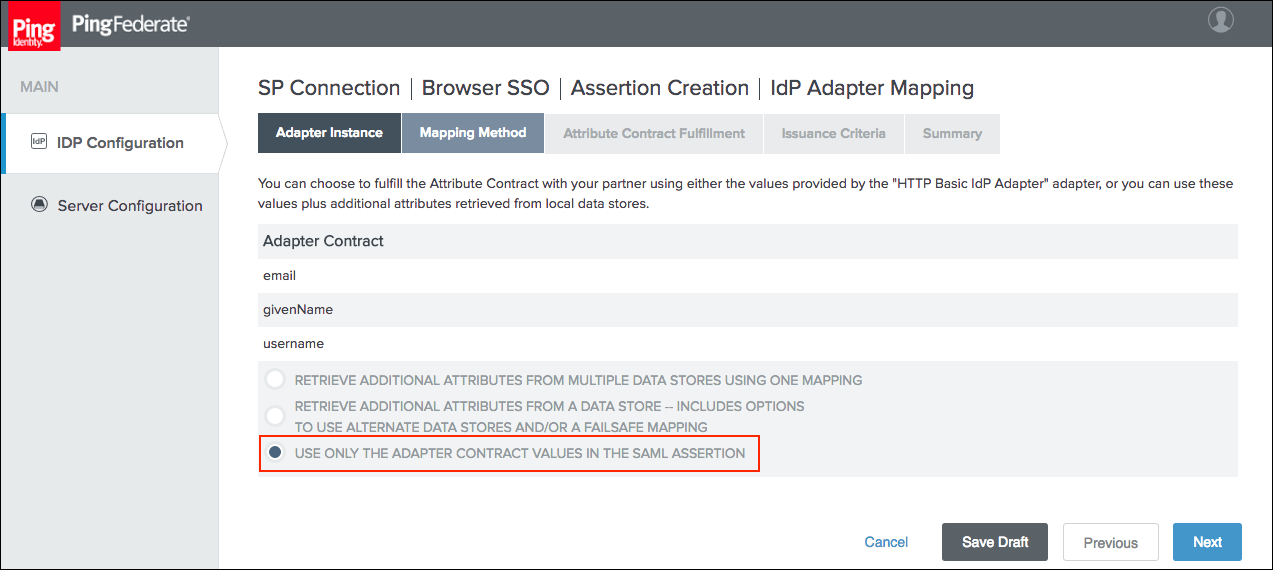
Select the Use only the adapter contract values in the SAML assertion option on the Mapping Method tab and click Next.
-
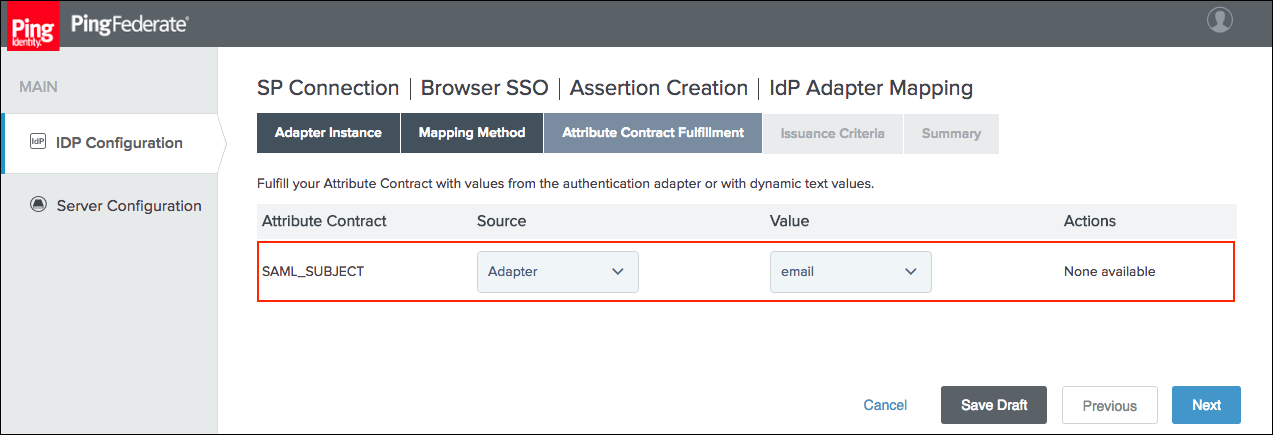
Select your adapter instance as the Source and the email as the Value on the Attribute Contract Fulfillment tab and click Next.
-
(Optional) Select any authorization conditions you want on the Issuance Criteria tab and then click Next.
-
Click Done on the Summary tab.
-
Click Next on the Authentication Source Mapping tab.
-
Click Done on the Summary tab.
-
Click Next on the Assertion Creation tab.
Configure Protocol Settings
To configure protocol settings:
-
Click Configure Protocol Settings on the Protocol Settings tab.
-
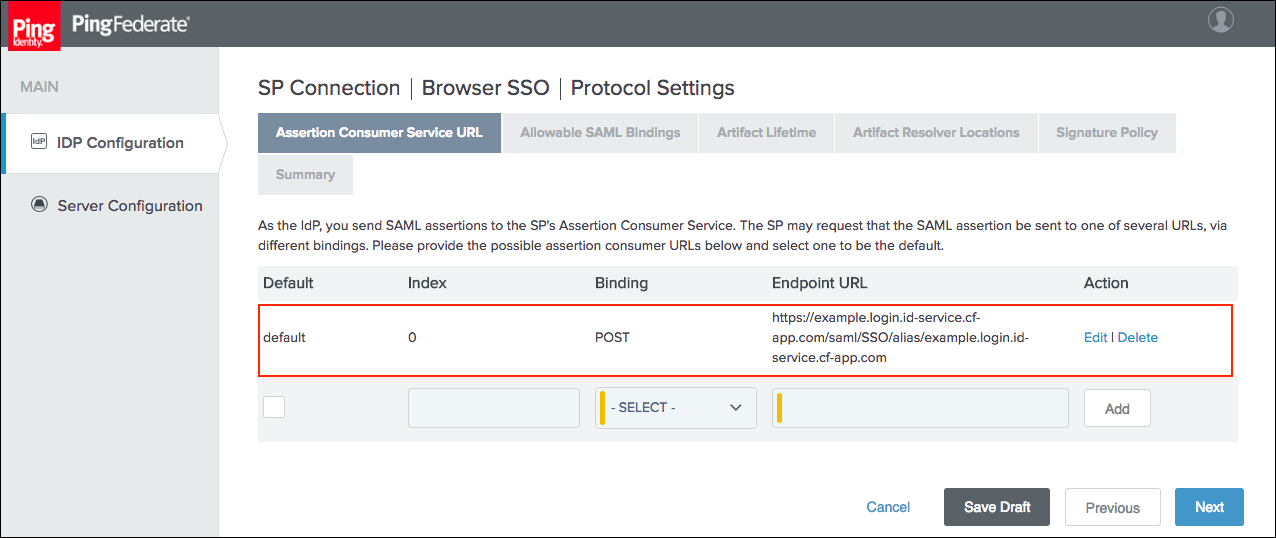
Select POST for Binding and specify the single sign-on endpoint URL in the Endpoint URL field on the Assertion Consumer Service URL tab. Click Next
-
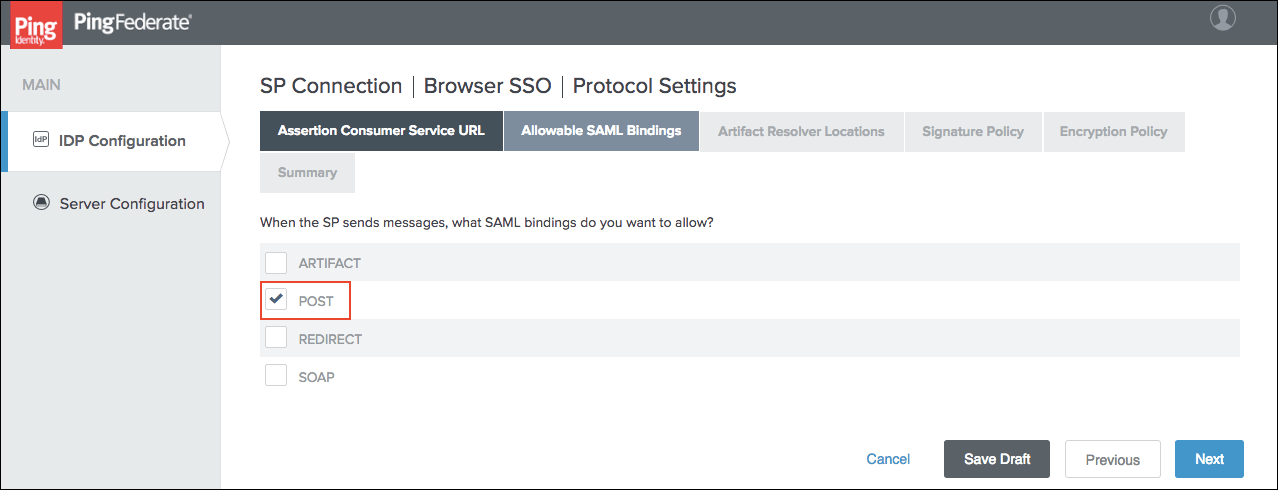
Select POST on the Allowable SAML Bindings tab and click Next.
-
Select your desired signature policies for assertions on the Signature Policy tab and click Next.
-
Select your desired encryption policy for assertions on the Encryption Policy tab and click Next.
-
Click Done on the Protocol Settings Summary tab.
-
Click Done on the Browser SSO Summary tab.
Configure Credentials
To configure credentials:
-
Click Configure Credentials on the Credentials tab.
-
Select the Signing Certificate to use with the Single Sign‑On for VMware Tanzu Application Service service and select Include the certificate in the signature
element . Click Next.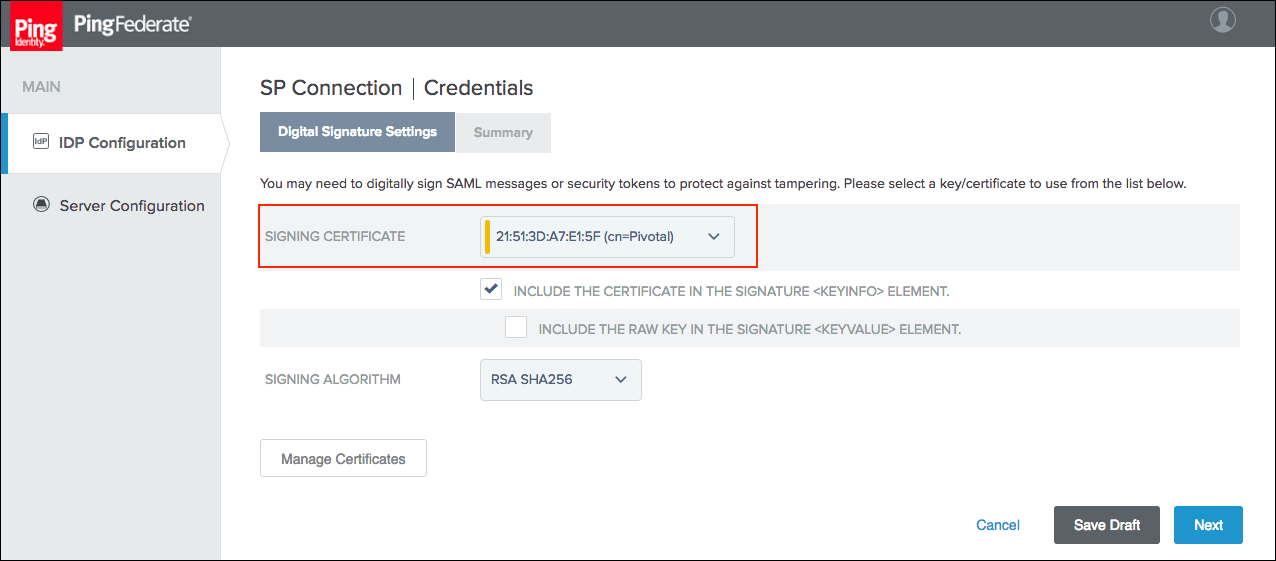
-
Click Done on the Summary tab.
-
Click Next on the Credentials tab.
-
Select Active for the Connection Status on the Activation & Summary tab and click Save.
-
Click Manage All under SP Connections.
-
Click Export Metadata for the desired service provider connection.
-
Choose a Signing Certificate on the Metadata Signing tab and click Next.
-
Click Export on the Export & Summary tab and click Done.