This topic tells you how a Space Developer defines resources required by an app bound to a Single Sign‑On for VMware Tanzu Application Service service instance and how an administrator grants resource permissions.
In this topic, resources are the API endpoints that users and apps need to retrieve information from a resource server. After an administrator creates resources, they assign the resources to users and apps. Users can then grant apps access to the resources, for example to query API endpoints on their behalf.
Because developers know what endpoints exist for their apps, they are responsible for creating resources.
Create or Edit Resources
If an app requires access to specific resources such as API endpoints, permissions for those resources must be either bootstrapped from the app manifest or defined by the Space Developer in the SSO Developer Dashboard.
To bootstrap resources from the manifest, follow the instructions in the Single Sign‑On Sample Applications repository.
To create resources in the SSO Developer Dashboard, do the following:
-
Log in to Apps Manager as a Space Developer.
-
Select the space where your service instance is located.
-
Under Services, click Manage next to your Single Sign‑On service instance to launch the SSO Developer Dashboard.
 View a larger version of this image.
View a larger version of this image. -
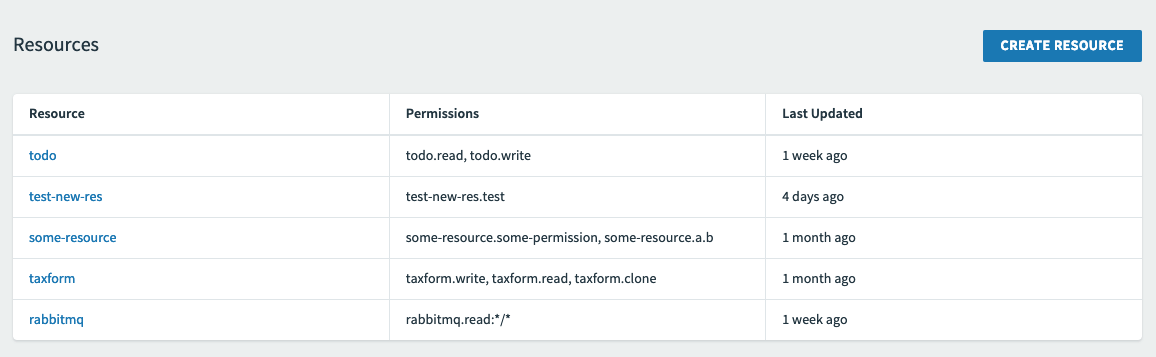
Click the Resources tab.
-
Click Create Resource.
-
Enter a Resource Name.
-
Create Permissions that the OAuth client for your app needs to access from the resource server.
-
Enter one or more attributes or actions for each permission.
-
Enter a Description for each permission.
-
-
Click Create Resource.
- An administrator can map existing groups to the created resource. For more information, see Create or Edit Resource Permissions Mapping.
Space Developers create resources within a space. Space Developers only see the resources created in the spaces they have access to and can only assign those to the apps in those spaces.
Delete Resources
-
Log in to Apps Manager as a Space Developer.
-
Click the Manage link under the Single Sign‑On service instance to launch the SSO Developer Dashboard.
 View a larger version of this image.
View a larger version of this image. -
Click the Resources tab.
-
Click the resource to delete.
-
Click Delete Resource at the bottom of the page.
-
On the popup, click Delete Resource to delete the resource.
Deleting a resource removes it from the permission mappings and from the app. You must reconfigure the updated permissions in both areas.
About Space Protection for Resources
OAuth 2.0 provides the concept of a scope in order to limit the amount of access that is granted to an access token. A scope is the intersection of a user’s groups and a client’s scopes.
For a user to gain access to a resource, they must meet the following conditions, which can only be set up by plan administrators:
- The user must be assigned the resource as a group. For information on how to do this, see Manage Users.
- The user must access an app that has the resource assigned as a scope.
App developers can assign scopes to any app that is not a service-to-service app. But, only plan administrators can assign scopes to users.
When assigning a resource as a scope for a service-to-service app, app developers can only assign resources they have created within their own space. Only a plan administrator can assign a scope from another space to a service-to-service app.