SAML enables integration into VMware Workspace ONE (WS1) and takes advantage of the App Catalog, network access restrictions, and step-up authentication when administrators sign in. In this section, you will understand how to configure SAML for Avi Load Balancer control plane authentication with WS1 access being the IDP.
You can configure granular role-based access control by adding application parameters into the Workspace One Access catalog item and then mapping those parameters to different roles in Avi Load Balancer. For more information, see Tenant and Role Mapping Examples.
Prerequisites
Before initiating the configuration, complete the following prerequisites:
Configure a DNS record for the Avi Load Balancer Controller. This will be used for the fully qualified domain name (FQDN) that is used when signing into the system.
Get the Workspace ONE Access IDP metadata.
Follow the steps below to download the idp.xml file:
Log in to the Workspace ONE Access administrator console.
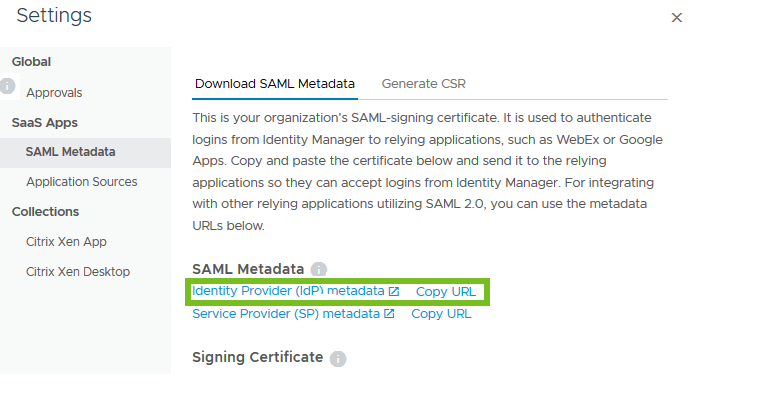
Navigate to the .
Click SAML Metadata under SaaS Apps.
-
In the Download SAML Metadata tab, click Copy URL next to Identity Provider (IdP) metadata.
SAML Configuration in Avi Load Balancer
To configure an authentication profile to support SAML on the Avi Load Balancer Controller, follow the below:
Log in to the Avi Load Balancer Controller with admin credentials.
Navigate to the and click CREATE.
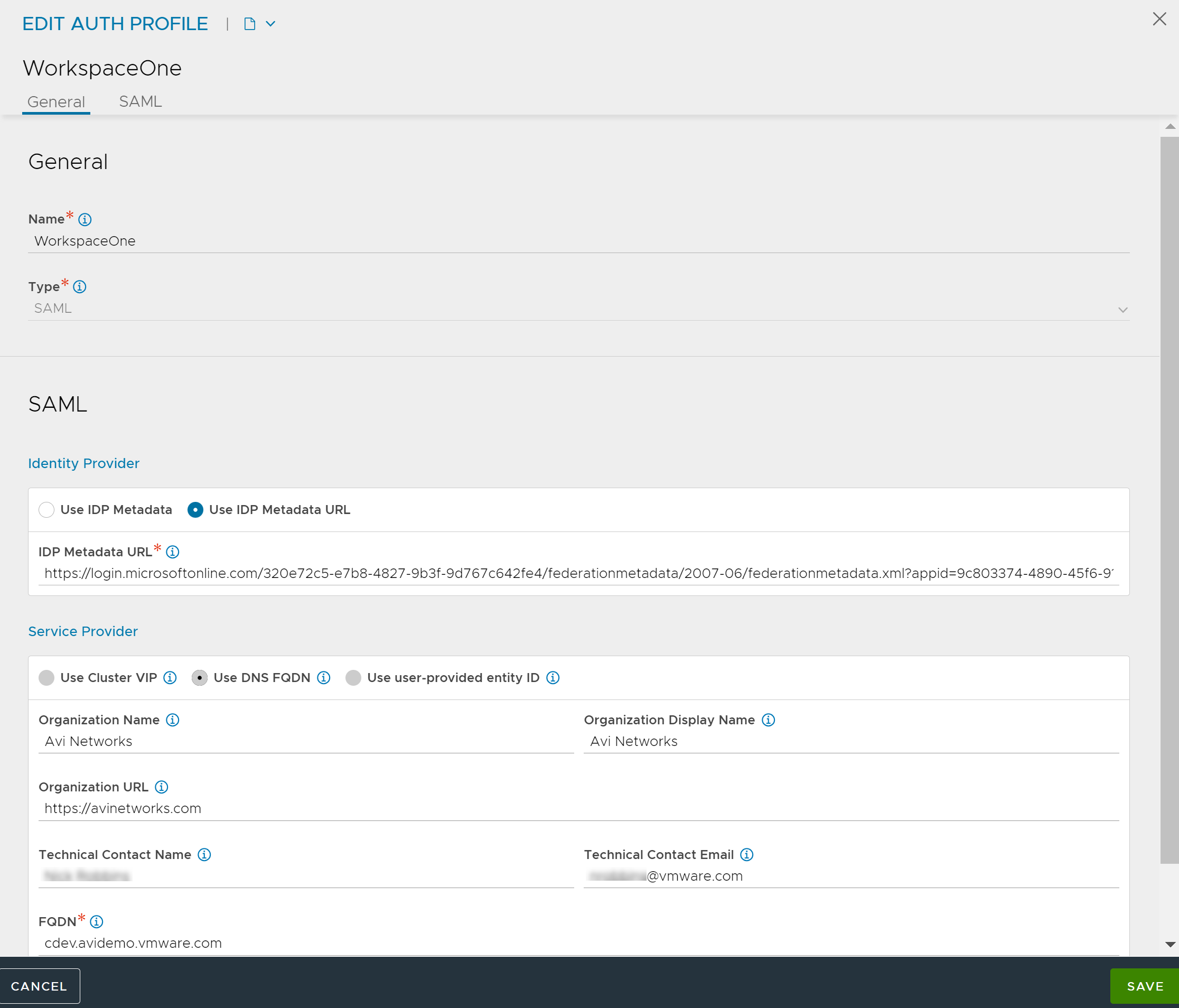
Enter the Name of the auth profile.
Select SAML as the Type of auth profile.
Select Use IDP Metadata URL option and paste the URL in theEnter IDP Metadata URL field.
Under Service Provider, select Use DNS FQDN.
Enter the service provider organization details, as required.
Enter the FQDN to be used for the SAML configuration.
Click Save.
Collecting Service Provider Metadata
Avi Load Balancer does not generate an xml file that can be imported into Workspace ONE Access. So, the metadata must be entered manually. Collect the following details:
Entity ID
SSO URL
Signing Certificate
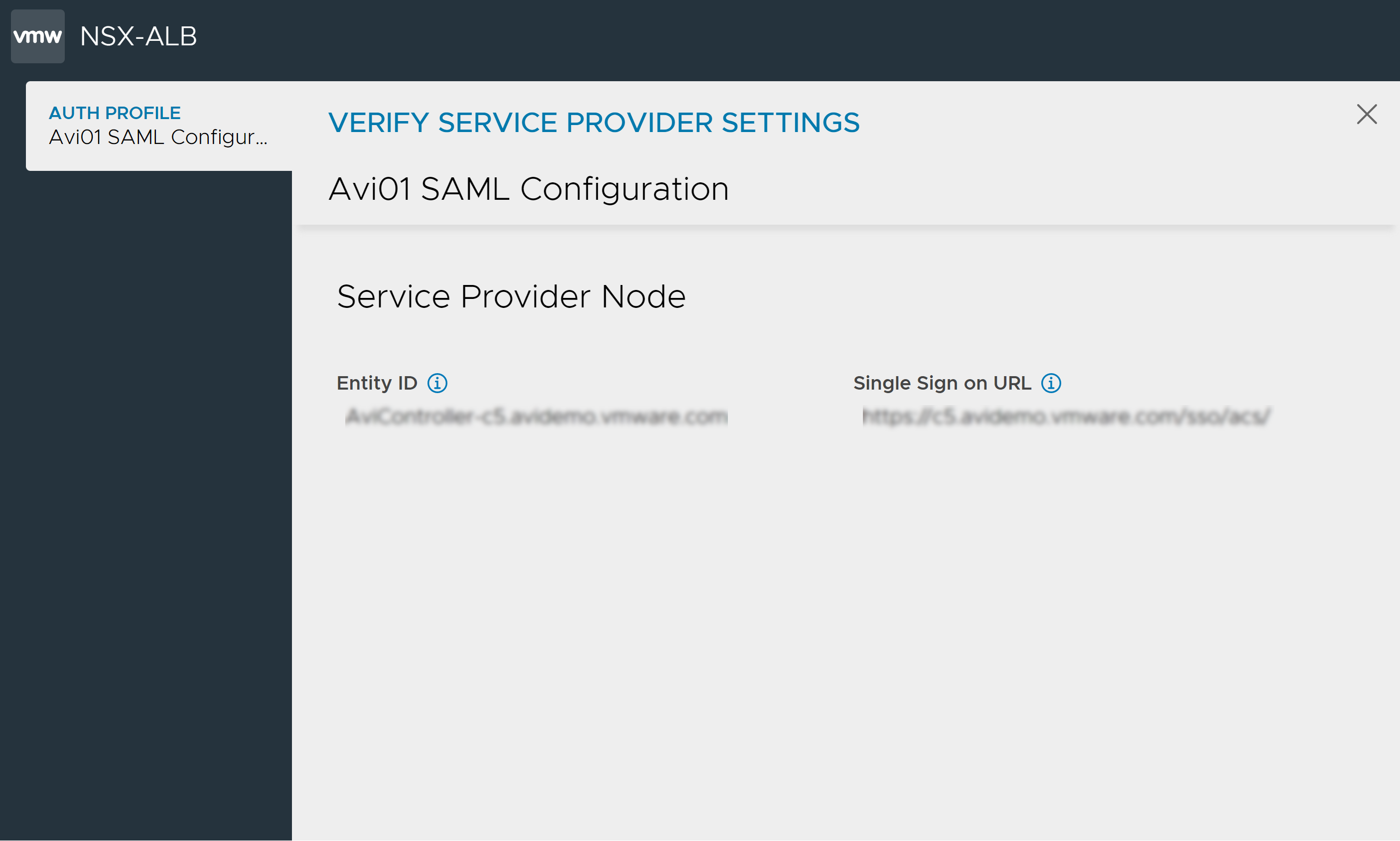
Get the entity ID and the SSO URL from the VERIFY SERVICE PROVIDER SETTINGS screen as shown below.
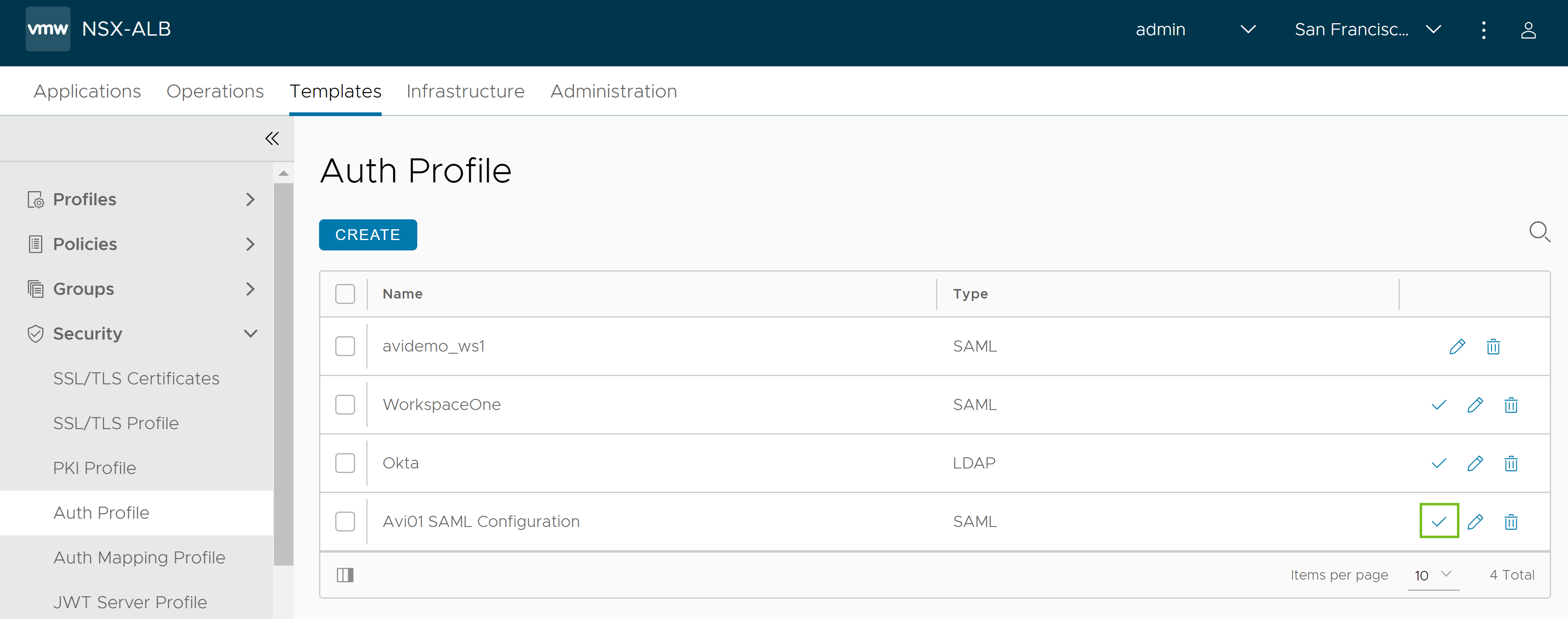
Navigate to .
-
Identify the authentication profile created and click verify icon.
-
The VERIFY SERVICE PROVIDER SETTINGS screen displays the Entity ID and the Single Sign on URL. Copy this information and paste in a text editor.
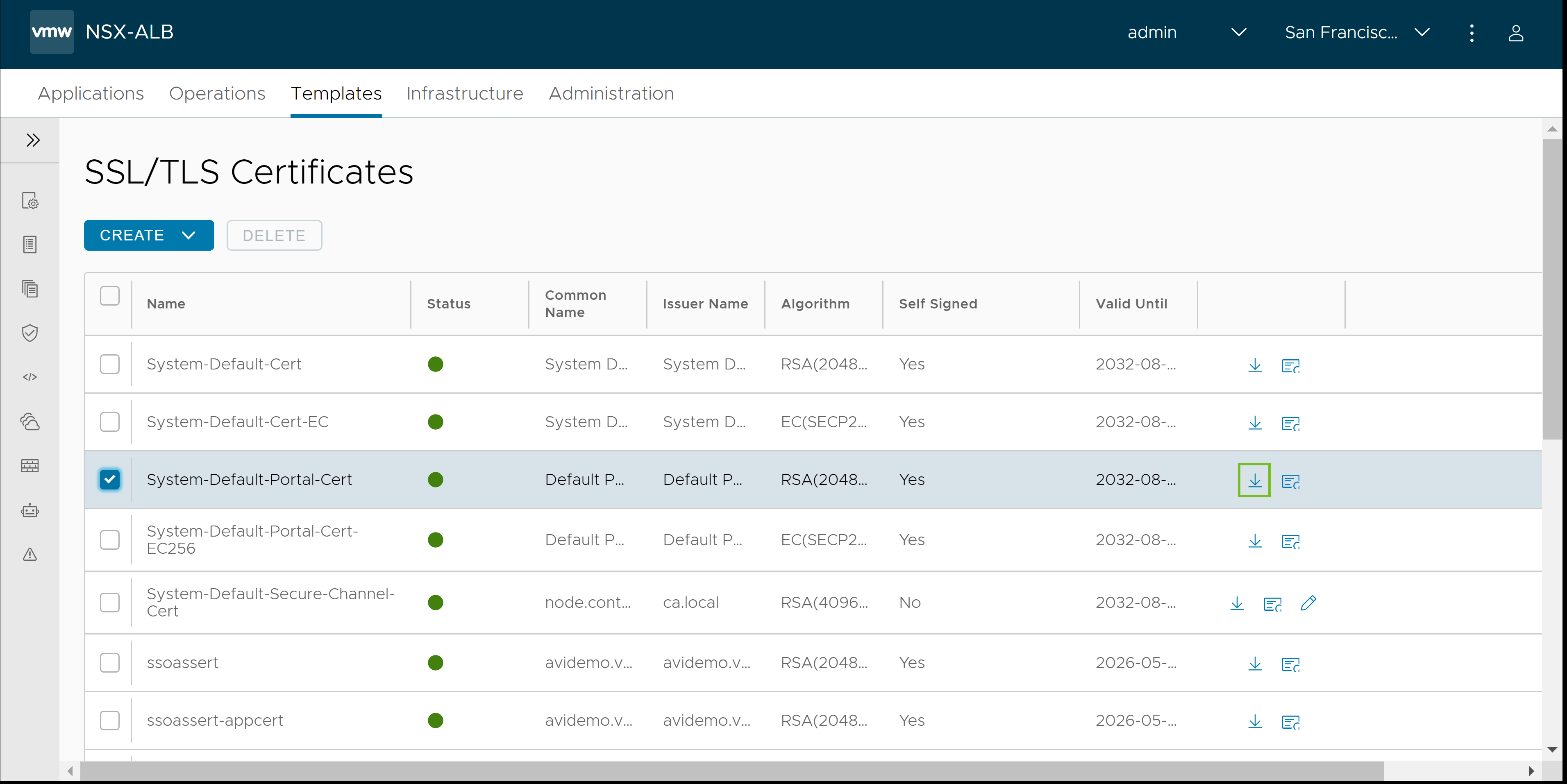
Get the signing certificate from SSL/TLS Certificates as shown below.
From the Avi Load Balancer UI, navigate to .
-
Identify the
System-Default-Portal-Certand click Export icon.
-
From the Export Certificate screen, click Copy to clipboard to copy the Key and the Certificate.
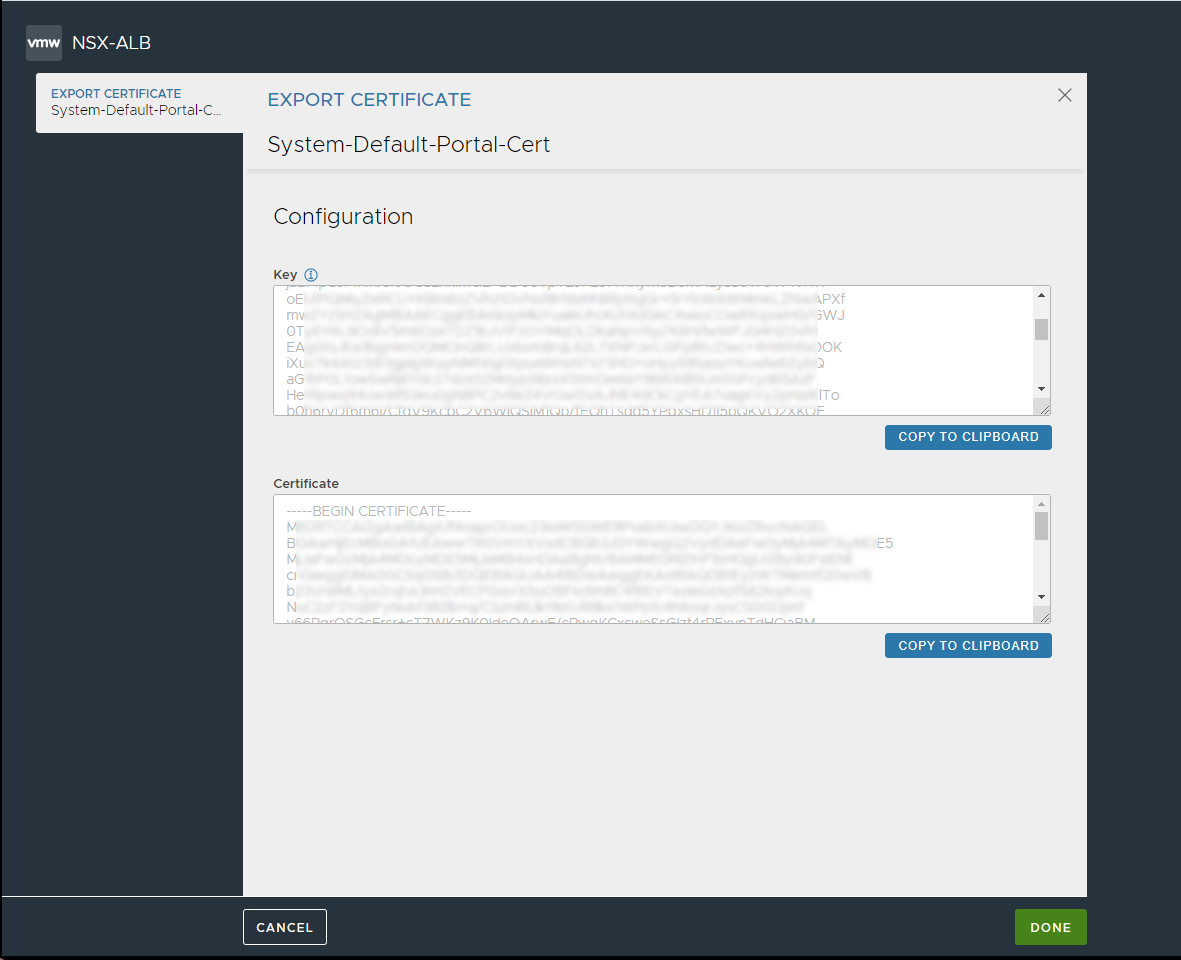
Paste the details into a text editor.
Click DONE.
Configuring Auth Mapping Profile
From the Avi Load Balancer UI, navigate to .
Click CREATE or edit an existing auth mapping rule.
Enter Name and Description.
Select SAML as the Type.
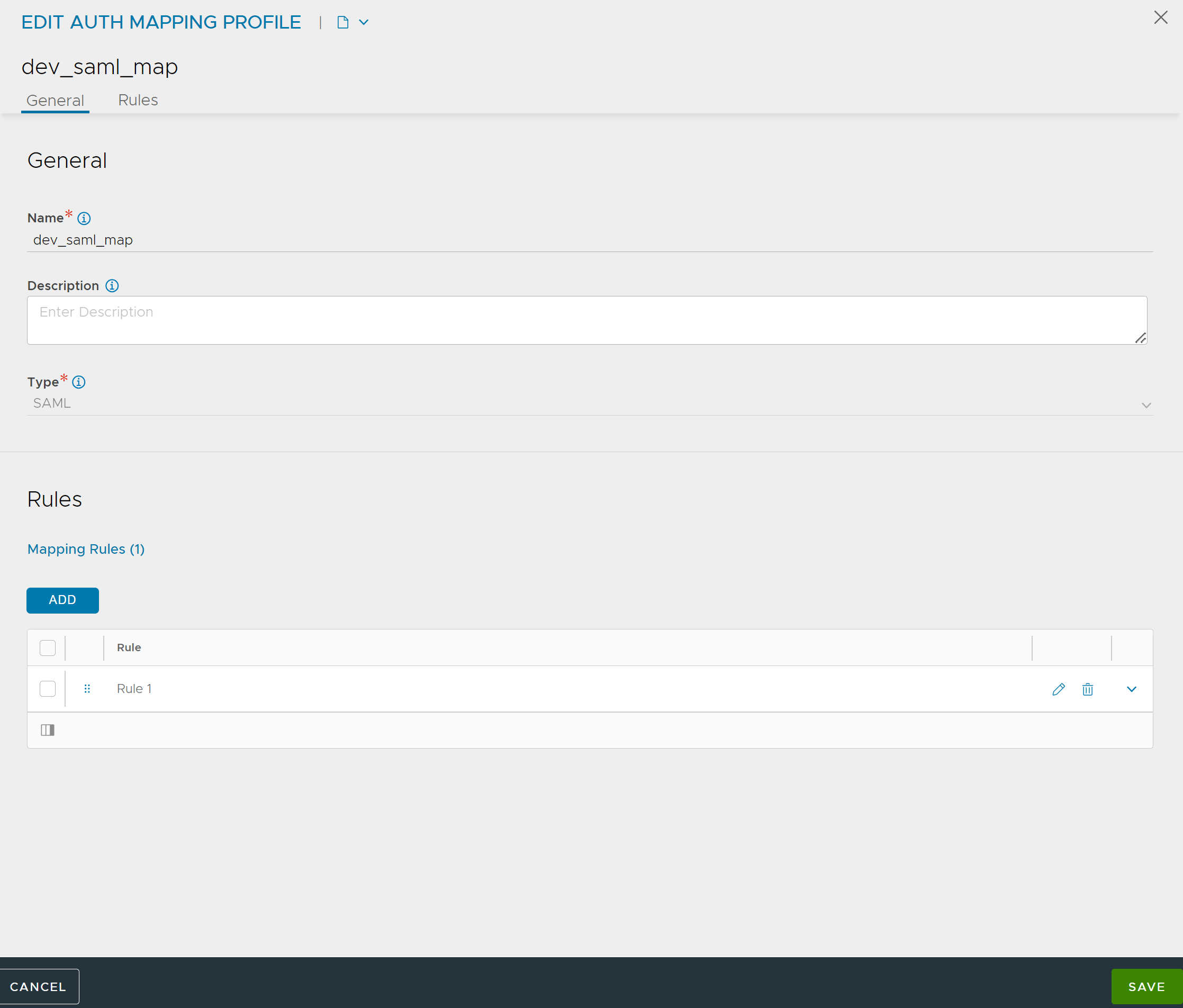
Note:Depending on the type selected, the auth profile settings are displayed.
Under Rules, Click ADD. A new Mapping Rule screen appears.
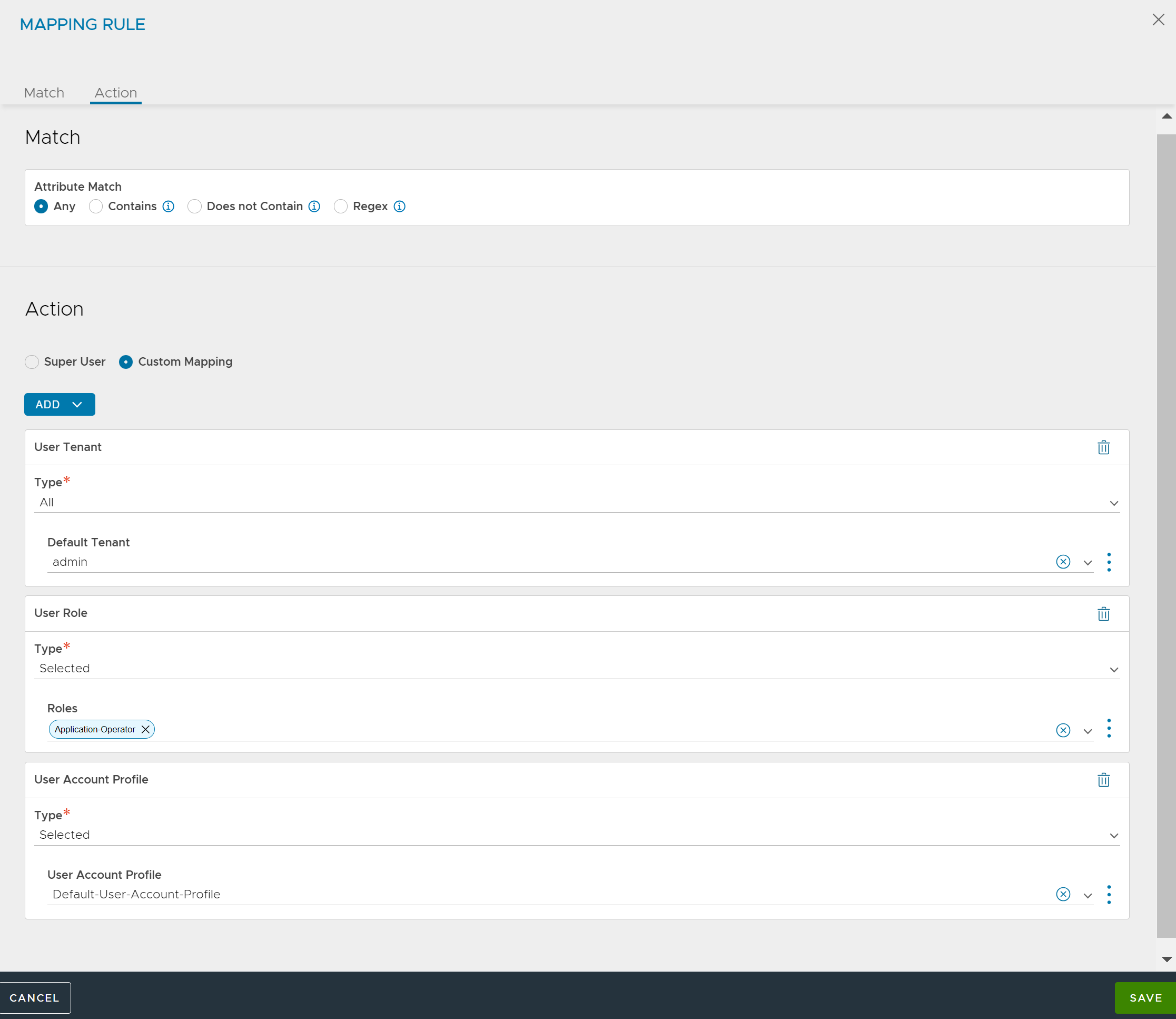
Under Match, select the filter for the Attribute Match.
Any: Users match regardless of attributes or their values.
Contains: The user must have the specified attribute, and the attribute must have one of the specified values.
Does Not Contain: The user must not have the specified attribute and value(s).
Regex:
Under Action, select Custom Mapping.
Select and configure User Tenant, User Role, or User Account Profile from the ADD drop-down menu as required. For more information, see User Tenant, User Roles, and User Account Profile.
Click Save.
Configuring Remote Authentication
By default, a Controller will have only local authentication established (Authentication/Authorization: Local).
To configure remote authentication using the NSX Advanced Load Balancer UI, follow the steps below:
Navigate to .
In the Edit System Settings screen, select Remote as the Authentication method.
SelectEnable Local User Login to allow users from the local user database to log in with their user credentials.
Under Auth Profiles & Mapping Profiles, click Add.
From the Select Auth Profile drop-down menu, select the previously created remote Auth Profile.
From the Select AUTH Mapping Profile drop-down menu, select an existing Mapping Profile or click the vertical menu icon (three dots) to create a new Mapping Profile. For more information, see Configuring Auth Mapping Profile.
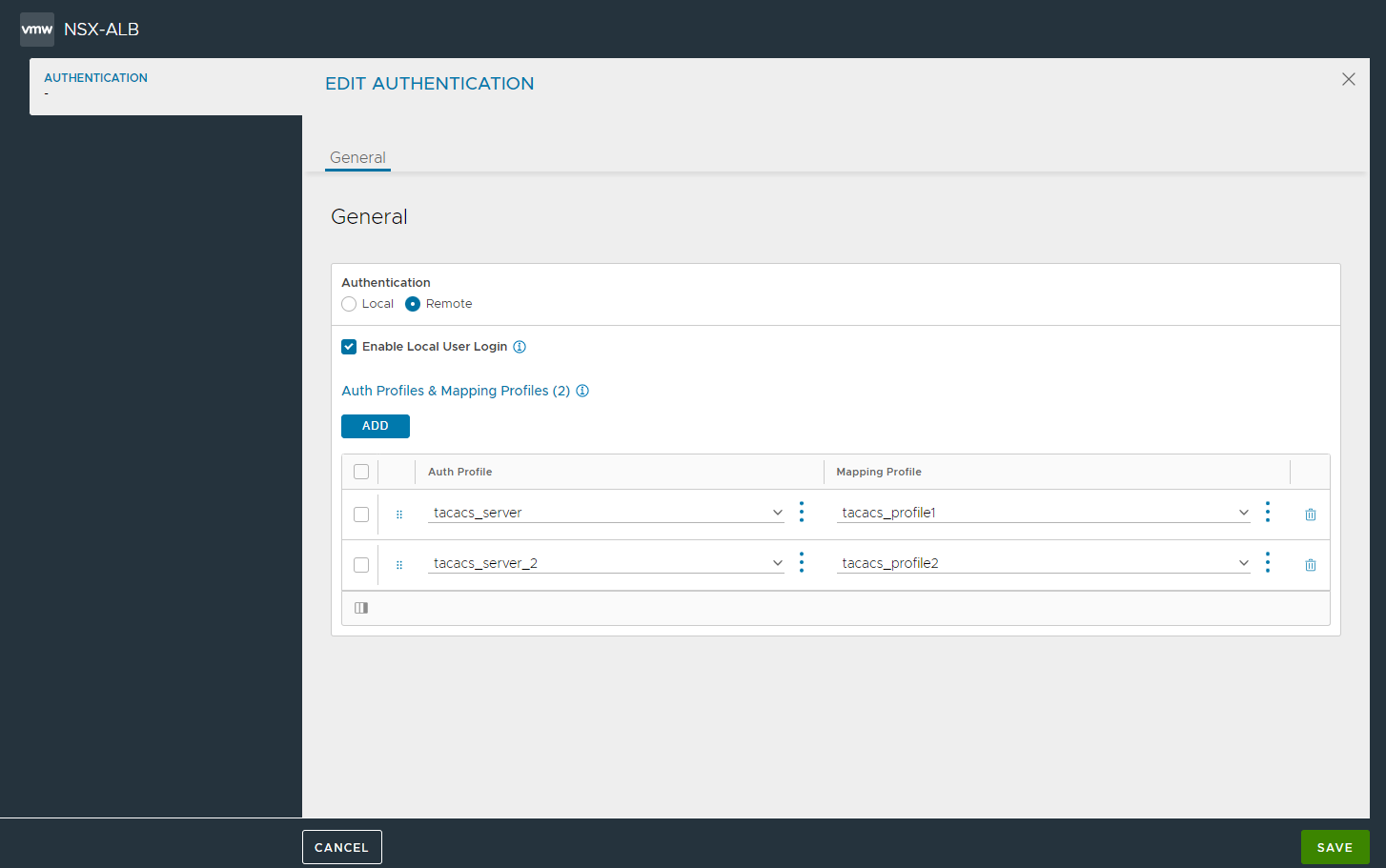
Click Save.
Note:Tenant and role mapping are available only with remote authentication.
Configuring the Avi Load Balancer Catalog Item in Workspace ONE Access
Once the SAML profile is created in the Avi Load Balancer Controller, the Workspace ONE catalog entry can be created.
To create the Workspace ONE catalog entry, do the following:
Log in to your Workspace ONE Access administrator console.
Navigate to the Catalog tab.
Click New.
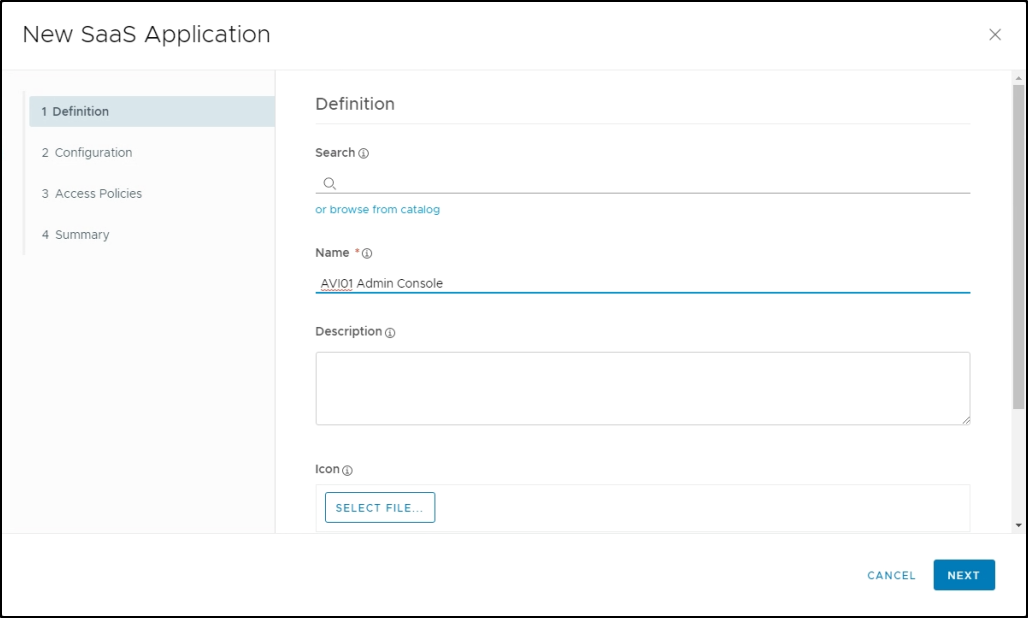
In the New SaaS Application screen, enter a Name for the new Avi Load Balancer entry in the App Catalog.
-
Under the Definition tab, if you have an icon to use, click Select File, upload the icon for the application, and click Next to view the Configuration tab.
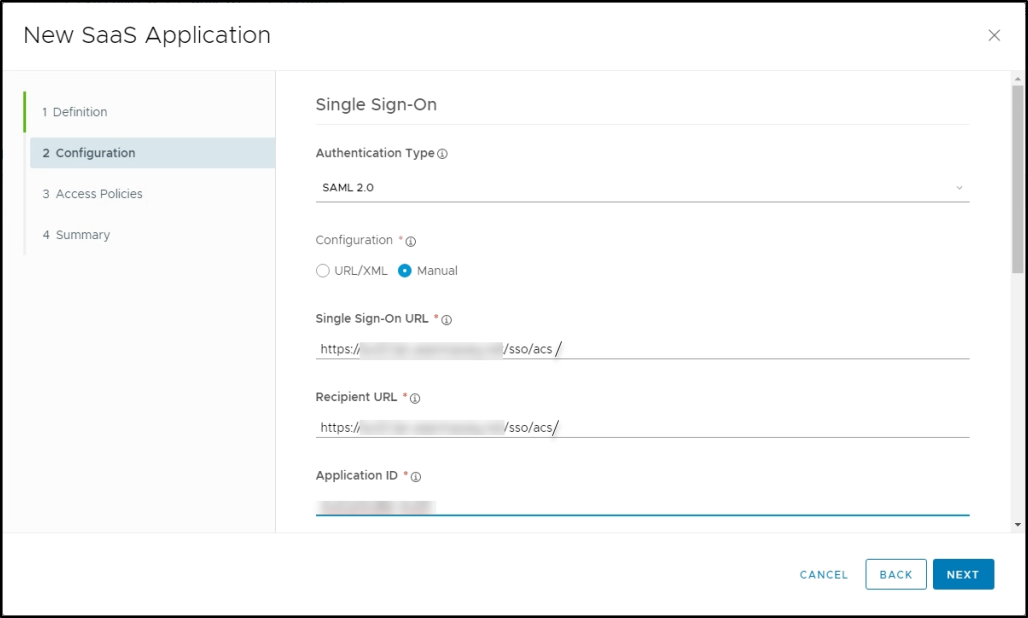
In the Configuration tab, enter the details as shown below:
The Configuration tab in the New SaaS Application screen is as shown below.Field
Description
Single Sign-On URL
Use the Single Sign on URL copied from the VERIFY SERVICE PROVIDER SETTINGS screen in Avi Load Balancer.
Note:The trailing slash (/) after acs is mandatory.
Recipient URL
Use the Single Sign-On URL.
Application ID
Use the Entity ID copied from the VERIFY SERVICE PROVIDER SETTINGS screen in Avi Load Balancer.
Username Format
Unspecified.
Username Value
${user.email}.
Relay State URL
The FQDN or IP address of your appliance.
Click Advanced Properties and configure the properties as shown below:
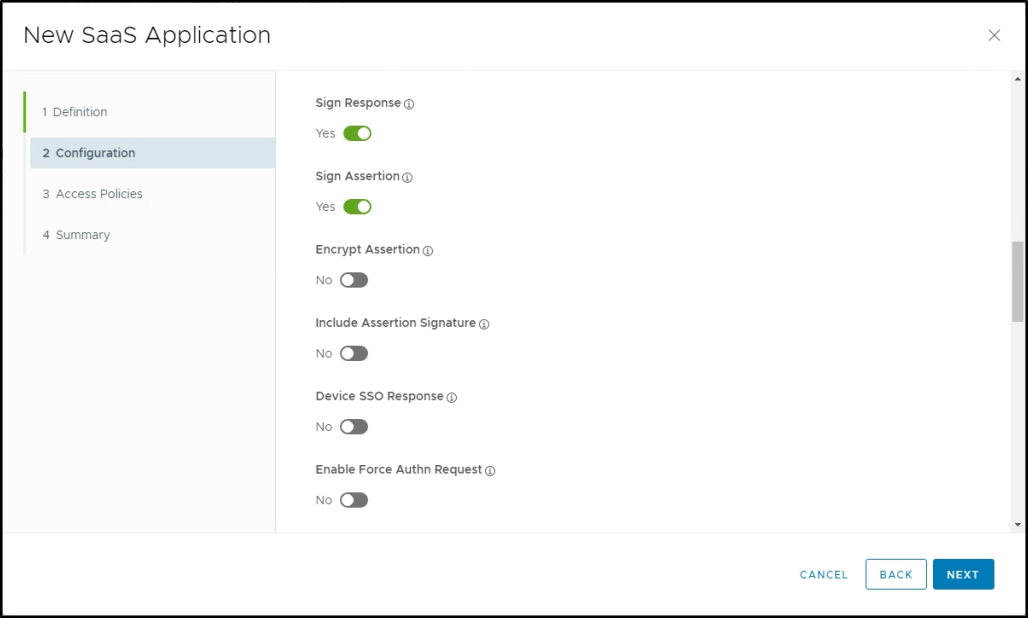
Copy the value of the System-Default-Portal-Cert certificate and paste it into the Request Signature field.
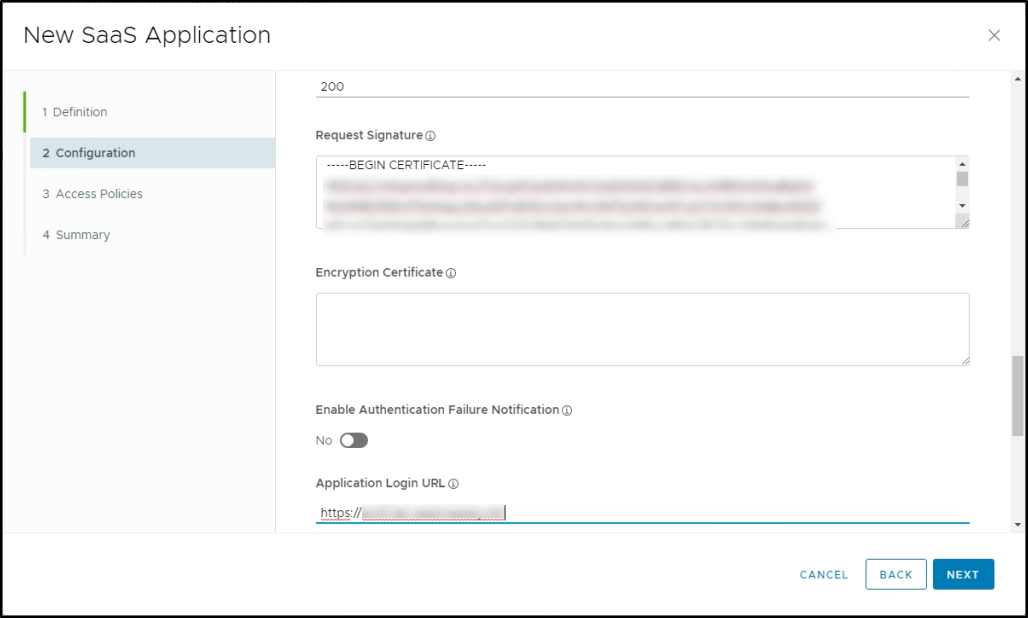
Enter the FQDN or IP address of the appliance as the Application Login URL. This enables SP-initiated login workflows.
Click Next to select Access Policies to use for this application. This determines the rules used for authentication and access to the application.
Click Next to review the Summary of the configuration.
Click Save & Assign and select the users or groups that will have access to this application and the deployment type.
Click Save.