Use VMware Aria Automation for Secure Clouds Cloud Entitlements to manage principal access in the cloud
BETA FEATURE: This feature is currently in public beta for AWS cloud accounts. Reach out to your support team if you have any questions about the process as written.
Most identities in the cloud do not use the majority of cloud entitlements they are granted. This is due to the complexity and high number of identities, roles, resources, policies, and permissions in the cloud environment, which is challenging to administrate. Cloud Infrastructure Entitlement Management (CIEM) is a concept that underpins a variety of tools designed to help improve your control and understanding over the various permissions assigned to users, identities, and roles in your cloud environment. VMware Aria Automation for Secure Clouds provides CIEM with the cloud entitlements feature, which you can access through the Explore menu on the browser client UI.
No additional configuration or credentials are required to view your cloud entitlements. VMware Aria Automation for Secure Clouds begins detecting and populating the IAM entities on your cloud accounts when they're added to your organization. As cloud entitlements are not updated in real-time, it may take several hours for results to reflect when a cloud account is updated or deleted based on your last inventory scan.
Understanding cloud entitlements
Cloud entitlements are organized under principals scanned from a cloud account, the services they can access, followed by resource types under those services. A principal is any IAM entity that can interact with resources, which includes users, groups, and roles.
The following presents an example of these concepts.
| User | Service | Resource type |
|---|---|---|
| jsmith | AWS.EC2 | AWS.EC2.Instance |
Cloud entitlements, the policies that grant a principal access to resources, can be viewed and investigated per resource type. This is demonstrated in the services through an access path:
jsmith -----> admin-group -----> aws/AdministratorAccess -----> AWS.EC2.Instance
Here, the user jsmith belongs to the user group admin-group, which is granted permissions by the aws/AdministratorAccess policy for the AWS.EC2.Instance resource type. The cloud entitlements page visualizes this relationship and enumerates specific actions granted by a policy. The following sections explain how to review and investigate this data.
How to use cloud entitlements
Most users find themselves needing to learn more about their IAM principal access privileges in two scenarios: investigating an incident and performing a security review. Cloud entitlements makes it possible to gather this information quicker and more efficiently than using the tools available in most cloud providers, which are often more complex and less visible. Review each scenario for a simple example of how to approach cloud entitlements.
Scenario one - Security audit
Imagine you're part of a development team that is getting ready to launch an app and are performing a security audit as part of the secure software development lifecycle. While developing the app the team has added many roles and permissions that may not conform to best practices for production. You can use the cloud entitlements page to understand and investigate the full breadth of your app's access footprint in the cloud and scope it to comply with your company's security standards before launch.
Start out by going to the cloud entitlements page (Explore > Entitlements from the browser client) and locating the app in the Users tab.
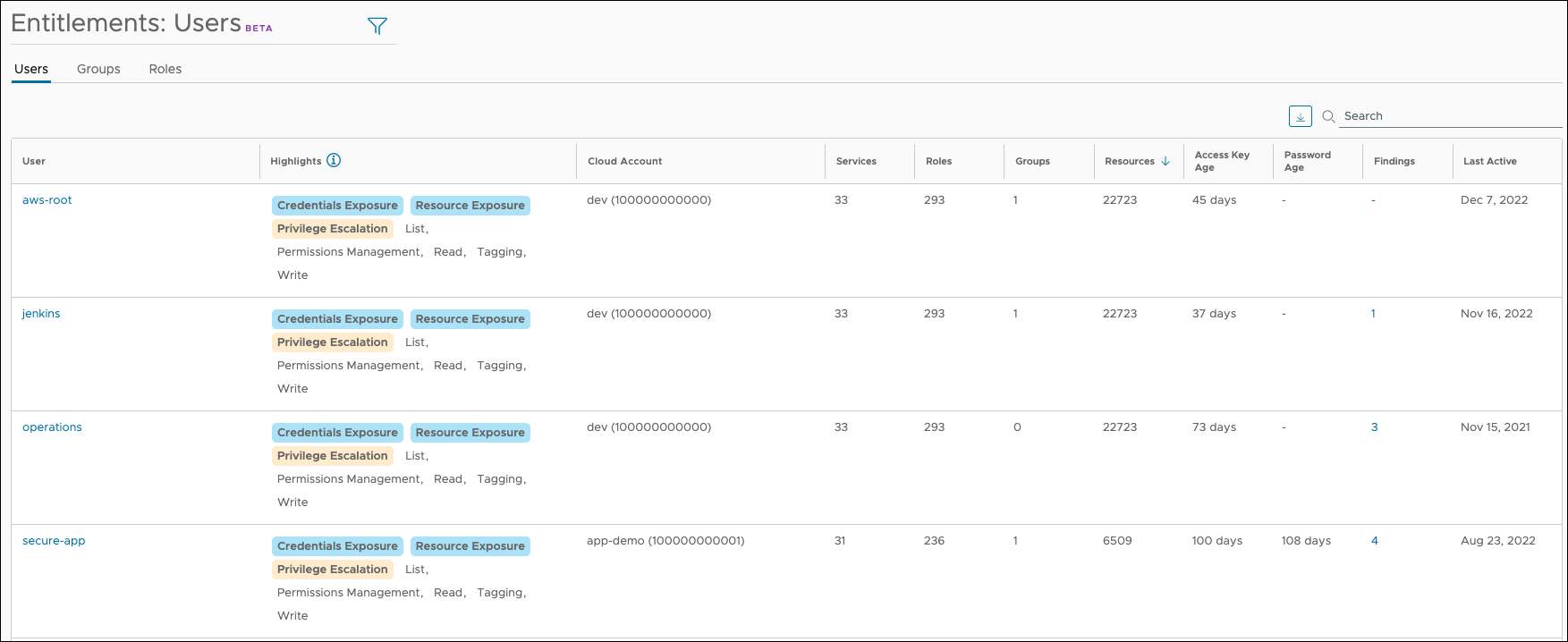
The information in the columns can be understood as follows:
- Highlights - A summary of action permissions and warnings the user has on one or more services. Warnings are designed to provide awareness and visibility on users that may have excessive permissions, and have three categories:
- Credentials Exposure - The user can control credentials for one or more services or principals.
- Resource Exposure - The user can set resource policies for one or more services, up to and including exposure outside the cloud account.
- Privilege Escalation - The user can gain access to broader permissions than the currently have, possibly through IAM misconfiguration.
- Cloud Account - The cloud account associated with the user.
- Services - The number of services for which the user has access.
- Roles - The number of roles assigned to the user.
- Groups - The number of groups to which the user belongs.
- Resources - The number of resources the user can access.
- Access key age - The age (in days) of the user's access key. Access keys that aren't periodically rotated usually trigger findings.
- Password age - The age (in days) of the user's password. Passwords that aren't periodically rotated usually trigger findings.
- Findings - The number of findings associated with the user, such as inactivity or credentials older than 90 days.
- Last Active - The date the user last accessed the associated cloud account.
The secure-app user hasn't had its access key or password rotated recently, which has likely generated a finding. While this is useful information, the highlighted warnings are of concern as well. Select the secure-app user to get a more detailed list of services your app can access.
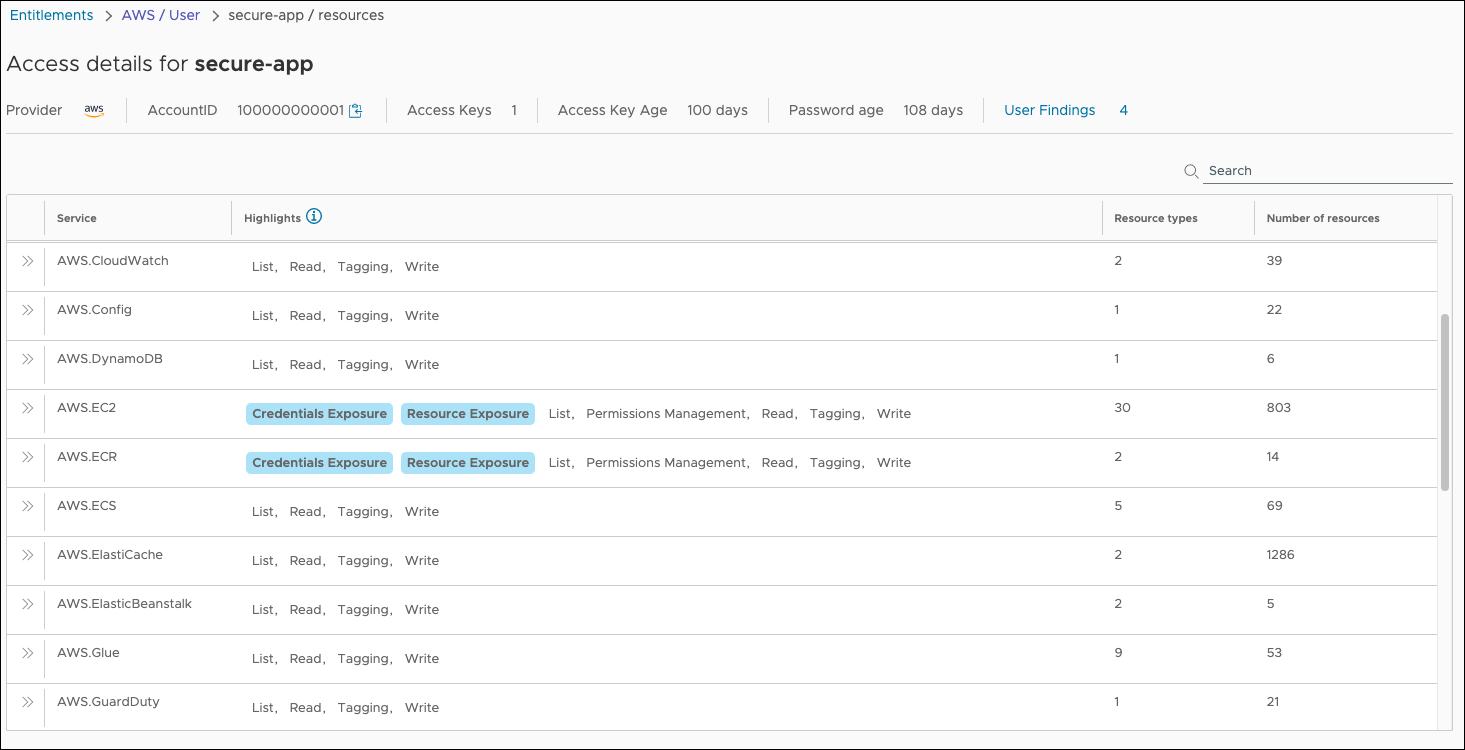
Here you can see that at least two services, AWS.EC2 and AWS.ECR, are at risk for a resource or credential exposure due to their permissions. Select the double arrow icon next to the AWS.EC2 service to see a list of resource types your app can access.
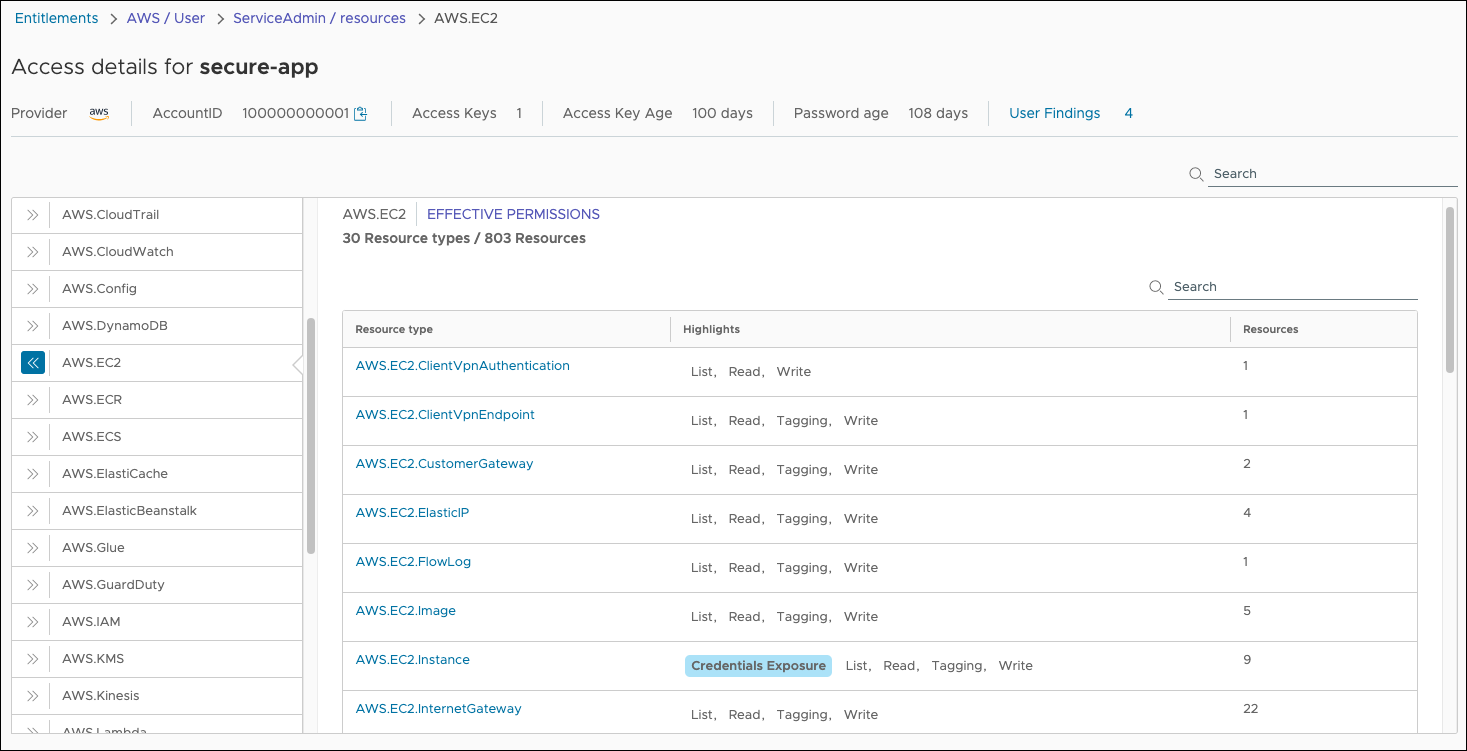
The cloud entitlements page now displays of a summary list of resource types for the AWS.EC2 and an aggregate count of resources for each type. There is a credential exposure highlight on the AWS.EC2.Instance resource type that extends to nine instance resources. Select the resource type link to get a comprehensive look at how your app gets access to the AWS.EC2.Instance service.
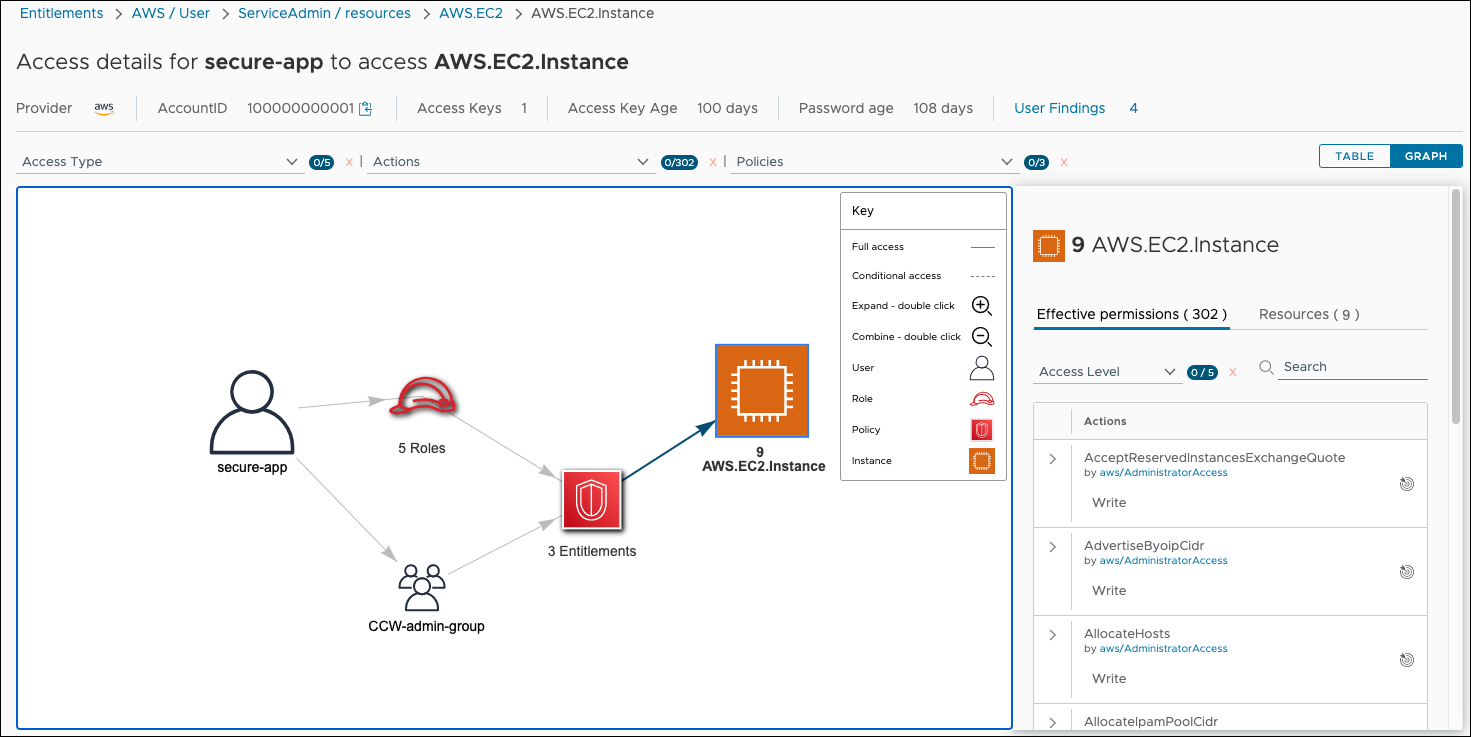
The secure-app user has three cloud entitlements that grant it 302 effective permissions to 9 AWS.EC2.Instance resources. The cloud entitlements are provided by a combination of roles the app is assigned and the CCW-admin-group it belongs to. You can review individual permissions and resources in the panel on the right, and double-click the roles and cloud entitlements icons in the graph to expand them (another double-click combines them back into a single icon).
NoteThe solid arrows connecting elements of the graph indicates full access between one element and another. A dotted arrow line indicates conditional access.
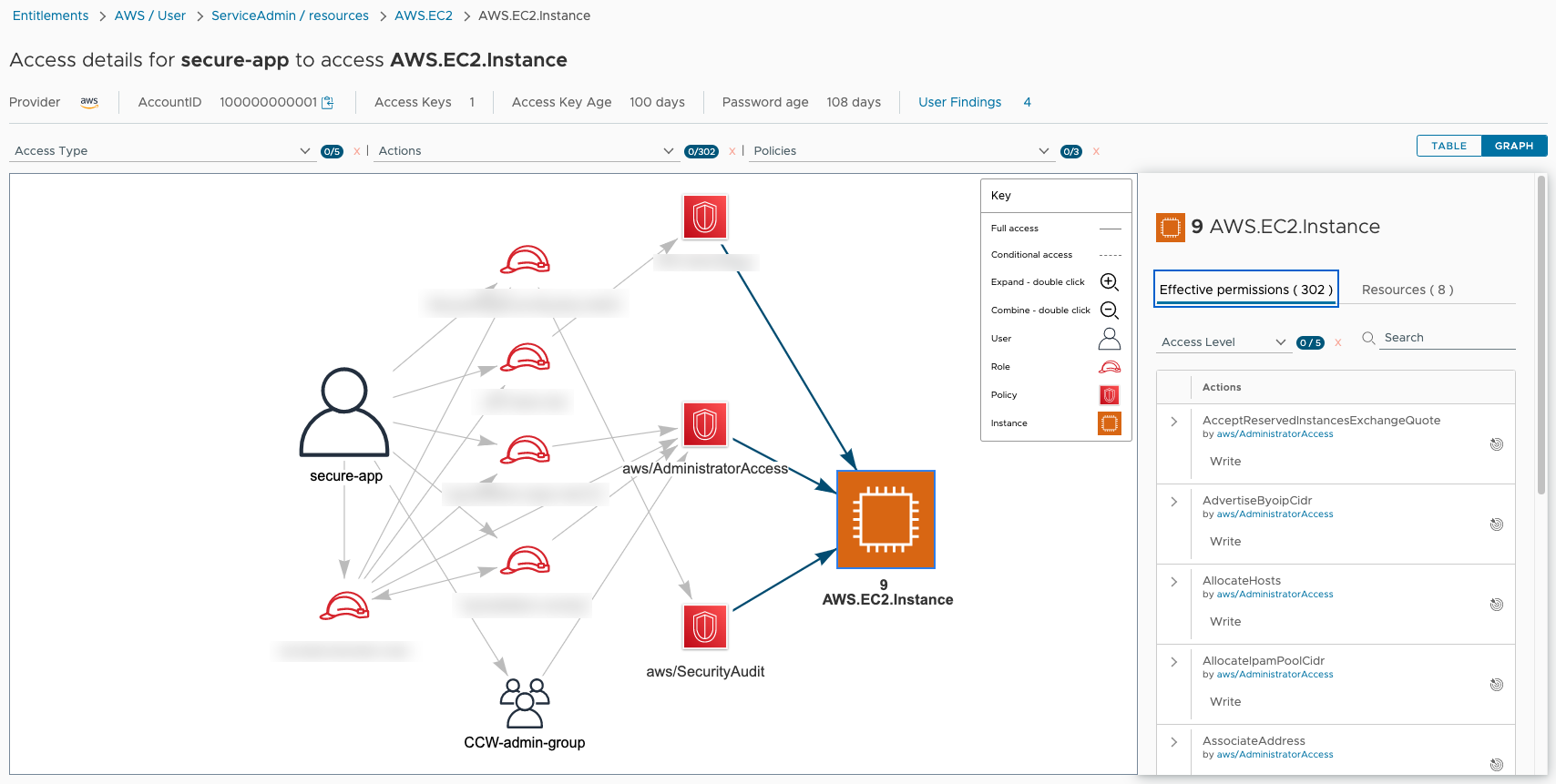
Searching through the permissions panel shows that the GetPasswordData permission is the source of a credential exposure risk on AWS.EC2.Instance. You can click the target icon (highlighted in blue) to isolate the access paths for this permission on the graph.
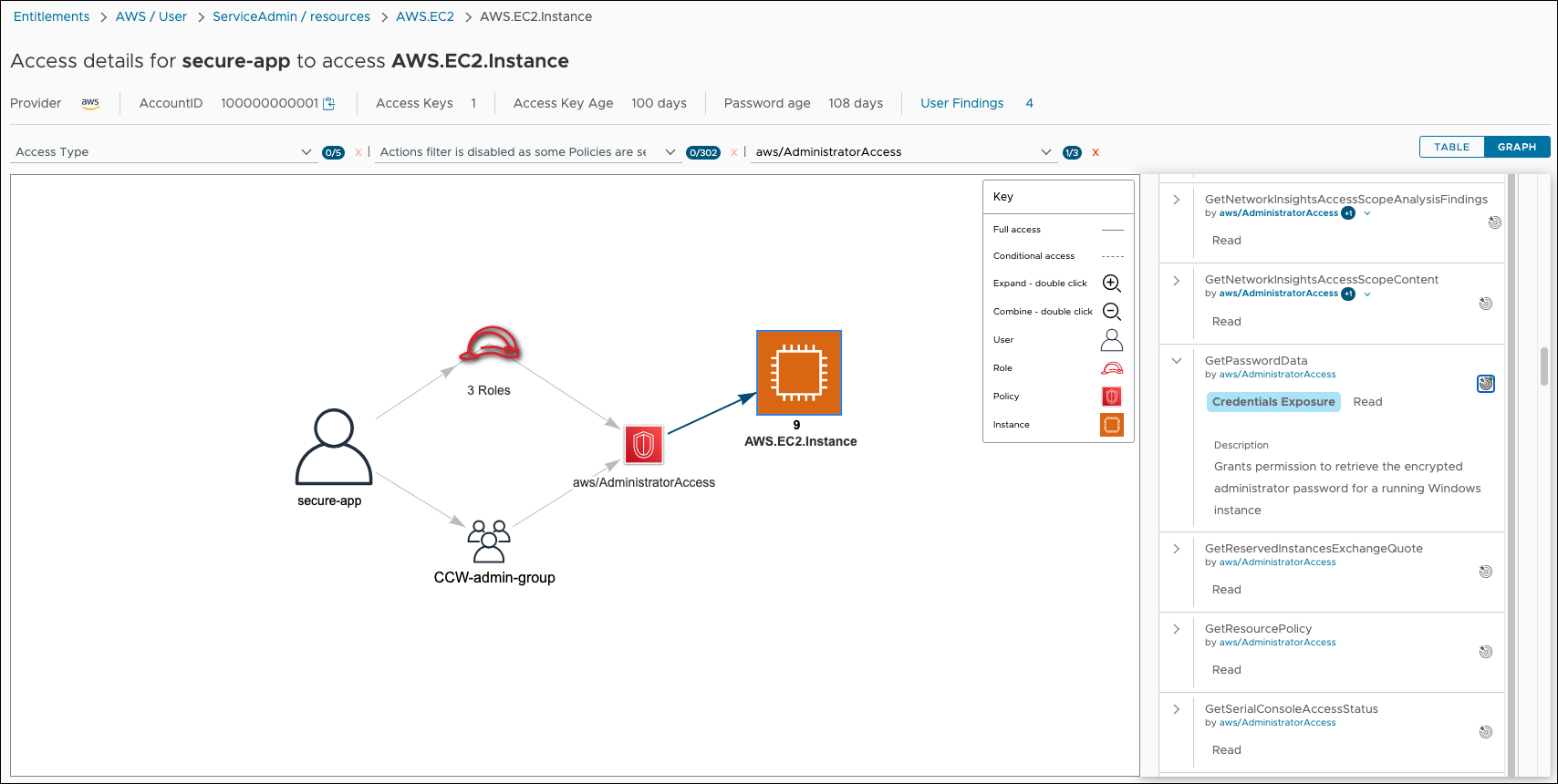
You can use this same process to investigate cloud entitlements for other services and determine how the permissions for your app should be structured before release.
Scenario two - Incident investigation
Consider another situation where you're part of a central security team that receives a finding for suspicious activity on one of your organization's resources. You can use VMware Aria Automation for Secure Clouds to identify the principles that are involved and understand any cloud entitlements contributing to vulnerability.
Start the investigation by locating the resource in Explore Search and reviewing the Entitlement Details in the left panel. Alternatively, go to the details page of the related finding and select the Entitlements tab.
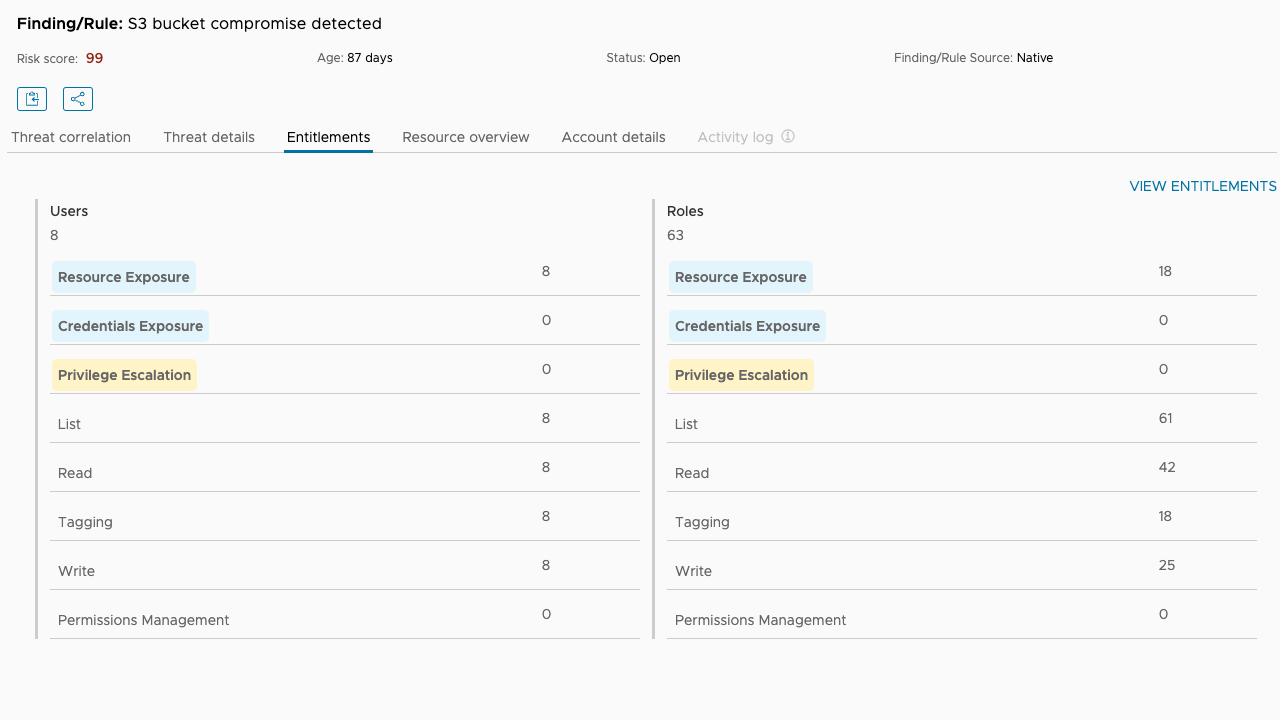
All 8 users and 18 of the roles with access to the S3 buckets are at risk of resource exposure and could be the source of a leak. Select the View Entitlements link to get a filtered list of users and roles for the S3 bucket, then select a principal from the list to see a breakdown of their cloud entitlements over the compromised resource.
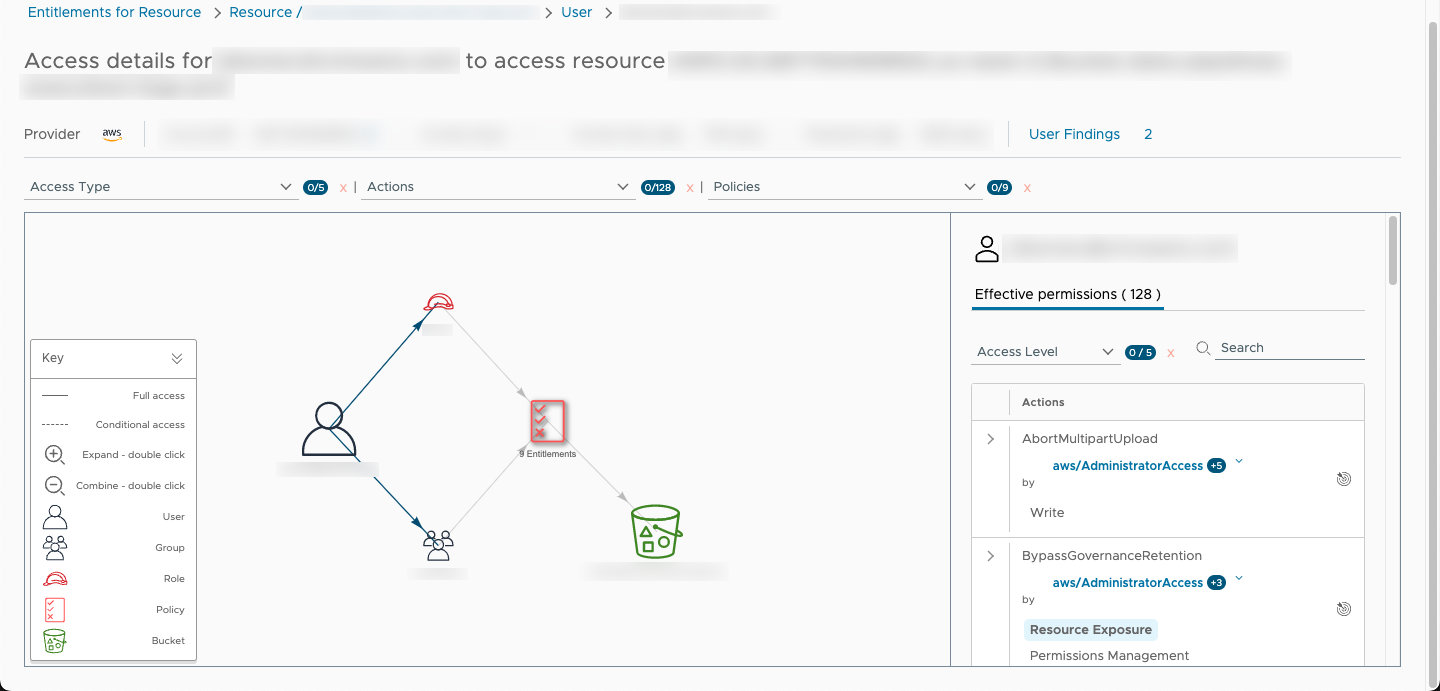
The access details page shows all access paths for the effective permissions set on a resource. In this example, the principal is a user with with 9 cloud entitlements to the compromised resource (an S3 bucket) granted by different groups and roles. On the right panel you can find a list of all accessible actions and search for the ones that can be used to expose resources.
Repeat these steps for all other users and roles reported on the findings detail page in case they have different cloud entitlement structures.
Navigating cloud entitlements
There are a number of actions you can take while using the cloud entitlements page to make it easier to search through the large amounts of principals an organization is likely to have in addition to the high number of permissions a principal may possess.
Filtering IAM principals and cloud entitlement criteria
To filter principals, select the filter icon and at least one filter option. Available filters are cloud account, tag, or environment. You can also use the search bar in the upper-right corner to locate a specific principal with regard to tab you're on (User, Group, or Role).
You can also filter the graph results on a principal's access details page for a given service by selecting the access types, actions, or policies you want to include from the drop-down menus above the graph.
View groups for your organization
From the cloud entitlements page, select the Groups tab to see a list of all IAM groups scanned from your cloud accounts. Available information includes the group name, the number of IAM users (if any) that belong to the group, IAM policies that are assigned to the group, and the cloud account the group belongs to. As many groups may have the same name across different cloud accounts, it's helpful to filter this tab to a single cloud account for review.
You can select a group to see additional information about it, including a filtered list of users, a total IAM policy count, and a link to any findings that have flagged for the group.
NoteWhile IAM groups are principals as defined by the cloud provider, the cloud entitlements service organizes them only as lists of users with one more policies attached. That means the service access details page and connected resources can only be viewed by selecting a user or role.
View roles for your organization
From the cloud entitlements page, select the Roles tab to see a list of all IAM roles scanned from your cloud accounts. Most of the information about roles is similar to that of the Users tab (highlights, services, and so on), but you can also see if the role can be assumed by any other entities (users, roles, services, or accounts), and how many. As many roles may have the same name across different cloud accounts, it's helpful to filter this tab to a single cloud account for review.
You can select a role to see additional information about it, including services it has permissions on and a count of resource types and total resources for each service. The Can be assumed by tab provides more detailed information (highlights, cloud account, services, and so on) about any user, role, service, or account that can assume the role.
Get reports for selected principals
If you'd like to distribute reports on one or more principals, apply the relevant filters to get the scope you want, then click the download icon next to the search bar from the Explore > Entitlements page. This produces a CSV file for the current list of users.
Switching between graph and table view
If you don't want to use the graph view on the service access details page, you can click the Table button in the upper-right corner of the page to see the same data represented in a table. The table format presents the resource groups first, their associated permissions, and the policies granting those permissions along with highlights of the most common access types available. To switch back to graph mode, just select the Graph button.
You may want to use the table view when a large number of cloud entitlements or roles is making it difficult to parse the data on a graph, and you're not sure which filters to apply.
Entitlements limitations
Cloud entitlements can only display the actions available to the user or role that it calculates from supported policies. This includes identity-based policies (inline and managed) and trust policies for roles.
The following are not supported in the service when calculating actions:
- Service control policies.
- Permission boundary policies.
- Resource policies.
This means that if a user or role has an action that is initially granted by a supported policy and then suppressed by an unsupported policy, the cloud entitlements service shows that action as available for the user or role. While unsupported policies are planned for implementation in future updates, be mindful of how they can impact your results in the current iteration of cloud entitlements.
Ephemeral resources
Ephemeral cloud resources are temporarily created and destroyed on demand once they've performed a required task. These resources are unlikely to appear in cloud entitlements due to the time needed to populate data and the temporary nature of the resource.