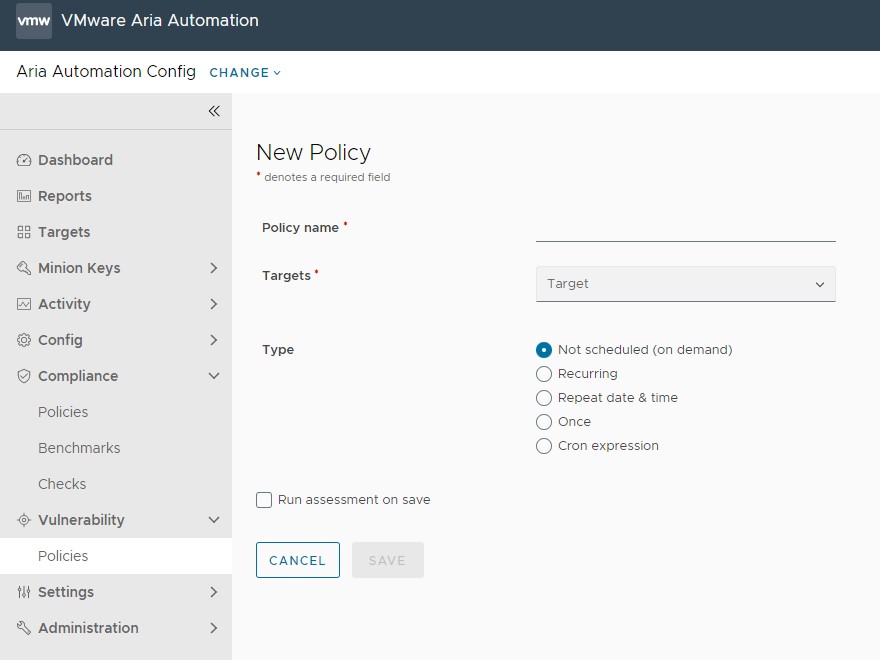
To begin using Automation for Secure Hosts Vulnerability, first create your security policy. In your policy, add the minions you want to target in an assessment and determine the assessment’s run schedule.
A vulnerability policy is comprised of a target and an assessment schedule. The target determines which minions to include in an assessment and the schedule determines when assessments will be run. A security policy also stores the results of the most recent assessment in Automation for Secure Hosts Vulnerability. Policies can also include schedules, as well as specifications for handling exemptions.
| Component | Description |
|---|---|
| Target | A target is the group of minions, across one or many Salt masters, that a job’s Salt command applies to. A Salt master can also be managed like a minion and can be a target if it is running the minion service. When you choose a target in Automation for Secure Hosts Vulnerability, you define the group of assets (referred to as minions) your policy will apply to. You can choose an existing target or create a new one. |
| Schedule | Choose the schedule frequency from Recurring, Repeat Date & Time, Once, or Cron Expression. Additional options are available, depending on the scheduled activity, and on the schedule frequency you choose.
|
Prerequisites
Before creating your first security policy, you need access to the vulnerability library. For more information, see Using the vulnerability library for more information.
You must also create the targets that you want to assess before creating your policy. A target is the group of assets (referred to as minions) your policy will apply to.
Procedure
Results
The policy is saved. If you selected Run assessment on save, the policy is run immediately after saving. If necessary, you can edit a policy by selecting the policy from the Vulnerability workspace and clicking Edit Policy and then Save.