Deploying VMware Tunnel using the Unified Access Gateway appliance provides a secure and effective method for individual applications to access corporate resources. Unified Access Gateway supports deployment on either ESXi or Microsoft Hyper-V environments.
VMware Tunnel is composed of two independent components: Tunnel Proxy and Per-App Tunnel. You deploy VMware Tunnel using either single or multi-tier network architecture models.
Both Tunnel Proxy and Per-App Tunnel deployment models can be used for a multi-tier network on the Unified Access Gateway appliance. The deployment consists of a front-end Unified Access Gateway server deployed in the DMZ and a back-end server deployed in the internal network.
The Tunnel Proxy component secures the network traffic between an end user device and a website through the Workspace ONE Web or any Workspace ONE SDK enabled application deployed from Workspace ONE UEM. The mobile application creates a secure HTTPS connection with the Tunnel Proxy server and protects the sensitive data. Devices are authenticated to the Tunnel Proxy with a certificate issued via the SDK as configured in the Workspace ONE UEM console. Typically, this component should be used when there are unmanaged devices that need secured access to internal resources.
For fully enrolled devices, the Per-App Tunnel component enables devices to connect to internal resources without needing the Workspace ONE SDK. This component uses the native Per-App VPN capabilities of the iOS, Android, Windows 10, and macOS operating systems.
For more information on these platforms and VMware Tunnel component capabilities, refer to the latest Tunnel documentation from the Workspace ONE UEM documentation page.
- Configure the VMware Tunnel hostname and port information in the Workspace ONE UEM console. See Firewall Rules for DMZ-Based Unified Access Gateway Appliances.
- Download and deploy the Unified Access Gateway OVF template.
- Manually configure the VMware Tunnel.
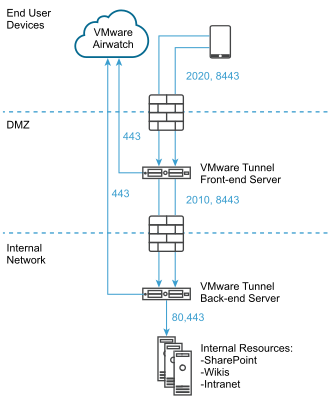
AirWatch v9.1 and above supports Cascade Mode as the Multi-Tier deployment model for VMware Tunnel. Cascade Mode requires a dedicated inbound port for each Tunnel component from the internet to the front-end Tunnel server. Both the front-end and back-end servers must be able to communicate with the Workspace ONE UEM API and AWCM servers. VMware Tunnel Cascade mode supports the multi-tier architecture for the Per-App Tunnel component.
For load balancing considerations for Content Gateway and Tunnel Proxy, see Unified Access Gateway Load Balancing Topologies.
Go to the VMware Workspace ONE UEM documentation page for a complete list of Workspace ONE UEM guides and release notes.